Lab 3-4
Analyze the malware found in the file Lab03-04.exe using basic dynamic analysis tools. (This program is analyzed further in the Chapter 9 labs.)
Questions and Short Answers
What happens when you run this file?
A: When you run this malware by double-clicking it, the program immediately deletes itself.
What is causing the roadblock in dynamic analysis?
A: We suspect that we may need to provide a command-line argument or a missing component to the program.
Are there other ways to run this program?
A: We try using the command-line parameters shown in the strings listing (like
-in), but doing so is not fruitful. More in-depth analysis is required. (We’ll analyze this malware further in the labs for Chapter 9.)
Detailed Analysis
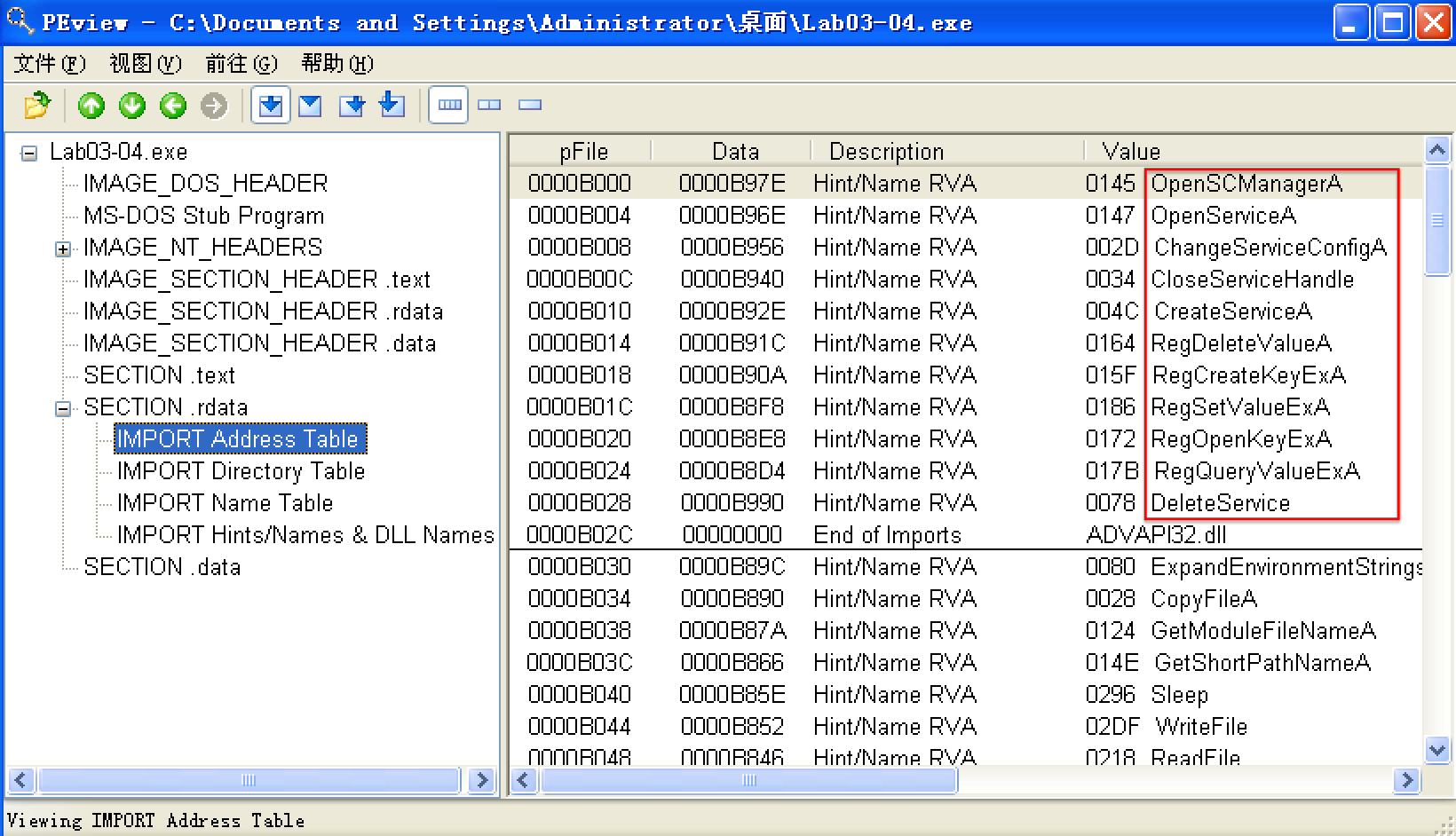
We begin with basic static analysis, examining the PE file structure and strings. We see that this malware imports networking functionality, service-manipulation functions, and registry-manipulation functions. In the following listing, we notice a number of interesting strings.
PEview
翻译版书1.3 查找字符串(英文版书,Part 1: Basic Analysis -> Finding Strings)
步骤:
下载Strings(英文原版书提供的链接好使,翻译版失效。)
cmd -> 进入下载的strings.exe可执行文件所在文件夹 -> 使用 strings 命令查看
C:\Documents and Settings\Administrator\桌面\杂\Strings>strings.exe "C:\Documents and Settings\Administrator\桌面\Lab03-04.exe"
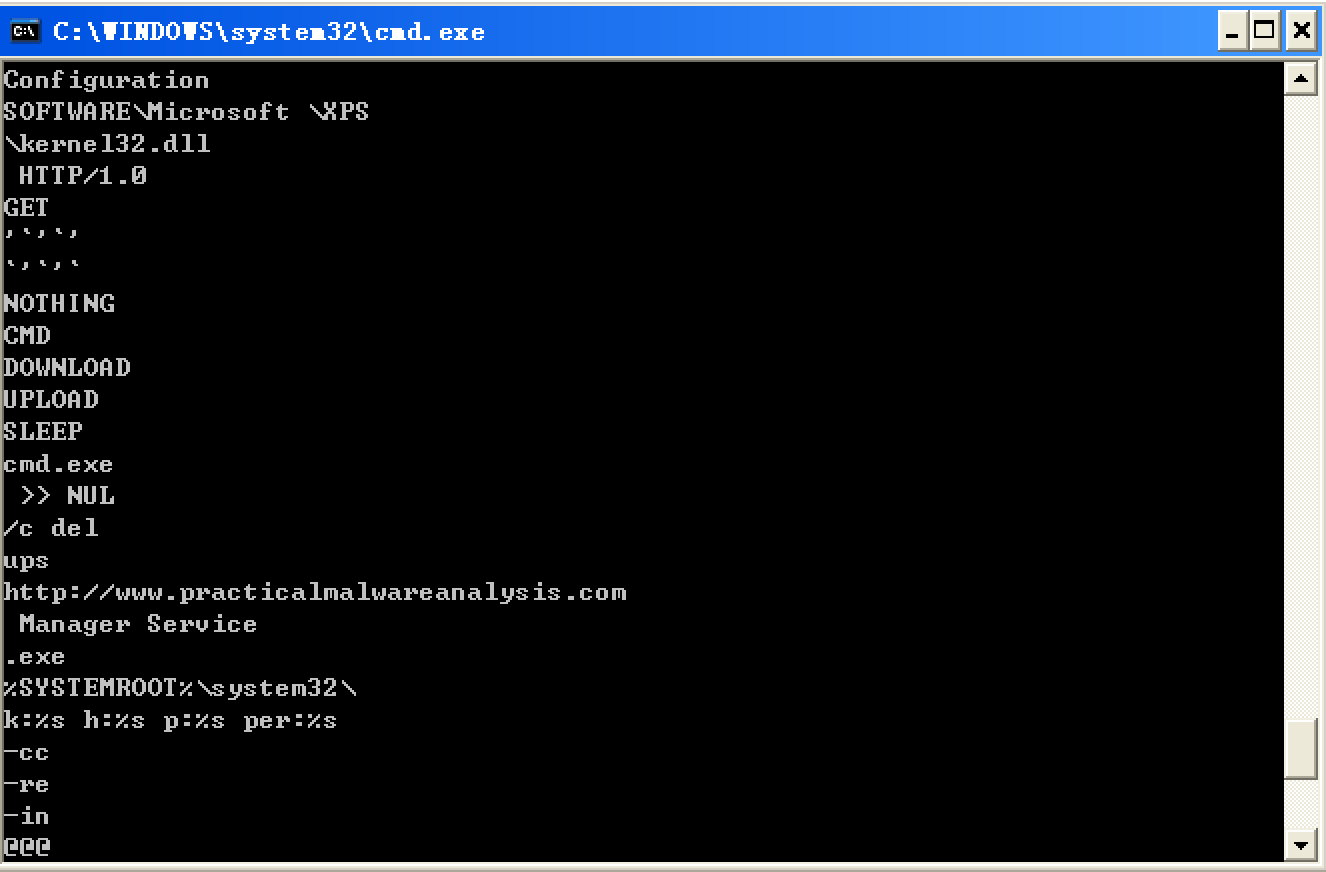
We see strings such as a domain name and the registry location SOFTWARE Microsoft \XPS. Strings like DOWNLOAD and UPLOAD, combined with the HTTP/1.0 string, suggest that this malware is an HTTP backdoor. The strings -cc, -re, and -in could be command-line parameters (for example -in may stand for install). Let’s see if basic dynamic techniques show us how these strings are used.
Before we run the malware, we run procmon and clear out all events, start Process Explorer, and set up a virtual network. When we run the malware, it appears to immediately delete itself, and we see nothing else of interest while watching with Process Explorer.
Next, we use procmon with a filter on the process name Lab03-04.exe. There aren’t any interesting WriteFile or RegSetValue entries, but upon further digging, we find an entry for Process Create. Double-clicking this entry brings up the dialog shown in Figure 3-11L, and we see that the malware is deleting itself from the system using "C:\WINDOWS\system32\cmd.exe" /c del Z: Lab03-04.exe >> NUL, as seen at \({\color{red}1}\).
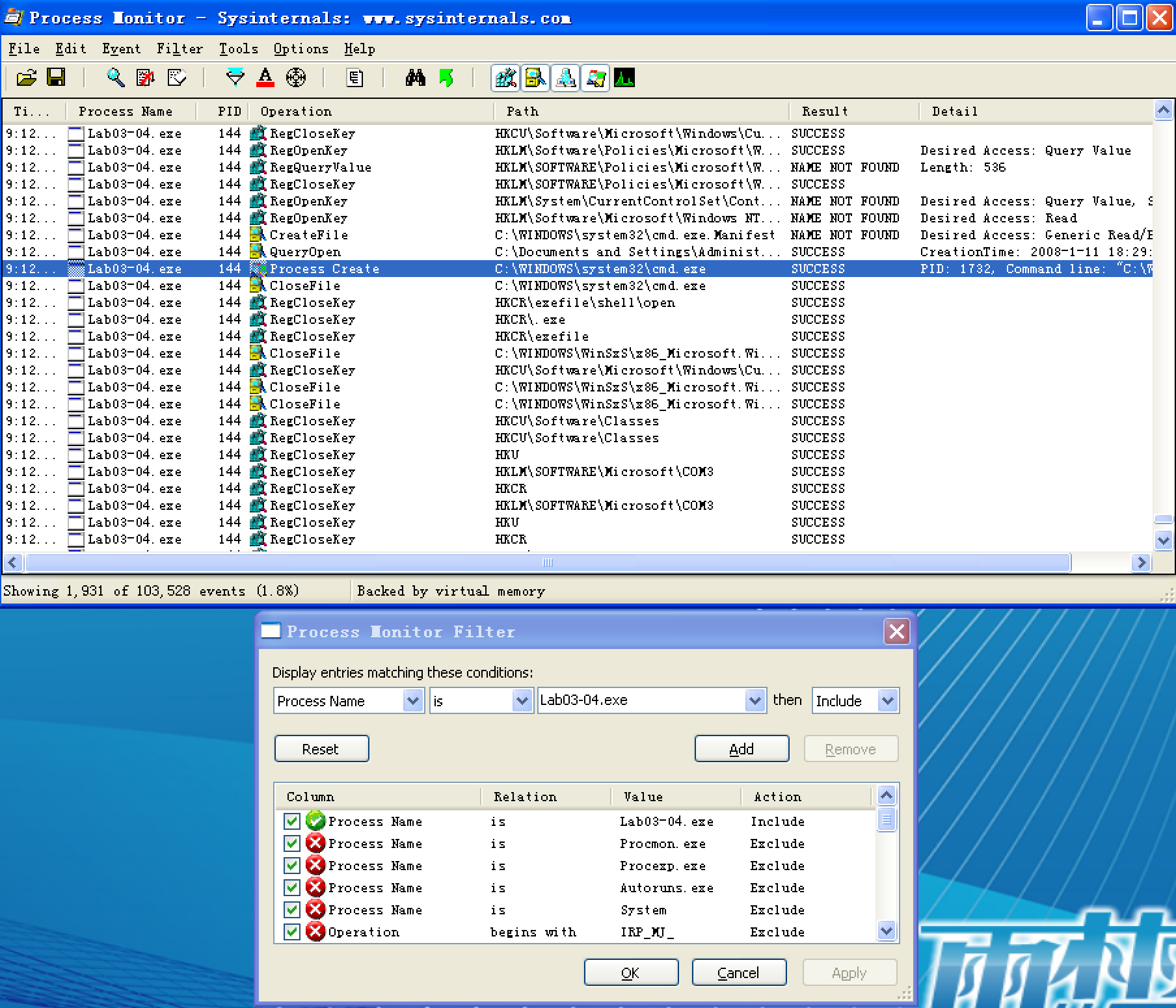
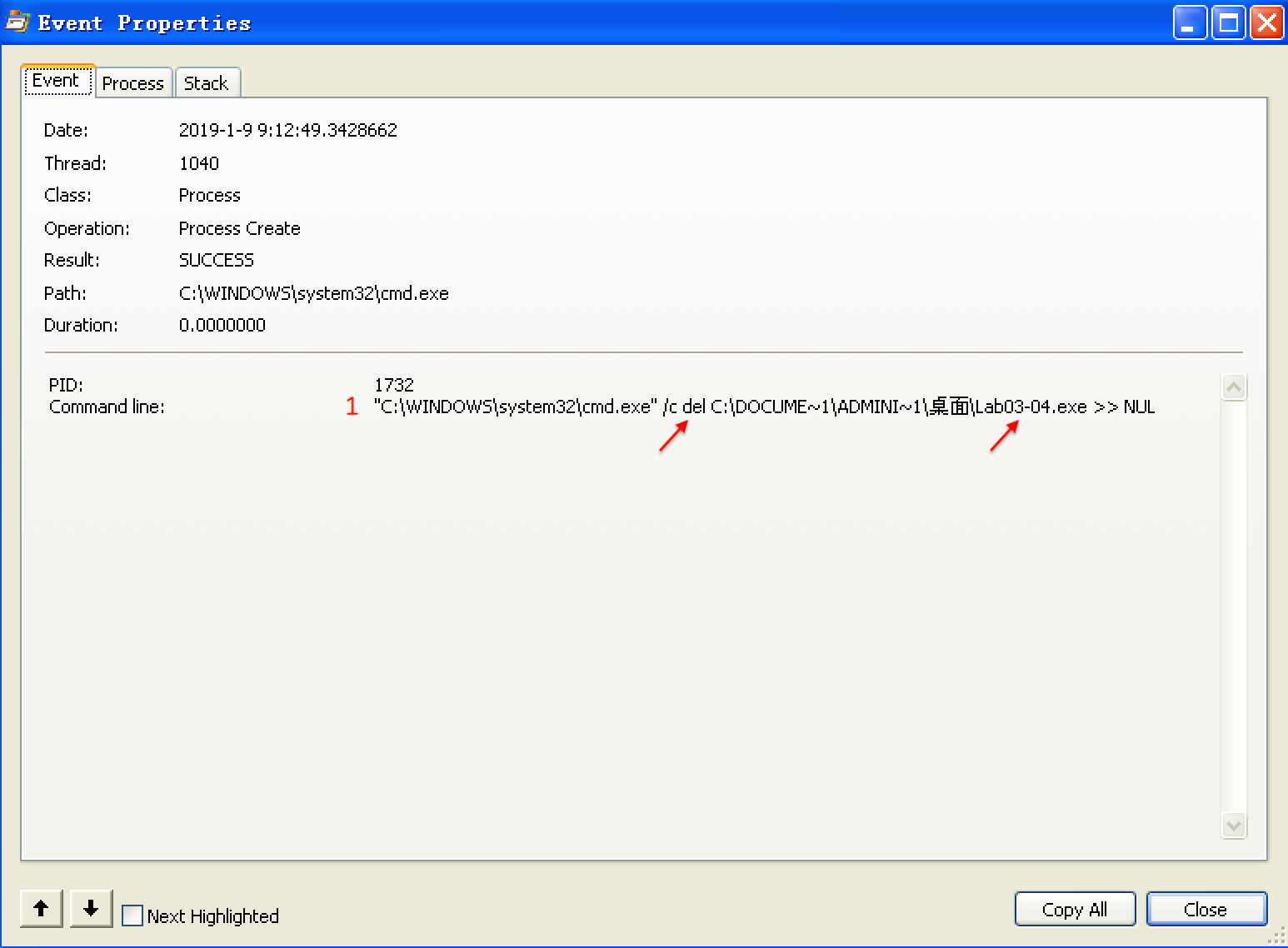
Figure 3-11L: Procmon view of the Process Create performed for self-deletion
We can try to run the malware from the command line using the command-line options we saw in the strings listing (-in, -re, and –cc), but all of them fail and result in the program deleting itself. There isn’t much more we can do with basic dynamic techniques at this point, until we dig deeper into the malware. (We will revisit this malware in the Chapter 9 labs.)
以选项 -in 试验,Lab03-04.exe 执行前:
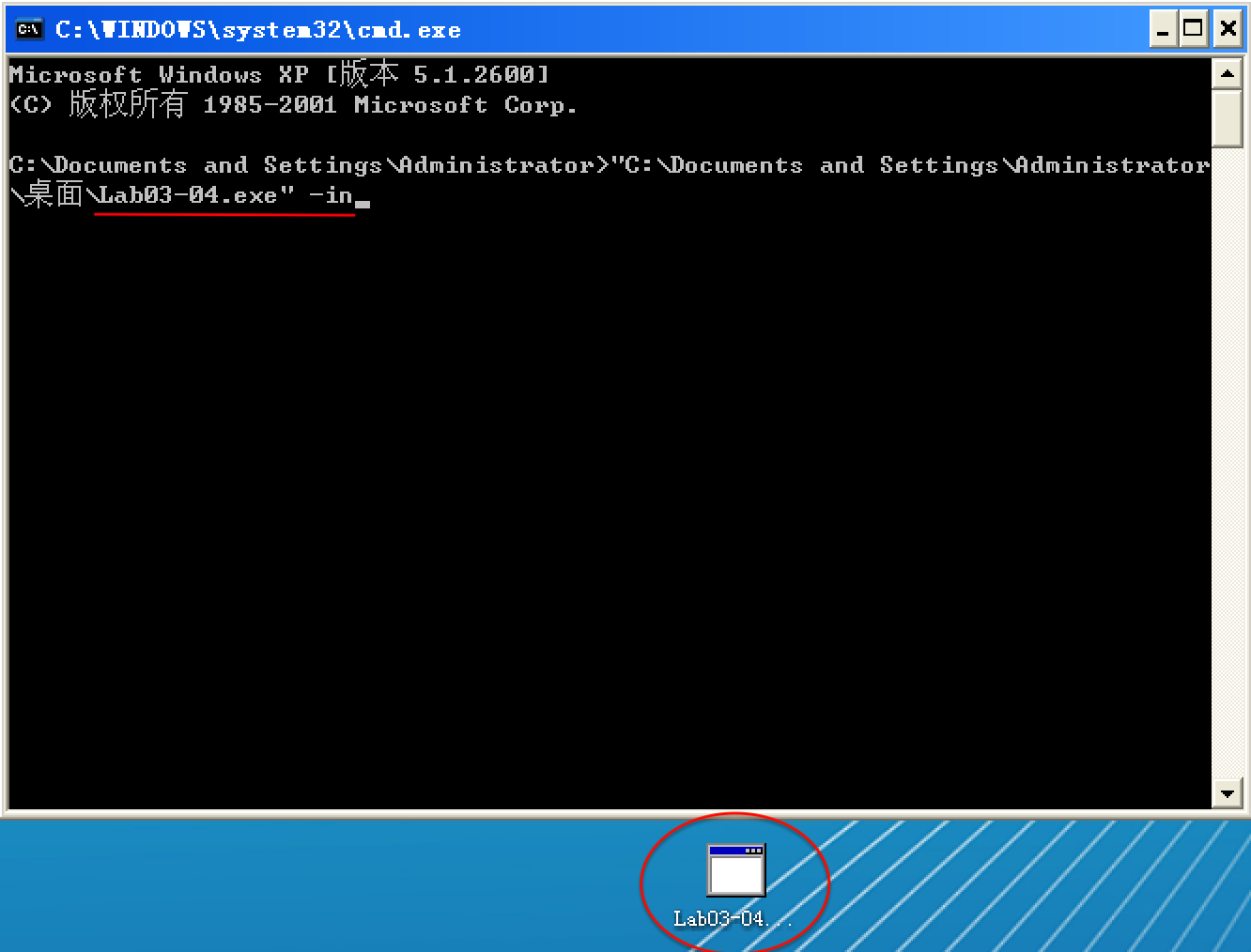
以选项 -in 试验,Lab03-04.exe 执行后:
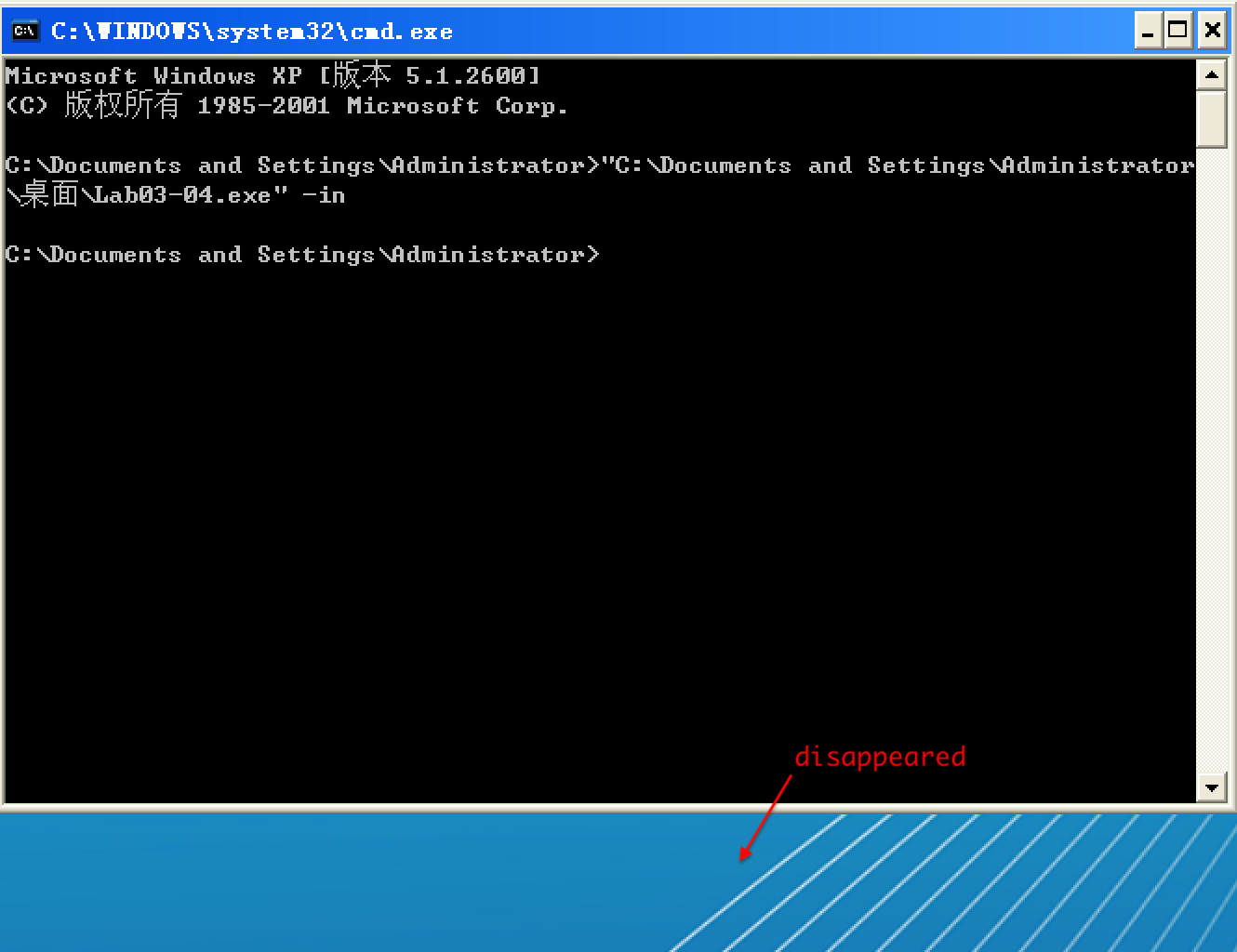
Preference
Lab 3-4的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- Python 读写文件 中文乱码 错误TypeError: write() argument must be str, not bytes+
今天写上传文件代码,如下 def uploadHandle(request): pic1=request.FILES['pic1'] picName=os.path.join(settings.MED ...
- php编程疑难解决-1
全局变量和超全局变量 如果是php脚本script 或php代码, 一定要放在 php标签内<?php ?> 内. 这样apache才会把他当做php脚本内容来解析, 才会去调用php模块 ...
- hihoCoder week13 最近公共祖先·一
用的dfs,自下往上搜索一个节点的所有祖先,然后在相应祖先 判断是否是另一个节点的祖先,如果是 就截止,否则继续往上搜索,直到搜索到,或者知道所有的祖先都被扫描完成 #include <bits ...
- oracle单行函数 之 时间函数
select systemdate from dual --得到时间 select systemdate+300 from dual --日期 +数字=日期,表示若干天之后的日期 select s ...
- Java中常用的方法
枚举: 1:DemoEnum.valueOf(String str) 从枚举类中中找字符串,如果有则返回对应枚举值 2:DemoEnum.values() 获得枚举集合 3:DemoEnum.prop ...
- NPOI 导入Excel和读取Excel
1.整个Excel表格叫做工作表:WorkBook(工作薄),包含的叫页(工作表):Sheet:行:Row:单元格Cell. 2.NPOI是POI的C#版本,NPOI的行和列的index都是从0开始 ...
- C# winform窗体间传值(使用委托或事件)
窗体间传值 今天得空,刚好看到网上好多人再找winform窗体间传值的问题,由于昨天项目的优化的感觉不错,就写了个C# winform窗体间传值的demo,希望能给需要的人的带来帮助: 工程的源代码地 ...
- 把一个List拆分为几个大小一样的List
static void Main(string[] args) { List<String> tarArr = new List<String>(); tarArr.Add(& ...
- 用python读写excel的强大工具:openpyxl
最近看到好几次群里有人问xlwt.wlrd的问题,怎么说呢,如果是office2007刚出来,大家用xlsx文件用不习惯,还可以理解,这都10年过去了喂,就算没有进化到office2016,还在用of ...
- JS快速构建数组方法
一.常用(普通)数组的构建 1.1 直接构建 let arr = ['mock1', 'mock2', 'mock3'] 1.2 通过new Array let arr = newArray('moc ...
