Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS
XSS - CROSS SITE SCRIPTING VULNS
- Allow an attacker to inject javascript code into the page.
- The code is executed when the page loads.
- The code is executed on the client machine, not the server.
Three main types:
1. Persistent/Stored XSS.
2. Reflected XSS.
3.DOM-based XSS
DISCOVERING XSS
- Try to inject javascript code into the pages.
- Test text boxes and URL parameters on the form
- http://target.com/page.php?something=something
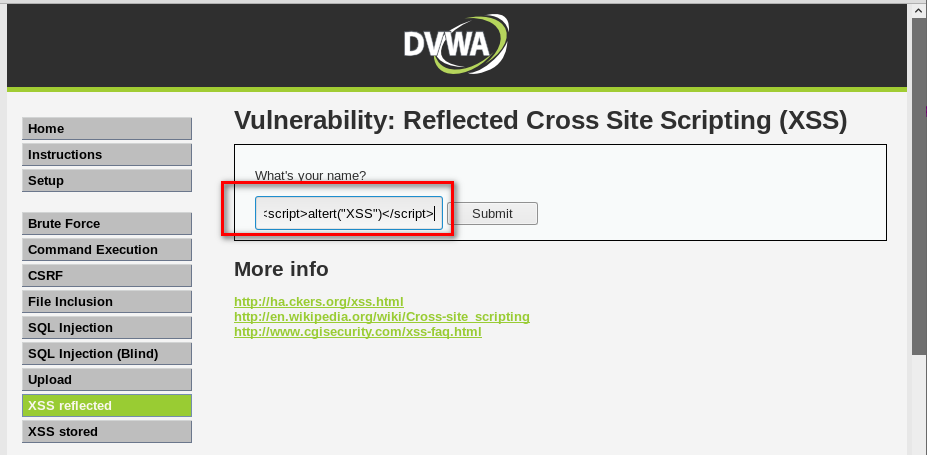
REFLECTED XSS
- None persistent, not stored.
- Only work if the target visits a specially crafted URL
- http://target.com/page.php?something=<script>altert("XSS")</script>
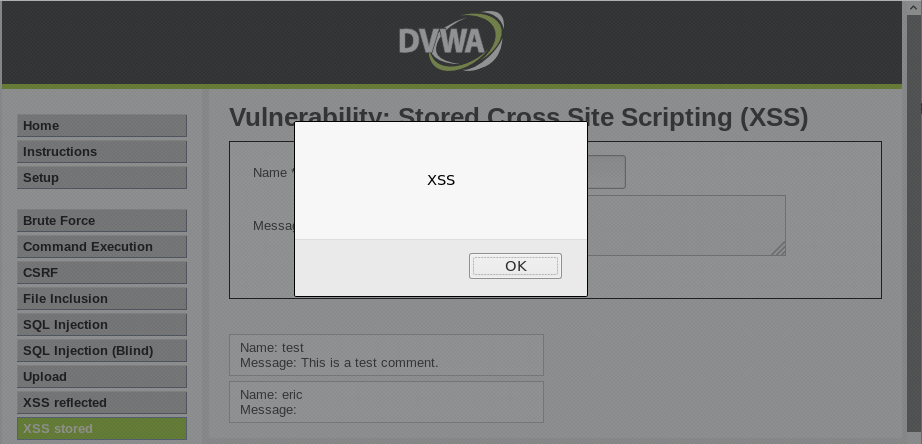
STORED XSS
- Persistent, stored on the page or DB.
- The injected code is executed every time the page is loaded.
Python Ethical Hacking - VULNERABILITY SCANNER(5)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- cb35a_c++_STL_算法_for_each
cb35a_c++_STL_算法_for_each for_each(b,e,p)使用for_each()算法遍历数据使用for_each()和函数对象修改数据使用for_each()的返回值 //转 ...
- cb07a_c++_迭代器和迭代器的范围
cb07a_c++_迭代器和迭代器的范围c++primer第4版https://www.cnblogs.com/txwtech/p/12309989.html--每一种容器都有自己的迭代器--所有的迭 ...
- linux环境下安装git(采用github下载git源码编译)
[目的]:linux环境下 安装配置git成功 [准备条件]linux系统,git包 1.先行下载git包 -- 从github上https://github.com/git/git/releases ...
- RocksDB事务的隔离性分析【原创】
Rocksdb事务隔离性指的是多线程并发事务使用时候,事务与事务之间的隔离性,通过加锁机制来实现,本文重点剖析Read Commited隔离级别下,Rocksdb的加锁机制. Rocksdb事务相关类 ...
- Kafka源码解析(二)---Log分析
上一篇文章讲了LogSegment和Log的初始化,这篇来讲讲Log的主要操作有哪些. 一般来说Log 的常见操作分为 4 大部分. 高水位管理操作 日志段管理 关键位移值管理 读写操作 其中关键位移 ...
- MQ消息队列(1)—— 概念和使用场景
一.什么是消息队列 消息即是信息的载体.为了让消息发送者和消息接收者都能够明白消息所承载的信息(消息发送者需要知道如何构造消息:消息接收者需要知道如何解析消息),它们就需要按照一种统一的格式描述消息 ...
- loadRunnner中90%的响应时间
参考博客https://blog.csdn.net/lengyue_112/article/details/1095320?utm_source=blogxgwz4 LR在场景执行完了会出个报告,其中 ...
- 在 Spring Boot 中使用 HikariCP 连接池
上次帮小王解决了如何在 Spring Boot 中使用 JDBC 连接 MySQL 后,我就一直在等,等他问我第三个问题,比如说如何在 Spring Boot 中使用 HikariCP 连接池.但我等 ...
- Java BigDecimal和double BigDecimal类
BigDecimal类 对于不需要任何准确计算精度的数字可以直接使用float或double,但是如果需要精确计算的结果,则必须使用BigDecimal类,而且使用BigDecimal类也可以进行大数 ...
- 如何在linux下安装tomcat服务器
linux作为现在比较主流的服务器操作系统,使用的机器广泛,安全稳定.tomcat作为应用容器当然可以有linux版本的tomcat.在linux上安装tomcat的方式也很简单,只需要运行脚本基本配 ...
