centos7.6 升级openssh openssl
centos7.3和centos7.6升级完毕测试登录ssh以及重启后登录ssh均无问题。
前期请自行配置好yum源(如果不会请百度)
整个过程不需要卸载原先的openssl包和openssh的rpm包。不影响我们的操作
本文的环境都是系统自带的openssh,没有经历过手动编译安装方式。如果之前有手动编译安装过openssh,请参照本文自行测试是否能成功。
如果严格参照本文操作,我保证你升级没问题
centos7.6升级后的效果
[root@testssh ~]# ssh -V
OpenSSH_8.0p1, OpenSSL 1.0.2r Feb
[root@testssh ~]# openssl version
OpenSSL 1.0.2r Feb [root@testssh ~]# cat /etc/redhat-release
CentOS Linux release 7.6. (Core)
[root@testssh ~]#
安装依赖包
升级需要几个组件,有些是和编译相关的等
[root@linux-node3 ~]# yum install -y gcc gcc-c++ glibc make autoconf openssl openssl-devel pcre-devel pam-devel
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors..com
* epel: mirrors.aliyun.com
* extras: mirrors.cn99.com
* updates: mirrors.cn99.com
Package gcc-4.8.-.el7_6..x86_64 already installed and latest version
Package gcc-c++-4.8.-.el7_6..x86_64 already installed and latest version
Package glibc-2.17-.el7_6..x86_64 already installed and latest version
Package :make-3.82-.el7.x86_64 already installed and latest version
Package autoconf-2.69-.el7.noarch already installed and latest version
Package :openssl-1.0.2k-.el7_6..x86_64 already installed and latest version
Package :openssl-devel-1.0.2k-.el7_6..x86_64 already installed and latest version
Package pcre-devel-8.32-.el7.x86_64 already installed and latest version
Package pam-devel-1.1.-.el7.x86_64 already installed and latest version
Nothing to do
[root@linux-node3 ~]#
安装pam和zlib等(后面的升级操作可能没用到pam,安装上也没啥影响,如果不想安装pam请自行测试)
[root@linux-node3 ~]# yum install -y pam* zlib*
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors..com
* epel: mirrors.aliyun.com
* extras: mirrors.cn99.com
* updates: mirrors.cn99.com
Package pam_yubico-2.26-.el7.x86_64 already installed and latest version
Package pam_script-1.1.-.el7.x86_64 already installed and latest version
Package pam_oath-2.4.-.el7.x86_64 already installed and latest version
Package pam_snapper-0.2.-.el7.x86_64 already installed and latest version
Package pam_ssh_agent_auth-0.10.-2.16.el7.x86_64 already installed and latest version
Package pam_2fa-1.0-.el7.x86_64 already installed and latest version
Package pam_mapi-0.3.-.el7.x86_64 already installed and latest version
Package pam_ssh_user_auth-1.0-.el7.x86_64 already installed and latest version
Package pam_mount-2.16-.el7.x86_64 already installed and latest version
Package pam_radius-1.4.-.el7.x86_64 already installed and latest version
Package pamtester-0.1.-.el7.x86_64 already installed and latest version
Package pam_afs_session-2.6-.el7.x86_64 already installed and latest version
Package pam_pkcs11-0.6.-.el7.x86_64 already installed and latest version
Package pam-1.1.-.el7.x86_64 already installed and latest version
Package pam_ssh-2.3-.el7.x86_64 already installed and latest version
Package :pam_url-0.3.-.el7.x86_64 already installed and latest version
Package pam_wrapper-1.0.-.el7.x86_64 already installed and latest version
Package pam-kwallet-5.5.-.el7.x86_64 already installed and latest version
Package pam-devel-1.1.-.el7.x86_64 already installed and latest version
Package pam_krb5-2.4.-.el7.x86_64 already installed and latest version
Package zlib-devel-1.2.-.el7.x86_64 already installed and latest version
Package zlib-static-1.2.-.el7.x86_64 already installed and latest version
Package zlib-1.2.-.el7.x86_64 already installed and latest version
Package zlib-ada-1.4-0.5.20120830CVS.el7.x86_64 already installed and latest version
Package zlib-ada-devel-1.4-0.5.20120830CVS.el7.x86_64 already installed and latest version
Nothing to do
[root@linux-node3 ~]#
下载openssh包和openssl的包
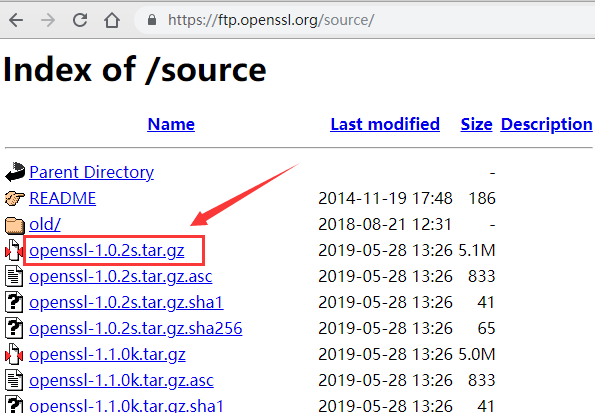
我们都下载最新版本,下载箭头指的包
https://openbsd.hk/pub/OpenBSD/OpenSSH/portable/

https://ftp.openssl.org/source
开始安装openssl
个人习惯把安装包或者工具之类的放下面目录。根据个人喜好随便放,不影响安装
[root@linux-node3 ~]# mkdir /data/tools -p
[root@linux-node3 ~]# cd /data/tools/
[root@linux-node3 /data/tools]# rz -E
rz waiting to receive.
[root@linux-node3 /data/tools]# ll
total
-rw-r--r-- root root Apr : openssl-1.0.2r.tar.gz 解压文件
[root@linux-node3 /data/tools]# tar xfz openssl-1.0.2r.tar.gz
[root@linux-node3 /data/tools]# ll
total
drwxr-xr-x root root Apr : openssl-1.0.2r
-rw-r--r-- root root Apr : openssl-1.0.2r.tar.gz
[root@linux-node3 /data/tools]# cd
[root@linux-node3 ~]# 现在是系统默认的版本,等会升级完毕对比下
[root@linux-node3 ~]# openssl version
OpenSSL 1.0.2k-fips Jan
[root@linux-node3 ~]#
备份下面2个文件或目录(如果存在的话就执行)
[root@linux-node3 ~]# mv /usr/bin/openssl /usr/bin/openssl_bak
[root@linux-node3 ~]# ll /usr/include/openssl
total
-rw-r--r-- root root Mar : aes.h
-rw-r--r-- root root Mar : asn1.h
-rw-r--r-- root root Mar : asn1_mac.h
-rw-r--r-- root root Mar : asn1t.h
-rw-r--r-- root root Mar : bio.h
-rw-r--r-- root root Mar : blowfish.h
...... [root@linux-node3 ~]# mv /usr/include/openssl /usr/include/openssl_bak
编译安装新版本的openssl
配置、编译、安装3个命令一起执行
&&符号表示前面的执行成功才会执行后面的
[root@linux-node3 ~]# cd /data/tools/openssl-1.0.2r/ [root@linux-node3 /data/tools/openssl-1.0.2r]# ./config shared && make && make install
下面2个文件或者目录做软链接 (刚才前面的步骤mv备份过原来的)
[root@linux-node3 ~]# ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
[root@linux-node3 ~]# ln -s /usr/local/ssl/include/openssl /usr/include/openssl
[root@linux-node3 ~]# ll /usr/bin/openssl
lrwxrwxrwx root root Apr : /usr/bin/openssl -> /usr/local/ssl/bin/openssl
[root@linux-node3 ~]# ll /usr/include/openssl -ld
lrwxrwxrwx root root Apr : /usr/include/openssl -> /usr/local/ssl/include/openssl
[root@linux-node3 ~]#
命令行执行下面2个命令加载新配置
echo "/usr/local/ssl/lib" >> /etc/ld.so.conf /sbin/ldconfig
查看确认版本。没问题
[root@testssh ~]# openssl version
OpenSSL 1.0.2s May
安装openssh
上传openssh的tar包并解压
[root@testssh ~]# cd /data/tools/
[root@testssh tools]# ll
total
-rw-r--r-- root root Apr : openssh-.0p1.tar.gz
drwxr-xr-x root root Apr : openssl-1.0.2r
-rw-r--r-- root root Feb : openssl-1.0.2r.tar.gz
-rwxr-xr-x root root Apr sshd
[root@testssh tools]# tar xfz openssh-.0p1.tar.gz
[root@testssh tools]# cd openssh-.0p1 可能文件默认显示uid和gid数组都是1000,这里重新授权下。不授权可能也不影响安装(请自行测试)
[root@testssh tools]# chown -R root.root /data/tools/openssh-.0p1
telnet 172.16.230.21
Connecting to 172.16.230.21:...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
SSH-2.0-OpenSSH_7.4
修改
[root@node1 openssh-.0p1]# vim version.h #define SSH_VERSION "SenyintSSH" #define SSH_PORTABLE ""
#define SSH_RELEASE SSH_VERSION SSH_PORTABLE
编译后,显示结果
telnet 172.16.230.21 Connecting to 172.16.230.21:...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
SSH-2.0-SenyintSSH
命令行删除原先ssh的配置文件和目录
然后配置、编译、安装
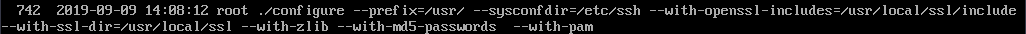
注意下面编译安装的命令是一行,请把第一行末尾的 \ 去掉,然后在文本里弄成一行之后放命令行执行
rm -rf /etc/ssh/* ./configure --prefix=/usr/ --sysconfdir=/etc/ssh --with-openssl-includes=/usr/local/ssl/include \
--with-ssl-dir=/usr/local/ssl --with-zlib --with-md5-passwords --with-pam && make && make install
参考下我的截图
修改配置文件最终为如下内容,其他的不要动
[root@linux-node3 ~]# grep "^PermitRootLogin" /etc/ssh/sshd_config
PermitRootLogin yes
[root@linux-node3 ~]# grep "UseDNS" /etc/ssh/sshd_config
UseDNS no
[root@linux-node3 ~]#
从原先的解压的包中拷贝一些文件到目标位置(如果目标目录存在就覆盖)
(可能下面的ssh.pam文件都没用到,因为sshd_config配置文件貌似没使用它,请自行测试。我这边是拷贝了)
[root@linux-node3 /data/tools/openssh-.0p1]# cp -a contrib/redhat/sshd.init /etc/init.d/sshd
[root@linux-node3 /data/tools/openssh-.0p1]# cp -a contrib/redhat/sshd.pam /etc/pam.d/sshd.pam
[root@linux-node3 /data/tools/openssh-.0p1]# chmod +x /etc/init.d/sshd [root@linux-node3 /data/tools/openssh-.0p1]# chkconfig --add sshd
[root@linux-node3 /data/tools/openssh-.0p1]# systemctl enable sshd
[root@linux-node3 /data/tools/openssh-.0p1]#
把原先的systemd管理的sshd文件删除或者移走或者删除,不移走的话影响我们重启sshd服务
[root@linux-node3 ~]# mv /usr/lib/systemd/system/sshd.service /data/
设置sshd服务开机启动
[root@linux-node3 ~]# chkconfig sshd on
Note: Forwarding request to 'systemctl enable sshd.socket'.
Created symlink from /etc/systemd/system/sockets.target.wants/sshd.socket to /usr/lib/systemd/system/sshd.socket.
接下来测试启停服务。都正常
以后管理sshd通过下面方式了
[root@linux-node3 ~]# /etc/init.d/sshd restart
Restarting sshd (via systemctl): [ OK ]
[root@linux-node3 ~]#
[root@linux-node3 ~]#
[root@linux-node3 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0.0.0.0: 0.0.0.0:* LISTEN /sshd
tcp6 ::: :::* LISTEN /sshd
tcp6 ::: :::* LISTEN /systemd
[root@linux-node3 ~]# /etc/init.d/sshd stop
Stopping sshd (via systemctl): [ OK ]
[root@linux-node3 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp6 ::: :::* LISTEN /systemd
[root@linux-node3 ~]# /etc/init.d/sshd start
Starting sshd (via systemctl): [ OK ]
[root@linux-node3 ~]#
[root@linux-node3 ~]#
使用systemd方式也行
[root@linux-node3 ~]# systemctl stop sshd
[root@linux-node3 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp6 ::: :::* LISTEN /systemd
[root@linux-node3 ~]# systemctl start sshd
[root@linux-node3 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0.0.0.0: 0.0.0.0:* LISTEN /sshd
tcp6 ::: :::* LISTEN /sshd
tcp6 ::: :::* LISTEN /systemd
[root@linux-node3 ~]# systemctl restart sshd
[root@linux-node3 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0.0.0.0: 0.0.0.0:* LISTEN /sshd
tcp6 ::: :::* LISTEN /sshd
tcp6 ::: :::* LISTEN /systemd
[root@linux-node3 ~]#
测试版本。都正常
[root@linux-node3 ~]# ssh -V
OpenSSH_8.0p1, OpenSSL 1.0.2r Feb
[root@linux-node3 ~]# [root@linux-node3 ~]# telnet 127.0.0.1
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
SSH-2.0-OpenSSH_8.
引用: https://www.cnblogs.com/nmap/p/10779658.html
centos7.6 升级openssh openssl的更多相关文章
- CentOS7.5升级OpenSSH
实验环境 OS:CentOS 7.5 当前openssh版本:OpenSSH_7.4p1 升级后的openssh版本:OpenSSH_8.0p1 开通telnet 为了防止升级过程中ssh断连,保险起 ...
- centos7 升级openssh到openssh-8.0p1版本
环境介绍 centos7.3和centos7.6升级完毕测试登录ssh以及重启后登录ssh均无问题. 前期请自行配置好yum源(如果不会请百度) 整个过程不需要卸载原先的openssl包和openss ...
- openssh/openssl升级到7.4和1.0.2j 源码方式
#!/bin/bashtar -xvf openssh-7.4p1.tar.gztar -xvf openssl-1.0.2j.tar.gz 升级 openssl 到1.0.2jcd openssl- ...
- 升级openssh基于openssl
OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It encrypts all tra ...
- 升级OPENSSH 和 OPENSSL
升级OPENSSH 和 OPENSSL 首先安装telnet服务,防止在操作过程中导致ssh远程中断 # 安装Telnetyum install telnet-server -y chkcon ...
- centos7升级openssh
注意: openssl版本(openssl版本要大于1.0.1,zlib版本要大于1.1.4) 一.安装依赖包 yum -y install gcc make perl # zlib zlib-dev ...
- CentOS 6.9 升级OpenSSH版本 关闭ssh服务后门
最近用低版本的OpenSSH(5.9p1版本) 的漏洞给系统留了个后门 , 可以劫持root密码或者给root开启后门密码 : 利用Openssh后门 劫持root密码 如果公司还在用CentOS6的 ...
- CentOS 升级 openSSH
openSSH作为linux远程连接工具,容易受到攻击,必须更新版本来解决,低版本有如下等漏洞: a. OpenSSH 远程代码执行漏洞(CVE-2016-10009) b. OpenSSH aut ...
- centos6升级openssh至7.9
1.为了防止升级失败登陆不了,所以需要安装telnet mkdir /root/ssh_updateyum install -y telnet-serveryum install -y xinetd ...
随机推荐
- BZOJ 3328: PYXFIB 单位根反演+矩阵乘法+二项式定理
如果写过 LJJ 学二项式那道题的话这道题就不难了. #include <bits/stdc++.h> #define ll long long #define setIO(s) freo ...
- ELK教程2:Kibana的安装
kibana作为ElastciSearch的数据查询展示界面,集成了很多的功能,本文主要讲述如下部署kibana. 安装 安装命令如下: # 下载kibana的npm wget https://art ...
- linux protobuf 测试官方例子遇到报错及解决办法。
测试例子时出现报错如下,在最下面会写出安装流程. -------------------------------------报错----1------------------------------- ...
- maven ssm 编译异常记录:
maven ssm 编译异常记录: javax.servlet.jsp 解决: 清除 tomacat libraries 修改 pom 文件 <dependency> <groupI ...
- 本地spark报:java.lang.UnsatisfiedLinkError: org.apache.hadoop.io.nativeio.NativeIO$Windows.createFileWithMode0(Ljava/lang/String;JJJI)Ljava/io/FileDescriptor;
我是在运行rdd.saveAsTextFile(fileName)的时候报的错,找了很多说法……最终是跑到hadoop/bin文件夹下删除了hadoop.dll后成功.之前某些说法甚至和这个解决方法自 ...
- ES6——class类继承(读书笔记)
前言 我一定是一个傻子,昨天这篇文章其实我已经写好了一半了,但是我没有保存 这是学习ES6的过程,我没有系统的看完阮大大的书.零零散散的,很多功能知道,但是没有实际的用过 看了几遍,总是看前面几章,所 ...
- Spring mybatis thymeleaf 基础操作,实现数据展示,修改,删除,查询
目录结构如图 index.html <!DOCTYPE html> <html lang="en" xmlns:th="http://www.thyme ...
- mac安装rust
1.安装 curl https://sh.rustup.rs -sSf | sh 使用brew各种出错,还慢. 2编译 source $HOME/.cargo/env 3.版本查看 rustc --v ...
- web前端兼容性问题
传送门:https://www.cnblogs.com/zhoudawei/p/7497544.html
- CSS(1)
使用CSS的注意点: 1.style标签必须写在head标签的开始标签和结束标签之间(也就是必须和title标签是兄弟关系). 2.style标签中的type属性其实可以不用写,默认就是type=&q ...