服务器遭受 ssh 攻击
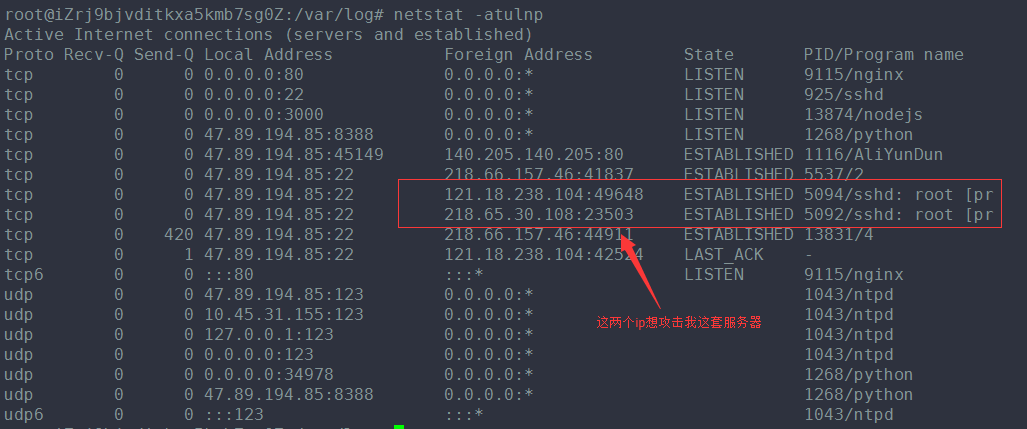
查看auth.log日志,差点吓一跳,好多攻击记录。
vim /var/log/auth.log
才两天的功夫,900多万条记录,

一些解决应对的办法:
|
43down voteaccepted
|
It is very common. Many botnets try to spread that way, so this is a wide scale mindless attack. Mitigation measures include:
|
标注黄色背景的是解决的办法!
stack-overflow上面,搜索了一下这方面的攻击,看到一个提问和我遇到的情况类似:
Is it normal to get hundreds of break-in attempts per day?
I just checked my server's /var/log/auth.log and found that I'm getting over 500 failed password/break-in attempt notifications per day! My site is small, and its URL is obscure. Is this normal? Should I be taking any measures?
下面是回答:
|
Until we locked down all unnecessary external ports, I remember not only did we get lots of hack attempts, but one day it was so bad that we were being hacked from two different countries -- at the same time! So yes, 100s of break-in attempts is perfectly normal. – Django Reinhardt Mar 8 '11 at 14:53
|
||
|
We have servers that experience a new attack "sequence" once every 16 seconds. A single sequence is usually a batch of around 100 attempts across various ports. Just for kicks one day I turned on an unpatched server outside our firewall; it tooks less than 10 minutes from the time it was powered on for it to get pwnd. Point is the internet truly is a jungle; try not to get eaten. – NotMe Mar 8 '11 at 18:55
|
||
|
I can see I posted my question to the wrong site: superuser.com/questions/200896/… – Justin C Mar 9 '11 at 22:01
|
||
|
while I agree with others this is normal on common ports required (80, 443) I practically eliminated these attempts against my SSH port by simply changing the default port from 22 to something obscure like 6022 for example. Just doing that, alone, nearly eliminated 99% of that type of attack. – Kilo Mar 11 '11 at 20:32
|
||
|
If you're going to change your SSH port, there are security reasons to keep it below port 1024 (only root can open ports < 1024, so it protects you from other users hijacking SSH). –
|
|
accepted
|
In today's internet this is quite normal sadly. There are hordes of botnets trying to login to each server they find in whole IP networks. Typically, they use simple dictionary attacks on well-known accounts (like root or certain applications accounts). The attack targets are not found via Google or DNS entries, but the attackers just try every IP address in a certain subnet (e.g. of known root-server hosting companies). So it doesn't matter that your URL (hence the DNS entry) is rather obscure. That's why it is so important to:
Additionally, you can install fail2ban which will scan the authlog and if it finds a certain amount of failed login attempts from an IP, it will proceed to add that IP to In addition to the SSH attacks, it is also becoming common to scan your webserver for vulnerable web-applications (some blogging apps, CMSs, phpmyadmin, etc.). So make sure to keep those up-to-date and securely configured too! |
||||||||||||||||||||
|
服务器遭受 ssh 攻击的更多相关文章
- 服务器被ddos攻击?分析如何防止DDOS攻击?
上周知名博主阮一峰的博客被DDOS攻击,导致网站无法访问而被迫迁移服务器的事情,引起了广大网友的关注及愤慨,包括小编的个人博客也曾接受过DDOS的“洗礼”,对此感同身受.所以,本文我们一起来了解下DD ...
- 向 Git 服务器添加 SSH 公钥
. . . . . 在网上很少找到文章有提到如何将自己的 Git 远程仓库配置成可以通过 SSH 公钥方式认证的,而几乎清一色都是告诉你怎么通过 web 界面向 GitHub 添加 SSH 公钥.LZ ...
- 发起SSH攻击主机IP地址列表
发起SSH攻击主机IP地址列表 东北大学 http://antivirus.neu.edu.cn/scan/ssh.php 以下IP地址对SSH服务进行攻击,严重增加主机成为肉鸡的可能性.强烈建议网管 ...
- Linux服务器使用SSH的命令(有详细的参数解释)
前一阵远程维护Linux服务器,使用的是SSH,传说中的secure shell. 登陆:ssh [hostname] -u user 输入密码:***** 登陆以后就可以像控制自己的机器一样控制它了 ...
- 批量实现多台服务器之间ssh无密码登录的相互信任关系
最近IDC上架了一批hadoop大数据业务服务器,由于集群环境需要在这些服务器之间实现ssh无密码登录的相互信任关系.具体的实现思路:在其中的任一台服务器上通过"ssh-keygen -t ...
- linux服务器的SSH 配置
远程连接服务器: 就是通过文字或图形接口的方式来远程登陆另外一台服务器系统,让你在远程的终端前面登陆linux 主机以取得可操作主机的接口 主要的远程连接服务器的主要类型: 1)文字接口明文传输 : ...
- Mac下如何连接linux服务器(SSH)-比较好用的SSH工具推荐
Mac下如何连接linux服务器(SSH) 1.用mac自带终端连接 步骤如下: 打开终端,在顶部shell菜单中选择新建远程连接 在右侧服务器窗口点击+号,添加服务器,输入IP等信息 输入用户名,点 ...
- Fail2ban 防止暴力破解centos服务器的SSH或者FTP账户
次尝试登陆root账户失败的情况.[说明服务器被攻击了] logtarget = SYSLOG #我们需要做的就是把这行改成/var/log/fail2ban.log,方便用来记录日志信息 so ...
- Linux服务器限制ssh登录,查看登录日志
网络上的服务器很容易受到攻击,最惨的就是被人登录并拿到root权限.有几个简单的防御措施: 1. 修改ssh服务的默认端口 ssh服务的默认端口是22,一般的恶意用户也往往扫描或尝试连接22端口.所以 ...
随机推荐
- ListView间隔设置颜色
在Adapter的getView中 if (position % 2 == 0) holder.shoucangbt.setBackgroundColor( Color.rgb(246, 246, 2 ...
- ASCII码对应表chr(9)、chr(10)、chr(13)、chr(32)、chr(34)、chr(39)
chr(9) tab空格 chr(10) 换行 chr(13) 回车 Chr(13)&chr(10) 回车换行 chr(32) 空格符 ...
- hdu_5701_中位数计数
题目连接:http://acm.hdu.edu.cn/showproblem.php?pid=5701 题意:不解释 题解:n^2的方法:sum[j]表示当前枚举的数到第j个数形成的区间里当前数偏离中 ...
- 1305: Substring
#include <iostream>#include<string.h>#include<stdio.h> using namespace std; #defin ...
- ice调通过iceReplica用所有server instance的方法---客户端控制服务端的负载均衡
I 使用此方法,可以增量的通知Ice服务配置的改变,刷新每个服务进程的数据 可以手动控制客户端调用的负载均衡,客户端程序决定将请求发往那个进程 上代码: import logging import I ...
- 如何使用 AngularJS 的 ngShow 和 ngHide
今天我们来看看怎样使用Angular的ngShow 和ngHide 指令来完成它们听起来应该完成的,显示和隐藏! 它们应该做的事 ngShow 和ngHide 允许我们显示或隐藏不同的元素.这有助于创 ...
- NSArray的containsObject漏洞
1.NSArray中的containsObject的用法 NSMutableArray *array=[NSMutableArray array]; if(