nvgre
GRE RFC2784 工作原理
Structure of a GRE Encapsulated Packet
A GRE encapsulated packet has the form:
---------------------------------
| |
| Delivery Header |
| |
---------------------------------
| |
| GRE Header |
| |
---------------------------------
| |
| Payload packet |
| |
---------------------------------
This specification is generally concerned with the structure of the
GRE header, although special consideration is given to some of the
issues surrounding IPv4 payloads.
GRE Header
The GRE packet header has the form:
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|C| Reserved0 | Ver | Protocol Type |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum (optional) | Reserved1 (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Key and Sequence Number Extensions to GRE RFC2890
Extensions to GRE Header
The GRE packet header[1] has the following format:
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|C| Reserved0 | Ver | Protocol Type |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum (optional) | Reserved1 (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
The proposed GRE header will have the following format:
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|C| |K|S| Reserved0 | Ver | Protocol Type |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum (optional) | Reserved1 (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Key (optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Sequence Number (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Key Present (bit 2)
If the Key Present bit is set to 1, then it indicates that the
Key field is present in the GRE header. Otherwise, the Key
field is not present in the GRE header.
Sequence Number Present (bit 3)
If the Sequence Number Present bit is set to 1, then it
indicates that the Sequence Number field is present.
Otherwise, the Sequence Number field is not present in the GRE
header.
The Key and the Sequence Present bits are chosen to be
compatible with RFC 1701 [2].
NVGRE RFC 7637
NVGRE是一个由RFC 2784定义和RFC 2890扩展的通道协议。 微软的blog
Outer Ethernet Header:
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Outer) Destination MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|(Outer)Destination MAC Address | (Outer)Source MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Outer) Source MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Optional Ethertype=C-Tag 802.1Q| Outer VLAN Tag Information |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Ethertype 0x0800 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Outer IPv4 Header:
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Version| HL |Type of Service| Total Length |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Identification |Flags| Fragment Offset |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Time to Live | Protocol 0x2F | Header Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Outer) Source Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Outer) Destination Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ GRE Header: key was set to 1
Protocol Type field in the GRE header is set to 0x6558
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|0| |1|0| Reserved0 | Ver | Protocol Type 0x6558 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Virtual Subnet ID (VSID) | FlowID |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Inner Ethernet Header
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Inner) Destination MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|(Inner)Destination MAC Address | (Inner)Source MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| (Inner) Source MAC Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Ethertype 0x0800 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Inner IPv4 Header:
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Version| HL |Type of Service| Total Length |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Identification |Flags| Fragment Offset |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Time to Live | Protocol | Header Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Source Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Destination Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options | Padding |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Original IP Payload |
| |
| |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Figure 1: GRE Encapsulation Frame Format
The best starting place is to first layout the addressing scheme for IP addresses and subnets that you'd like to virtualize. When configuring Hyper-V Network Virtualization, there are two types of IP Addresses that you'll be interacting with:
- Provider Addresses (PA) - these are unique IP addresses assigned to each Hyper-V host that are routable across the physical network infrastructure. I like to think of "PA" addresses as "Physical Addresses", because they are assigned to physical Hyper-V hosts. Each Hyper-V host requires at least one PA to be assigned.
- Customer Addresses (CA) - these are unique IP addresses assigned to each Virtual Machine that will be participating on a virtualized network. I like to think of "CA" addresses as "Container Addresses", because they are the IP Addresses assigned to each VM "container" for use by the guest operating system running inside that VM. Using NVGRE, multiple CA's for VMs running on a Hyper-V host can be tunneled using a single PA on that Hyper-V host. CA's must be unique across all VMs on the same virtualized network, but CA's do not need to be unique across virtualized networks (such as in multi-tenant scenarios where each customer's VMs are isolated on separate virtualized networks).
Let's look at a simple example of NVGRE with two Hyper-V hosts using PA's and CA's:

In this example, you'll note that each Hyper-V host is assigned one PA address ( e.g., 192.168.x.x ) used for tunneling NVGRE traffic across two physical subnets ( e.g., 192.168.1.x/24 and 192.168.2.x/24 ) on the physical network. In addition, each VM is assigned a CA address ( e.g., 10.x.x.x ) that is unique within each virtualized network and is tunneled inside the NVGRE tunnel between hosts.
To separate the traffic between the two virtualized networks, the GRE headers on the tunneled packets include a GRE Key that provides a unique Virtual Subnet ID ( e.g., 5001 and 6001 ) for each virtualized network.
Based on this configuration, we have two virtualized networks ( e.g., the "Red" network and the "Blue" network ) that are isolated from one another as separate IP networks and extended across two physical Hyper-V hosts located on two different physical subnets.
Once you have the following defined for your environment in a worksheet, you're ready to move on to the next steps in configuring Hyper-V Network Virtualization:
- PA's for each Hyper-V Host
- CA's for each Virtual Machine
- Virtual Subnet ID's for each subnet to be virtualized
Neutron 理解 (3): Open vSwitch + GRE/VxLAN 组网 [Netruon Open vSwitch + GRE/VxLAN Virutal Network]
Tunneling And Network Virtualization: NVGRE, VXLAN
Demo:
Using GRE Tunnels with Open vSwitch
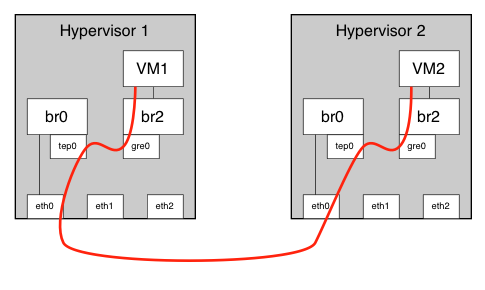
普通的GRE 应该是需要arp代理吗?
script: gre.sh
#!/bin/bash
# sudo apt install bridge-utils
REMOTE_IP=$
SUBNET=$ # HOST1: 192.168.0.1, HOST2: 192.169.0.1
GREIP=$ # HOST1: 10.10.10.1, HOST2: 10.10.10.2
R_GREIP=$ # HOST1: 10.10.10.2, HOST2: 10.10.10.1
DEV=$
LOCAL_IP=`ip addr show $DEV| awk '/inet /{split($2,a,"/"); print a[1]}'`
sudo ip tunnel add gre1 mode gre remote $REMOTE_IP local $LOCAL_IP ttl
sudo ip link set gre1 up sudo ip addr add $GREIP/ dev gre1
# sudo ip route add ${SUBNET%.*}./ via $R_GREIP dev gre1 # 不能工作
sudo ip route add ${SUBNET%.*}./ dev gre1 #为 gre 添加ip
sudo echo > /proc/sys/net/ipv4/ip_forward #让服务器支持转发
# HOST1
sudo iptables -t nat -A POSTROUTING -d ${SUBNET%.*}./ -j SNAT --to $GREIP#否则访问 ${SUBNET%.*}./24网段不通 # HOST2
iptables -t nat -A POSTROUTING -s $GREIP -d ${SUBNET%.*}./ -j SNAT --to $SUBNET #否则192.168.1.X等机器访问10.1.1.x网段不通
iptables -A FORWARD -s $GREIP -m state --state NEW -m tcp -p tcp --dport -j DROP #禁止直接访问线上的3306,防止内网被破 sudo brctl addbr br1 # sudo ifconfig br1 192.169.0.7/
sudo ip link set br1 up
# sudo brctl addif br1 gre1 # 不能工作 sudo ip link add type veth
sudo ifconfig veth0 ${SUBNET%.*}./ up
sudo ifconfig veth0 mtu
sudo ifconfig veth1 up
sudo ifconfig veth1 mtu
sudo brctl addif br1 veth1 ip route show
on host 1: $ ./gre.sh 10.0.0.52 192.168.0.1 10.10.10.1 10.10.10.2 ens3
on host 2: $ ./gre.sh 10.0.0.32 192.169.0.1 10.10.10.2 10.10.10.1 ens3
on host 1
sudo ovs-vsctl add-br br0
sudo ovs-vsctl add-port br0 tep0 -- set interface tep0 type=internal
sudo ifconfig tep0 192.168.200.20 netmask 255.255.255.0
sudo ovs-vsctl add-br br2
sudo ovs-vsctl add-port br2 gre0 -- set interface gre0 type=gre options:remote_ip=192.168.200.21
route
# ip link add br0 type bridge
sudo ip tuntap add mode tap
sudo ifconfig tap0 192.168.200.20 netmask 255.255.255.0
sudo ip link set tap0 up
sudo ip link set br1 up
sudo brctl addif br1 tap0
sudo brctl addif br1 ens3 # 该命令会导致网络访问不了
sudo ip link add type veth
sudo ifconfig veth0 192.167.0.6/ up
sudo ifconfig veth0 mtu
sudo ifconfig veth1 up
sudo ifconfig veth1 mtu
sudo ovs-vsctl add-port br2 veth1
$ sudo ovs-vsctl add-port br0 ens3 # 该命令会导致网络访问不了
on host 2
sudo ovs-vsctl add-br br0
sudo ovs-vsctl add-port br0 tep0 -- set interface tep0 type=internal
sudo ifconfig tep0 192.168.200.21 netmask 255.255.255.0
sudo ovs-vsctl add-br br2
sudo ovs-vsctl add-port br2 gre0 -- set interface gre0 type=gre options:remote_ip=192.168.200.20
route
$ sudo ovs-vsctl show
ffb98c3f-a7a4--b84a-c7c2b2616c72
Bridge "br0"
Port "tep0"
Interface "tep0"
type: internal
Port "br0"
Interface "br0"
type: internal
Bridge "br2"
Port "br2"
Interface "br2"
type: internal
Port "gre0"
Interface "gre0"
type: gre
options: {remote_ip="192.168.200.21"}
ovs_version: "2.5.2"
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default localhost 0.0.0.0 UG ens3
10.0.0.0 * 255.255.255.0 U ens3
169.254.169.254 localhost 255.255.255.255 UGH ens3
192.168.200.0 * 255.255.255.0 U tep0
$ sudo ip link show
: lo: <LOOPBACK,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN mode DEFAULT group default qlen
link/loopback ::::: brd :::::
: ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast state UP mode DEFAULT group default qlen
link/ether fa::3e::b0: brd ff:ff:ff:ff:ff:ff
: ovs-system: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN mode DEFAULT group default qlen
link/ether b6::ba:ee:7d:b6 brd ff:ff:ff:ff:ff:ff
: br2: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN mode DEFAULT group default qlen
link/ether a2:::5a::4a brd ff:ff:ff:ff:ff:ff
: br0: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN mode DEFAULT group default qlen
link/ether 3e:2f:8d::: brd ff:ff:ff:ff:ff:ff
: tep0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN mode DEFAULT group default qlen
link/ether ::8c:1d:2b: brd ff:ff:ff:ff:ff:ff
: gre0@NONE: <NOARP> mtu qdisc noop state DOWN mode DEFAULT group default qlen
link/gre 0.0.0.0 brd 0.0.0.0
: gretap0@NONE: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN mode DEFAULT group default qlen
link/ether ::::: brd ff:ff:ff:ff:ff:ff
: gre_sys@NONE: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast master ovs-system state UNKNOWN mode DEFAULT group default qlen
link/ether a6:ee:6f:a2:0e: brd ff:ff:ff:ff:ff:ff
$ sudo ip addr show [/]
: lo: <LOOPBACK,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN group default qlen
link/loopback ::::: brd :::::
inet 127.0.0.1/ scope host lo
valid_lft forever preferred_lft forever
inet6 ::/ scope host
valid_lft forever preferred_lft forever
: ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast state UP group default qlen
link/ether fa::3e::b0: brd ff:ff:ff:ff:ff:ff
inet 10.0.0.54/ brd 10.0.0.255 scope global ens3
valid_lft forever preferred_lft forever
inet6 fe80::f816:3eff:fe88:b029/ scope link
valid_lft forever preferred_lft forever
: ovs-system: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN group default qlen
link/ether b6::ba:ee:7d:b6 brd ff:ff:ff:ff:ff:ff
: br2: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN group default qlen
link/ether a2:::5a::4a brd ff:ff:ff:ff:ff:ff
: br0: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN group default qlen
link/ether 3e:2f:8d::: brd ff:ff:ff:ff:ff:ff
: tep0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN group default qlen
link/ether ::8c:1d:2b: brd ff:ff:ff:ff:ff:ff
inet 192.168.200.20/ brd 192.168.200.255 scope global tep0
valid_lft forever preferred_lft forever
inet6 fe80:::8cff:fe1d:2b99/ scope link
valid_lft forever preferred_lft forever
: gre0@NONE: <NOARP> mtu qdisc noop state DOWN group default qlen
link/gre 0.0.0.0 brd 0.0.0.0
: gretap0@NONE: <BROADCAST,MULTICAST> mtu qdisc noop state DOWN group default qlen
link/ether ::::: brd ff:ff:ff:ff:ff:ff
: gre_sys@NONE: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast master ovs-system state UNKNOWN group default qlen
link/ether a6:ee:6f:a2:0e: brd ff:ff:ff:ff:ff:ff
inet6 fe80::a4ee:6fff:fea2:e22/ scope link
valid_lft forever preferred_lft forever
$ sudo ovs-vsctl add-port br0 ens3 # 该命令会导致网络访问不了
sudo ip link add type veth
sudo ifconfig veth0 192.167.0.6/ up
sudo ifconfig veth0 mtu
sudo ifconfig veth1 up
sudo ifconfig veth1 mtu
sudo ovs-vsctl add-port br2 veth1
$ ip link help
...
TYPE := { vlan | veth | vcan | dummy | ifb | macvlan | macvtap |
bridge | bond | ipoib | ip6tnl | ipip | sit | vxlan |
gre | gretap | ip6gre | ip6gretap | vti | nlmon |
bond_slave | ipvlan | geneve | bridge_slave | vrf }
深入理解 GRE tunnel GRE 与IPIP的区别。 ipip tunnel 是端对端的,通信也就只能是点对点的,而 GRE tunnel 却可以进行多播。
该ppt中内置了GRE和IPIP的包, 可供大家分析。
nvgre的更多相关文章
- Windows Server 2012 虚拟化实战:网络(一)
虚拟化对于计算的抽象,大家可能相对熟悉,也许都有在单机使用诸如Virtual PC或者Virtual Box的经验.使用的这些虚拟化软件的第一印象就是我们的CPU可以同时运行多套不同的操作系统,并且其 ...
- RedHat 和 Mirantis OpenStack 产品的版本和功能汇总和对比(持续更新)
Mirantis 和 Red Hat 作为 OpenStack 商业化产品领域的两大领军企业,在行业内有重要的地位.因此,研究其产品版本发布周期和所支持的功能,对制定 OpenStack 产品的版本和 ...
- 深入浅出Hyper-V网络虚拟化技术
年后综合症刚刚消失殆尽,转眼就要迎接各种新的工作任务了:之前写过一篇有关hyper-v网络虚拟化内容的博文,主要是从操作系统层面入手,概要性的总结了一下,基本也都是参考了大部分官方内容再加以个人修饰: ...
- Neutron 理解 (3): Open vSwitch + GRE/VxLAN 组网 [Netruon Open vSwitch + GRE/VxLAN Virutal Network]
学习 Neutron 系列文章: (1)Neutron 所实现的虚拟化网络 (2)Neutron OpenvSwitch + VLAN 虚拟网络 (3)Neutron OpenvSwitch + GR ...
- SDN跟网络虚拟化的完美结合
SDN跟网络虚拟化的完美结合 之前说过,所谓的“SDN最适合的领域是数据中心”的说法,笔者认为更准确的说法应该是SDN最适合的领域是数据中心中的网络虚拟化应用.为什么说SDN 非常适合用在网络虚拟化中 ...
- Overlay network 覆盖网络
From Wikipedia, the free encyclopedia An overlay network is a computer network that is built on top ...
- YY游戏私有云平台实践 (转自InfoQ )
作者 风河 发布于 2016年1月13日 | 讨论 编者按:YY游戏的页游早在2013年就在云平台上运行,其Cloud 1.0已经支撑几十万的同时在线用户.日前,YY游戏云平台进行了Cloud 2 ...
- 【Networking】flannel,pipework,weave,udp,vxlan,ovs等资料
Add Open vSwitch-based multitenant backend for use with OpenShift / Kubernetes: https://github.com/ ...
- 【Kubernetes】两篇文章 搞懂 K8s 的 fannel 网络原理
近期公司的flannel网络很不稳定,花时间研究了下并且保证云端自动部署的网络能够正常work. 1.网络拓扑 拓扑如下:(点开看大图) 容器网卡通过docker0桥接到flannel0网卡,而每个 ...
随机推荐
- React对比Vue(一些小细节的差异)
@1===>发现一个神奇的地方在对数组进行增加删除的时候 react中一个输入框点击enter键,然后数组push,然后渲染 <input ref='valInput' onKeyUp={ ...
- Selenium基础知识(六)下拉列表定位
1.下拉列表定位 要选择下拉列表中的元素,要先定位到,下拉列表元素,然后可以通过xpath去点击,表内内容 例如,百度搜索-->百度设置-->搜索设置-->选择下拉列表框内" ...
- PyQT5速成教程-1 简介与环境搭建
本文由 沈庆阳 所有,转载请与作者取得联系! PyQt简介 一个良好的界面是人机交互中十分重要的一环. Python作为脚本语言,起初并未拥有GUI开发的部分.但随着其开放的扩展性,使得Python不 ...
- 不同版本Hibernate.获取SessionFactory的方式
不同版本Hibernate.获取SessionFactory的方式 Hibernate 版本说明: 我当前使用的是 Hibernate 5.x ,(hibernate-release-5.3.6.Fi ...
- [ Windows BAT Script ] BAT 脚本获取windows权限
BAT 脚本获取windows权限 @echo off echo I am trying to run as Administrator %1 %2 ver|find "5."&g ...
- [13]Windows 内核情景分析 --- 网络通信
典型的基于tcpip协议套接字方式的网络通信模块层次: 应用程序 socket api WS2_32.dll socket irp Afd.sys tdi irp Tcpip.sys 回调函数接口 各 ...
- Intel 80386 微处理器的存储器管理
一.存储器的管理 存储器的管理是一种硬件机制,微处理器在总线地址上对物理存储器进行寻址.但是,为了给程序提供比物理存储器容量更大的空间,就引入了虚拟存储器的概念,它在外存(比如磁盘)的支持 ...
- d'jang基础
1,建立一个名为guest的django项目,django-admin startproject guest 生成一个guest文件夹,包含一个guest文件夹和一个manage.py cd gue ...
- 导航,头部,CSS基础
1.制作自己的导航条. 2.HTML头部元素: <base> 定义了页面链接标签的默认链接地址 <style> 定义了HTML文档的样式文件 <link> 定 ...
- mysql 安装目录说明
