12-kubernetes Dashboard 认证及分级授权
部署 dashboard
根据官方文的安装介绍,直接远程执行即可,这里先下载下来,然后执行:
[root@master ~]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml[root@master ~]# kubectl apply -f kubernetes-dashboard.yamlsecret/kubernetes-dashboard-certs createdserviceaccount/kubernetes-dashboard createdrole.rbac.authorization.k8s.io/kubernetes-dashboard-minimal createdrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal createddeployment.apps/kubernetes-dashboard createdservice/kubernetes-dashboard created
查看
[root@master ~]# kubectl get pods -n kube-systemNAME READY STATUS RESTARTS AGEcoredns-5c98db65d4-8mzfz 1/1 Running 0 44dcoredns-5c98db65d4-spjx8 1/1 Running 0 44detcd-master.kubernetes 1/1 Running 0 44dkube-apiserver-master.kubernetes 1/1 Running 0 44dkube-controller-manager-master.kubernetes 1/1 Running 0 44dkube-flannel-ds-amd64-4szk7 1/1 Running 0 44dkube-flannel-ds-amd64-b4ssp 1/1 Running 1 44dkube-flannel-ds-amd64-nmklz 1/1 Running 0 44dkube-flannel-ds-amd64-wjczq 1/1 Running 0 44dkube-proxy-8fqsz 1/1 Running 0 44dkube-proxy-bkrw4 1/1 Running 0 44dkube-proxy-n75g8 1/1 Running 1 44dkube-proxy-rmckk 1/1 Running 0 44dkube-scheduler-master.kubernetes 1/1 Running 0 44dkubernetes-dashboard-7d75c474bb-cqwh6 1/1 Running 0 18s # 已经启动成功
开放访问
默认dashboard中启动的svc只能集群内部访问,所以需要手动配置对外访问,打一个补丁即可:
[root@master ~]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-systemservice/kubernetes-dashboard patched[root@master ~]# kubectl get svc -n kube-systemNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEkube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 44dkubernetes-dashboard NodePort 10.106.202.90 <none> 443:30090/TCP 3m16s
通过查看,dashboard的svc已经被映射到30090 这个端口,所以在浏览器直接输入任意节点的ip + 端口即可访问。
注意访问的地址是 https://IP:PORT
配置dashboard用户
Dashboard 登陆有两种认证方式:
- kubeconfig 文件认证
- token 令牌认证
下面对这两种认证都进行测试验证
1. token 令牌认证
创建一个 serviceAccount
在 kube-system 名称空间中创建
[root@master ~]# kubectl create serviceaccount dashboard-admin -n kube-system[root@master ~]# kubectl describe sa/dashboard-admin -n kube-systemName: dashboard-adminNamespace: kube-systemLabels: <none>Annotations: <none>Image pull secrets: <none>Mountable secrets: dashboard-admin-token-wrdvzTokens: dashboard-admin-token-wrdvzEvents: <none>
dashboard-admin 绑定 clusterbinding 的 sa
[root@master ~]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:\dashboard-adminclusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created[root@master ~]# kubectl describe clusterrolebinding/dashboard-cluster-adminName: dashboard-cluster-adminLabels: <none>Annotations: <none>Role:Kind: ClusterRoleName: cluster-adminSubjects:Kind Name Namespace---- ---- ---------ServiceAccount dashboard-admin kube-system
这帮绑定后,serviceaccount 的 dashboard-admin 就有集群的管理员权限了。
获取 serviceaccount 的 dashboard-admin 的secret信息
在创建好serviceaccount 的 dashboard-admin 后,会在 kube-system名称空间下的secret 中,自动创建一个 以 dashboard-admin 开头的 secret,携带者 token 字样
[root@master ~]# kubectl get secret -n kube-systemNAME TYPE DATA AGEattachdetach-controller-token-7nxx6 kubernetes.io/service-account-token 3 44dbootstrap-signer-token-c44r9 kubernetes.io/service-account-token 3 44dbootstrap-token-cgw8vp bootstrap.kubernetes.io/token 7 44dcertificate-controller-token-6682d kubernetes.io/service-account-token 3 44dclusterrole-aggregation-controller-token-g7l5s kubernetes.io/service-account-token 3 44dcoredns-token-gsrxq kubernetes.io/service-account-token 3 44dcronjob-controller-token-qch7l kubernetes.io/service-account-token 3 44ddaemon-set-controller-token-gmp2z kubernetes.io/service-account-token 3 44d# 下面这个就是自动生成的dashboard-admin-token-wrdvz kubernetes.io/service-account-token 3 6m50sdefault-token-ll59x kubernetes.io/service-account-token 3 44d... ...... ...
从上已经查看到了,下面需要查看一下详细信息即可获取到token的值
[root@master ~]# kubectl describe secret/dashboard-admin-token-wrdvz -n kube-systemName: dashboard-admin-token-wrdvzNamespace: kube-systemLabels: <none>Annotations: kubernetes.io/service-account.name: dashboard-adminkubernetes.io/service-account.uid: 4c593334-7f68-4190-85a2-f92fcab234d4Type: kubernetes.io/service-account-tokenData====namespace: 11 bytestoken: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4td3JkdnoiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNGM1OTMzMzQtN2Y2OC00MTkwLTg1YTItZjkyZmNhYjIzNGQ0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.YxE09BRCQbUA_nzE60s9eXOYZMjsWLEZfXqXuiRffpsl_KgfosSKtII_YbBESvLeaSi3qivrkgSNKHdPytS2zmZd9BdNbGbABjecRER5jSjNNeRjok6cixghSVR51VyzJN5PlpPHtlhOlshJLXg_IAXtYzq36AZTf4LQ5_17k_1DXIjOsL5j0N0CEljcQVvOhEPlyu3OGsVEJOijKSMcEXJmrV2z5Z4rUczSn83qNy1ZjT-DF2Avg3eMua5Pw0LkgP9zQF76q2MGYwWZDc5z0y53SoYxs7k12OKnRrHL0Vai11a8snGLH_Dt7jXY0UAKwpew6a6Gj4F4xsK1InxBtgca.crt: 1025 bytes
上面查看到的token 后面的一大串就是,把这一串复制到页面中就可以登录。
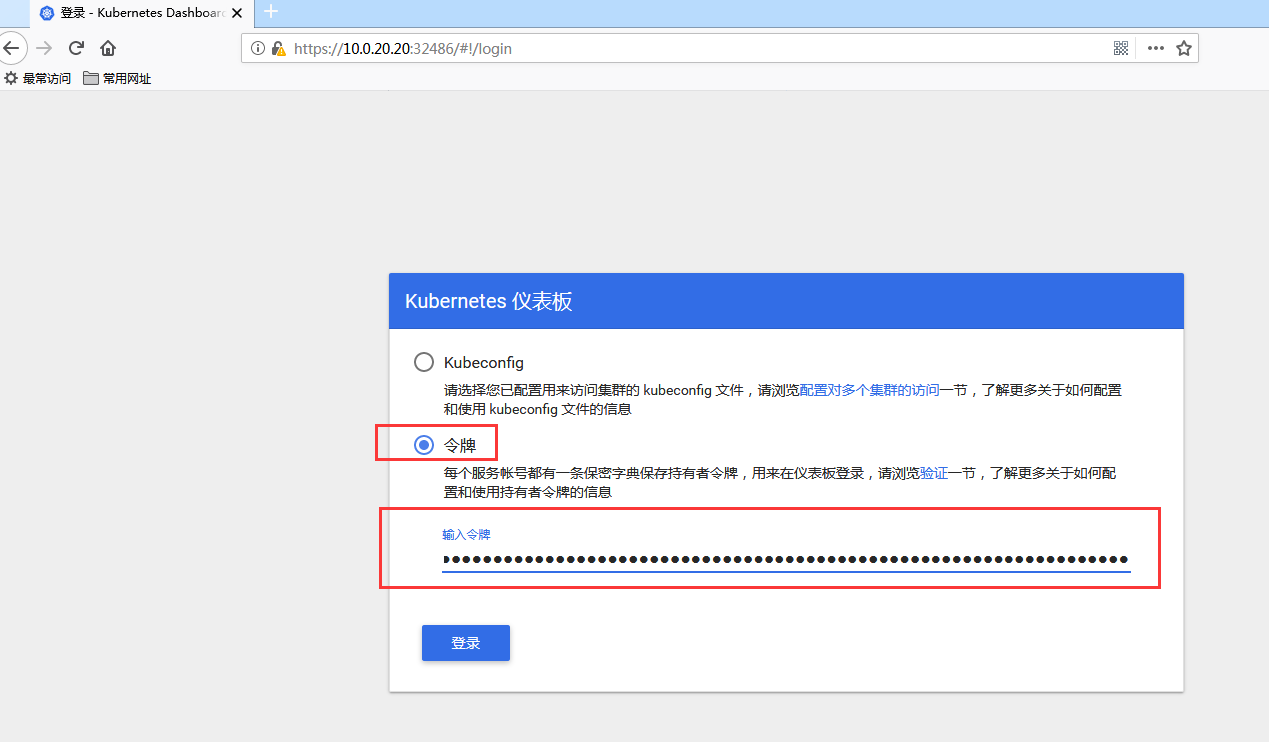
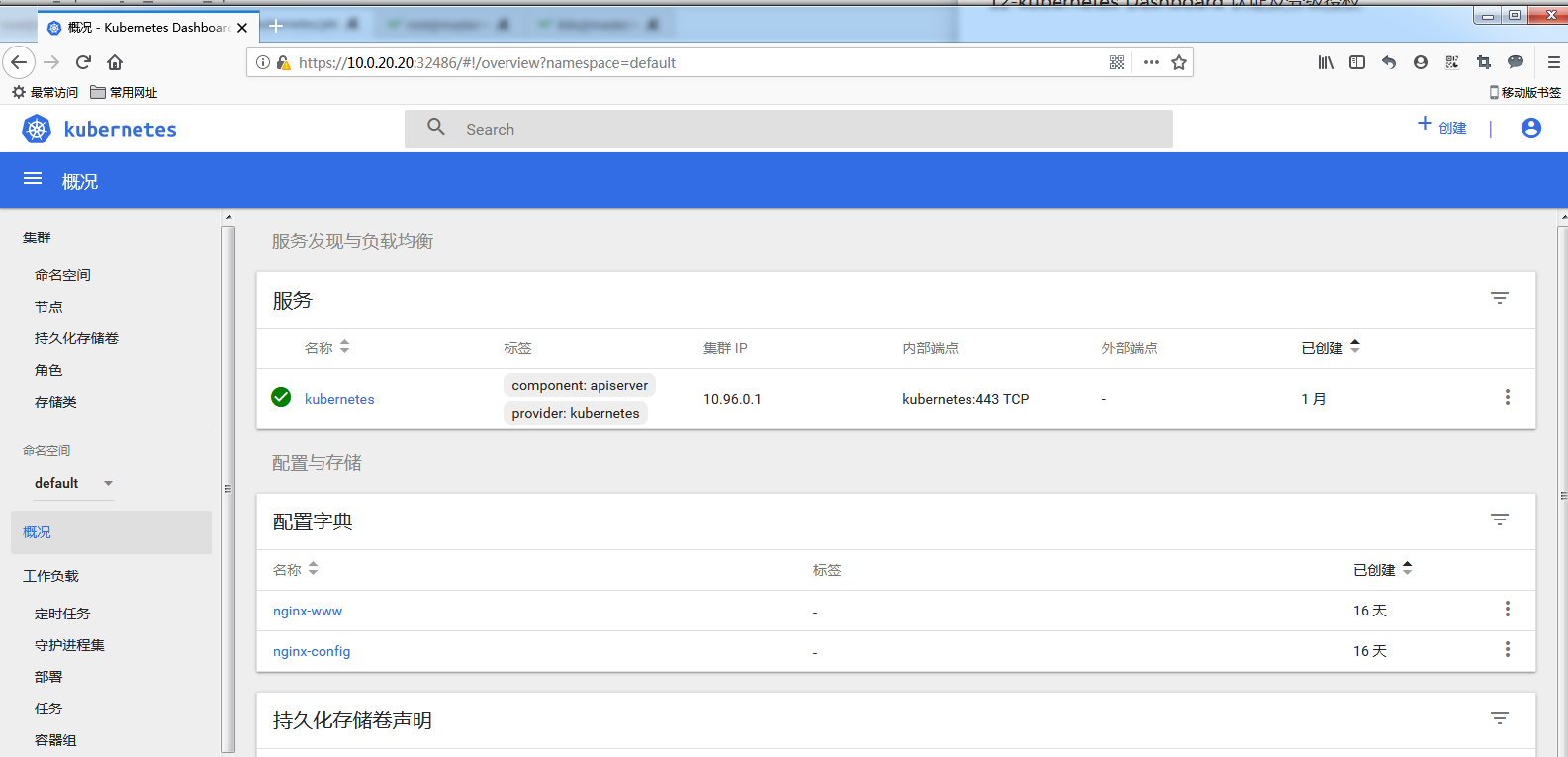
2. kubeconfig 文件认证
创建测试一个权限小一点的,只能访问default名称空间资源的账户
创建一个 serviceAccount
[root@master pki]# kubectl create serviceaccount def-ns-admin -n defaultserviceaccount/def-ns-admin created[root@master pki]# kubectl describe sa/def-ns-admin -n defaultName: def-ns-adminNamespace: defaultLabels: <none>Annotations: <none>Image pull secrets: <none>Mountable secrets: def-ns-admin-token-qfrqjTokens: def-ns-admin-token-qfrqjEvents: <none>
创建 rolebinding 绑定 def-ns-admin
[root@master pki]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-adminrolebinding.rbac.authorization.k8s.io/def-ns-admin created[root@master pki]# kubectl describe rolebinding/def-ns-admin -n defaultName: def-ns-adminLabels: <none>Annotations: <none>Role:Kind: ClusterRoleName: adminSubjects:Kind Name Namespace---- ---- ---------ServiceAccount def-ns-admin default
提示:这里和上面一样,到此步骤系统已经自动创建出一个secret,详细信息中包含token,可以直接使用此token登录dashboard,只能管理default名称空间下的资源。
创建集群和创建kubeconfig配置文件
[root@master pki]#[root@master pki]# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://10.0.20.20:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.confCluster "kubernetes" set.[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.confapiVersion: v1clusters:- cluster:certificate-authority-data: DATA+OMITTEDserver: https://10.0.20.20:6443name: kubernetescontexts: []current-context: ""kind: Configpreferences: {}users: []
拿到 def-ns-admin 用户的base64格式的token
先拿到对应的token后base64 解码
[root@master pki]# kubectl get secret def-ns-admin-token-qfrqj -o jsonpath={.data.token} | base64 -deyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
这样就获取到解码后的值了,然后保存到变量中
[root@master pki]# DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-qfrqj -o jsonpath={.data.token} | base64 -d)
这样执行后就保存下来了
设置 set-credentials 保存至 def-ns-admin.conf
[root@master pki]# kubectl config set-credentials def-ns-admin --token=${DEF_NS_ADMIN_TOKEN} --kubeconfig=/root/def-ns-admin.conf[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.confapiVersion: v1clusters:- cluster:certificate-authority-data: DATA+OMITTEDserver: https://10.0.20.20:6443name: kubernetescontexts: []current-context: ""kind: Configpreferences: {}users:- name: def-ns-admin # 认证的serviceaccountuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
配置成功
配置 def-ns-admin.conf 上下文
[root@master pki]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.confContext "def-ns-admin@kubernetes" created.[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.confapiVersion: v1clusters:- cluster: # 这里是上面创建的集群certificate-authority-data: DATA+OMITTEDserver: https://10.0.20.20:6443 # 这里是集群地址name: kubernetes # 这里集群名称contexts:- context: # 上面创建的上下文cluster: kubernetes # 集群user: def-ns-admin # serviceaccountname: def-ns-admin@kubernetescurrent-context: "" # 这里还没有配置当前上下文kind: Configpreferences: {}users:- name: def-ns-adminuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
配置当前上下文
[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.confapiVersion: v1clusters:- cluster:certificate-authority-data: DATA+OMITTEDserver: https://10.0.20.20:6443name: kubernetescontexts:- context:cluster: kubernetesuser: def-ns-adminname: def-ns-admin@kubernetescurrent-context: def-ns-admin@kubernetes # 当前上下文用户kind: Configpreferences: {}users:- name: def-ns-adminuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
这样,就把当前 上下文的用户配置成功
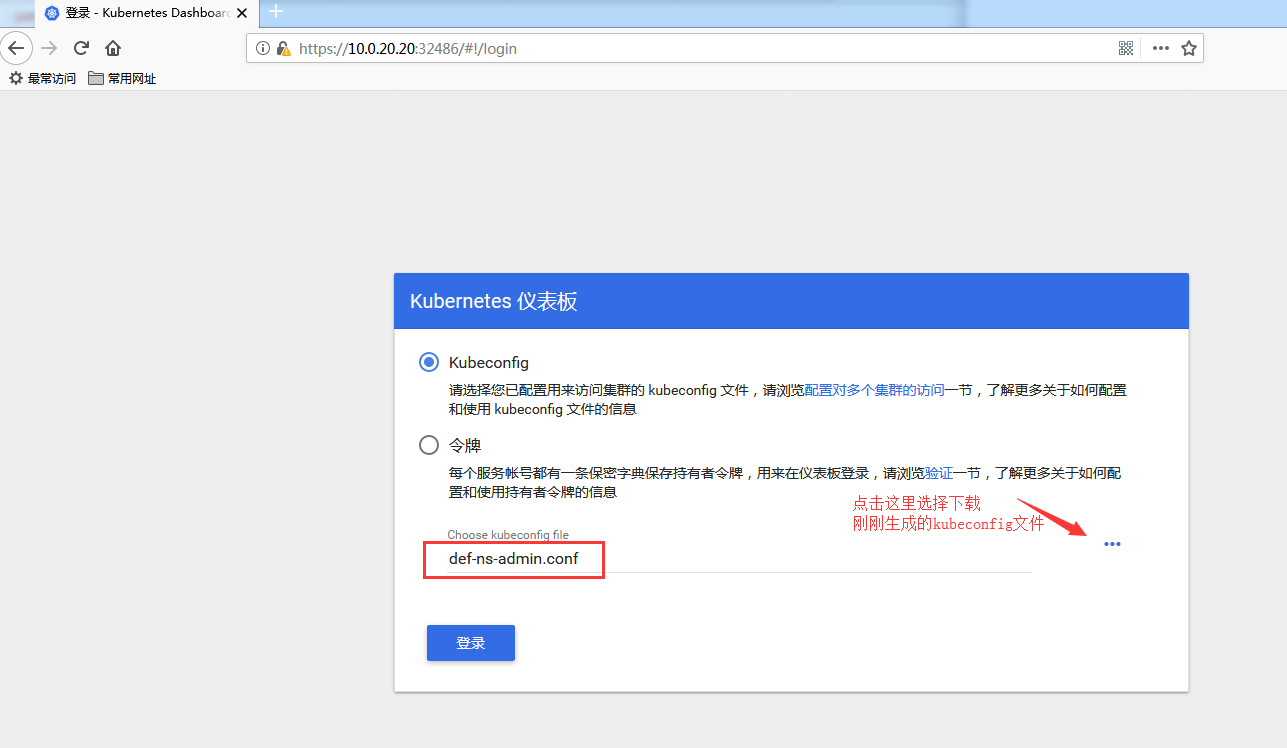
测试使用kubeconfig文件登陆
下载刚刚生成好的 def-ns-admin.conf
然后测试登陆:

基于 tls 验证
创建 dashboard 专用的 tls 证书
进入到 kubernetes 集群的 master 节点中的 /etc/kubernetes/pki/ 目录
这个目录是专门存放 kubernetes 集群证书的目录
生成dashboard 用户的私钥
[root@master ~]# cd /etc/kubernetes/pki/[root@master pki]# (umask 077; openssl genrsa -out dashboard.key 2048)Generating RSA private key, 2048 bit long modulus........................+++.........................................................+++e is 65537 (0x10001)[root@master pki]# ll dashboard.key-rw------- 1 root root 1679 Aug 22 17:51 dashboard.key
生成证书签署请求
[root@master pki]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=tracy/CN=dashboard"[root@master pki]# ll dashboard.csr-rw-r--r-- 1 root root 911 Aug 22 17:54 dashboard.csr
给dashboard证书签证
这里需要注意,一定要kubernetes集群中的 ca.crt 和 ca.key 来签署,这样才能在此集群中使用。
[root@master pki]# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 365Signature oksubject=/O=tracy/CN=dashboardGetting CA Private Key
这样就签署完成了
创建 dashboard 对应的 secret
[root@master pki]# kubectl create secret generic dashboard-cert -n kube-system --from-file=dashboard.crt --from-file=dashboard.keysecret/dashboard-cert created[root@master pki]# kubectl get secret -n kube-system dashboard-certNAME TYPE DATA AGEdashboard-cert Opaque 2 16s[root@master pki]# kubectl describe secret -n kube-system dashboard-certName: dashboard-certNamespace: kube-systemLabels: <none>Annotations: <none>Type: OpaqueData====dashboard.crt: 1001 bytesdashboard.key: 1679 bytes
12-kubernetes Dashboard 认证及分级授权的更多相关文章
- kubernetes学习笔记之十一:kubernetes dashboard认证及分级授权
第一章.部署dashboard 作为Kubernetes的Web用户界面,用户可以通过Dashboard在Kubernetes集群中部署容器化的应用,对应用进行问题处理和管理,并对集群本身进行管理.通 ...
- Kubernetes 学习17 dashboard认证及分级授权
一.概述 1.我们前面介绍了kubernetes的两个东西,认证和授权 2.在kubernetes中我们对API server的一次访问大概会包含哪些信息?简单来讲它是restfule风格接口,也就是 ...
- k8s系列--- dashboard认证及分级授权
http://blog.itpub.net/28916011/viewspace-2215214/ 因版本不一样,略有改动 Dashboard官方地址: https://github.com/kube ...
- Kubernetes学习之路(十九)之Kubernetes dashboard认证访问
Dashboard:https://github.com/kubernetes/dashboard 一.Dashboard部署 由于需要用到k8s.gcr.io/kubernetes-dashboar ...
- kubernetes Dashboard 使用RBAC 权限认证控制
kubernetes RBAC实战 环境准备 先用kubeadm安装好kubernetes集群,[包地址在此](https://market.aliyun.com/products/56014009/ ...
- Kubernetes Dashboard 安装与认证
1.安装dashboard $ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/ ...
- kubernetes dashboard 安装
环境:CentOS Linux release 7.3.1611 (Core)IP:192.168.0.103 [1]组件安装yum install device-mapperyum install ...
- (十三)Kubernetes Dashboard
Dashboard概述 Github地址 Dashboard是Kubernetes的Web GUI,可用于在Kubernetes集群上部署容器化应用.应用排障.管理集群本身及附加的资源等.常用于集群及 ...
- k8s之dashboard认证、资源需求、资源限制及HeapSter
1.部署dashboard kubernetes-dashboard运行时需要有sa账号提供权限 Dashboard官方地址:https://github.com/kubernetes/dashboa ...
随机推荐
- javadoc的使用
在进行项目开发过程中,项目接口文档是很重要的一块内容,在java项目中我们可以用swagger,asciidoc,javadoc等方式来生产文档,而其中最基本的文档生成方式就是javadoc,它一般用 ...
- 盘点一下Creator星球上的开源工具包!
晓衡开始写公众号,最早是从上架 Cocos 商店的 pbkiller 插件开始的,到至今有2年2个月了.在这期间,又陆续在公众号上分享了多个实用工具包,在这里统一盘点一下,方便与大家交流学习. 一.u ...
- Spring Boot2 系列教程(二十)Spring Boot 整合JdbcTemplate 多数据源
多数据源配置也算是一个常见的开发需求,Spring 和 SpringBoot 中,对此都有相应的解决方案,不过一般来说,如果有多数据源的需求,我还是建议首选分布式数据库中间件 MyCat 去解决相关问 ...
- 监控tomcat,自动启动
tomcatID=`ps -ef |grep tomcat |grep -v 'grep'|awk '{print $2}'` tomcatCount=`ps -ef|grep tomcat |gr ...
- Java Stream函数式编程第三篇:管道流结果处理
一.Java Stream管道数据处理操作 在本号之前写过的文章中,曾经给大家介绍过 Java Stream管道流是用于简化集合类元素处理的java API.在使用的过程中分为三个阶段.在开始本文之前 ...
- p4141(消失之物)
题目描述 ftiasch 有 N 个物品, 体积分别是 W1, W2, …, WN. 由于她的疏忽, 第 i 个物品丢失了. “要使用剩下的 N – 1 物品装满容积为 x 的背包,有几种方法呢?” ...
- Python实现获取IP代码
代码如下: # -*- coding: utf-8 -*- #!/usr/bin/env python # @Time : 2018/5/30 11:05 # @Desc : 获取ip # @File ...
- 域名解析 | A记录 ,CNAME,MX,NS 你懂了吗
域名解析 | A记录 ,CNAME,MX,NS 你懂了吗 域名解析 什么是域名解析?域名解析就是国际域名或者国内域名以及中文域名等域名申请后做的到IP地址的转换过程.IP地址是网路上标识您站点的数字地 ...
- 基于docker搭建Jenkins+Gitlab+Harbor+Rancher架构实现CI/CD操作(续)
说明:前期的安装,请转向https://www.cnblogs.com/lq-93/p/11824039.html (4).查看gitlab镜像是否启动成功 docker inspect 容器id ...
- 护网杯web
首先进入网页后,观察到有sign up 点击sign up 进行注册 再点击sign in 进行登录 进入一个买辣条的界面,可以知道,5元可以买一包大辣条,多包大辣条可以换一包辣条之王,多包辣条之王可 ...
