Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap
Nmap is a network discovery tool that can be used to gather detailed information about any client or network.
We shall have a look at some of its uses to discover connected clients and gather information about them.
We are going to use Zenmap - the GUI for Namp.
1. Ping scan: Very quick - only shows connected clients.

2. Quick scan plus: Quick - shows MAC and open clients.
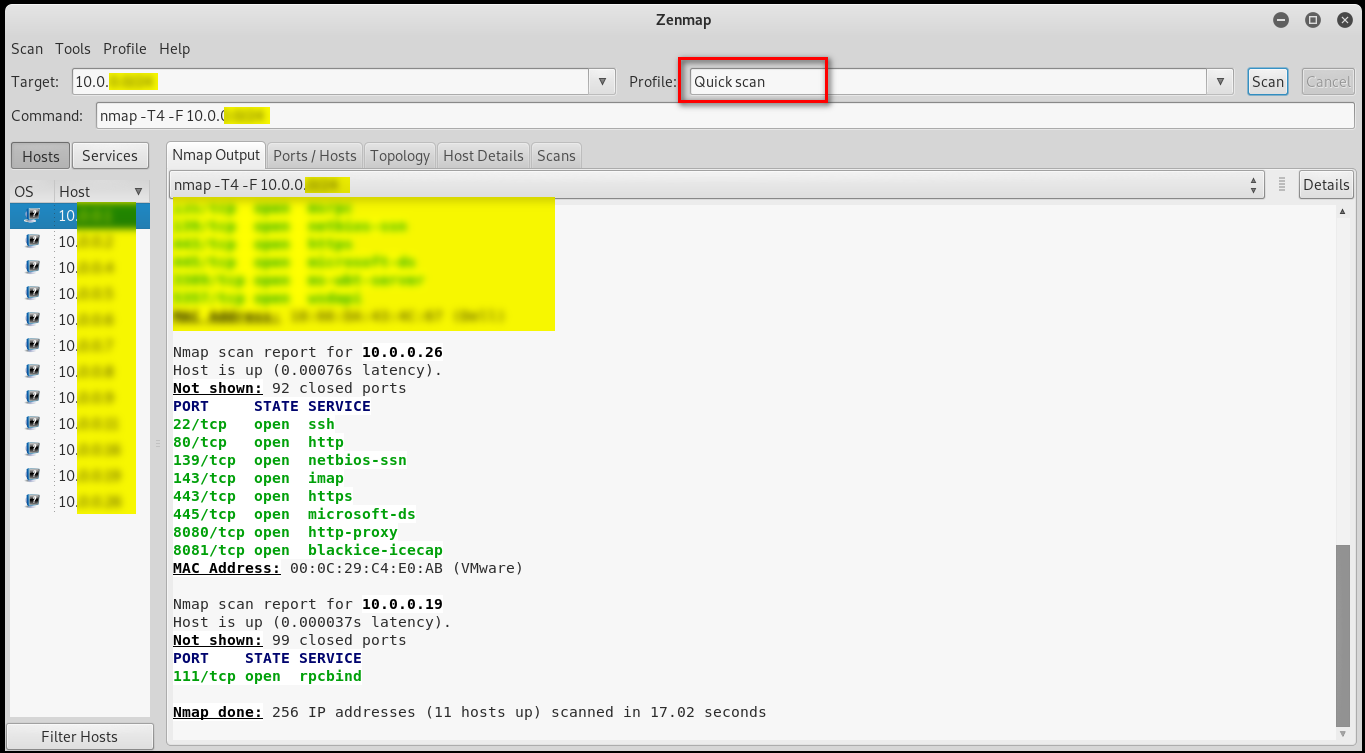
3. Quick scan plus: Slower than the 2 above, more detailed info.

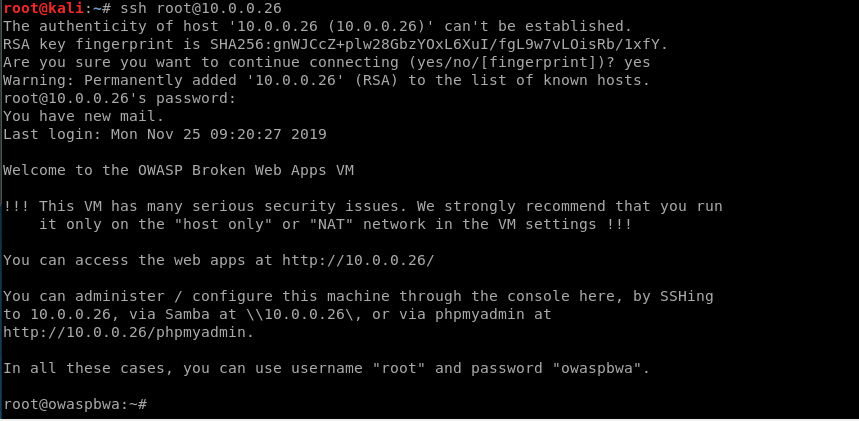
Many people are too lazy to change the password, so I log in to the target victim pc through default username/password.
Ethical Hacking - NETWORK PENETRATION TESTING(13)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 一文搞懂GitLab安装部署及服务配置
GitLab安装部署 Git,GitHub,GitLab,这三个东东长得好像呀,都是个啥? Git是Linus Torvalds(如果不知道这位大神是谁,请出门左转,慢走不送~)为了帮助管理Linux ...
- cb42a_c++_STL_算法_替换_replace
cb42a_c++_STL_算法_替换_replacereplace(b,e,ov,nv),ov,old value, nv,new valuereplace_if(b,e,p,v) 根据p的条件,全 ...
- web api(基于NFine框架) 中接口跳转数据格式错误解决方案
using NFine.Code; using NFine.Domain; using System.Web.Http; using Newtonsoft.Json; namespace Api.Co ...
- 07.Easymock的实际应用
第一步下载对应的java包添加到工程中 并静态导入所需要的j类 import static org.easymock.EasyMock.*; 这里有的注意点 package com.fjnu.serv ...
- pikachu靶场-XSS
.Tips: 一般查询接口容易出现反射型XSS,留言板容易出现存储型XSS 由于后台可能存在过滤措施,构造的script可能会被过滤掉,而无法生效,或者环境限制了执行(浏览器): 通过变化不同的scr ...
- 入门大数据---HDFS,Zookeeper,ZookeeperFailOverController(简称:ZKFC),JournalNode是什么?
HDFS介绍: 简述: Hadoop Distributed File System(HDFS)是一种分布式文件系统,设计用于在商用硬件上运行.它与现有的分布式文件系统有许多相似之处.但是,与其他分布 ...
- C++中i++和++i的区别
目录 效果上的区别 性能上的区别 分析汇编代码 进行性能实验 二者的选择 效果上的区别 i++是对变量i递增,但返回原值,++i是对变量i进行递增,并返回终值. 可以用以下代码加以验证: int i ...
- C# 模型赋值
/// <summary> /// 模型赋值 /// </summary> /// <param name="target">目标</pa ...
- 洛谷 P1186 【玛丽卡】
这道题题目真的想吐槽一下...是在机房同学的解释下才看懂的.就是让你求在可以删一条边的情况下,并且删后保证可以到达终点时,求删了后的最大的最短路径. 70分暴力思路: 枚举删边,然后跑一下最短路即可, ...
- IdentityServer4 4.x版本 配置Scope的正确姿势
前言 IdentityServer4 是为ASP.NET Core系列量身打造的一款基于 OpenID Connect 和 OAuth 2.0 认证的框架 IdentityServer4官方文档:ht ...
