Lab 6-4
In this lab, we’ll analyze the malware found in the file Lab06-04.exe.
Questions and Short Answers
What is the difference between the calls made from the main method in Labs 6-3 and 6-4?
A: The function at 0x401000 is the check Internet connection method, 0x401040 is the parse HTML method, 0x4012B5 is printf, and 0x401150 is the switch statement.
What new code construct has been added to main?
A: A for loop has been added to the main method.
What is the difference between this lab’s parse HTML function and those of the previous labs?
A: The function at 0x401040 now takes a parameter and calls sprintf with the format string Internet Explorer 7.50/pma%d. It builds a User-Agent for use during HTTP communication using the argument passed in.
How long will this program run? (Assume that it is connected to the Internet.)
A: This program will run for 1440 minutes (24 hours).
Are there any new network-based indicators for this malware?
A: Yes, a new User-Agent is used. It takes the form Internet Explorer 7.50/
pma%d, where %d is the number of minutes the program has been running.What is the purpose of this malware?
A: First, the program checks for an active Internet connection. If none is found, the program terminates. Otherwise, the program will use a unique User-Agent to attempt to download a web page containing a counter that tracks the number of minutes the program has been running. The web page downloaded contains an embedded HTML comment starting with
<!--. The next character is parsed from this comment and used in a switch statement to determine the action to take on the local system. These are hard-coded actions, including deleting a file, creating a directory, setting a registry run key, copying a file, and sleeping for 100 seconds. This program will run for 24 hours before terminating.
Detailed Analysis
We begin by performing basic static analysis on the binary. We see one new string of interest that was not in Lab 6-3, as follows:
Internet Explorer 7.50/pma%d

It looks like this program may use a dynamically generated User-Agent. Looking at the imports, we don’t see any Windows API functions that were not in Lab 6-3. When performing dynamic analysis, we also notice this User-Agent change when we see Internet Explorer 7.50/pma0.

注:可参考 Lab 6-2 相应部分。
Next, we perform more in-depth analysis with disassembly. We load the executable into IDA Pro and look at the main method, which is clearly structurally different from main in Lab 6-3, although many of the same functions are called. We see the functions 0x401000 (check Internet connection method), 0x401040 (parse HTML method), 0x4012B5 as printf, and 0x401150 (the switch statement). You should rename these functions as such in IDA Pro to make them easier to analyze.
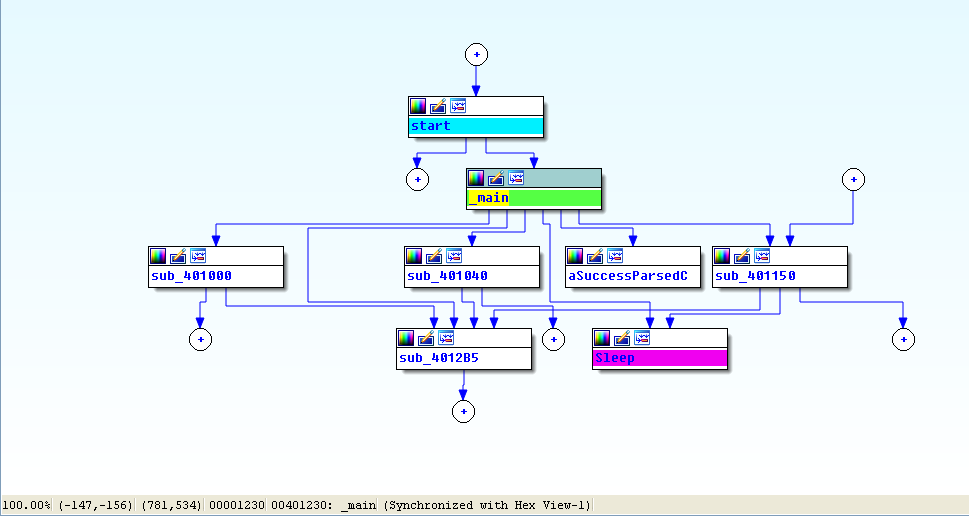
View -> Graphs -> Flow chart :
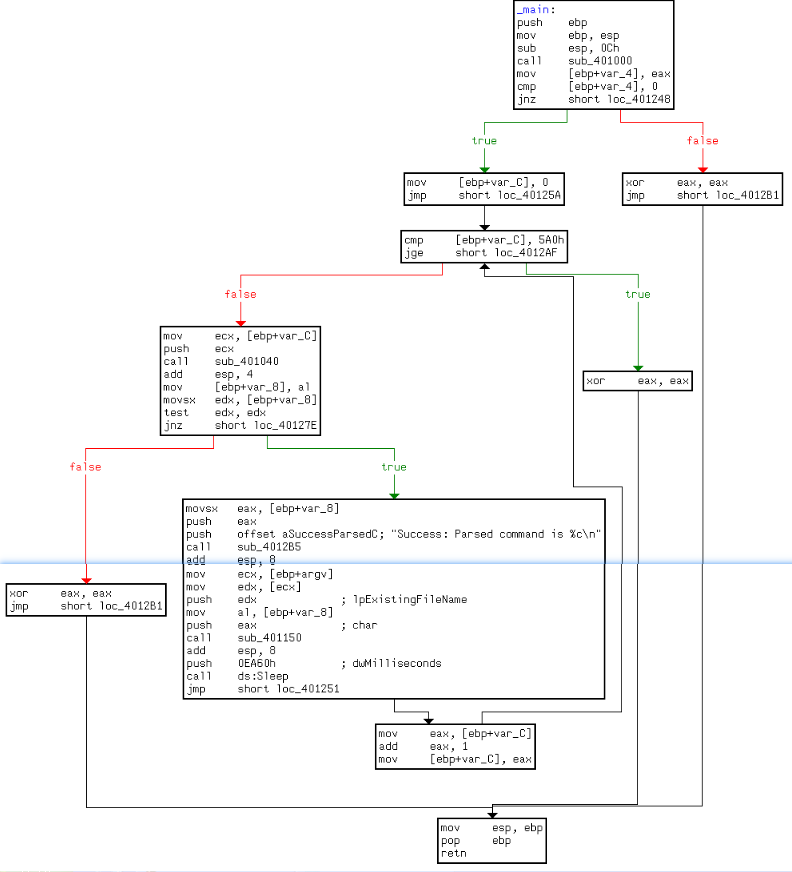
Looking at the main method in IDA Pro’s graphical view mode, we see an upward-facing arrow, which signifies looping. Listing 6-9L shows the loop structure.
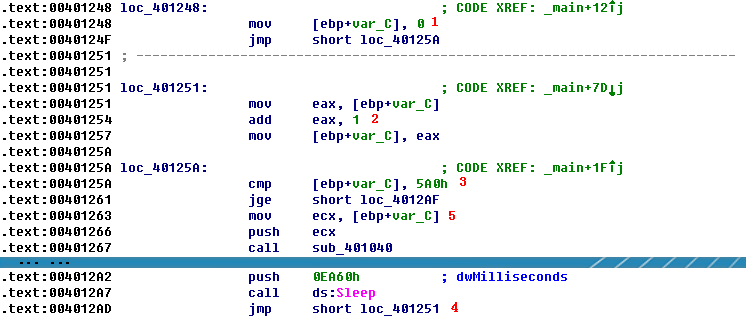
Listing 6-9L: The loop structure
The variable var_C is the local variable used for the loop counter. The counter is initialized to 0 at \({\color{red} 1 }\), jumps past the incrementing at \({\color{red} 2 }\), performs a check at \({\color{red} 3 }\), and loops back to the incrementor when it gets to \({\color{red} 4 }\). The presence of these four code sections tells us that we are looking at a for loop code construct. If the var_C (counter) is greater than or equal to 0x5A0 (1440), the loop will end. Otherwise, the code starting at \({\color{red} 5 }\) is executed. The code pushes var_C on the stack before calling 0x401040, and then sleeps for 1 minute before looping up at \({\color{red}4}\) and incrementing the counter by one. Therefore, this process will repeat for 1440 minutes, which is equal to 24 hours.
In previous labs, 0x401040 did not take a parameter, so we need to investigate this further. Listing 6-10L shows the start of 0x401040.
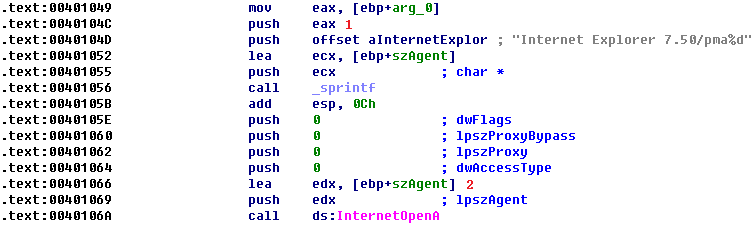
Listing 6-10L: The function at 0x401040
Here, arg_0 is the only parameter, and main is the only method calling 0x401040, so we conclude that arg_0 is always the counter (var_C) from the main method. Arg_0 is pushed on the stack at
Lab 6-4的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- sql 查分数段人数
select count(case 分数字段 when 100 then 1 end) as [满分],count(case when 分数字段 between 90 and 99 then 1 en ...
- iPhone IOS10安装APP没提示连接网络(无法联网)的解决办法
iPhone升级ios10之后,遇到如标题所述问题时: 1.退出APP,设置-蜂窝移动网络-无线局域网助理-开启 2.进入APP,这时候就回提示连接网络了. 提醒: 数据流量有限的朋友,平时请关闭&q ...
- ueditor富文本上传图片的时候报错"未找上传数据"
最近因为需求所以在ssh项目中使用了Ueditor富文本插件,但是在上传图片的时候总是提示“未找到上传数据”,之后百度了好久终于弄明白了.因为Ueditor在上传图片的时候会访问controller. ...
- 为什么入门首选C语言
对于大部分程序员,C语言是学习编程的第一门语言,很少有不了解C的程序员. C语言除了能让你了解编程的相关概念,带你走进编程的大门,还能让你明白程序的运行原理,比如,计算机的各个部件是如何交互的,程序在 ...
- poj1733(并查集+离散化)
题目大意:有一个长度为n的0,1字符串, 给m条信息,每条信息表示第x到第y个字符中间1的个数为偶数个或奇数个, 若这些信息中第k+1是第一次与前面的话矛盾, 输出k; 思路:x, y之间1的个数为偶 ...
- java poi 合并 word文档
import java.io.FileInputStream;import java.io.FileOutputStream;import java.io.InputStream;import jav ...
- 2017.11.18 手把手教你学51单片机-点亮LED
In Doing We Learning 在操作中学习.如果只是光看教程,没有实际的操作,对编程语言的理解很空泛,所以决定从单片机中学习C语言. #include<reg52.h> ...
- Linux+Jenkins环境搭建
一.安装基础环境 1. yum -y install java-1.8.0-openjdk.x86_64 #安装1.8jdk 2. 查看java 版本 [root@localhost djanggo_ ...
- Python pyYAML模块
pyYaml模块 一.pyYAML python也可以很容的处理ymal文档格式,只不过取药安装一个模块. 语法例子 注:主要用来做配置文件. 注:需要下载标准库.
- Shell 实践、常用脚本进阶
1.备份单个文件 #!/bin/bash #备份单个文件 DATE=`/bin/date +%y%m%d` /bin/tar -czpf /backup/$1.$DATE.tar.gz /backup ...
