Ethical Hacking - NETWORK PENETRATION TESTING(1)
Pre--Connection-Attacks that can be done before connecting to the network.
Gaining Access - How to break Wi-Fi keys(WEP/WPA/WPA2)
Post-Connection-Attacks can be done after connecting to the network.
Detection&Security - detect and prevent the above attacks
Sniffing Basics - MAC Address
Each network card has a physical static address assigned by the card manufacturer called MAC address(Media Access Control)
This address is used between devices to identify each other and to transfer packets to the right place.
Each packet has a source MAC and a destination MAC.
We can change your MAC address value that is stored in the memory using a program called macchanger like so:
ifconfig [INTERFACE] down
macchanger -m [MAC] [INTERFACE]
ifconfig [INTERFACE] up
[INFTERFACE] = your wifi card name
[MAC] = the mac address you want to use
Install TP-Link TL-WDN5200 Driver on Kali Linux:
1. Check system information and network setting.
root@kali:~# uname -a
Linux kali 5.2.-kali2-amd64 # SMP Debian 5.2.-2kali1 (--) x86_64 GNU/Linux
root@kali:~# cat /etc/issue
Kali GNU/Linux Rolling \n \l root@kali:~# lsusb
Bus Device : ID 0bda:c811 Realtek Semiconductor Corp. .11ac NIC
Bus Device : ID 1d6b: Linux Foundation 2.0 root hub
Bus Device : ID 0e0f: VMware, Inc. Virtual USB Hub
Bus Device : ID 0e0f: VMware, Inc. Virtual Mouse
Bus Device : ID 1d6b: Linux Foundation 1.1 root hub
root@kali:~# lsusb -t
/: Bus .Port : Dev , Class=root_hub, Driver=uhci_hcd/2p, 12M
|__ Port : Dev , If , Class=Human Interface Device, Driver=usbhid, 12M
|__ Port : Dev , If , Class=Hub, Driver=hub/7p, 12M
/: Bus .Port : Dev , Class=root_hub, Driver=ehci-pci/6p, 480M
|__ Port : Dev , If , Class=Vendor Specific Class, Driver=, 480M
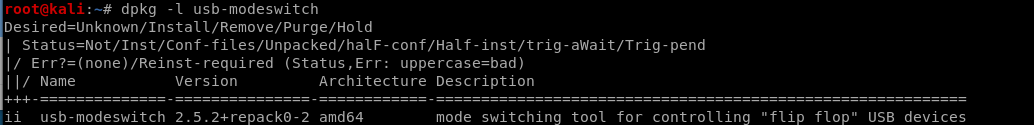
2. Check the usb-modeswitch installation status.
dpkg -l usb-modeswitch
3. Down load the driver code.
https://github.com/chenhaiq/mt7610u_wifi_sta_v3002_dpo_20130916
4.
I will continue after receive the ALFA AWUS1900 WiFi adapter.
Ethical Hacking - NETWORK PENETRATION TESTING(1)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- laravel向视图传递变量
向视图中传递变量 我们在开发web应用当中,通常都不是为了写静态页面而生的,我们需要跟数据打交道,那么这个时候,问题就来了,在一个MVC的框架中,怎么将数据传给视图呢?比如我们要在 ArticleCo ...
- 【Azure SQL】数据库性能分析
前置条件 用户有查询数据统计权限 GRANT VIEW DATABASE STATE TO database_user; CPU性能问题 正在发生 查看前X个CPU消耗查询 (汇总) SELECT T ...
- [ C++ ] 勿在浮沙筑高台 —— 内存管理(1~8p)primitives(上)
C++ memory primitives(原语) new 若malloc失败会调用 int _callnewh(size_t t); 即调用用户设定的handler(回调函数指针),可用于内存回收防 ...
- 虚拟机VMware克隆之后网络不可用的解决办法
现在有两台虚拟机,113是111的克隆,要让113能够使用,需要做下面的修改 5.解决办法5.1.修改克隆后机器(B机器)70-persistent-net.rules文件内容 对克隆后机器(B机器) ...
- 33_栈程序演示.swf
pBottom执行栈底有效元素的前一个节点,该节点没有存储有效数据,这样设计是便于栈的管理,向链表一样pHead指向链表的第一个节点,该节点是不存储有效数据的 pTop执行栈顶最新的节点 如果pTop ...
- 尚学堂 208.Annotation注解和内置注解
208.Annotation注解和内置注解 override:这个注释的作用是标识某一个方法是否覆盖了它的父类的方法deprecated:表示果某个类成员的提示中出现了个词,就表示这个并不建议使用这个 ...
- C# CLosedXML四句代码搞定DataTable数据导出到Excel
最近用到DataTable导出到Excel,网上看了一下,都不怎么好使,逛了下GitHub一下完美解决了 用到的.net库CLosedXML,这个库用于读取,处理和写入Excel 2007+(.xls ...
- BigDecimal类型比较数字大小
BigDecimal类型比较数字大小1.转成intBigDecimal b1 = new BigDecimal("-121454125453.145");if(b1.intValu ...
- [源码解析]Oozie来龙去脉之提交任务
[源码解析]Oozie来龙去脉之提交任务 0x00 摘要 Oozie是由Cloudera公司贡献给Apache的基于工作流引擎的开源框架,是Hadoop平台的开源的工作流调度引擎,用来管理Hadoop ...
- IDEA 2020.1 插件市场无法找到官方的汉化包解决办法
问题: idea 终于更新了2020.1版本,新增了好多的特性,官方也终于支持了中文语言包,但是下载后在插件市场无法找到官方的汉化包 解决: 去IDEA插件中心 (https://plugins.je ...
