Lab 1-1
LABS
The purpose of the labs is to give you an opportunity to practice the skills taught in the chapter. In order to simulate realistic malware analysis you will be given little or no information about the program you are analyzing. Like all of the labs throughout this book, the basic static analysis lab files have been given generic names to simulate unknown malware, which typically use meaningless or misleading names.
Each of the labs consists of a malicious file, a few questions, short answers to the questions, and a detailed analysis of the malware. The solutions to the labs are included in Appendix C.
The labs include two sections of answers. The first section consists of short answers, which should be used if you did the lab yourself and just want to check your work. The second section includes detailed explanations for you to follow along with our solution and learn how we found the answers to the questions posed in each lab.
Lab 1-1
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
Questions and Short Answers
Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
A: These files were written specifically for this book, so as of this writing, you should not find a signature for them on VirusTotal.com. Of course, if these files become part of the antivirus signatures as a result of the publication of this book, the results will be different.
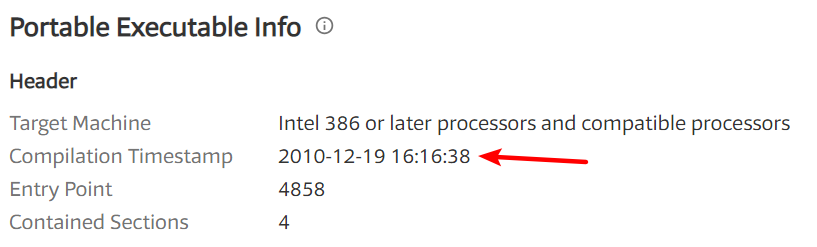
When were these files compiled?
A: Both files were compiled on December 19, 2010, within 1 minute of each other.
在 VT(http://www.VirusTotal.com/)中查看的结果如下:
Lab01-01.exe:
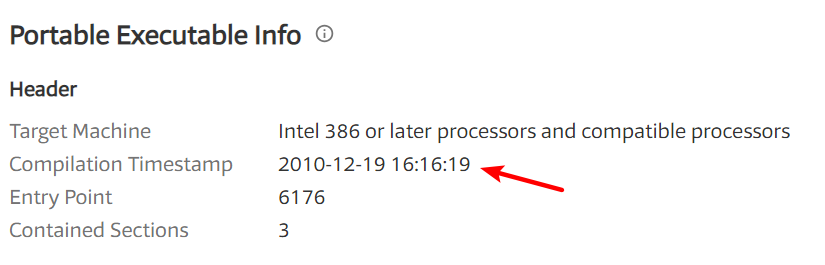
Lab01-01.dll:
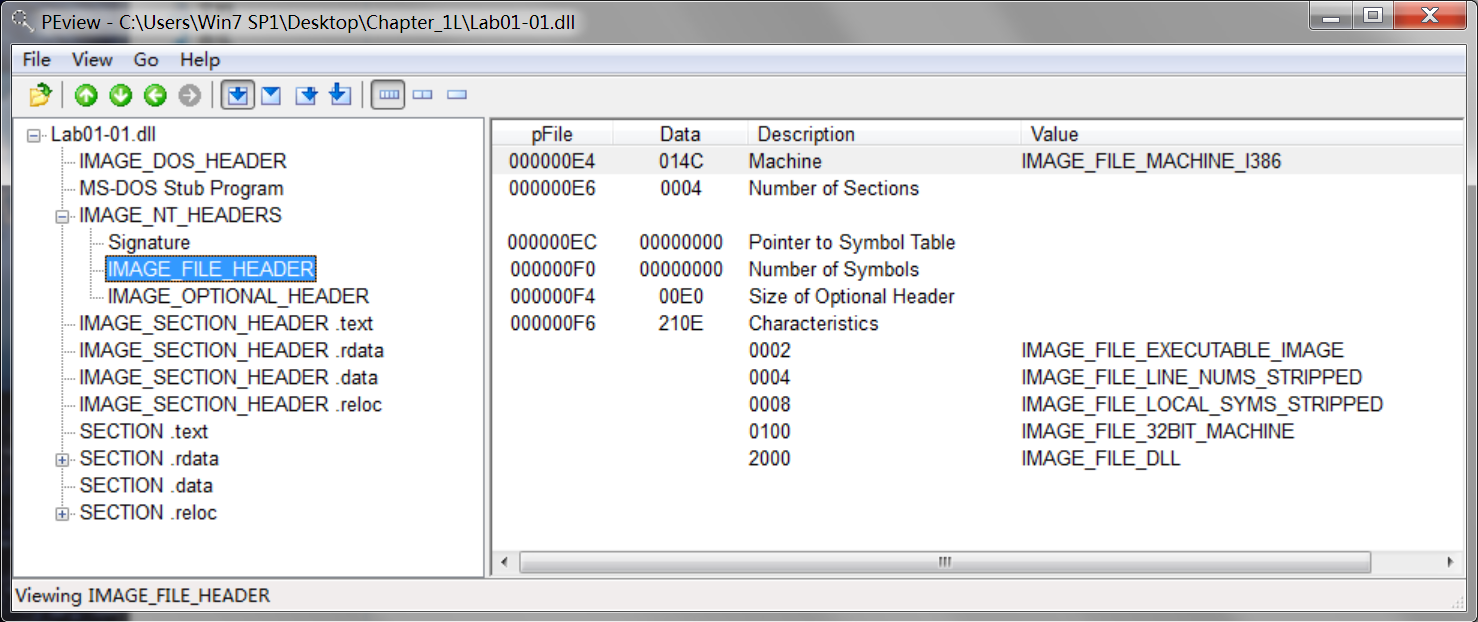
使用 PEview 软件查看如下:
Lab01-01.exe:
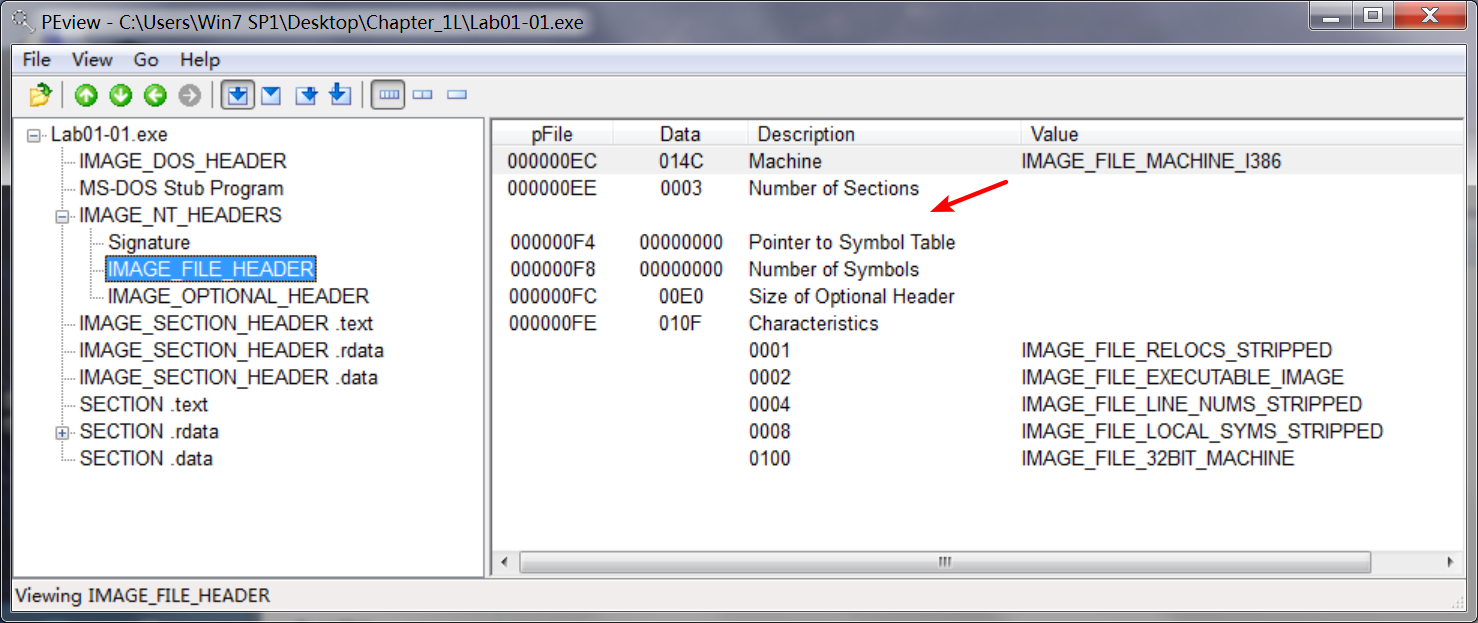
本该在箭头处显示,却为空。
Lab01-01.dll:
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
A: There are no indications that either file is packed or obfuscated.
查看是否加壳可以用PEiD软件:
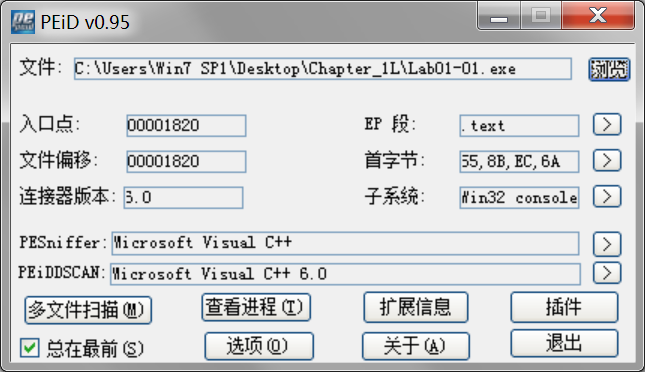
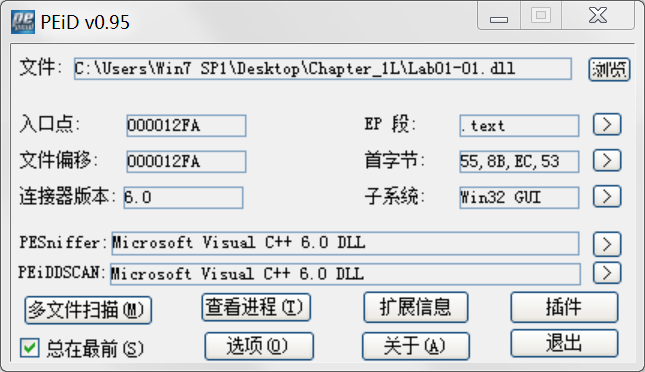
Do any imports hint at what this malware does? If so, which imports are they?
A: The interesting imports from Lab01-01.exe are FindFirstFile, FindNextFile, and CopyFile. These imports tell us that the program searches the file-system and copies files.
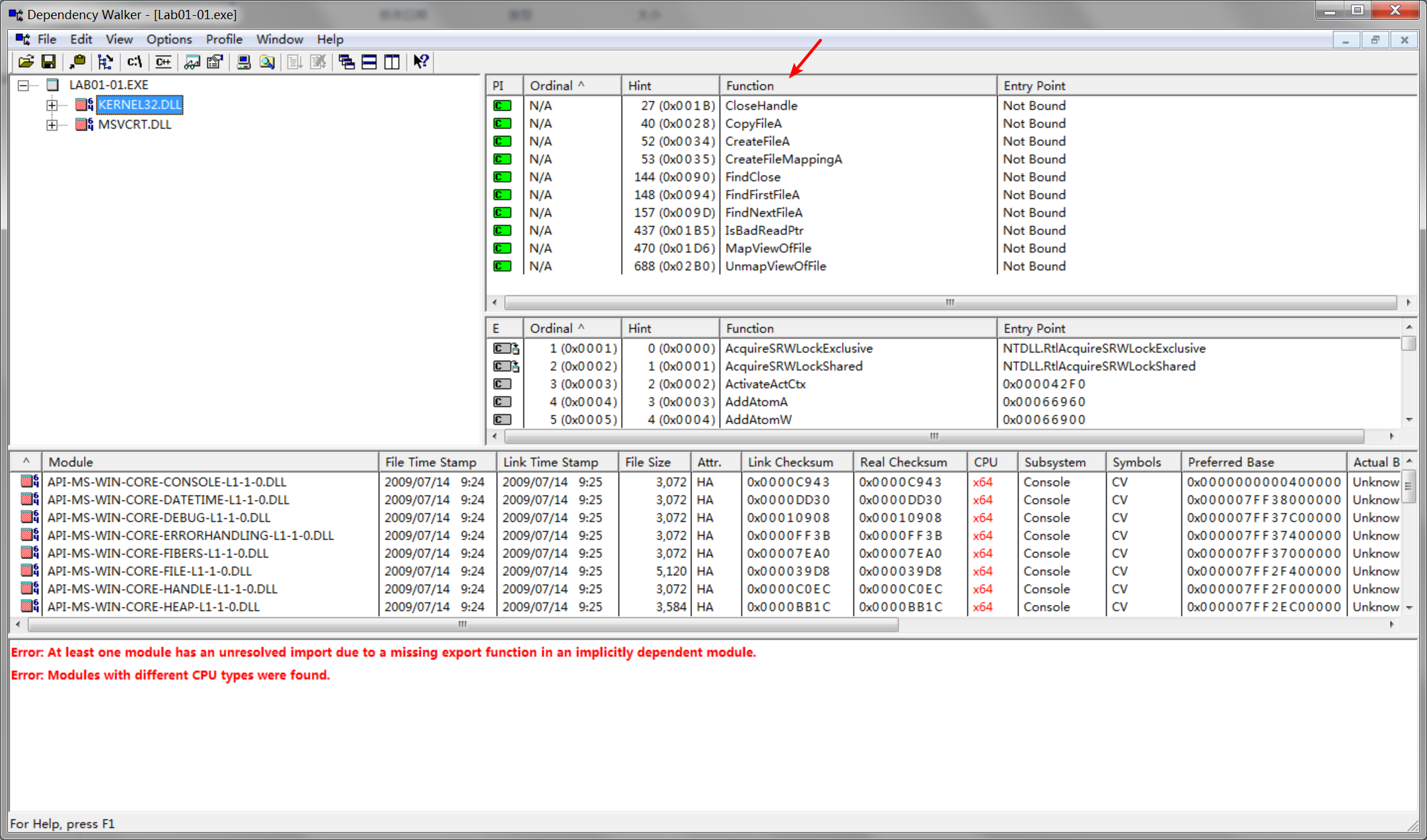
kernel32.dll是Windows 9x/Me中非常重要的32位动态链接库文件,属于内核级文件。它控制着系统的内存管理、数据的输入输出操作和中断处理,当Windows启动时,kernel32.dll就驻留在内存中特定的写保护区域,使别的程序无法占用这个内存区域。
msvcrt.dll是微软在windows操作系统中提供的C语言运行库执行文件(MicrosoftCRuntimeLibrary),其中提供了printf、malloc、strcpy等C语言库函数的具体运行实现,并且为使用C/C++(Vc)编绎的程序提供了初始化(如获取命令行参数)以及退出等功能。
The most interesting imports from Lab01-01.dll are CreateProcess and Sleep. We also see that this file imports functions from WS2_32.dll, which provides network functionality.
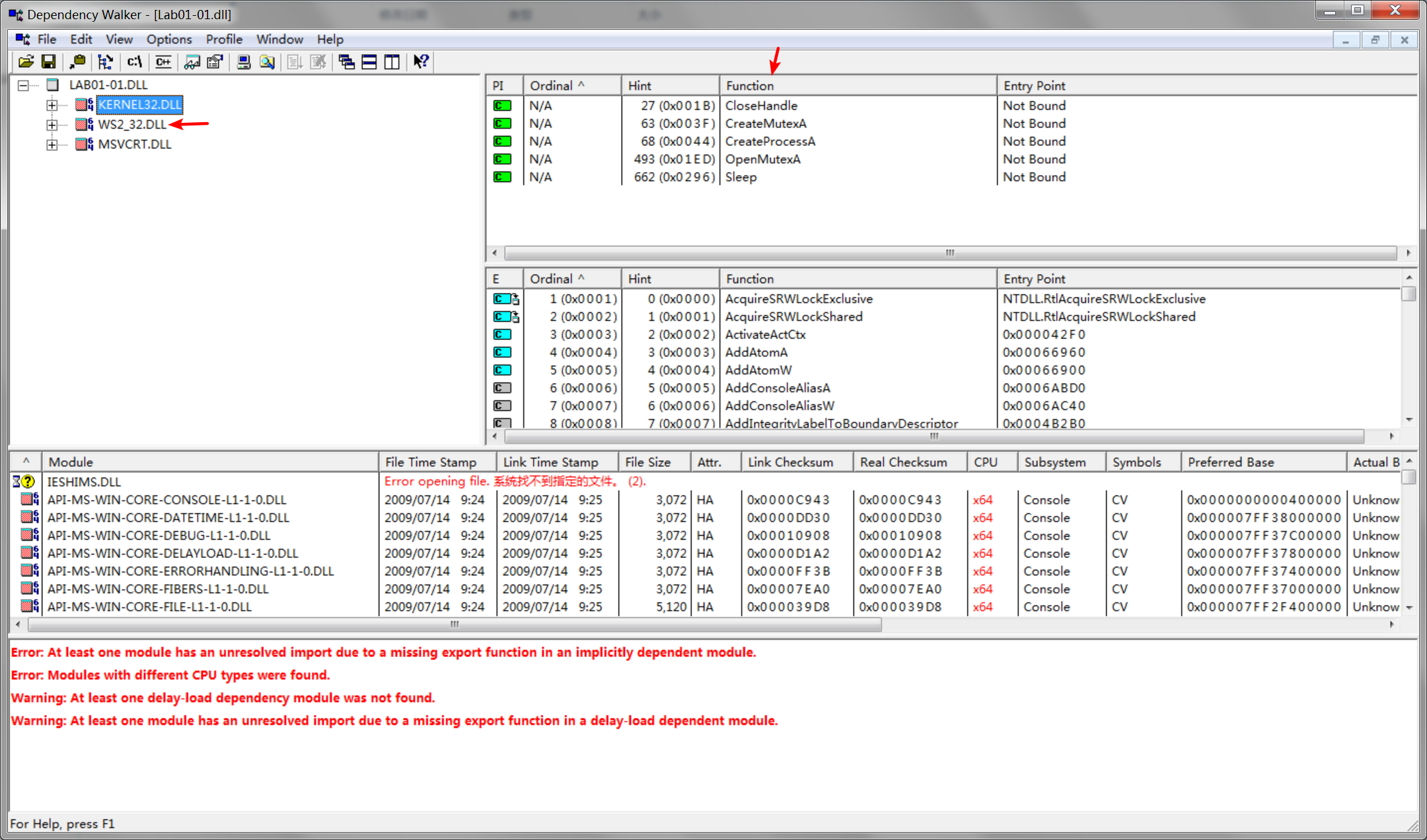
Are there any other files or host-based indicators that you could look for on infected systems?
A: Examine C:\Windows System32 kerne132.dll for additional malicious activity. Note that the file kerne132.dll, with the number 1 instead of the letter l, is meant to look like the system file kernel32.dll. This file can be used as a host indicator to search for the malware.
通过 IDA 查看 Lab01-01.exe,View -> Open subviews -> Strings :
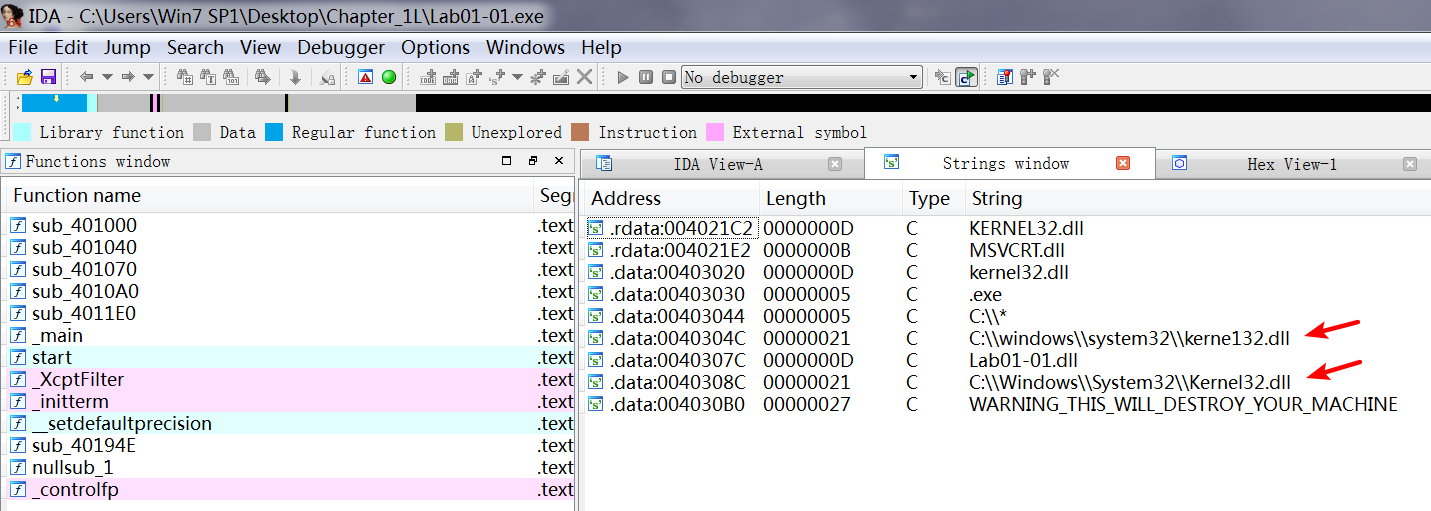
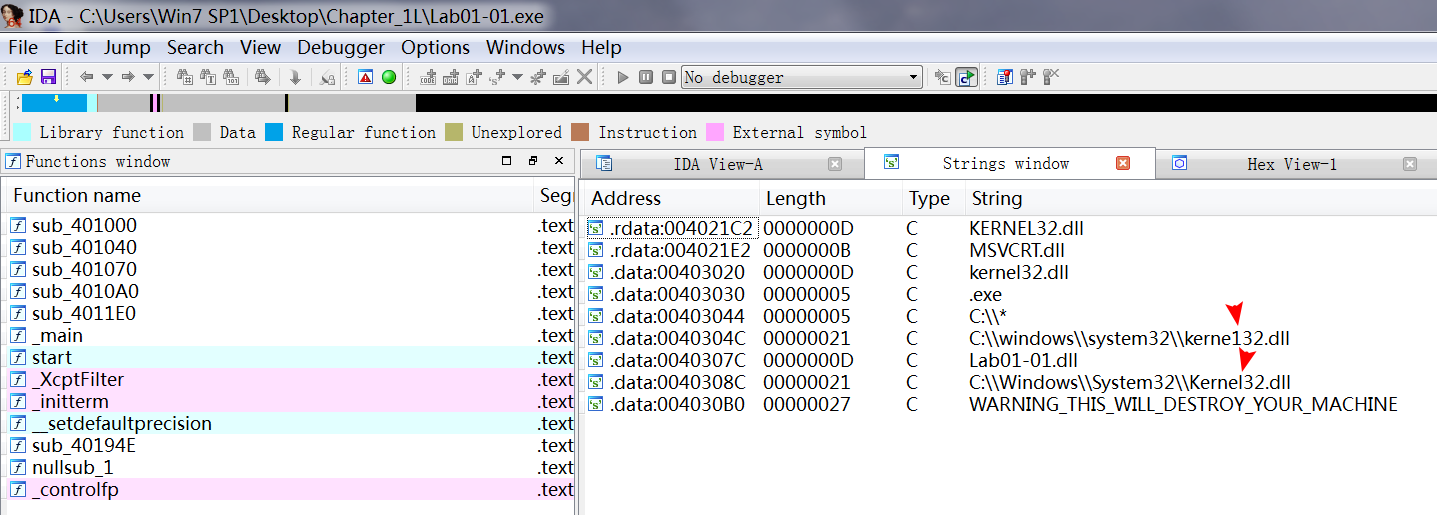
What network-based indicators could be used to find this malware on infected machines?
A: The .dll file contains a reference to local IP address 127.26.152.13. This address is an artifact of this program having been created for educational and not malicious purposes. If this was real malware, the IP address should be routable, and it would be a good network-based indicator for use in identifying this malware.
通过 IDA 查看 Lab01-01.dll,View -> Open subviews -> Strings :
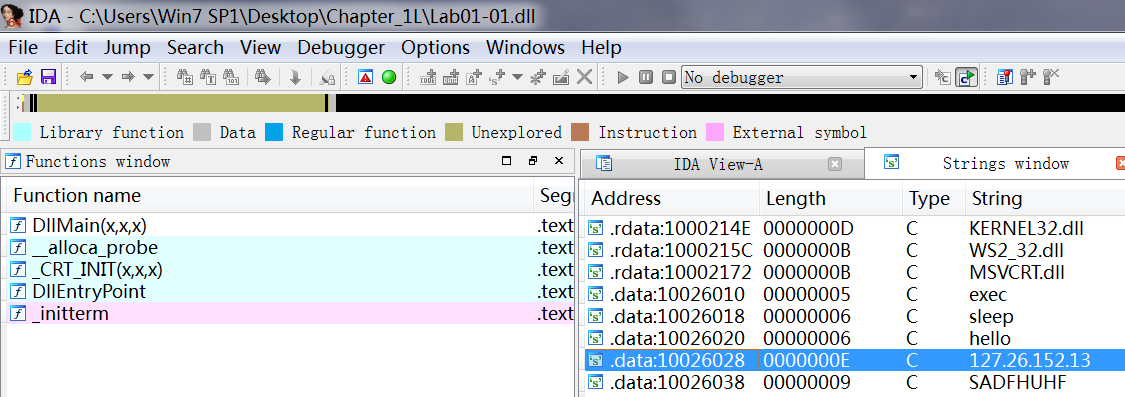
What would you guess is the purpose of these files?
A: The .dll file is probably a backdoor. The .exe file is used to install or run the DLL.
Detailed Analysis
To answer the first question, we upload the file to VirusTotal.com, which performs a scan against antivirus signatures.
Next, we open the files in PEview. For each file, we navigate to the IMAGE_NT_HEADERS
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ... Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ... Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ... Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ... Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ... Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ... 前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ... 又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ... 在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ... 感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ... 一.环境搭建 本次实验的环境为Ubuntu 16.04,Jenkins 2.8.3 1.安装ssh sudo apt-get update # 更新软件源 sudo apt-get install o ... 封装的JS代码 // 网页简繁体转换 // 本js用于客户在网站页面选择繁体中文或简体中文显示,默认是正常显示,即简繁体同时显示 // 在用户第一次访问网页时,会自动检测客户端语言进行操作并提示.此功 ... 16.统计出当前各个title类型对应的员工当前薪水对应的平均工资.结果给出title以及平均工资avg.CREATE TABLE `salaries` (`emp_no` int(11) NOT N ... SELECT * INTO [excel .xls].Sheet1 FROM tableName 背景 现在很多Linux系统在安装完成时就自带jdk,但是系统自带的jdk有时候并不符合我们的需求,这时候我们需要自己来安装jdk. 步骤 下载jdk,我下载的是64位的jdk-8u161-linux ... 添加中科大源 #打开配置文件 kate /etc/pacman.conf 在文件末尾添加 [archlinuxcn] SigLevel = Optional TrustedOnly Server = ... 题目链接 https://codeforces.com/contest/113/problem/D 思路 \(k[i]=\frac{1-p[i]}{ru[i]}\) f[i][j]表示经过i和j的次数 ... 目录 函数式接口: JDK 8之前已有的函数式接口: 新定义的函数式接口: 函数式接口中可以额外定义多个Object的public方法一样抽象方法: 声明异常: 静态方法: 默认方法 泛型及继承关系 ... 安装后smpd无法运行,进程中没有smpd.exe.注册过程也完成了.运行自带的测试程序cpi.exe,提示:Error: No smpd passphrase specified through t ... Problem Description \(Sylvia\) 是一个热爱学习的女孩子. 前段时间,\(Sylvia\) 参加了学校的军训.众所周知,军训的时候需要站方阵. \(Sylvia\) 所在的 ...Lab 1-1的更多相关文章
随机推荐
