Ethical Hacking - GAINING ACCESS(7)
Server Side Attacks - NEXPOSE
NeXpose is a vulnerability management framework, it allows us to discover, assess and act on discovered vulnerabilities, it also tells us a lot of info about the discovered vulnerabilities, whether they are exploitable and helps us write a report at the end of the assessment.
Installation Steps:
1. Download it from http://download2.rapid7.com/download/NeXpose-v4/NeXposeSetup-Linux64.bin
2. Stop postgresql > service postgresql stop
3. Change permissions to executable. > chmod +x [installer file name]
4. Run installer > ./[installer file name]
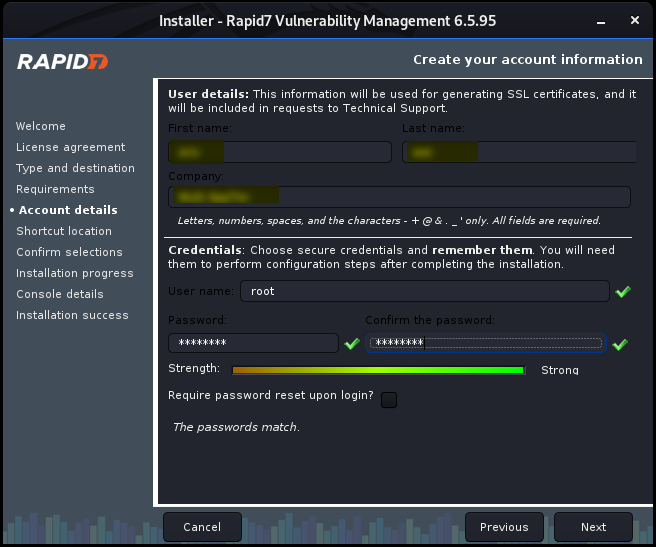
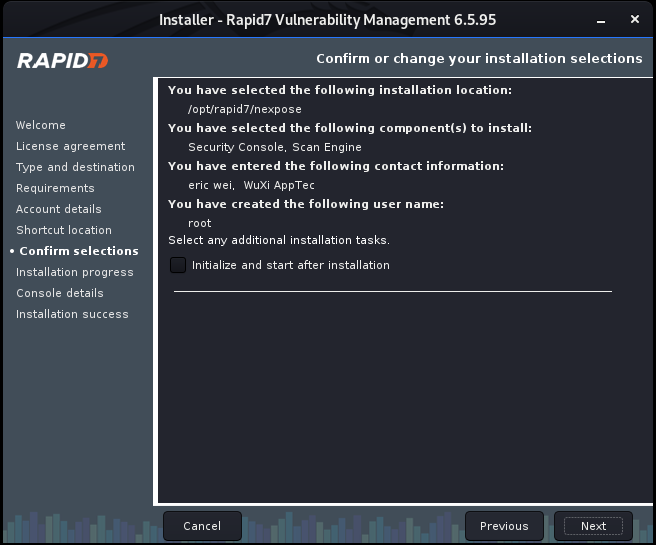
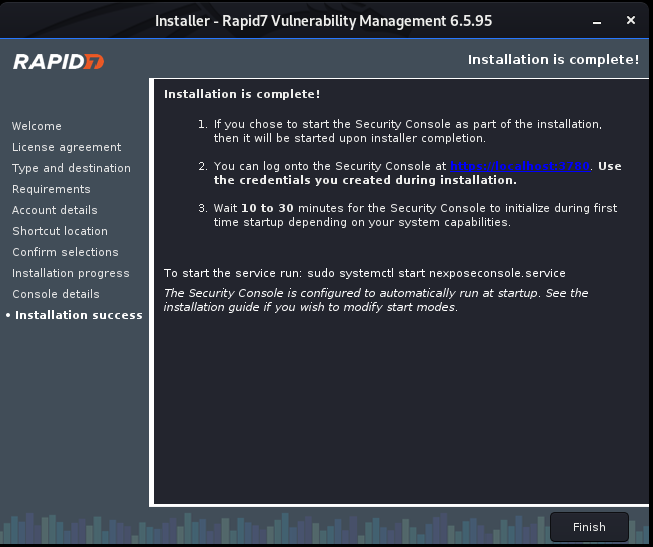
Install Nexpose step by step:



Ethical Hacking - GAINING ACCESS(7)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- rust 学习之旅一, rust编程环境相关
Mac rust环境 rust安装: curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh rust更新: rustup upd ...
- git 提交流程
Git提交流程: 1. Menu remote > (拉取)fetch 2. 重新扫描(rescan) 3. 缓存改动(stage change) 4. 写注释后提交(commit) 5. Me ...
- ca33a_demo_c++_新旧代码的兼容char数组与vector_string相互转换
/*ca33a_demo_c++33_CppPrimer_新旧代码的兼容_txwtech旧代码:数组和c风格字符串新代码:vector和string相互转换:c风格字符串<- ->stri ...
- rest_framework django 简单使用(数据库创建数据, 覆盖数据, 其他的大同小异)
事先说几个坑:数据库定义字段时候,不要定义name 要定义 username 首先, 定义model(简单定义) from django.db import models from django.co ...
- 小技巧:如何快速开启一个静态 HTTP 服务?
静态 HTTP 服务的几个用途: 静态网页的 HTTP 服务,以访问浏览 如:生成的文档.博客等 公开文件的 HTTP 服务,以访问下载 如:分享的文档.安装包等 以下会介绍目前我了解的方式中,最推荐 ...
- dart快速入门教程 (3)
3.运算符 运算符本质上就是代表某运算规则的符号,例如: + ,这个符号,代表着数学运算里面的加法,按照加法法则进行运算即可,同理,学习运算符就是掌握这些规则而已 3.1.算术运算符 算术运算符主要包 ...
- CListBOX 用法
ListBox的操作比较简单: 1添加数据 声明控件变量的类别为Control,变量类型为CListBox,变量名为m_ListBox_Content. m_ListBox_Content.AddSt ...
- GRpc异常处理Filter
全局错误处理服务端 微软已经实施了Interceptors,它们类似于Filter或Middlewares在ASP.NET MVC的核心或的WebAPI,它们可以用于全局异常处理,日志记录,验证等. ...
- C# 从1到Core--委托与事件
委托与事件在C#1.0的时候就有了,随着C#版本的不断更新,有些写法和功能也在不断改变.本文温故一下这些改变,以及在NET Core中关于事件的一点改变. 一.C#1.0 从委托开始 1. 基本方式 ...
- c语言学习笔记第二章———入门
B站有视频演示 2.1软件安装 推荐软件 1.dev-c++ 下载链接:(腾讯软件管家的下载地址) https://sm.myapp.com/original/Development/Dev-Cpp_ ...
