IP packet transmission using vehicular transport
In one embodiment, a first stationary router may detect a disconnected backhaul link to a destination. In response to detecting the disconnected backhaul link, the first stationary router may send a message to a first traveling mobile device, to cause the message to be sent toward the destination via a second stationary router. The second stationary router may receive the message from the first traveling mobile device, and in response to forwarding the message to the destination over its connected backhaul link, may send an acknowledgment toward the first stationary router via a second traveling mobile device. The first stationary router may then, in response to receiving the acknowledgment, cease sending copies of the message to other traveling mobile devices.
TECHNICAL FIELD
The present disclosure relates generally to computer networks, and, more particularly, to communicating messages from a field area router to a destination.
BACKGROUND
Field area routers (FARs) may be installed in strategic locations in order to communicate wirelessly with a variety of endpoints in a field area network (FAN), such as for utility grids (e.g., electric meters and distribution automation devices), vehicular communication, etc. Field area routers provide communication for the endpoints in the FAN to one or more destinations outside of the FAN (e.g., over the Internet), such as a control center, data collection sinks, etc. Typically, for communication outside of the FAN, FARs tend to use a backhaul link such as 3G/LTE, Wimax, or WiFi, which are not always reliable or may otherwise become temporarily or permanently disconnected. As such, a disconnected FAR may be unable to communicate messages over its backhaul link, which can be especially problematic for critical messages.
DESCRIPTION OF EXAMPLE EMBODIMENTS
Overview
According to one or more embodiments of the disclosure, a local stationary router may detect a disconnected backhaul link and may send a message (e.g., a critical message) to a first traveling mobile device, causing the message to be sent toward a destination via a remote stationary router. In response to receiving an acknowledgment from the remote stationary router, the local stationary router may cease sending copies of the message to other traveling mobile devices.
According to one or more additional embodiments of the disclosure, a local stationary router with a connected backhaul link may receive a message from a first traveling mobile device, where the message originated from a remote stationary router having a disconnected backhaul link. The local stationary router may forward the message to its destination over the connected backhaul link, and in response, the local stationary router may send an acknowledgment toward the remote stationary router via a second traveling mobile device.
Description
A computer network is a geographically distributed collection of nodes interconnected by communication links and segments for transporting data between end nodes, such as personal computers and workstations, or other devices, such as sensors, etc. Many types of networks are available, ranging from local area networks (LANs) to wide area networks (WANs). LANs typically connect the nodes over dedicated private communications links located in the same general physical location, such as a building or campus. WANs, on the other hand, typically connect geographically dispersed nodes over long-distance communications links, such as common carrier telephone lines, optical lightpaths, synchronous optical networks (SONET), synchronous digital hierarchy (SDH) links. In addition, a Mobile Ad-Hoc Network (MANET) is a kind of wireless ad-hoc network, which is generally considered a self-configuring network of mobile routes (and associated hosts) connected by wireless links, the union of which forms an arbitrary topology.
Smart object networks, such as sensor networks, in particular, are a specific type of network having spatially distributed autonomous devices such as sensors, actuators, etc., that cooperatively monitor physical or environmental conditions at different locations, such as, e.g., energy/power consumption, resource consumption (e.g., water/gas/etc. for advanced metering infrastructure or "AMI" applications) temperature, pressure, vibration, sound, radiation, motion, pollutants, etc and may improve field operations support. Other types of smart objects include actuators, e.g., responsible for turning on/off an engine or perform any other actions. Sensor networks, a type of smart object network, are typically shared-media networks, such as wireless. That is, in addition to one or more sensors, each sensor device (node) in a sensor network may generally be equipped with a radio transceiver or other communication port such as a microcontroller, and an energy source. Often, smart object networks are considered field area networks (FANs), neighborhood area networks (NANs), etc. Generally, size and cost constraints on smart object nodes (e.g., sensors) result in corresponding constraints on resources such as energy, memory, computational speed and bandwidth. Notably, the objects in such networks may be stationary or mobile.
As an example of a FAN involving both mobile and stationary devices, FIG. 1 is a schematic block diagram of an example simplified computer network 100illustratively comprising a plurality of stationary routers, such as field area routers (FARs) 300 and 410, as well as a plurality of mobile devices traveling within the vicinity of the FARs, such as devices 320 and 505 as shown. Each of the devices may be interconnected by various methods of communication (links), such as wired links or shared media (e.g., wireless links, etc.) where certain mobile devices may be in communication with a particular FAR based on distance, signal strength, current operational status, location, etc. In addition, the FARs may each be connected to one or more destination devices (e.g., a control center) 310 through a backhaul link 305 or 405, as shown. Those skilled in the art will understand that any number of nodes, devices, links, etc. may be used in the computer network, and that the view shown herein is for simplicity.
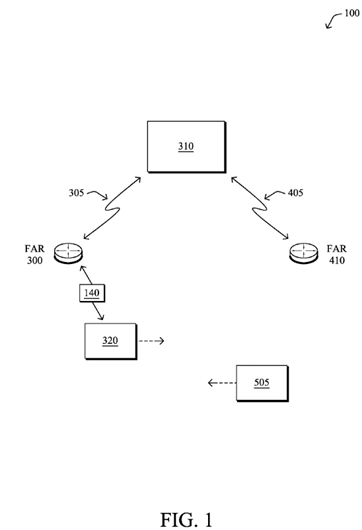
Data packets 140 (e.g., traffic and/or messages sent between the devices/nodes) may be exchanged among the nodes/devices of the computer network 100 using predefined network communication protocols such as certain known wired protocols, wireless protocols (e.g., IEEE Std. 802.15.4, WiFi, Bluetooth®, etc.), or other shared-media protocols where appropriate. In this context, a protocol consists of a set of rules defining how the nodes interact with each other.
FIG. 2 is a schematic block diagram of an example simplified node/device 200that may be used with one or more embodiments described herein, e.g., as any of the nodes shown in FIG. 1 above. The device may comprise one or more network interfaces 210 (e.g., wired, wireless, etc.), at least one processor 220, and a memory 240 interconnected by a system bus 250, as well as a power supply 260 (e.g., battery, plug-in, etc.).

The network interface(s) 210 contain the mechanical, electrical, and signaling circuitry for communicating data over links coupled to the network 100. The network interfaces may be configured to transmit and/or receive data using a variety of different communication protocols. Note, further, that certain nodes, particularly the FARs, may have two different types of network connections 210, e.g., wireless (both for the FAN of mobile devices as well as a backhaul link) and wired/physical connections (e.g., for a certain embodiment of the backhaul link), and that the view herein is merely for illustration.
The memory 240 comprises a plurality of storage locations that are addressable by the processor 220 and the network interfaces 210 for storing software programs and data structures associated with the embodiments described herein. The processor 220 may comprise hardware elements or hardware logic adapted to execute the software programs and manipulate the data structures245. An operating system 242, portions of which are typically resident in memory240 and executed by the processor, functionally organizes the device by, inter alia, invoking operations in support of software processes and/or services executing on the device. These software processes and/or services may comprise routing process/services 244, and an illustrative communication process 248, as described herein. Note that while communication process 248 is shown in centralized memory 240, alternative embodiments provide for the process to be specifically operated within the network interfaces 210, (process "248 a").
It will be apparent to those skilled in the art that other processor and memory types, including various computer-readable media, may be used to store and execute program instructions pertaining to the techniques described herein. Also, while the description illustrates various processes, it is expressly contemplated that various processes may be embodied as modules configured to operate in accordance with the techniques herein (e.g., according to the functionality of a similar process). Further, while the processes have been shown separately, those skilled in the art will appreciate that processes may be routines or modules within other processes.
Routing process (services) 244 contains computer executable instructions executed by the processor 220 to perform functions provided by one or more routing protocols, such as proactive or reactive routing protocols as will be understood by those skilled in the art. These functions may, on capable devices, be configured to manage a routing/forwarding table (a data structure 245) containing, e.g., data used to make routing/forwarding decisions. In particular, in proactive routing, connectivity is discovered and known prior to computing routes to any destination in the network, e.g., link state routing such as Open Shortest Path First (OSPF), or Intermediate-System-to-Intermediate-System (ISIS), or Optimized Link State Routing (OLSR). Reactive routing, on the other hand, discovers neighbors (i.e., does not have an a priori knowledge of network topology), and in response to a needed route to a destination, sends a route request into the network to determine which neighboring node may be used to reach the desired destination. Example reactive routing protocols may comprise Ad-hoc On-demand Distance Vector (AODV), Dynamic Source Routing (DSR), DYnamic MANET On-demand Routing (DYMO), etc. Notably, on devices not capable or configured to store routing entries, routing process 244 may consist solely of providing mechanisms necessary for source routing techniques. That is, for source routing, other devices in the network can tell the less capable devices exactly where to send the packets, and the less capable devices simply forward the packets as directed.
Notably, mesh networks have become increasingly popular and practical in recent years. In particular, shared-media mesh networks, such as wireless networks, are often on what is referred to as Low-Power and Lossy Networks (LLNs), which are a class of network in which both the routers and their interconnect are constrained: LLN routers typically operate with constraints, e.g., processing power, memory, and/or energy, and their interconnects are characterized by, illustratively, high loss rates, low data rates, and/or instability. LLNs are comprised of anything from a few dozen and up to thousands or even millions of LLN routers, and support point-to-point traffic (between devices inside the LLN), point-to-multipoint traffic (from a central control point such at the root node to a subset of devices inside the LLN) and multipoint-to-point traffic (from devices inside the LLN towards a central control point).
An example implementation of LLNs is an "Internet of Things" network. Loosely, the term "Internet of Things" or "IoT" may be used by those in the art to refer to uniquely identifiable objects (things) and their virtual representations in a network-based architecture. In particular, the next frontier in the evolution of the Internet is the ability to connect more than just computers and communications devices, but rather the ability to connect "objects" in general, such as lights, appliances, vehicles, HVAC (heating, ventilating, and air-conditioning), windows and window shades and blinds, doors, locks, etc. The "Internet of Things" thus generally refers to the interconnection of objects (e.g., smart objects), such as sensors and actuators, over a computer network (e.g., IP), which may be the Public Internet or a private network. Such devices have been used in the industry for decades, usually in the form of non-IP or proprietary protocols that are connected to IP networks by way of protocol translation gateways. With the emergence of a myriad of applications, such as the smart grid, smart cities, and building and industrial automation, and cars (e.g., that can interconnect millions of objects for sensing things like power quality, tire pressure, and temperature and that can actuate engines and lights), it has been of the utmost importance to extend the IP protocol suite for these networks.
As an illustrative IoT implementation, with the sharp increase of vehicles on roads in the recent years, leading car manufacturers decided to jointly work with national government agencies to develop solutions aimed at helping drivers on the roads by anticipating hazardous events or avoiding bad traffic areas. One of the outcomes has been a new type of wireless access called Wireless Access for Vehicular Environment (WAVE) dedicated to vehicle-to-vehicle and vehicle-to-roadside communications. While the major objective has clearly been to improve the overall safety of vehicular traffic, promising traffic management solutions and on-board entertainment applications are also expected in this field. For instance, when equipped with WAVE communication devices, cars and roadside units (RSUs) form a highly dynamic network called a Vehicular Ad Hoc Network (VANET), a special kind of Mobile Ad Hoc Network (MANET) where vehicles communicate with one another through wireless infrastructures to the Internet using a multihop-to-infrastructure routing protocol.
As an example, FIG. 1 may specifically illustrate a simplified VANET scenario, where a plurality of vehicles (mobile devices320 and 505, such as cars, trucks, etc.) may be in proximity to one another, while traveling at different speeds and directions. Also, one or more RSUs (e.g., FARs 300 and 410) may also be present along side the roadway, whether placed specifically for the purpose of vehicular communication (e.g., highways), or else another roadside unit configuration, such as a WiFi hotspot in the city.
As noted above, FARs seeking to communicate with a destination, such as a control center, may lose connectivity of their backhaul link, such as a 3G/LTE, Wimax, or WiFi link. For example, the backhaul link may be generally unreliable and may suffer from temporary outages, or else may have been physically disconnected or tampered with. At such times, the FAR would be unable to transmit messages over the backhaul link, which may be particularly detrimental where such messages are critical, such as messages indicating the disconnected state, other failure or alarm conditions, etc.
IP Packet Transmission Using Mobile Devices
The techniques herein allow for reliable transmission of IP packets via mobile devices, such as vehicles. In particular, according to the techniques herein, a disconnected FAR may send a message to a destination, such as a control center, via traveling vehicles. The message may be sent from the traveling vehicle to a connected FAR, which then relays the message to the destination. In response to sending the message to the destination, the connected FAR may send an acknowledgment to the disconnected FAR (e.g., again using a mobile device in the opposite direction), preventing duplicate copies of the message.
Illustratively, the techniques described herein may be performed by hardware, software, and/or firmware, such as in accordance with the communication process 248/248 a, which may contain computer executable instructions executed by the processor 220 (or independent processor of interfaces 210) to perform functions relating to the techniques described herein, e.g., in conjunction with routing process 244. For example, the techniques herein may be treated as extensions to conventional protocols, such as the various wireless communication protocols, and as such, may be processed by similar components understood in the art that execute those protocols, accordingly.
Operationally, the techniques herein allow for a field router with a disconnected backhaul link to compose and transmit a message to a destination, illustratively through vehicular transport. As illustrated in FIG. 3, in the event that a field area router (FAR) 300 loses connectivity to its backhaul link 305 to a destination 310 and the now-disconnected FAR 300 has a message 315 to send to the destination, a mobile device 320 may be used to transmit the message 315 according to the techniques herein. In particular, once the FAR (300) locates a mobile device (e.g., a vehicle), the message may be transmitted to the mobile device 320 in hopes that the mobile device will reach a remote connected FAR, as described below.
In one embodiment, the destination that the disconnected FAR 300 is attempting to send a message to may be a control center or a network management station. For instance, the message may be a critical message, such as a door open alarm, detection of an attempt to tamper, notification of the failed backhaul link, etc. Alternatively or in addition, the message may simply be any desired message, such as measurement data, diagnostic data, system status data, etc. Note that the message 315 may be transmitted to the destination 310 securely, such as by encrypting it with a key shared with the destination 310 where an intended server may decrypt the message and take appropriate action. Furthermore, the messages sent toward the destination may include identifiers indicating which FAR sent the message toward the destination, such that when multiple FARs send messages to multiple mobile devices (e.g., when there is a regional disturbance to multiple backhaul links simultaneously), the identifiers would allow distinguishing between multiple copies of the same message and different messages sent from different FARs.
In certain embodiments, as shown in FIG. 3A, once the FAR 300 sends the message 315 to the mobile device, the FAR300 may set a timer 301. The timer may be set so that a second message may be sent out within a predefined period of time, without having received an acknowledgment for the first message, as described below. Note that the timer for additional messages may be set to a fixed value or an exponentially decreasing value (e.g., a back-off timer). In this manner, the timer 301 prevents the FAR 300 from attempting to send the message 315 to each traveling device, thereby preventing an overload at the intended destination or remote connected FAR. Note that the number of additional copies to send may be set to a specific (fixed) value, or set to infinite to continue sending messages until the message is successfully received by a connected FAR 410 (or else the backhaul link is restored on the disconnected FAR 300).

According to the techniques herein, the mobile device 320 hopefully travels to a remote FAR 410 having a backhaul connectivity (link 405) to the destination 310, as illustrated in FIG. 4. In particular, the mobile device 320 may locate a FAR and sends the message 315 to the FAR 410, accordingly. Notably, in one embodiment the remote FAR 410 may indicate that it is connected via a backhaul link in order for the mobile device to transmit the carried message 315, however in other embodiments the mobile device may simply transmit the message to the first FAR encountered in its travels. In response to receiving the message 315 from the traveling mobile device 320, the connected FAR 410 may then send the message 315to the destination, as further illustrated in FIG. 5. (In the event the mobile device 320 does not reach a connected FAR, e.g., within some configured time limit prior to dropping the message, the disconnected FAR 300 would have sent additional copies of the message 320, as mentioned above.)

According to one or more embodiments herein, the FAR 410 with the operational backhaul link may, in response to sending the message 315 to the destination 310, send an acknowledgment message 500 back to the disconnected FAR 300. For instance, as further illustrated in FIG. 5, the acknowledgment message 500 may be sent back to the disconnected FAR 300via another traveling mobile device 505. The mobile device 505 carrying the acknowledgment message 500 would need to travel in a direction opposite from the mobile device 320 that carried the original message 315 toward the destination 310. Accordingly, in one embodiment, the connected FAR 410 may determine the direction of the first device 320, and may select the acknowledgment return device 505 based on it traveling in a substantially opposite direction. Alternatively, the acknowledging FAR 410 may send a plurality of messages in hopes that one or more will reach the disconnected FAR 300. In still another embodiment, the connected FAR 410 may continue to send acknowledgments only for as long as it continues to receive copies of the same message 315 from the disconnected FAR 300, implying that the disconnected FAR 300 has yet to receive the acknowledgment 500.

In particular, in response to receiving the acknowledgment message 500, the disconnected FAR 300 may cease sending any copies of the message 315 toward the destination 310, particularly via mobile devices. That is, if the disconnected FAR300 does not receive an acknowledgment message 500, such as before the timer 301 expires, the disconnected FAR 300may send a copy of the message to another traveling mobile device.
Note that as shown in FIG. 6, should the backhaul link 305 of the disconnected FAR 300 be restored prior to reception of the acknowledgment 500, the FAR 300 may send the message 315 over the connected backhaul link. In one embodiment, the message 315 over the connected backhaul link 305 may include an indication to indicate potential copies of the message 315 from one or more remote FARs according to the techniques above, such as by setting a newly defined flag of an IPv6 ho-by-hop header.

Note that while certain embodiments are described above, other enhancements may be made to the techniques herein depending upon device capability. For instance, if the traveling mobile device 320 carrying the message 315 detects that another mobile device may reach the destination first, the first mobile device 320 may pass the message along to the faster traveling mobile device. Additionally, the disconnected stationary router may detect the vehicle's direction or even ultimate destination, and determines whether to send the message to an alternative vehicle depending on the direction being toward another known FAR in the network 100.
FIG. 7 illustrates an example simplified procedure 700 for transmitting an IP packet from a disconnected router to a destination using a mobile device in accordance with one or more embodiments described herein, particularly from the perspective of a disconnected FAR. The procedure 700 may start at step 705, and continues to step 710, where, as described in greater detail above, a stationary router 300 detects a disconnected backhaul link 305 to a destination 310, where the stationary router has a message 315 to send to the destination. In order to reach the destination, in step 715, the stationary router sends the message to a traveling mobile device 320, to cause the message to be (hopefully) sent toward the destination. As described above, the mobile device may store the message in a local memory while traveling and thus transporting the message to a remote stationary router (e.g., connected FAR 410).

In response to not receiving an acknowledgment in step 720, then in step 725 the disconnected stationary router may continue to send additional copies of the message to other traveling mobile devices, to hopefully cause a copy of the message to be sent toward the destination. For instance, as noted above, a timer may be set such that it may be determined whether the acknowledgment is received by expiration of the timer. If an acknowledgment is received in step720, however, then in step 730 the disconnected FAR may cease sending additional copies of the message to other traveling mobile devices. The illustrative procedure may then end in step 735.
In addition, FIG. 8 illustrates another example simplified procedure 800 for transmitting an IP packet from a disconnected router to a destination using a mobile device in accordance with one or more embodiments described herein, particularly from the perspective of a connected FAR. The procedure 800 may start at step 805, and continues to step 810, where, as described in greater detail above, a local stationary router (e.g., FAR 410) receives a message 315 from a first traveling mobile device 320, wherein the message originated from a remote stationary router (e.g., disconnected FAR 300). In step815, the local stationary router forwards the message to the intended destination 310 over its connected backhaul link 405. In response to forwarding the message, in step 820 the local stationary router sends an acknowledgment 500 toward the remote (disconnected) stationary router via a second traveling mobile device 505. For instance, as mentioned above, it may be first determined that the second traveling mobile device is traveling in a direction opposite from the first traveling mobile device. The illustrative procedure may end in step 825.

It should be noted that while certain steps within procedures 700 and 800 may be optional as described above, the steps shown in FIGS. 7-8 are merely examples for illustration, and certain other steps may be included or excluded as desired. Further, while a particular order of the steps is shown, this ordering is merely illustrative, and any suitable arrangement of the steps may be utilized without departing from the scope of the embodiments herein. Moreover, while procedures 700 and800 are described separately, certain steps from each procedure may be incorporated into each other procedure, and the procedures are not meant to be mutually exclusive.
The techniques described herein, therefore, provide for transmitting an IP packet from a disconnected router to a destination using a mobile device. In particular, the techniques herein provide for a reliable message transmission process with an acknowledgment messaging system (e.g., a bi-directional communication system), avoiding duplication of critical messages from a stranded (disconnected) stationary router. For instance, without the acknowledgment, the connected FAR and/or control center may become overloaded with duplicate messages from the stranded FAR. In addition, the techniques may also provide for additional network security by allowing critical messages to reach the intended destination through mobile transmission, such as when an attacker has purposefully disconnected the backhaul link (e.g., physically or through jamming techniques).
While there have been shown and described illustrative embodiments that provide for transmitting an IP packet from a disconnected router to a destination using a mobile device, it is to be understood that various other adaptations and modifications may be made within the spirit and scope of the embodiments herein. For example, the embodiments herein have been generally described in terms of vehicular transport of the packets. However, the embodiments in their broader sense are not as limited, and may, in fact, be used with other types of mobile device transport, such as personal devices (e.g., smartphones, tablets). In addition, while certain protocols are shown, other suitable protocols may be used, accordingly. Also, while the techniques generally describe the backhaul link as a wireless backhaul link (e.g., 3G/LTE, Wimax, WiFi, etc.), one or more of the backhaul links may in fact be a wired link, where disconnection could imply hardware or software failure of the link.
SRC=https://www.google.com/patents/US20140126348
IP packet transmission using vehicular transport的更多相关文章
- Method of packet transmission from node and content owner in content-centric networking
A method of transmitting a content reply packet from a content owner in content-centric networking ( ...
- TCP-IP Architecture and IP Packet
Why Internet working? To build a "network of networks" or internet. operating over multipl ...
- Linux内核--网络栈实现分析(四)--网络层之IP协议(上)
本文分析基于Linux Kernel 1.2.13 原创作品,转载请标明http://blog.csdn.net/yming0221/article/details/7514017 更多请看专栏,地址 ...
- IP, TCP, and HTTP--reference
IP, TCP, and HTTP Issue #10 Syncing Data, March 2014 By Daniel Eggert When an app communicates with ...
- TCP/IP协议栈与数据报封装
一.ISO/OSI参考模型 OSI(open system interconnection)开放系统互联模型是由ISO(International Organization for Standardi ...
- TCP/IP协议栈与数据报封装 (802.3 Ethernet 以太网 802.11 WLAN 无线网 )
http://blog.csdn.net/jnu_simba/article/details/8957242 一.ISO/OSI参考模型 OSI(open system interconnection ...
- Method of offloading iSCSI TCP/IP processing from a host processing unit, and related iSCSI TCP/IP offload engine
A method of offloading, from a host data processing unit (205), iSCSI TCP/IP processing of data stre ...
- 计算机网络基础之TCP/IP 协议栈
计算机网络基础之TCP/IP 协议栈 作者:尹正杰 版权声明:原创作品,谢绝转载!否则将追究法律责任. 一.TCP/IP 协议栈概述 1>.什么是TCP/IP协议栈 Transmission C ...
- 数据包接收系列 — IP协议处理流程(一)
本文主要内容:在接收数据包时,IP协议的处理流程. 内核版本:2.6.37 Author:zhangskd @ csdn blog IP报头 IP报头: struct iphdr { #if defi ...
随机推荐
- linux中获取系统时间 gettimeofday函数
linux的man页中对gettimeofday函数的说明中,有这样一个说明: $ man gettimeofday DESCRIPTION The functions gettimeof ...
- thinkphp3.1课程 1-2 thinkphp中入口文件的实质是什么
thinkphp3.1课程 1-2 thinkphp中入口文件的实质是什么 一.总结 一句话总结:在thinkphp中,我们访问的始终是入口文件,并没有主动去访问任何一个其他文件,只不过在入口文件体内 ...
- win32程序如何改变字体大小颜色
//设定文字大小和颜色 LOGFONT logfont; //改变输出字体 ZeroMemory(&logfont, sizeof(LOGFONT)); logfont.lfCharSet = ...
- 解决java中ZipFile解压缩时候的中文路径和乱码问题
JAVA中对jar文件或zip文件解压的时候,能够使用JDK内置的API:JarFile和ZipFile,在windows下解压这2种格式文件的时候,常常报下面错误: Exception in thr ...
- jquery简单使用(看教程:快全有实例)(固定样式:$().val()设置属性,$().click()设置方法)
jquery简单使用(看教程:快全有实例)(固定样式:$().val()设置属性,$().click()设置方法) 一.总结 1.jquery不懂之处直接看教程,案例都有,有简单又快 2.jquery ...
- 【C++竞赛 D】树的深度
时间限制:1s 内存限制:32MB 问题描述 数据结构中定义,树的高度为一棵树中所有节点的层次的最大值.现在yyy有一棵树请你帮他求出该树的高度. 输入描述 第一行一个整数T(1≤T≤20)表示数据组 ...
- 全栈JavaScript之路( 二十五 )訪问元素的样式
不论什么支持style 特性的元素在 ,在其DOM 节点 对象中都有一个 style 属性与之相应. 这个style 对象是 CSSStyleDeclaration类型的实例,包括着html sty ...
- dom对象常用的属性和方法有哪些?
dom对象常用的属性和方法有哪些? 一.总结 一句话总结: 1.document属性和方法:document的属性有head,body之类,方法有各种获取element的方法 2.element的属性 ...
- html常用样式margin、border怎么使用
html常用样式margin.border怎么使用 一.总结 一句话总结:1.margin:auto配合width才能居中:2.border的三个属性依次是边框宽度,边框样式,边框颜色 1.html中 ...
- 理解Erlang/OTP - Application
http://www.cnblogs.com/me-sa/archive/2011/12/27/erlang0025.html 1>application:start(log4erl). 我们就 ...
