Ethical Hacking - Web Penetration Testing(2)
INFORMATION GATHERING
- IP address.
- Domain name Info.
- Technologies used.
- Other websites on the same server.
- DNS records.
- Unlisted files, sub-domains, directories.
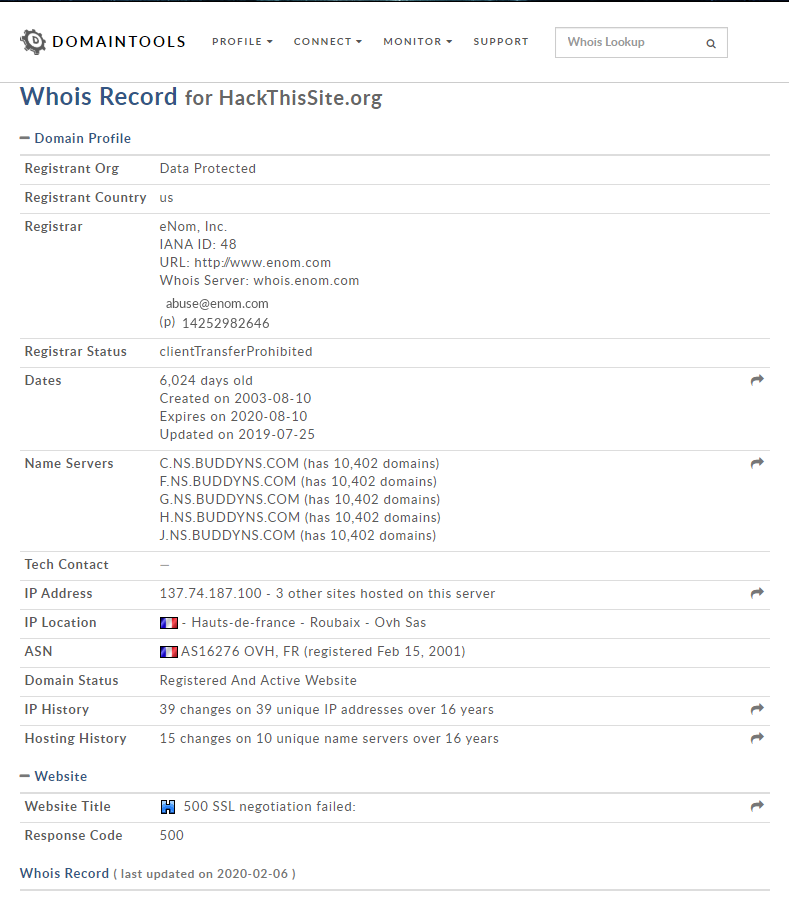
1. Whois Lookup - Find info about the owner of the target. ()
-> http://whois.domaintools.com/ https://www.whois.net/ etc.
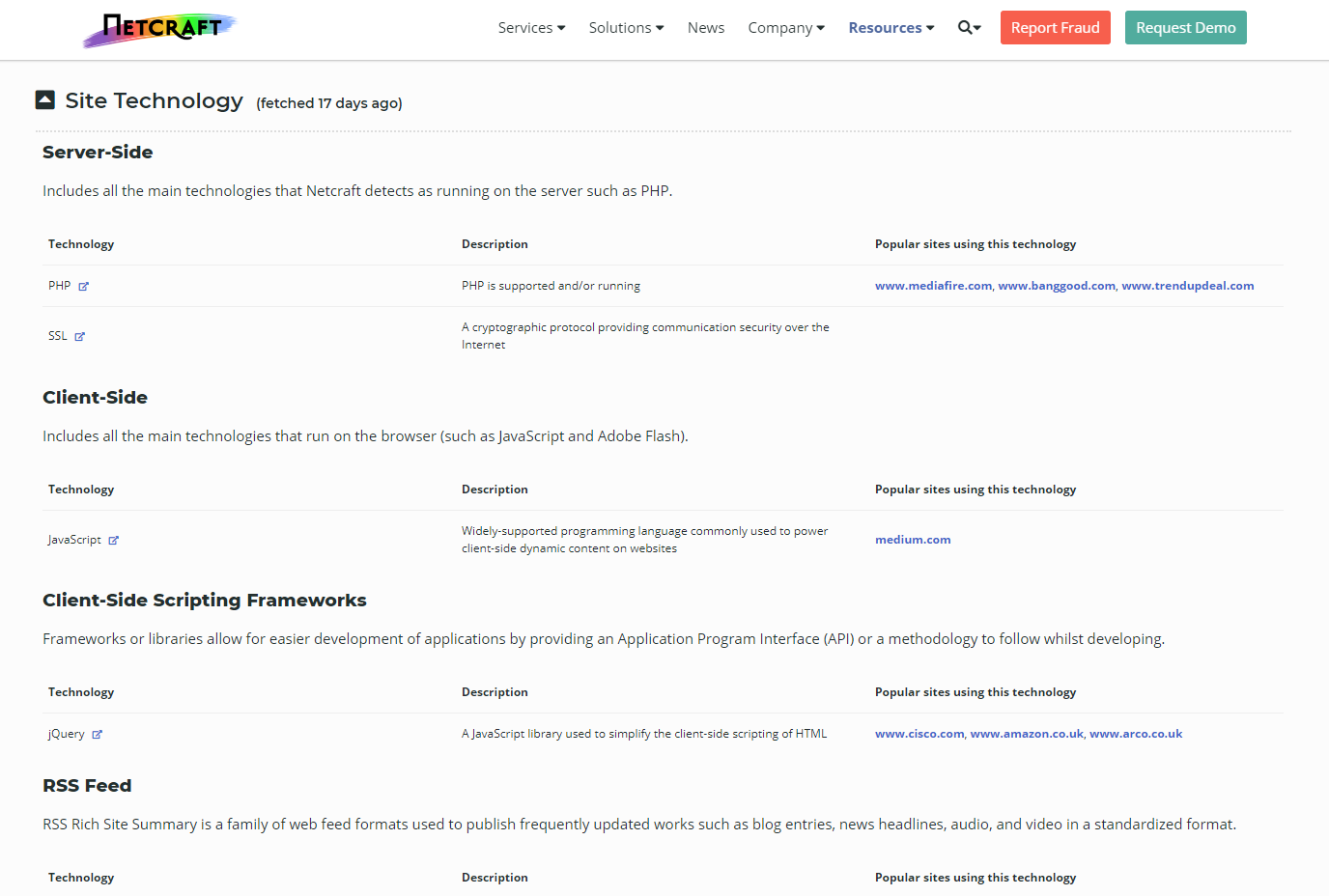
2. Netcraft Site Report - Shows technologies used on the target.
-> http://toolbar.netcraft.com/site_report
Such as :https://sitereport.netcraft.com/?url=https%3A%2F%2Fwww.hackthissite.org%2F
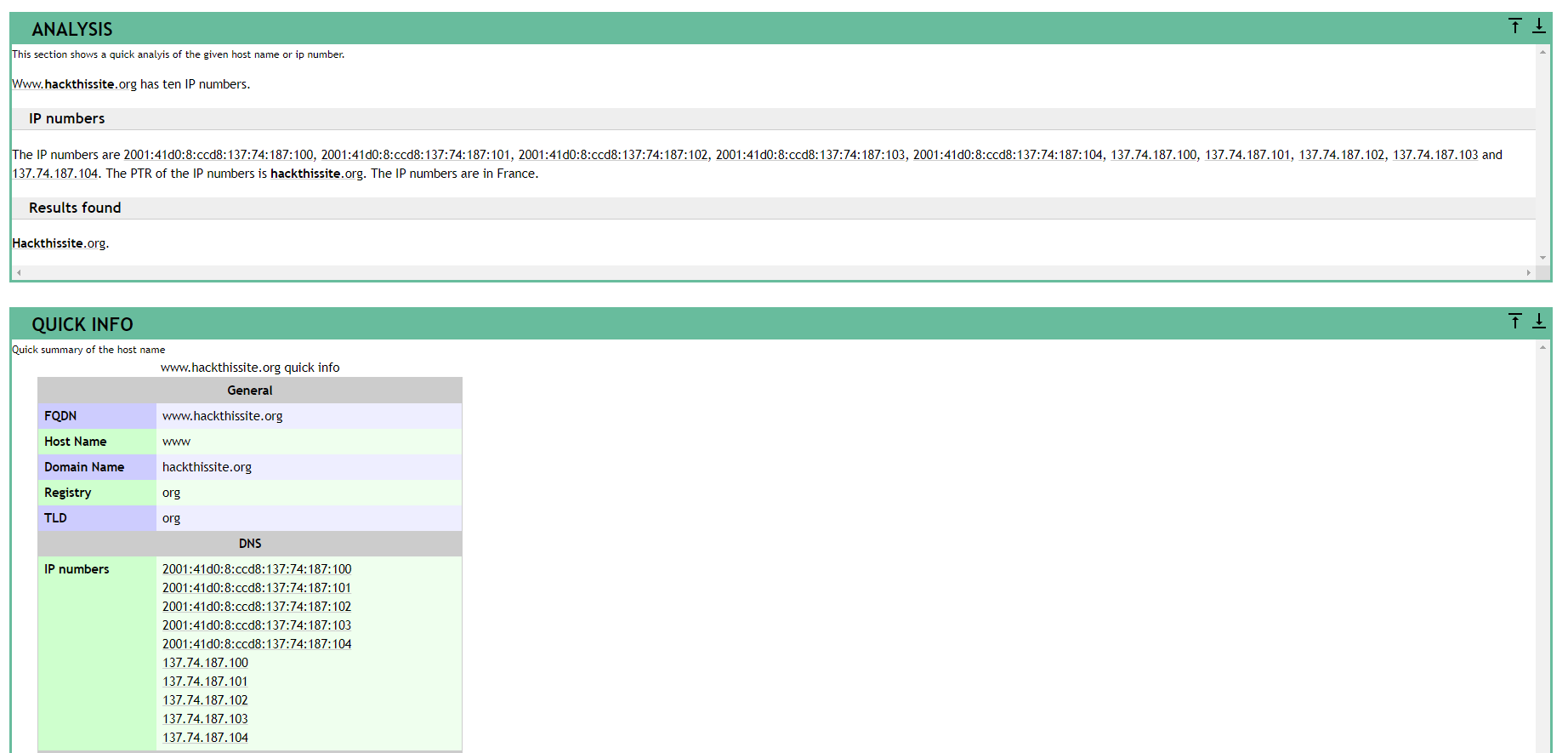
3. Robtex DNS lookup - Shows comprehensive info about the target website.
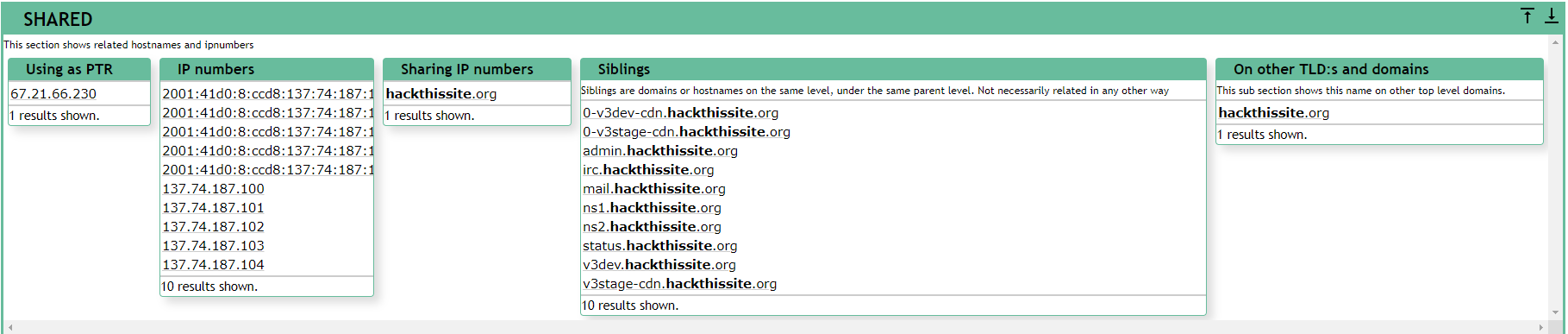
4. Discovering Websites On the Same Server
- One server can serve a number of websites.
- Gaining access to one can help gaining access to others.
To find websites on the same server:
(1) Use Robtex DNS lookup under"names pointing to same IP".
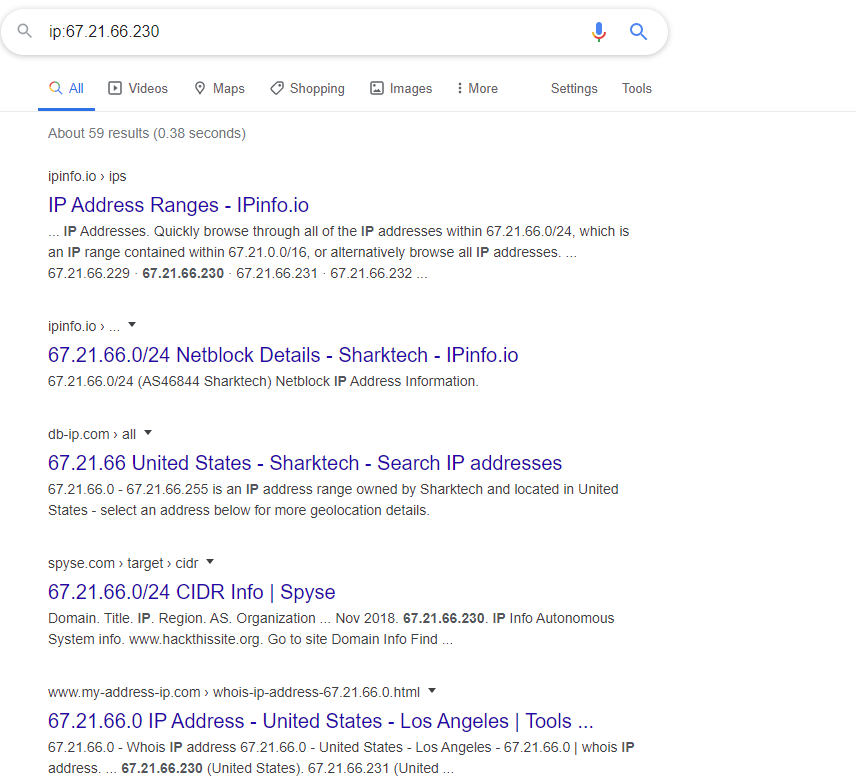
(2) Using bing.com, search for ip:[target ip]
5. Discovering subdomains
- Subdomain.target.com
- Ex:https://www.hackthissite.org/
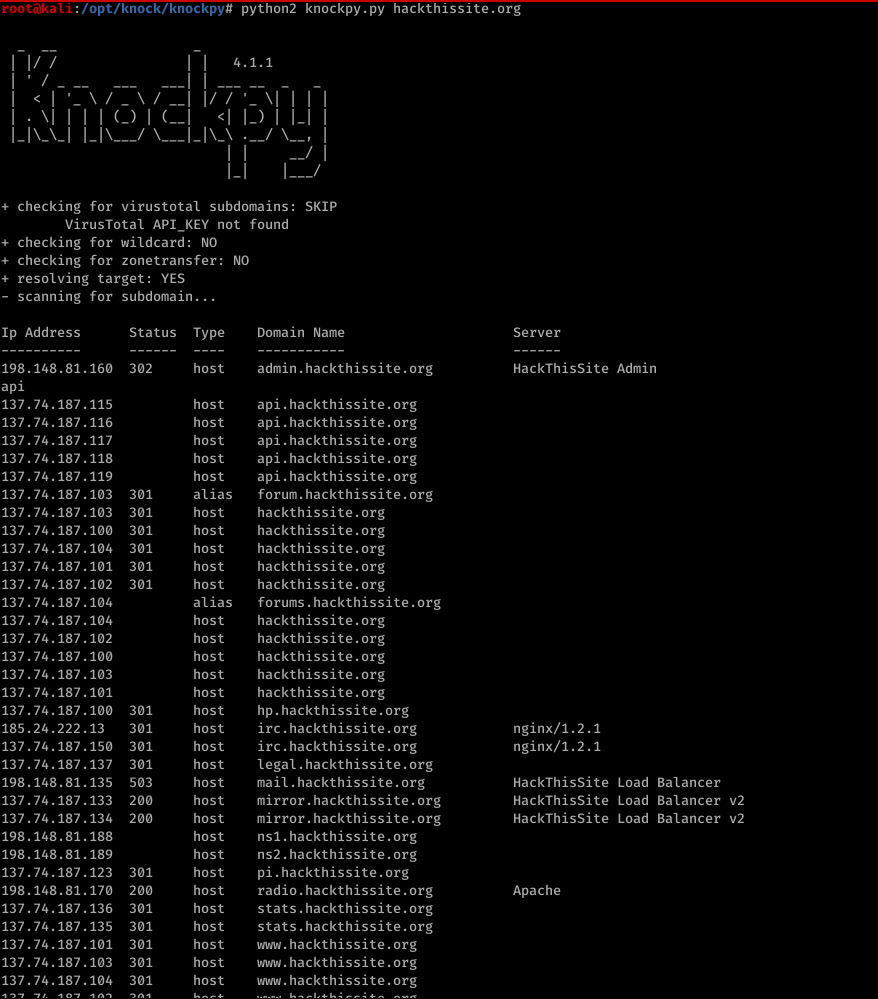
Knock can be used to find subdomainings of target.
(1)Download > git clone https://github.com/guelfoweb/knock.git
(2)Navigate to knock.py >cd knock/knock.py
(3)Run it > python knock.py [target]
6. Discovering Sensitive Files
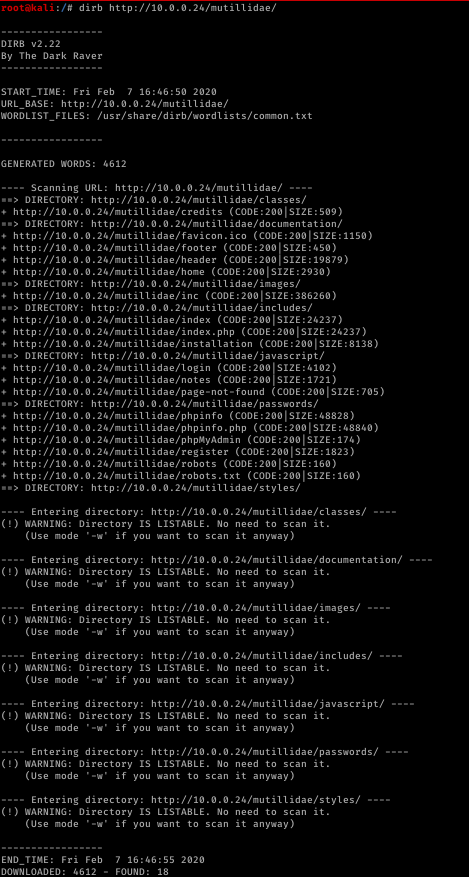
Find files&directories in target website
Tool: drib
dirb [target] [worlist] [options]
For more info run > man dirb
Analysing Discovered Files
---- Scanning URL: http://10.0.0.24/mutillidae/ ----
==> DIRECTORY: http://10.0.0.24/mutillidae/classes/
+ http://10.0.0.24/mutillidae/credits (CODE:200|SIZE:509)
==> DIRECTORY: http://10.0.0.24/mutillidae/documentation/
+ http://10.0.0.24/mutillidae/favicon.ico (CODE:200|SIZE:1150)
+ http://10.0.0.24/mutillidae/footer (CODE:200|SIZE:450)
+ http://10.0.0.24/mutillidae/header (CODE:200|SIZE:19879)
+ http://10.0.0.24/mutillidae/home (CODE:200|SIZE:2930)
==> DIRECTORY: http://10.0.0.24/mutillidae/images/
+ http://10.0.0.24/mutillidae/inc (CODE:200|SIZE:386260)
==> DIRECTORY: http://10.0.0.24/mutillidae/includes/
+ http://10.0.0.24/mutillidae/index (CODE:200|SIZE:24237)
+ http://10.0.0.24/mutillidae/index.php (CODE:200|SIZE:24237)
+ http://10.0.0.24/mutillidae/installation (CODE:200|SIZE:8138)
==> DIRECTORY: http://10.0.0.24/mutillidae/javascript/
+ http://10.0.0.24/mutillidae/login (CODE:200|SIZE:4102)
+ http://10.0.0.24/mutillidae/notes (CODE:200|SIZE:1721)
+ http://10.0.0.24/mutillidae/page-not-found (CODE:200|SIZE:705)
==> DIRECTORY: http://10.0.0.24/mutillidae/passwords/
+ http://10.0.0.24/mutillidae/phpinfo (CODE:200|SIZE:48828)
+ http://10.0.0.24/mutillidae/phpinfo.php (CODE:200|SIZE:48840)
+ http://10.0.0.24/mutillidae/phpMyAdmin (CODE:200|SIZE:174)
+ http://10.0.0.24/mutillidae/register (CODE:200|SIZE:1823)
+ http://10.0.0.24/mutillidae/robots (CODE:200|SIZE:160)
+ http://10.0.0.24/mutillidae/robots.txt (CODE:200|SIZE:160)
==> DIRECTORY: http://10.0.0.24/mutillidae/styles/ ---- Entering directory: http://10.0.0.24/mutillidae/classes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/documentation/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/javascript/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/passwords/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.0.0.24/mutillidae/styles/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway) -----------------
END_TIME: Fri Feb 7 16:46:55 2020
DOWNLOADED: 4612 - FOUND: 18
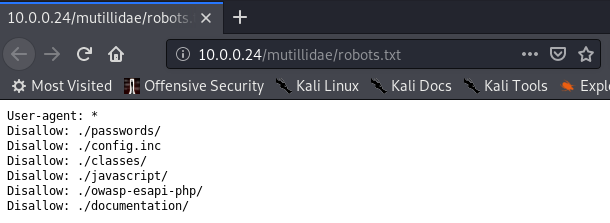
The URL in Red is useful to discove.
For example:
Gethering information is important, while it is harder to get useful information than before.
Ethical Hacking - Web Penetration Testing(2)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- 数据库整理(三) SQL基础
数据库整理(三) SQL基础 SQL语言的特点 集数据定义语言(DDL),数据操纵语言(DML),数据控制语言(DCL)功能于一体. 可以独立完成数据库生命周期中的全部活动: ●定义和修改.删除关 ...
- Linux下重新设置 MySQL 的密码
1.重置密码的第一步就是跳过MySQL的密码认证过程,方法如下: #vim /etc/my.cnf(注:windows下修改的是my.ini) 很多老铁,在开始时设置了 MySQL 的密码,后来一段时 ...
- 为什么说String是线程安全的
String是final修饰的类,是不可变的,所以是线程安全的. 一.Java String类为什么是final的? 1.为了实现字符串池 2.为了线程安全 3.为了实现String可以创建HashC ...
- Django实现图片上传并前端页面显示
Django实现图片上传和图片显示 开始之前我们先确认环境中已经安装了Pillow,如果没有安装,可以通过pip install Pillow来安装,这个是python的图像处理库 数据库设置 我们创 ...
- Flask项目实战:创建电影网站(2)
flask网站制作后台时候常见流程总结 安利一个神神器: 百度脑图PC版 创建数据库 下面是创建User数据库,需要导入db库 #coding:utf8 from flask import Flask ...
- Spring Boot是什么?
背景 最近因公司需要,开始研究java相关的开发,之前一直从事.net相关开发,所以写的或者理解的不对的地方呢,希望大家批评指正. 首先开发框架吧,就像.net很早之前有asp.net webForm ...
- 接口&&多态&&构造函数&&关键字
day06 抽象类的局限性(与接口的区别) 抽象类可以定义非抽象方法,避免子类重复实现这些方法,提高代码重用性;接口只能包含抽象方法;jdk1.8之后接口可以包含默认方法. 一个类只能继承一个直接父类 ...
- 部署JUnit
JUnit的简介和使用:http://blog.csdn.net/luanlouis/article/details/37562165 jar包下载地址:http://www.java2s.com/C ...
- P4817 Fruit Feast G
最开始拿到这道题的时候,题目中其实只规定了两种水果的饱食度,可以理解成价值或是重量,在不超过T的情况求最大值.第一眼看过去感觉就是装箱问题(背包),只不过这道题用的是完全背包,但是考虑到喝水的情况,做 ...
- css与javascript重难点,学前端,基础不好一切白费!
JavaScript是一种属于网络的脚本语言,已经被广泛用于Web应用开发,常用来为网页添加各式各样的动态功能,为用户提供更流畅美观的浏览效果.通常JavaScript脚本是通过嵌入在HTML中来实现 ...
