jks & pfk
keytool and jks
keytool
Name
keytool - Key and Certificate Management Tool
Manages a keystore (database) of cryptographic keys, X.509 certificate chains, and trusted certificates.DESCRIPTION
keytool is a key and certificate management utility. It allows users to administer their own public/private key pairs and associated certificates for use in self-authentication (where the user authenticates himself/herself to other users/services) or data integrity and authentication services, using digital signatures. It also allows users to cache the public keys (in the form of certificates) of their communicating peers.
A certificate is a digitally signed statement from one entity (person, company, etc.), saying that the public key (and some other information) of some other entity has a particular value.(See Certificates.) When data is digitally signed, the signature can be verified to check the data integrity and authenticity. Integrity means that the data has not been modified or tampered with, and authenticity means the data indeed comes from whoever claims to have created and signed it.
keytool also enables users to administer secret keys used in symmetric encryption/decryption (e.g. DES).
keytool stores the keys and certificates in a keystore.
Commands
Key and Certificate Management Tool
Commands:
-certreq Generates a certificate request
-changealias Changes an entry's alias
-delete Deletes an entry
-exportcert Exports certificate
-genkeypair Generates a key pair
-genseckey Generates a secret key
-gencert Generates certificate from a certificate request
-importcert Imports a certificate or a certificate chain
-importkeystore Imports one or all entries from another keystore
-keypasswd Changes the key password of an entry
-list Lists entries in a keystore
-printcert Prints the content of a certificate
-printcertreq Prints the content of a certificate request
-printcrl Prints the content of a CRL file
-storepasswd Changes the store password of a keystore
1. 创建keystore文件
-genkey
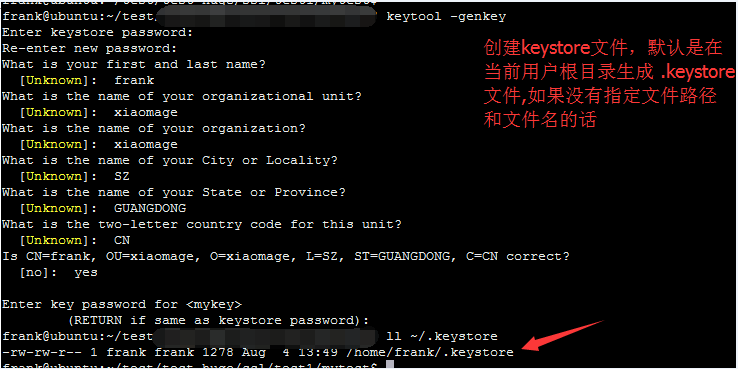
-genkeypair
keytool -genkeypair [OPTION]...
Generates a key pair
Options:
-alias <alias> alias name of the entry to process
-keyalg <keyalg> key algorithm name
-keysize <keysize> key bit size
-sigalg <sigalg> signature algorithm name
-destalias <destalias> destination alias
-dname <dname> distinguished name
-startdate <startdate> certificate validity start date/time
-ext <value> X.509 extension
-validity <valDays> validity number of days
-keypass <arg> key password
-keystore <keystore> keystore name
-storepass <arg> keystore password
-storetype <storetype> keystore type
-providername <providername> provider name
-providerclass <providerclass> provider class name
-providerarg <arg> provider argument
-providerpath <pathlist> provider classpath
-v verbose output
-protected password through protected mechanism
keytool -genkeypair -alias xmg -keyalg RSA -keysize 2048 -validity 365 -keypass 123456 -storepass 123456 -keystore xmg.jks -dname "CN=frank, OU=xiaomage, O=xiaomage, L=SZ, ST=GUANGDONG, C=CN"
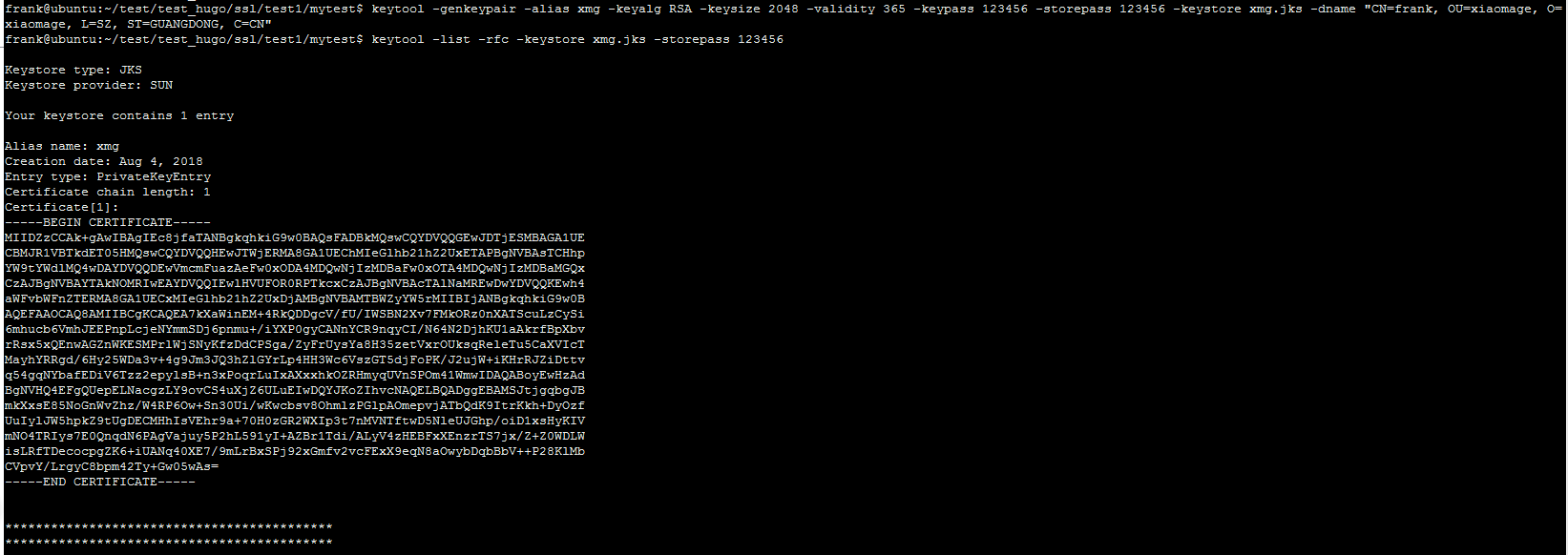
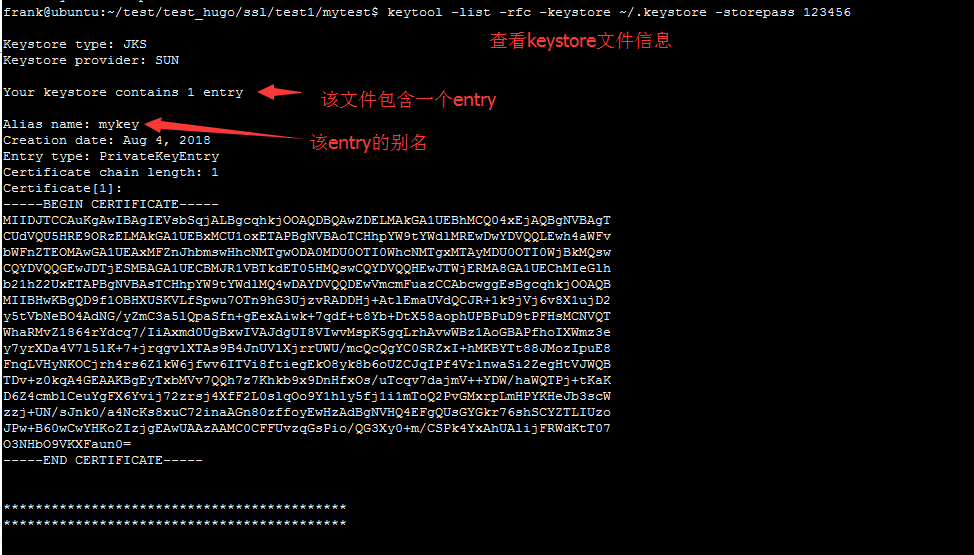
2. 查看keystore文件的信息
keytool -list -rfc -keystore xmg.jks -storepass 123456
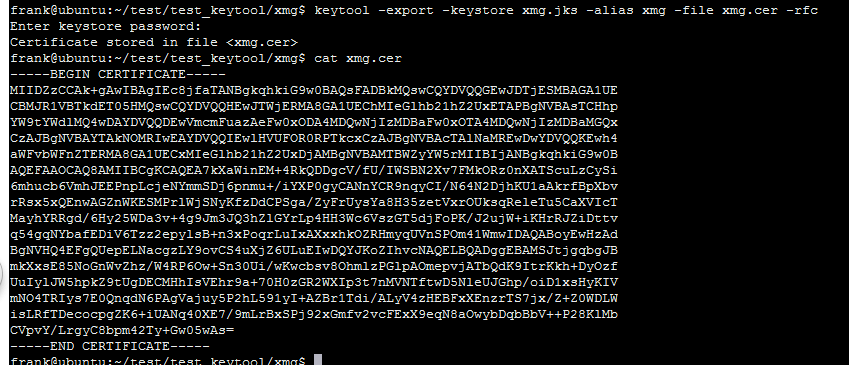
3. 从keystore文件中导出certificate
keytool -exportcert [OPTION]...
Exports certificate
Options:
-rfc output in RFC style
-alias <alias> alias name of the entry to process
-file <filename> output file name
-keystore <keystore> keystore name
-storepass <arg> keystore password
-storetype <storetype> keystore type
-providername <providername> provider name
-providerclass <providerclass> provider class name
-providerarg <arg> provider argument
-providerpath <pathlist> provider classpath
-v verbose output
-protected password through protected mechanism
keytool -exportcert -keystore xmg.jks -alias xmg -file xmg.cer -rfc
-rfc 会将certificate的内容以可读的形式保存在 xmg.cer文件中,否则,cat xmg.cer将是一堆ASCII码.
一般 -keystore 和 -alias 要一起使用,如果在创建keystore文件时指定了alias.
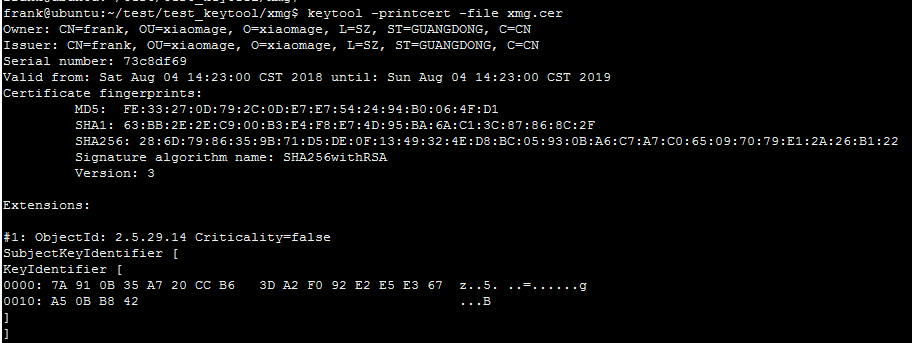
4. 查看certificate的信息
keytool -printcert [OPTION]...
Prints the content of a certificate
Options:
-rfc output in RFC style
-file <filename> input file name
-sslserver <server[:port]> SSL server host and port
-jarfile <filename> signed jar file
-v verbose output
keytool -printcert -file xmg.cer
5. 将jks 转为 pfx格式
keytool -importkeystore [OPTION]...
Imports one or all entries from another keystore
Options:
-srckeystore <srckeystore> source keystore name
-destkeystore <destkeystore> destination keystore name
-srcstoretype <srcstoretype> source keystore type
-deststoretype <deststoretype> destination keystore type
-srcstorepass <arg> source keystore password
-deststorepass <arg> destination keystore password
-srcprotected source keystore password protected
-srcprovidername <srcprovidername> source keystore provider name
-destprovidername <destprovidername> destination keystore provider name
-srcalias <srcalias> source alias
-destalias <destalias> destination alias
-srckeypass <arg> source key password
-destkeypass <arg> destination key password
-noprompt do not prompt
-providerclass <providerclass> provider class name
-providerarg <arg> provider argument
-providerpath <pathlist> provider classpath
-v verbose output
keytool -alias xmg -importkeystore -srckeystore xmg.jks -srcstoretype jks -srcstorepass 123456 -destkeystore xmg.pfx -deststoretype pkcs12 -deststorepass 654321 -destkeypass 654321
.PFX或.P12文件: 这样的证书文件是二进制格式,同时包含证书和密钥,且一般有密码保护。
6. 将pfx格式 转为 pem格式
PEM文件: 这样的文件一般是文本格式,可以存放证书或密钥,或者两者都包含。 PEM 文件如果只包含密钥,一般用KEY文件代替。
从pem文件从分别提取 证书,PKCS#1 私钥,PKCS#8 私钥/公钥
#输出证书和密钥信息
openssl pkcs12 -in xmg.pfx -out xmg1.pem -nodes
#仅输出证书信息
openssl pkcs12 -in xmg.pfx -out xmg1.cer -nokeys
#仅输出密钥信息
openssl pkcs12 -in xmg.pfx -out xmg1.key -nocerts
#提取公钥
#本指令输出的公钥是PKCS#8 格式
#-----BEGIN PUBLIC KEY-----
#-----END PUBLIC KEY-----
openssl rsa -in xmg1.key -pubout -out pub.key
#提取私钥
#本指令输出的私钥是PKCS#1 格式
#-----BEGIN RSA PRIVATE KEY-----
#-----END RSA PRIVATE KEY-----
openssl rsa -in xmg1.key -out pri.key
#PKCS#1私钥 转换为 PKCS#8私钥
#-----BEGIN PRIVATE KEY-----
#-----END PRIVATE KEY-----
openssl pkcs8 -topk8 -in pri.key -out pri_8.key
Usage: pkcs12 [options]
where options are
-export output PKCS12 file
-chain add certificate chain
-inkey file private key if not infile
-certfile f add all certs in f
-CApath arg - PEM format directory of CA's
-CAfile arg - PEM format file of CA's
-name "name" use name as friendly name
-caname "nm" use nm as CA friendly name (can be used more than once).
-in infile input filename
-out outfile output filename
-noout don't output anything, just verify. -仅作为验证
-nomacver don't verify MAC.
-nocerts don't output certificates. -不输出证书信息
-clcerts only output client certificates. -仅输出客户端证书,尚不清楚client certificates是什么
-cacerts only output CA certificates.
-nokeys don't output private keys. -不输出密钥
-info give info about PKCS#12 structure.
-des encrypt private keys with DES
-des3 encrypt private keys with triple DES (default)
-seed encrypt private keys with seed
-aes128, -aes192, -aes256
encrypt PEM output with cbc aes
-camellia128, -camellia192, -camellia256
encrypt PEM output with cbc camellia
-nodes don't encrypt private keys -不对私钥进行加密,如果不指定,则会提示输入 私钥加密password
-noiter don't use encryption iteration
-nomaciter don't use MAC iteration
-maciter use MAC iteration
-nomac don't generate MAC
-twopass separate MAC, encryption passwords
-descert encrypt PKCS#12 certificates with triple DES (default RC2-40)
-certpbe alg specify certificate PBE algorithm (default RC2-40)
-keypbe alg specify private key PBE algorithm (default 3DES)
-macalg alg digest algorithm used in MAC (default SHA1)
-keyex set MS key exchange type
-keysig set MS key signature type
-password p set import/export password source
-passin p input file pass phrase source
-passout p output file pass phrase source
-engine e use engine e, possibly a hardware device.
-rand file:file:...
load the file (or the files in the directory) into
the random number generator
-CSP name Microsoft CSP name
-LMK Add local machine keyset attribute to private key
rsa [options] <infile >outfile
where options are
-inform arg input format - one of DER NET PEM //输入文件格式,默认pem格式
-outform arg output format - one of DER NET PEM //输出文件格式,默认pem格式
-in arg input file //输入文件
-sgckey Use IIS SGC key format //指定SGC编码格式,兼容老版本,不应再使用
-passin arg input file pass phrase source //指定输入文件的加密口令,可来自文件、终端、环境变量等
-out arg output file //输出文件
-passout arg output file pass phrase source //指定输出文件的加密口令,可来自文件、终端、环境变量等
-des encrypt PEM output with cbc des //使用des加密输出的文件
-des3 encrypt PEM output with ede cbc des using 168 bit key //使用des3加密输出的文件
-seed encrypt PEM output with cbc seed //使用seed加密输出的文件
-aes128, -aes192, -aes256 //使用aes加密输出的文件
encrypt PEM output with cbc aes
-camellia128, -camellia192, -camellia256 //使用camellia加密输出的文件
encrypt PEM output with cbc camellia
-text print the key in text //以明文形式输出各个参数值
-noout don't print key out //不输出密钥到任何文件
-modulus print the RSA key modulus //输出模数值
-check verify key consistency //检查输入密钥的正确性和一致性
-pubin expect a public key in input file //指定输入文件是公钥
-pubout output a public key //指定输出文件是公钥
-engine e use engine e, possibly a hardware device. //指定三方加密库或者硬件
Usage pkcs8 [options]
where options are
-in file input file
-inform X input format (DER or PEM)
-passin arg input file pass phrase source
-outform X output format (DER or PEM)
-out file output file
-passout arg output file pass phrase source
-topk8 output PKCS8 file -指定输出文件的格式为PKCS#8
-nooct use (nonstandard) no octet format
-embed use (nonstandard) embedded DSA parameters format
-nsdb use (nonstandard) DSA Netscape DB format
-noiter use 1 as iteration count
-nocrypt use or expect unencrypted private key -不对私钥加password
-v2 alg use PKCS#5 v2.0 and cipher "alg"
-v1 obj use PKCS#5 v1.5 and cipher "alg"
-engine e use engine e, possibly a hardware device.
DER&CER&CRT&PEM&PFX&P12什么含义
*.DER或*.CER文件: 这样的文件是二进制格式,一般只含有证书信息,不包含私钥。
*.CRT文件: 这样的文件可以是二进制格式,也可以是文本格式,一般均为文本格式,功能与 *.DER及*.CER文件相同。
*.PEM文件: 这样的文件一般是文本格式,可以存放证书或私钥,或者两者都包含。 *.PEM 文件如果只包含私钥,一般用*.KEY文件代替。
*.PFX或*.P12文件: 这样的文件一般是二进制格式,同时包含证书和私钥,且一般有密码保护。jks & pfk的更多相关文章
- JKS和PKCS#12
今天来点实际工作中的硬通货! 与计费系统打交道,少不了用到加密/解密实现.为了安全起见,通过非对称加密交换对称加密密钥更是不可或缺.那么需要通过什么载体传递非对称算法公钥/私钥信息?数字证书是公钥的载 ...
- p12(PKCS12)和jks互相转换
p12 -> jks keytool -importkeystore -srckeystore keystore.p12 -srcstoretype PKCS12 -deststoretype ...
- 使用keytool生产jks证书
使用JDK中的keytool生成服务器证书 1.创建服务器KeyStorekeytool -genkey -alias server_jks_cennavi -keyalg RSA -keystor ...
- JKS TO PEM
tomcat 的ssl 会使用到jks,而haproxy的ssl(非tcp代理方式)会使用到pem 如果从tomcat的ssl需要迁移到haproxy的ssl,就需要从jks中读取相关信息生成pem文 ...
- ssl证书生成:cer&jks文件生成摘录
一.生成.jks文件 1.keystore的生成: 分阶段生成: keytool -genkey -alias yushan(别名) -keypass yushan(别名密码) -keyalg ...
- OpenSSL 1.0.0生成p12、jks、crt等格式证书的命令个过程(转)
OpenSSL 1.0.0生成p12.jks.crt等格式证书的命令个过程 此生成的证书可用于浏览器.java.tomcat.c++等.在此备忘! 1.创建根证私钥命令:openssl g ...
- Converting a .jks Key Store to a .pem Key Store
In order to convert a Java key store into a Privacy Enhanced Mail Certificate, you will need to use ...
- 如何让OpenSSL得到JKS格式的keystore中的public and private key
国内私募机构九鼎控股打造APP,来就送 20元现金领取地址:http://jdb.jiudingcapital.com/phone.html内部邀请码:C8E245J (不写邀请码,没有现金送)国内私 ...
- 密钥,密钥对,公钥,pfx,jks和https的几个概念
密钥: 我理解是公钥+私钥的统称. 密钥对: 公钥(证书)和私钥成对存在. 通信双方各持有自己的私钥和对方的公钥.自己的私钥需密切保护,而公钥是公开给对方的.在windows下,单独存在的公钥一般是后 ...
随机推荐
- Unity3d-Socket之龙一编年史network.dll分析(1)
今天闲着无聊,看到群里的老大共享了反编译的工具,就下载下来玩下. 说道反编译我个人不太推崇反编译,感觉不道德,毕竟是人家的代码,但是又回想一下,我们拿代码看是抱着学习的态度又有何不可,所谓既是民族的也 ...
- [Todo]Redis & Mysql可以看的书籍
Redis实战(我下的版本是网络版,还有一版是黄健宏翻译的版本,正在找) 高性能Mysql第三版 都在目录: /Users/baidu/Documents/Data/Interview/存储-Nosq ...
- MVC工作原理
MVC(Model-View-Controller,模型—视图—控制器模式)用于表示一种软件架构模式.它把软件系统分为三个基本部分:模型(Model),视图(View)和控制器(Controller) ...
- shorthand trick with boolean expressions
https://stackoverflow.com/questions/2802055/what-does-the-construct-x-x-y-mean --------------------- ...
- centos6.8服务器配置之编译安装PHP、配置nginx
php version 5.6.31.nginx version: nginx/1.10.2 1.下载: wget http://cn2.php.net/distributions/php-5.6.3 ...
- 转: git的图文使用教程(巨详细)
转自: http://blog.jobbole.com/78960/ Git使用教程 一:Git是什么? Git是目前世界上最先进的分布式版本控制系统. 二:SVN与Git的最主要的区别? SVN是集 ...
- JS 数字左补零函数
/* 左边自动补零 质朴长存法 by lifesinger */ function pad(num, n) { var len = num.toString().length; while(len & ...
- Android 使用 Gradle 多渠道打包
安卓开发完毕.对于一个开放应用而言,我们须要公布到不同的应用市场,同一时候我们也须要统计不同市场的用户下载量. (通过启动应用后获取不同市场apk中的不同值来区分) 以下用一个详细的实例来说明: 1. ...
- BEGINNING SHAREPOINT® 2013 DEVELOPMENT 第9章节--client对象模型和REST APIs概览 Windows Phone
BEGINNING SHAREPOINT® 2013 DEVELOPMENT 第9章节--client对象模型和REST APIs概览 Windows Phone 和.NET托管代码和 ...
- Intent传递对象的方法
//传递对象 Bundle bundle = new Bundle(); intent = new Intent(getApplicationContext(), YourActivity.class ...
