Network Security Threats
Network Security
- Combination of low-cost powerful computing and high-performance networks is a two-edged sword:
- Many powerful new services and applications are enabled
- But computer systems and networks become highly susceptible(敏感) to a wide variety of security threats
- Openness vs Security
- Network security involves countermeasures(对策) to protect computer systems from intruders(入侵者)
- Firewalls, security protocols, security practices, etc.
Eavesdropping
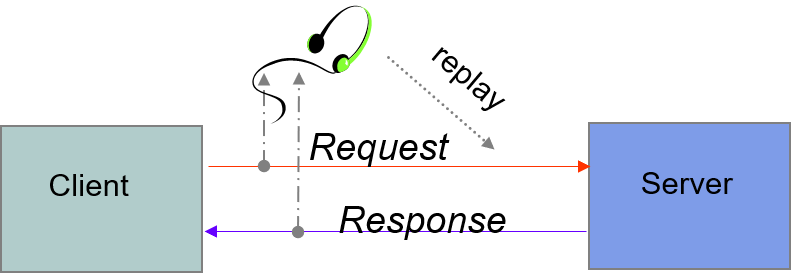
- Information transmitted over network can be observed and recorded by eavesdroppers (using a packet sniffer)
- Information can be replayed(重播) in attempts to access server
- Requirements: privacy, authentication(认证), non-repudiation(否认)
Client Imposter
client imposter(冒名顶替者)
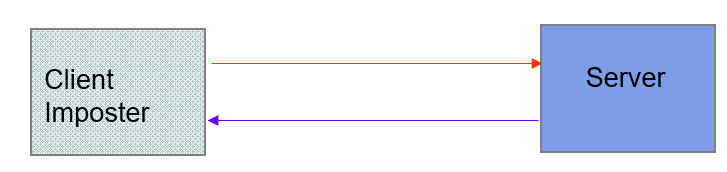
- Imposters attempt to gain unauthorized(未经授权的) access to server
- Ex. bank account or database of personal records
- For example, in IP spoofing(戏弄) imposter sends packets with false source IP address
Requirements: privacy, authentication
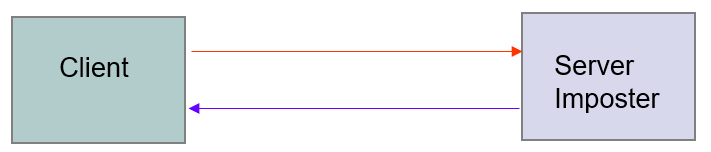
Server Imposter

- An imposter impersonates(模拟) a legitimate(合法的) server to gain sensitive information from a client
- E.g. bank account number and associated user password
- Requirements: privacy, authentication, non-repudiation
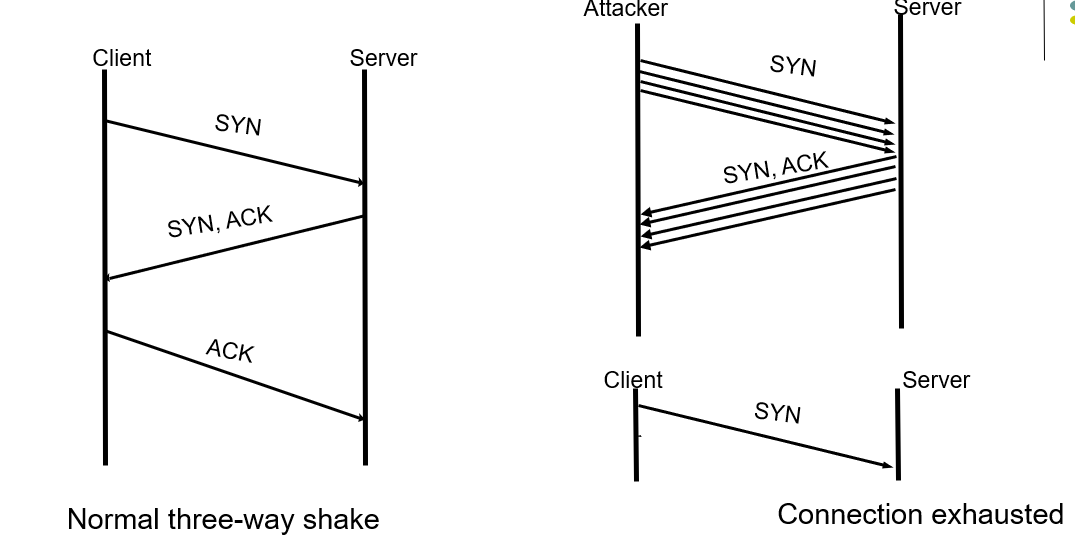
Denial of Service (DoS) Attack
- Attacker can flood a server with requests, overloading the server resources (er. TCP Three-way handshake)
- Results in denial of service to legitimate clients
- Distributed denial of service attack on a server involves coordinated attack from multiple (usually hijacked) computers
- Requirement: availability
TCP SYN Flood
- The attacker sends a repeated same packet, to every port on the target server over using a fake IP address.
- The server will send back ack continunously, prevents other client sending syn.
Man-in-the-Middle Attack

- An imposter manages to place itself as man in the middle
- convincing the server that it is legitimate client
- convincing legitimate client that it is legitimate server
- gathering sensitive information and possibly hijacking(劫持) session
- Requirements: integrity, authentication
Malicious Code
- A client becomes infected with malicious code
- Virus: code that when executed, inserts itself in other programs
- Worms: code that installs copies of itself in other machines attached to a network
- Requirements: privacy, integrity, availability
Security Requirements
Security threats motivate requirements:
- Privacy: information should be readable only by intended recipient(接受者)
- Integrity: recipient can confirm that a message has not been altered during transmission
- Authentication: it is possible to verify that sender or receiver is who he claims to be
- Non-repudiation*(不可抵赖性): sender cannot deny having sent a given message.
- Availability: of information and services
Countermeasures
- Secure communication channels
- Encryption
- Cryptographic checksums and hashes (加密校验和和散列)
- Authentication
- Digital Signatures
- Secure borders
- Firewalls
- Virus checking
- Intrusion detection(入侵检测)
- Authentication
- Access Control (访问控制)
Network Security Threats的更多相关文章
- android9.0适配HTTPS:not permitted by network security policy'
app功能接口正常,其他手机运行OK,但是在Android9.0的手机上报错 CLEARTEXT communication to 192.168.1.xx not permitted by netw ...
- Android版本28使用http请求报错not permitted by network security policy
Android版本28使用http请求报错not permitted by network security policy android模拟器调试登录的时候报错 CLEARTEXT communic ...
- 《Network Security A Decision and Game Theoretic Approach》阅读笔记
网络安全问题的背景 网络安全研究的内容包括很多方面,作者形象比喻为盲人摸象,不同领域的网络安全专家对网络安全的认识是不同的. For researchers in the field of crypt ...
- Azure PowerShell (13) 批量设置Azure ARM Network Security Group (NSG)
<Windows Azure Platform 系列文章目录> 刚刚在帮助一个合作伙伴研究需求,他们的虚拟机全面的网络安全组(Network Security Group, NSG)会经常 ...
- Network Security Services If you want to add support for SSL, S/MIME, or other Internet security standards to your application, you can use Network Security Services (NSS) to implement all your securi
Network Security Services | MDN https://developer.mozilla.org/zh-CN/docs/NSS 网络安全服务 (NSS) 是一组旨在支持支持安 ...
- Firewall & Network Security
Firewall & Network Security 防火墙 & 网络安全 NAT Gateway VPC Virtual Private Cloud refs https://en ...
- 网络安全服务(Network Security Services, NSS
网络安全服务(Network Security Services, NSS)是一套为网络安全服务而设计的库 支持支持安全的客户端和 服务器应用程序.使用NSS构建的应用程序可以支持SSL v2 和v3 ...
- Network Security final project---War Game
项目介绍: 为自己的网段设置防火墙并尝试攻击其他组 网络结构: 每组有3个机器,包含一个gateway和两个workstation,其中gateway是可以连接到其他组的gateway,但是无法连接到 ...
- Mozilla Network Security Services拒绝服务漏洞
解决办法: 运行 yum update nss yum update nss
随机推荐
- Effective C++ .06 阻止编译器自动生成函数以及被他人调用
这节讲了下如何防止对象拷贝(隐藏并不能被其他人调用) 两种方法: 1. 将拷贝构造函数声明为private 并且声明函数但不进行定义 #include <iostream> #includ ...
- easy html+css tree 简单的HTML+css导航树
code: show:
- sql left join 字符串
select * FROM table1 as t1 right join (select '1,2,3,4,5' as t) as tt on t1.Id=tt.t select * FROM t ...
- 原生JS,运动的小人
今天突然想起来,不知道在什么网站上看的一个纯纯的原生JS写的效果,运动的小人,所以在这里给大家分享一下代码: 并说明:这不是本人写的,而是我在浏览网站是无意中发现的,现在已经不记得是哪个网站了,但是要 ...
- 使用spring tool suite(STS)工具创建spring boot项目和出现错误后的处理
一.先下载配置maven环境 1.下载地址:http://maven.apache.org/download.cgi windows下下载zip文件 2.解压后放到某个文件目录下 3.配置环境变量 ( ...
- Opencv2.4.13与Visual Studio2013环境搭建配置教程
转载:http://www.jb51.net/article/108943.htm 一.安装包的下载与安装 Opencv可免费到官网上去下载,opencv是国外软件,在下载是由于受资源的限制,可能会出 ...
- sqlserver批量删除表
--批量删除表 ) DECLARE tmpCur CURSOR FOR SELECT name FROM sys.objects WHERE TYPE='U' AND name LIKE N'%_Qu ...
- Linux ->> Ubuntu 14.04 LTE下配置SSH免密码登录
首先用apt-get命令安装SSH jerry@ubuntu:~$ sudo apt-get install ssh [sudo] password for jerry: Reading packag ...
- 关于windows server 里Let's Encrypt续订的问题
引言 Let's Encrypt是什么就不详细说了,它是免费的https证书,优点就是免费,缺点就是每三个月就要自己续上.今天主要介绍的是续上有效期的环节. 1.安装certify 下载地址: htt ...
- Python学习---重点模块之re
正则表达式是用来操作字符串,但是字符串提供的正则是完全匹配,有时候我们需要进行模糊匹配,这个时候就需要正则表达式了.通过re模块来实现,由C语言来执行底层的匹配 字符匹配(普通字符,元字符): 1 普 ...
