POJ1523 SPF
| Time Limit: 1000MS | Memory Limit: 10000K | |
| Total Submissions: 8254 | Accepted: 3772 |
Description
Node 3 is therefore a Single Point of Failure (SPF) for this network. Strictly, an SPF will be defined as any node that, if unavailable, would prevent at least one pair of available nodes from being able to communicate on what was previously a fully connected network. Note that the network on the right has no such node; there is no SPF in the network. At least two machines must fail before there are any pairs of available nodes which cannot communicate. 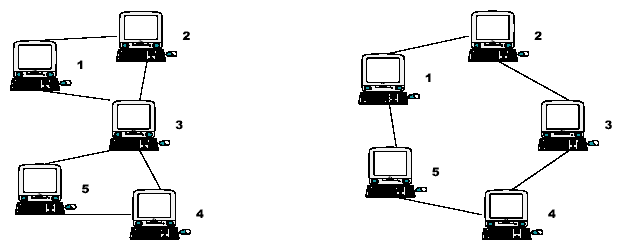
Input
Output
The first network in the file should be identified as "Network #1", the second as "Network #2", etc. For each SPF node, output a line, formatted as shown in the examples below, that identifies the node and the number of fully connected subnets that remain when that node fails. If the network has no SPF nodes, simply output the text "No SPF nodes" instead of a list of SPF nodes.
Sample Input
- 1 2
- 5 4
- 3 1
- 3 2
- 3 4
- 3 5
- 0
- 1 2
- 2 3
- 3 4
- 4 5
- 5 1
- 0
- 1 2
- 2 3
- 3 4
- 4 6
- 6 3
- 2 5
- 5 1
- 0
- 0
Sample Output
- Network #1
- SPF node 3 leaves 2 subnets
- Network #2
- No SPF nodes
- Network #3
- SPF node 2 leaves 2 subnets
- SPF node 3 leaves 2 subnets
Source
点双连通分量模板题
- /*by SilverN*/
- #include<algorithm>
- #include<iostream>
- #include<cstring>
- #include<cstdio>
- #include<cmath>
- #include<vector>
- using namespace std;
- const int mxn=;
- struct edge{
- int v,nxt;
- }e[mxn<<];
- int hd[mxn],mct=;
- void add_edge(int u,int v){
- e[++mct].v=v;e[mct].nxt=hd[u];hd[u]=mct;
- return;
- }
- int n;
- int low[mxn],dfn[mxn],dtime=;
- int num[mxn];
- int st[mxn],top=;
- bool cut[mxn];
- void DFS(int u,int fa){
- low[u]=dfn[u]=++dtime;
- st[++top]=u;
- int i,j;
- for(i=hd[u];i;i=e[i].nxt){
- int v=e[i].v;
- if(v==fa)continue;
- if(!dfn[v]){
- DFS(v,u);
- if(low[v]>=dfn[u]){
- cut[u]=;
- int s=;
- do{
- s=st[top--];
- ++num[s];
- }while(u!=s);
- top++;
- }
- // num[u]++;
- low[u]=min(low[u],low[v]);
- }
- else low[u]=min(dfn[v],low[u]);
- }
- return;
- }
- bool have[mxn];
- int main(){
- int cas=;
- while(){
- memset(hd,,sizeof hd);
- memset(cut,,sizeof cut);
- memset(low,,sizeof low);
- memset(dfn,,sizeof dfn);
- memset(have,,sizeof have);
- memset(num,,sizeof num);
- mct=dtime=top=;
- int i,j,u,v;
- bool flag=;
- while(scanf("%d",&u) && u){
- scanf("%d",&v);
- have[u]=have[v]=;
- add_edge(u,v);
- add_edge(v,u);
- flag=;
- }
- if(!flag)break;
- for(i=;i<=;i++)
- if(have[i] && !dfn[i])DFS(i,);
- printf("Network #%d\n",++cas);
- flag=;
- for(i=;i<=;i++){
- if(num[i]>=){
- flag=;
- printf(" SPF node %d leaves %d subnets\n",i,num[i]);
- }
- }
- if(!flag)printf(" No SPF nodes\n");
- printf("\n");
- }
- return ;
- }
POJ1523 SPF的更多相关文章
- POJ1523 SPF[无向图割点]
SPF Time Limit: 1000MS Memory Limit: 10000K Total Submissions: 8139 Accepted: 3723 Description C ...
- POJ1523 SPF 单点故障
POJ1523 题意很简单,求删除割点后原先割点所在的无向连通图被分成了几个连通部分(原题说prevent at least one pair of available nodes from bein ...
- POJ1523 SPF(割点模板)
题目求一个无向图的所有割点,并输出删除这些割点后形成几个连通分量.用Tarjan算法: 一遍DFS,构造出一颗深度优先生成树,在原无向图中边分成了两种:树边(生成树上的边)和反祖边(非生成树上的边). ...
- POJ1523:SPF(无向连通图求割点)
题目:http://poj.org/problem?id=1523 题目解析: 注意题目输入输入,防止PE,题目就是求割点,并问割点将这个连通图分成了几个子图,算是模版题吧. #include < ...
- poj图论解题报告索引
最短路径: poj1125 - Stockbroker Grapevine(多源最短路径,floyd) poj1502 - MPI Maelstrom(单源最短路径,dijkstra,bellman- ...
- Tarjan求割点和桥
by szTom 前置知识 邻接表存储及遍历图 tarjan求强连通分量 割点 割点的定义 在一个无向图中,如果有一个顶点集合,删除这个顶点集合以及这个集合中所有顶点相关联的边以后,图的连通分量增多, ...
- POJ1523:SPF——题解
http://poj.org/problem?id=1523 这题明显就是求割点然后求割完之后的强连通分量的个数. 割点都会求,怎么求割完的分量个数呢? 我们可以通过万能的并查集啊!(具体做法看代码吧 ...
- POJ 1523 SPF(求割点)
题目链接 题意 : 找出图中所有的割点,然后输出删掉他们之后还剩多少个连通分量. 思路 : v与u邻接,要么v是u的孩子,要么u是v的祖先,(u,v)构成一条回边. //poj1523 #includ ...
- POJ 1523 SPF 割点与桥的推断算法-Tarjan
题目链接: POJ1523 题意: 问一个连通的网络中有多少个关节点,这些关节点分别能把网络分成几部分 题解: Tarjan 算法模板题 顺序遍历整个图,能够得到一棵生成树: 树边:可理解为在DFS过 ...
随机推荐
- oracle用sqlplus创建新用户,不是plsql developer
1.sqlplus /nolog 2.conn /as sysdba 3.alter user system identified by "123456"; 4.alter use ...
- final-----finalize----finally---区别
一.性质不同 (1)final为关键字: (2)finalize()为方法: (3)finally为为区块标志,用于try语句中: 二.作用 (1)final为用于标识常量的关键字,final标识的关 ...
- [转]redis.conf的配置解析
# redis 配置文件示例 # 当你需要为某个配置项指定内存大小的时候,必须要带上单位, # 通常的格式就是 1k 5gb 4m 等酱紫: # # 1k => 1000 bytes # 1kb ...
- Minimum Window Substring
Given a string S and a string T, find the minimum window in S which will contain all the characters ...
- Jdev Run Page 没有反应
从旧电脑把原有的Jdeveloper完整的拷贝至新电脑,且已完整配置JDEV_USER_HOME,JAVA_HOME等环境变量, Run Page报以下错误. [Starting OC4J using ...
- System.Web.HttpRequestValidationException——从客户端检测到危险的Request值
这是比较常见的问题了,如果Web表单中有输入类似于Html标签之类的文本,在通过Request.QueryString或者Request.Form传递这些值的时候,就会触发这样的异常,出于脚本注入等安 ...
- 软件开发之路、Step 1 需求分析
百度百科 需求分析 所谓"需求分析",是指对要解决的问题进行详细的分析,弄清楚问题的要求,包括需要输入什么数据,要得到什么结果,最后应输出什么.可以说,在软件工程当中的“需求分析” ...
- 用python简单处理图片(2):图像通道\几何变换\裁剪
一.图像通道 1.彩色图像转灰度图 from PIL import Image import matplotlib.pyplot as plt img=Image.open('d:/ex.jpg') ...
- gdb学习
gdb学习 [参考资料] http://www.cnblogs.com/jiu0821/p/4483804.html 程序的运行状态有"运行"."暂停".&qu ...
- 零散知识记录-一个MQ问题
[背景]我有一项零散工作:维护大部门的一台测试公用MQ服务器.当大部分MQ被建立起来,编写了维护手册,大家都按照规程来后,就基本上没有再动过它了.周五有同学跟我反映登录不进去了,周日花了1个小时来解决 ...
