Docker容器网络配置
Docker容器网络配置
1、Linux内核实现名称空间的创建
1.1 ip netns命令
可以借助ip netns命令来完成对 Network Namespace 的各种操作。ip netns命令来自于iproute安装包,一般系统会默认安装,如果没有的话,请自行安装。
[root@localhost ~]# dnf -y install iproute
注意:ip netns命令修改网络配置时需要 sudo 权限。
可以通过ip netns命令完成对Network Namespace 的相关操作,可以通过ip netns help查看命令帮助信息:
[root@localhost ~]# ip netns help
Usage: ip netns list
ip netns add NAME
ip netns attach NAME PID
ip netns set NAME NETNSID
ip [-all] netns delete [NAME]
ip netns identify [PID]
ip netns pids NAME
ip [-all] netns exec [NAME] cmd ...
ip netns monitor
ip netns list-id [target-nsid POSITIVE-INT] [nsid POSITIVE-INT]
NETNSID := auto | POSITIVE-INT
默认情况下,Linux系统中是没有任何 Network Namespace的,所以ip netns list命令不会返回任何信息。
1.2 创建Network Namespace
通过命令创建一个名为ns0的命名空间:
[root@localhost ~]# ip netns list
[root@localhost ~]# ip netns add ns0
[root@localhost ~]# ip netns list
ns0
新创建的 Network Namespace 会出现在/var/run/netns/目录下。如果相同名字的 namespace 已经存在,命令会报Cannot create namespace file "/var/run/netns/ns0": File exists的错误。
[root@localhost ~]# ls /var/run/netns/
ns0
[root@localhost ~]# ip netns add ns0
Cannot create namespace file "/var/run/netns/ns0": File exists
对于每个 Network Namespace 来说,它会有自己独立的网卡、路由表、ARP 表、iptables 等和网络相关的资源。
扩展:
问:可不可以直接在/var/run/netns/目录下直接创建一个命名空间ns2呢?
[root@localhost ~]# touch /var/run/netns/ns2
[root@localhost ~]# ip netns list
Error: Peer netns reference is invalid.
Error: Peer netns reference is invalid.
ns2
ns0
从上得知是不行的
1.3 操作Network Namespace
ip命令提供了ip netns exec子命令可以在对应的 Network Namespace 中执行命令。
查看新创建 Network Namespace 的网卡信息
[root@localhost ~]# ip netns exec ns0 ip a
1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
可以看到,新创建的Network Namespace中会默认创建一个lo回环网卡,此时网卡处于关闭状态。此时,尝试去 ping 该lo回环网卡,会提示Network is unreachable
[root@localhost ~]# ip netns exec ns0 ping 127.0.0.1
connect: Network is unreachable
通过下面的命令启用lo回环网卡:
[root@localhost ~]# ip netns exec ns0 ip link set lo up
[root@localhost ~]# ip netns exec ns0 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
[root@localhost ~]# ip netns exec ns0 ping 127.0.0.1
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.031 ms
^C
--- 127.0.0.1 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.031/0.031/0.031/0.000 ms
1.4 转移设备
我们可以在不同的 Network Namespace 之间转移设备(如veth)。由于一个设备只能属于一个 Network Namespace ,所以转移后在这个 Network Namespace 内就看不到这个设备了。
其中,veth设备属于可转移设备,而很多其它设备(如lo、vxlan、ppp、bridge等)是不可以转移的。
1.5 veth pair
veth pair 全称是 Virtual Ethernet Pair,是一个成对的端口,所有从这对端口一 端进入的数据包都将从另一端出来,反之也是一样。
引入veth pair是为了在不同的 Network Namespace 直接进行通信,利用它可以直接将两个 Network Namespace 连接起来。

1.6 创建veth pair
[root@localhost ~]# ip link show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN mode DEFAULT group default
link/ether 02:42:f0:ef:67:fd brd ff:ff:ff:ff:ff:ff
14: veth0@veth1: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/ether 92:53:e7:1c:f2:8c brd ff:ff:ff:ff:ff:ff
15: veth1@veth0: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/ether 56:2b:0c:45:fb:03 brd ff:ff:ff:ff:ff:ff
可以看到,此时系统中新增了一对veth pair,将veth0和veth1两个虚拟网卡连接了起来,此时这对 veth pair 处于”未启用“状态。
1.7 实现Network Namespace间通信
下面我们利用veth pair实现两个不同的 Network Namespace 之间的通信。刚才我们已经创建了一个名为ns0的 Network Namespace,下面再创建一个信息Network Namespace,命名为ns1
[root@localhost ~]# ip netns add ns1
[root@localhost ~]# ip netns list
ns1
ns0
然后我们将veth0加入到ns0,将veth1加入到ns1
[root@localhost ~]# ip link set veth0 netns ns0
[root@localhost ~]# ip link set veth1 netns ns1
然后我们分别为这对veth pair配置上ip地址,并启用它们
[root@localhost ~]# ip netns exec ns0 ip link set veth0 up
[root@localhost ~]# ip netns exec ns0 ip addr add 192.168.100.1/24 dev veth0
[root@localhost ~]# ip netns exec ns1 ip link set lo up
[root@localhost ~]# ip netns exec ns1 ip link set veth1 up
[root@localhost ~]# ip netns exec ns1 ip addr add 192.168.100.2/24 dev veth1
查看这对veth pair的状态
[root@localhost ~]# ip netns exec ns0 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
14: veth0@if15: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 92:53:e7:1c:f2:8c brd ff:ff:ff:ff:ff:ff link-netns ns1
inet 192.168.100.1/24 scope global veth0
valid_lft forever preferred_lft forever
inet6 fe80::9053:e7ff:fe1c:f28c/64 scope link
valid_lft forever preferred_lft forever
[root@localhost ~]# ip netns exec ns1 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
15: veth1@if14: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 56:2b:0c:45:fb:03 brd ff:ff:ff:ff:ff:ff link-netns ns0
inet 192.168.100.2/24 scope global veth1
valid_lft forever preferred_lft forever
inet6 fe80::542b:cff:fe45:fb03/64 scope link
valid_lft forever preferred_lft forever
从上面可以看出,我们已经成功启用了这个veth pair,并为每个veth设备分配了对应的ip地址。我们尝试在ns1中访问ns0中的ip地址:
[root@localhost ~]# ip netns exec ns1 ping 192.168.100.1
PING 192.168.100.1 (192.168.100.1) 56(84) bytes of data.
64 bytes from 192.168.100.1: icmp_seq=1 ttl=64 time=0.051 ms
^C
--- 192.168.100.1 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.051/0.051/0.051/0.000 ms
可以看到,veth pair成功实现了两个不同Network Namespace之间的网络交互。
1.8 veth设备重命名
# 需要先停用设备才能重命名
[root@localhost ~]# ip netns exec ns0 ip link set dev veth0 name zsl0
RTNETLINK answers: Device or resource busy
# 停用veth0
[root@localhost ~]# ip netns exec ns0 ip link set veth0 down
# 将veth0重命名为zsl0
[root@localhost ~]# ip netns exec ns0 ip link set dev veth0 name zsl0
# 启用zsl0
[root@localhost ~]# ip netns exec ns0 ip link set zsl0 up
# 查看是否修改成功
[root@localhost ~]# ip netns exec ns0 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
14: zsl0@if15: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 92:53:e7:1c:f2:8c brd ff:ff:ff:ff:ff:ff link-netns ns1
inet 192.168.100.1/24 scope global zsl0
valid_lft forever preferred_lft forever
inet6 fe80::9053:e7ff:fe1c:f28c/64 scope link
valid_lft forever preferred_lft forever
扩展:
创建veth pair,一个给名称空间a1,一个给本机,并且都配上ip地址,两个能相互通信吗?
# 创建名称空间a1
[root@localhost ~]# ip netns add a1
[root@localhost ~]# ip netns list
a1
# 创建veth pair
[root@localhost ~]# ip link add type veth
# 将veth1给a1
[root@localhost ~]# ip link set veth1 netns a1
# 启用主机和a1的虚拟网卡
[root@localhost ~]# ip link set veth0 up
[root@localhost ~]# ip netns exec a1 ip link set lo up
[root@localhost ~]# ip netns exec a1 ip link set veth1 up
# 给主机的veth0配上ip地址
[root@localhost ~]# ip addr add 192.168.200.1/24 dev veth0
[root@localhost ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1524sec preferred_lft 1524sec
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:ac:46:f8:53 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
4: veth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 2e:f3:88:07:d4:97 brd ff:ff:ff:ff:ff:ff link-netns a1
inet 192.168.200.1/24 scope global veth0
valid_lft forever preferred_lft forever
inet6 fe80::2cf3:88ff:fe07:d497/64 scope link
valid_lft forever preferred_lft forever
# 给a1的veth1配上ip地址
[root@localhost ~]# ip netns exec a1 ip addr add 192.168.200.2/24 dev veth1
[root@localhost ~]# ip netns exec a1 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
5: veth1@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 4a:87:cf:df:f6:46 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 192.168.200.2/24 scope global veth1
valid_lft forever preferred_lft forever
inet6 fe80::4887:cfff:fedf:f646/64 scope link
valid_lft forever preferred_lft forever
# 用主机ping名称空间a1的veth1测试
[root@localhost ~]# ping 192.168.200.2
PING 192.168.200.2 (192.168.200.2) 56(84) bytes of data.
64 bytes from 192.168.200.2: icmp_seq=1 ttl=64 time=0.098 ms
64 bytes from 192.168.200.2: icmp_seq=2 ttl=64 time=0.095 ms
^C
--- 192.168.200.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1045ms
rtt min/avg/max/mdev = 0.095/0.096/0.098/0.009 ms
从上得知是可以相互通信的
2、四种网络模式配置
2.1 bridge模式配置
在创建容器时添加--network bridge与不加--network选项效果是一致的
# 添加--network bridge
[root@localhost ~]# docker run -it --rm --network bridge busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: eth0@if7: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
# 不加--network bridge
[root@localhost ~]# docker run -it --rm busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
8: eth0@if9: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
2.2 none模式配置
[root@localhost ~]# docker run -it --rm --network none busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
# 以上是docker容器帮你做好了,与自己开辟名字空间效果相同
[root@localhost ~]# ip netns add z1
[root@localhost ~]# ip netns exec z1 ip link set lo up
[root@localhost ~]# ip netns exec z1 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2.3 container模式配置
启动第一个容器web1
[root@localhost ~]# docker run -it --rm --name web1 busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
启动第二个容器web2
[root@localhost ~]# docker run -it --rm --name web2 busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: eth0@if7: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
可以看到名为web2的容器IP地址是172.17.0.3,与第一个容器的IP地址不是一样的,也就是说并没有共享网络,此时如果我们将第二个容器的启动方式改变一下,就可以使名为web2的容器IP与web1容器IP一致,也即共享IP,但不共享文件系统。
[root@localhost ~]# docker run -it --rm --name web2 --network container:web1 busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
此时我们在web1容器上创建一个目录
/ # mkdir /tmp/data
/ # ls /tmp/
data
到web2容器上检查/tmp目录会发现并没有这个目录,因为文件系统是处于隔离状态,仅仅是共享了网络而已。
在web2容器上部署一个站点
/ # echo 'hello word' > /tmp/index.html
/ # ls /tmp/
index.html
/ # httpd -h /tmp
/ # netstat -anlt
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 :::80 :::* LISTEN
在web1容器上用本地地址去访问此站点
/ # wget -O - -q 127.0.0.1:80
hello word
由此可见,container模式下的容器间关系就相当于一台主机上的两个不同进程
2.4 host模式配置
启动容器时直接指明模式为host
[root@localhost ~]# docker run -it --rm --network host busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1121sec preferred_lft 1121sec
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue
link/ether 02:42:54:0c:19:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:54ff:fe0c:1902/64 scope link
valid_lft forever preferred_lft forever
此时如果我们在这个容器中启动一个http站点,我们就可以直接用宿主机的IP直接在浏览器中访问这个容器中的站点了。
/ # echo 'hello word' > /tmp/index.html
/ # httpd -h /tmp
/ # netstat -anlt
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 192.168.111.135:22 192.168.111.1:1052 ESTABLISHED
tcp 0 0 :::80 :::* LISTEN
tcp 0 0 :::22 :::* LISTEN
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 9 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*
[root@localhost ~]# curl 192.168.111.135
hello word
扩展:
问:此时还能在创建一个容器再部署一个http站点吗?
[root@localhost ~]# docker run -it --rm --network host busybox
/ # echo 'hello word' > /tmp/index.html
/ # httpd -h /tmp
httpd: bind: Address already in use
从上得知是是不能的,因为端口会冲突。
3、容器的常用操作
3.1 查看容器的主机名
[root@localhost ~]# docker run -it --rm busybox
/ # hostname
a7898c7df6f9
# 主机名默认为容器的ID
[root@localhost ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
a7898c7df6f9 busybox "sh" About a minute ago Up About a minute priceless_swartz
# 无法修改主机名,因为是只读状态
/ # hostname zsl
hostname: sethostname: Operation not permitted
3.2 在容器启动时注入主机名
[root@localhost ~]# docker run -it --rm --hostname zsl busybox
/ # hostname
zsl
# 容器ID不会因为指定hostname而改变成一致
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
7558f343d7b7 busybox "sh" 33 seconds ago Up 32 seconds objective_hoover
# 注入主机名时会自动创建主机名到IP的映射关系
/ # cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.17.0.2 zsl
# DNS也会自动配置为宿主机的DNS
/ # cat /etc/resolv.conf
# Generated by NetworkManager
search localdomain
nameserver 192.168.111.2
# ping zsl
/ # ping zsl
PING zsl (172.17.0.2): 56 data bytes
64 bytes from 172.17.0.2: seq=0 ttl=64 time=0.028 ms
64 bytes from 172.17.0.2: seq=1 ttl=64 time=0.113 ms
^C
--- zsl ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.028/0.070/0.113 ms
3.3 手动指定容器要使用的DNS
[root@localhost ~]# docker run -it --rm --hostname zsl --dns 8.8.8.8 busybox
/ # cat /etc/resolv.conf
search localdomain
nameserver 8.8.8.8
/ # cat /etc/hostname
zsl
/ # ping www.baidu.com
PING www.baidu.com (36.152.44.95): 56 data bytes
64 bytes from 36.152.44.95: seq=0 ttl=127 time=20.362 ms
64 bytes from 36.152.44.95: seq=1 ttl=127 time=35.127 ms
^C
--- www.baidu.com ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 20.362/27.744/35.127 ms
3.4 手动往/etc/hosts文件中注入主机名到IP地址的映射
如果要映射多个主机名就用多个--hostname
[root@localhost ~]# docker run -it --rm busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
14: eth0@if15: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
/ # hostname
c582a2f0d137
(另开一个终端)
# 映射172.17.0.2为zsl2
[root@localhost ~]# docker run -it --rm --hostname zsl1 --dns 8.8.8.8 --add-host zsl2:172.17.0.2 busybox
/ # cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.17.0.2 zsl2
172.17.0.3 zsl1
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
18: eth0@if19: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
/ # ping zsl1
PING zsl1 (172.17.0.3): 56 data bytes
64 bytes from 172.17.0.3: seq=0 ttl=64 time=0.043 ms
^C
--- zsl1 ping statistics ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.043/0.043/0.043 ms
/ # ping zsl2
PING zsl2 (172.17.0.2): 56 data bytes
64 bytes from 172.17.0.2: seq=0 ttl=64 time=0.149 ms
64 bytes from 172.17.0.2: seq=1 ttl=64 time=0.162 ms
^C
--- zsl2 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.149/0.155/0.162 ms
3.5 开放容器端口
执行docker run的时候有个-p选项,可以将容器中的应用端口映射到宿主机中,从而实现让外部主机可以通过访问宿主机的某端口来访问容器内应用的目的。
-p选项能够使用多次,其所能够暴露的端口必须是容器确实在监听的端口。
-p选项的使用格式:
- -p
- 将指定的容器端口映射至主机所有地址的一个动态端口
- -p :
- 将容器端口映射至指定的主机端口
- -p ::
- 将指定的容器端口映射至主机指定的动态端口
- -p ::
- 将指定的容器端口映射至主机指定的端口
示例:
-p (containerPort)
将指定的容器端口映射至主机所有地址的一个动态端口
[root@localhost ~]# docker run -d -p 80 httpd
5d969f5c435c02164caf5945ba2a0f5d0ff3c8b7d3e6217adc5c03f855b1c028
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
5d969f5c435c httpd "httpd-foreground" 28 seconds ago Up 27 seconds 0.0.0.0:49153->80/tcp, :::49153->80/tcp competent_payne
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 0.0.0.0:49153 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 [::]:49153 [::]:*
[root@localhost ~]# curl 172.17.0.2
<html><body><h1>It works!</h1></body></html>
[root@localhost ~]# curl 192.168.111.135:49153
<html><body><h1>It works!</h1></body></html>
-p (hostPort):(containerPort)
将容器端口(containerPort)映射至指定的主机端口(hostPort)
[root@localhost ~]# docker run -d -p 8080:80 httpd
554dc98f55155d31e6b79adedda74c937eaf4459582a088bae5d2e3fbfb25307
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
554dc98f5515 httpd "httpd-foreground" 9 seconds ago Up 8 seconds 0.0.0.0:8080->80/tcp, :::8080->80/tcp distracted_galileo
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:8080 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:8080 [::]:*
LISTEN 0 128 [::]:22 [::]:*
[root@localhost ~]# curl 172.17.0.2
<html><body><h1>It works!</h1></body></html>
[root@localhost ~]# curl 192.168.111.135:8080
<html><body><h1>It works!</h1></body></html>
-p (ip)::(containerPort)
将指定的容器端口(containerPort)映射至主机指定(ip)的动态端口
[root@localhost ~]# docker run -d -p 192.168.111.135::80 httpd
edde41dc824b45b2aafd50e41268a19faf0f31d11a43c67c821d0b8fa997ecec
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
edde41dc824b httpd "httpd-foreground" 7 seconds ago Up 5 seconds 192.168.111.135:49153->80/tcp strange_curie
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 192.168.111.135:49153 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
root@localhost ~]# curl 172.17.0.2
<html><body><h1>It works!</h1></body></html>
[root@localhost ~]# curl 192.168.111.135:49153
<html><body><h1>It works!</h1></body></html>
-p (ip):(hostPort):(containerPort)
将指定的容器端口(containerPort)映射至主机指定(ip)的端口(hostPort)
[root@localhost ~]# docker run -d -p 192.168.111.135:80:80 httpd
c044e47fbff6473c26df06a78f523b9683e60ac906e136799669dba47d92059a
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c044e47fbff6 httpd "httpd-foreground" 5 seconds ago Up 4 seconds 192.168.111.135:80->80/tcp mystifying_chatterjee
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 192.168.111.135:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
[root@localhost ~]# curl 172.17.0.2
<html><body><h1>It works!</h1></body></html>
[root@localhost ~]# curl 192.168.111.135:80
<html><body><h1>It works!</h1></body></html>
动态端口指的是随机端口,具体的映射结果可使用docker port命令查看。
[root@localhost ~]# docker port c044e47fbff6
80/tcp -> 192.168.111.135:80
注意:
iptables防火墙规则将随容器的创建自动生成,随容器的删除自动删除规则。
3.6 自定义docker0网桥的网络属性信息
自定义docker0网桥的网络属性信息很多,以下只演示bip,更多详情见官方文档相关配置
需要修改/etc/docker/daemon.json配置文件
[root@localhost ~]# vim /etc/docker/daemon.json
{
"registry-mirrors": ["https://6vrrj6n2.mirror.aliyuncs.com"],
"bip": "192.168.100.1/24"
}
[root@localhost ~]# systemctl daemon-reload
[root@localhost ~]# systemctl restart docker
[root@localhost ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1224sec preferred_lft 1224sec
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:35:39:6d:e6 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.1/24 brd 192.168.100.255 scope global docker0
valid_lft forever preferred_lft forever
# 网桥修改后,创建出来的容器虚拟网卡IP地址规律也会改变
[root@localhost ~]# docker run -it --rm busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:64:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.2/24 brd 192.168.100.255 scope global eth0
valid_lft forever preferred_lft forever
/ # route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 0.0.0.0 UG 0 0 0 eth0
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
核心选项为bip,即bridge ip之意,用于指定docker0桥自身的IP地址;其它选项可通过此地址计算得出。
3.7 Docker 远程连接
dockerd守护进程的C/S,其默认仅监听Unix Socket格式的地址(/var/run/docker.sock),如果要使用TCP套接字,则需要修改/etc/docker/daemon.json配置文件,添加如下内容,然后重启docker服务:
[root@localhost ~]# vim /lib/systemd/system/docker.service
......
ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock -H unix:///run/docker.sock -H tcp://0.0.0.0:2375
......
[root@localhost ~]# systemctl daemon-reload
[root@localhost ~]# systemctl restart docker
在客户端上向dockerd直接传递“-H|--host”选项指定要控制哪台主机上的docker容器
[root@localhost ~]# docker -H 192.168.111.135:2375 ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3.8 Docker创建自定义桥接网络
创建一个额外的自定义桥,区别于docker0
[root@localhost ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
90e83c543376 bridge bridge local
38bb8b947433 host host local
c74fce351c8a none null local
[root@localhost ~]# docker network create -d bridge --subnet "192.168.1.0/24" --gateway "192.168.1.1" br0
a932f50dbb6bff81a904962fda8f7ec348ac2dfdab0833e339a988b85b7926f3
[root@localhost ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
a932f50dbb6b br0 bridge local
90e83c543376 bridge bridge local
38bb8b947433 host host local
c74fce351c8a none null local
[root@localhost ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1042sec preferred_lft 1042sec
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:35:39:6d:e6 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.1/24 brd 192.168.100.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:35ff:fe39:6de6/64 scope link
valid_lft forever preferred_lft forever
6: br-a932f50dbb6b: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:ee:0a:b3:e1 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-a932f50dbb6b
valid_lft forever preferred_lft forever
使用新创建的自定义桥来创建容器c2:
[root@localhost ~]# docker run -it --name c2 --network br0 busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7: eth0@if8: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:01:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.2/24 brd 192.168.1.255 scope global eth0
valid_lft forever preferred_lft forever
再创建一个容器c1,使用默认的bridge桥:
[root@localhost ~]# docker run -it --name c1 --network bridge busybox
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
9: eth0@if10: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:64:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.2/24 brd 192.168.100.255 scope global eth0
valid_lft forever preferred_lft forever
试想一下,此时的c1(192.168.100.2)与c2(192.168.1.2)能否互相通信?如果不能该如何实现通信?
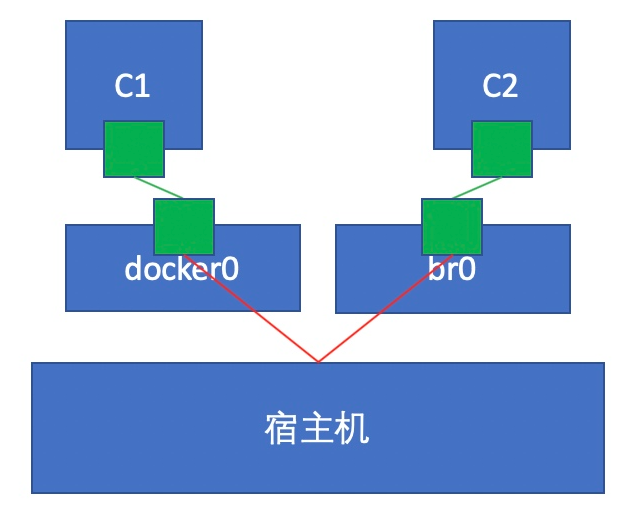
给容器添加网络
# 给c1加br0
[root@localhost ~]# docker network connect br0 c1
# 容器c1:
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
13: eth0@if14: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:64:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.2/24 brd 192.168.100.255 scope global eth0
valid_lft forever preferred_lft forever
15: eth1@if16: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:01:03 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.3/24 brd 192.168.1.255 scope global eth1
valid_lft forever preferred_lft forever
# ping c2
/ # ping 192.168.1.2
PING 192.168.1.2 (192.168.1.2): 56 data bytes
64 bytes from 192.168.1.2: seq=0 ttl=64 time=0.127 ms
64 bytes from 192.168.1.2: seq=1 ttl=64 time=0.102 ms
^C
--- 192.168.1.2 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.102/0.114/0.127 ms
# 给c2加bridge
[root@localhost ~]# docker network connect bridge c2
# 容器c2:
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: eth0@if12: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:01:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.2/24 brd 192.168.1.255 scope global eth0
valid_lft forever preferred_lft forever
17: eth1@if18: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:c0:a8:64:03 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.3/24 brd 192.168.100.255 scope global eth1
valid_lft forever preferred_lft forever
# ping c1测试
/ # ping 192.168.100.2
PING 192.168.100.2 (192.168.100.2): 56 data bytes
64 bytes from 192.168.100.2: seq=0 ttl=64 time=0.226 ms
64 bytes from 192.168.100.2: seq=1 ttl=64 time=0.088 ms
^C
--- 192.168.100.2 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.088/0.157/0.226 ms
由上可见,c1(192.168.100.2)与c2(192.168.1.2)能互相通信。
Docker容器网络配置的更多相关文章
- Docker容器安装配置SQLServer服务(Linux)
一:前言 随着不断的对Docker容器的实践和学习,越来越觉得容器的强大,把 SQL Server 数据库服务放在docker容器中,比你自己在宿主服务器上面安装配置一个SQL Server服务器是要 ...
- Docker容器网络篇
Docker容器网络篇 作者:尹正杰 版权声明:原创作品,谢绝转载!否则将追究法律责任. 一.Docker的网络模型概述 如上图所示,Docker有四种网络模型: 封闭式网络(Closed conta ...
- 【转】理解Docker容器网络之Linux Network Namespace
原文:理解Docker容器网络之Linux Network Namespace 由于2016年年中调换工作的原因,对容器网络的研究中断过一段时间.随着当前项目对Kubernetes应用的深入,我感觉之 ...
- docker 之网络配置
Docker 网络实现 首先,要实现网络通信,机器需要至少一个网络接口(物理接口或虚拟接口)来收发数据包:此外,如果不同子网之间要进行通信,需要路由机制. Docker 中的网络接口默认都是虚拟的接口 ...
- docker.[5] 网络配置-1
docker[5] 网络配置-1 执行 ifconfig 可以看到有一个 docker01 ,这个其实就是容器的虚拟网桥,在执行指令:brctl show(如果该指令不能执行,请先安装: yum -y ...
- 两台主机间docker容器网络互通
服务器1: 网络172.30.0.0/16 服务器2: 网络172.31.0.0/16 服务器1和服务器2上的docker容器网络之间是无法互通的,如果需要互通,需要做以下配置: 服务器1上执行: i ...
- docker容器网络bridge
我们知道docker利用linux内核特性namespace实现了网络的隔离,让每个容器都处于自己的小世界里面,当这个小世界需要与外界(宿主机或其他容器)通信的时候docker的网络就发挥作用了,这篇 ...
- Docker容器网络-基础篇
开源Linux 一个执着于技术的公众号 Docker的技术依赖于Linux内核的虚拟化技术的发展,Docker使用到的网络技术有Network Namespace.Veth设备对.Iptables/N ...
- Linux namespace技术应用实践--调用宿主机命令(tcpdump/ip/ps/top)检查docker容器网络、进程状态
背景 最近偶然听了几堂极客时间的云原生免费公开课程,首次接触到了Linux namespace技术,并了解到这正是现在风头正劲的容器技术基石,引起了自己探究一二的兴趣,结合课程+网络搜索+实践操作,也 ...
随机推荐
- BUUCTF刷题记录(更新中...)
极客大挑战 2019]EasySQL-1 直接通过输入万能密码:' or 1=1#实现注入: 思考:服务端sql语句应该为:select * from users where username='xx ...
- 如何在 pyqt 中自定义工具提示 ToolTip
前言 Qt 自带的工具提示样式不太好看,就算加了样式表也时不时会失效,同时工具提示没有阴影,看起来就更难受了.所以本篇博客将会介绍自定义工具提示的方法,效果如下图所示: 实现过程 工具提示其实就是一个 ...
- 关于TornadoFx和Android的全局配置工具类封装实现及思路解析
原文地址: 关于TornadoFx和Android的全局配置工具类封装实现及思路解析 - Stars-One的杂货小窝 目前个人开发软件存在设置页面,可以让用户自定义些设置,但我发现,存储数据的代码逻 ...
- GO GMP协程调度实现原理 5w字长文史上最全
1 Runtime简介 Go语言是互联网时代的C,因为其语法简洁易学,对高并发拥有语言级别的亲和性.而且不同于虚拟机的方案.Go通过在编译时嵌入平台相关的系统指令可直接编译为对应平台的机器码,同时嵌入 ...
- Halodoc使用 Apache Hudi 构建 Lakehouse的关键经验
Halodoc 数据工程已经从传统的数据平台 1.0 发展到使用 LakeHouse 架构的现代数据平台 2.0 的改造.在我们之前的博客中,我们提到了我们如何在 Halodoc 实施 Lakehou ...
- Ubuntu-apt-get出错
ubuntu apt-get的时候出现: E: Could not open lock file /var/lib/dpkg/lock-frontend - open (13: Permission ...
- 基于SqlSugar的开发框架循序渐进介绍(9)-- 结合Winform控件实现字段的权限控制
字段的权限控制,一般就是控制对应角色人员对某个业务对象的一些敏感字段的可访问性:包括可见.可编辑性等处理.本篇随笔结合基于SqlSugar的开发框架进行的字段控制管理介绍. 在设计字段权限的时候,我们 ...
- Elasticsearch学习系列四(聚合搜索)
聚合分析 聚合分析是数据库中重要的功能特性,完成对一个查询的集中数据的聚合计算.如:最大值.最小值.求和.平均值等等.对一个数据集求和,算最大最小值等等,在ES中称为指标聚合,而对数据做类似关系型数据 ...
- Linux yum搭建私有仓库
搭建yum仓库需要两种资源: rpm包 rpm包的元数据(repodata) 搭建好仓库后需要使用三种网络协议共享出来 http或https ftp 范例: 使用http协议搭建私有仓库 (本示例使用 ...
- Work Center View * cannot be used for report assignment. Please deselect错误解决方法
by zyi
