Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION
WHAT IS SQL?
- Most websites use a database to store data.
- Most data stored in it(usernames, passwords ..etc.)
- Web application reads, updates and inserts data in the database.
- Interaction with DB done using SQL.
WHY ARE THEY SO DANGEROUS
1. They are everywhere.
2. Give access to the database –> sensitive data.
3. Can be used to read local files outside www root.
4. Can be used to log in as admin and further exploit the system.
5. Can be used to upload files.
DISCOVERING SQLi in POST
- Try to break the page.
- Using ‘and’, ‘order by’ or “’”.
- Testing text boxes and URL parameters on the form.
http://target.com/page.php?something=something
Pre-Configure about Metasplitable2:

Following is a very useful error message.
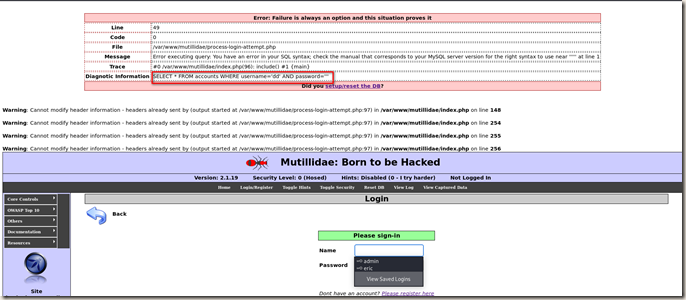
So let’s modify the input on password box. We can login with a wrong password now.
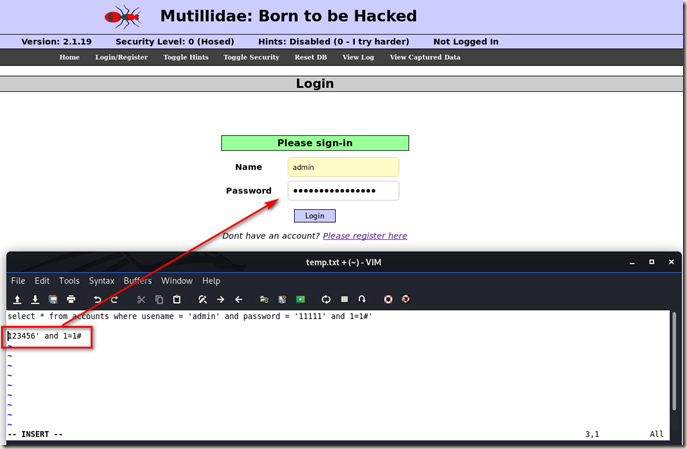
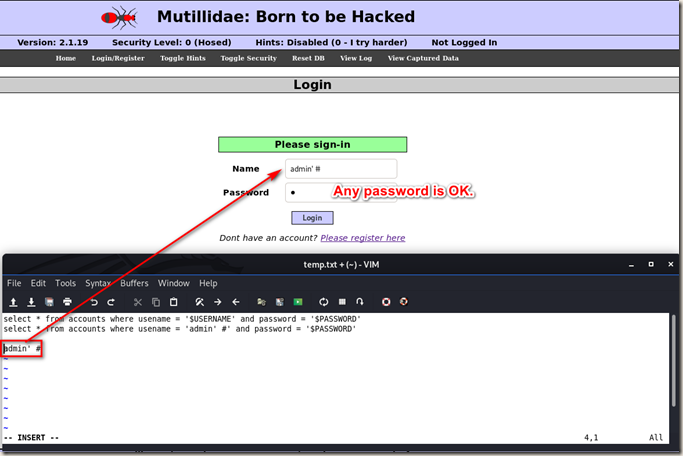
Bypassing Authentication.
Ethical Hacking - Web Penetration Testing(8)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- LNMP 环境更换Nginx 服务器为Tengine
本人之前所使用 LNMP 环境一直是原生的Nginx服务器,最近几天看了好多大网站使用 淘宝团队基于Nginx开发的 Tengine 决定给自己的虚拟机也装个玩玩. 关于Tengine的介绍就不多说了 ...
- c++ UDP套接字客服端代码示范
c++ UDP套接字客服端代码示范 #include<winsock2.h> //包含头文件 #include<stdio.h> #include<windows.h&g ...
- 08.DRF-反序列化
三.反序列化使用 3.1 验证 使用序列化器进行反序列化时,需要对数据进行验证后,才能获取验证成功的数据或保存成模型类对象. 在获取反序列化的数据前,必须调用is_valid()方法进行验证,验证成功 ...
- 打个总结:Web性能优化
前段时间优化一个公司历史老项目的Web性能,却引出了一系列的问题,让我反思良多. 我通过Chrome的Lighthouse工具可以看出一些性能参数和问题反馈,我逐一对其进行优化. 根据资源请求的不同, ...
- 007.OpenShift管理应用部署
一 REPLICATION CONTROLLERS 1.1 RC概述 RC确保pod指定数量的副本一直运行.如果pod被杀死或被管理员显式删除,复制控制器将自动部署相应的pod.类似地,如果运行的po ...
- Redis Wendows安装步骤
1.打开cmd命令提示符2.打开cmd如下图,输入Redis下载磁盘名称+“:” ,然后回车 3.如下图:输入"cd" 然后空格,后面是Redis的路径 回车 4.设置服务命令 ...
- 寻找hive数据倾斜路
前言 一直以来我都是从书上.博客上.别人口中听说数据倾斜,自己也从而指导一些解决数据倾斜的方式或者一些容易出现数据倾斜的场景.但是从来没有认真的去发现过,寻求过,研究过. 正文 我打开了hive官网 ...
- Plugns
Lombok Translation Rainbow Brackets
- Python 简明教程 --- 4,Python 变量与基本数据类型
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 任何一个人都会写出能够让机器理解的代码,只有好的程序员才能写出人类可以理解的代码. -- Marti ...
- .net core 使用Tu Share获取股票交易数据
一.什么是Tu Share Tushare是一个免费.开源的python财经数据接口包.主要实现对股票等金融数据从数据采集.清洗加工 到 数据存储的过程,用户可以免费(部分数据的下载有积分限制)的通 ...
