彻底弄懂“PKIX path building failed”问题
SSL的基础知识
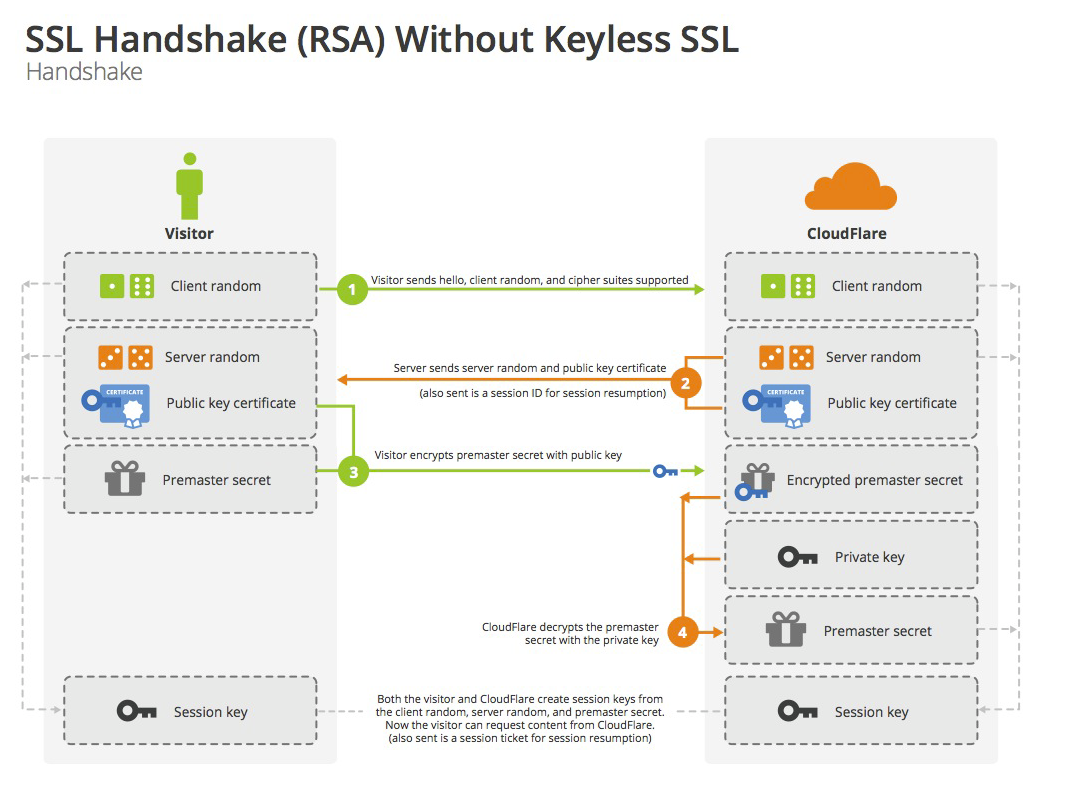
SSL的全称是Secure Socket Layer。它的通信流程如下图所示,客户端与服务端会通过几次通信,通过非对称加密创建出一个加密密钥,用于以后的对称信息加密。
1,客户端明文向服务器打招呼,告诉服务器自己支持的加密算法、随机数A;
2,服务器明文返回给客户端自己的证书和另外一个随机数B;
3,客户端验证收到的证书。验证通过则使用这个证书的公钥加密一个密码发送给服务器;
4,服务器通过自己的私钥解密客户端发送过来的密码;
5,服务器使用这个密码进行对称加密通信。
重点:用-Djavax.net.debug=all跟踪调试,确定对的证书
任何一个环节出错,都可能出现下面的错误:
PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
用-Djavax.net.debug=all来开启调试信息的输出,SSL的握手过程一目了然:
-- :: --INFO-- ***Helper : https://xxx.xxx.com:8443/***/ws/***Service
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_256_CBC_SHA256
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_128_CBC_SHA256
Allow unsafe renegotiation: false
Allow legacy hello messages: true
Is initial handshake: true
Is secure renegotiation: false
%% Client cached [Session-, TLS_RSA_WITH_AES_256_CBC_SHA]
%% Try resuming [Session-, TLS_RSA_WITH_AES_256_CBC_SHA] from port
##客户端跟服务器第一次打招呼##
*** ClientHello, TLSv1
RandomCookie: GMT: bytes = { , , , , , , , , , , , , , , , , , , , , , , , , , , , }
Session ID: {, , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , }
##支持的加密算法##
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA, TLS_RSA_WITH_AES_256_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDH_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_DSS_WITH_AES_256_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_ECDSA_WITH_RC4_128_SHA, TLS_ECDHE_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_SHA, TLS_ECDH_ECDSA_WITH_RC4_128_SHA, TLS_ECDH_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_MD5, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { }
Extension elliptic_curves, curve names: {secp256r1, sect163k1, sect163r2, secp192r1, secp224r1, sect233k1, sect233r1, sect283k1, sect283r1, secp384r1, sect409k1, sect409r1, secp521r1, sect571k1, sect571r1, secp160k1, secp160r1, secp160r2, sect163r1, secp192k1, sect193r1, sect193r2, secp224k1, sect239k1, secp256k1}
Extension ec_point_formats, formats: [uncompressed]
Extension server_name, server_name: [host_name: idmtest.dcpc.com]
***
[
: D8 5A D8 5F D8 ......Zr.T_x..E"
: CD 1E F0 B2 BB E4 7F D8 .I....%...I.....
...
DefaultQuartzScheduler_Worker-, WRITE: TLSv1 Handshake, length =
[Raw
: DC D8 5A D8 5F ...........Zr.T_
: D8 CD 1E F0 B2 BB E4 7F x..E".I....%...I
...
[Raw read]: length =
: ...."
[Raw read]: length =
: 5A 4E F2 CF 4B 0F CE ...F..ZrcN..K..X
: 0E EF D4 F3 3E C0 AD 6D 4B 8D DB CA FB ....>...mK....w
: B3 A1 D2 A7 D5 A6 FD 6E A7 FF 5A D4 DF ...... ...n..Z..
...
DefaultQuartzScheduler_Worker-, READ: TLSv1 Handshake, length =
##服务器响应
*** ServerHello, TLSv1
RandomCookie: GMT: bytes = { , , , , , , , , , , , , , , , , , , , , , , , , , , , }
Session ID: {, , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , }
##服务器选定的加密算法
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA
Compression Method:
***
Warning: No renegotiation indication extension in ServerHello
%% Initialized: [Session-, TLS_RSA_WITH_AES_256_CBC_SHA]
** TLS_RSA_WITH_AES_256_CBC_SHA
[read] MD5 and SHA1 hashes: len =
: 5A 4E F2 CF 4B 0F CE ...F..ZrcN..K..X
: 0E EF D4 F3 3E C0 AD 6D 4B 8D DB CA FB ....>...mK....w
...
##服务器返回给客户端的证书链,证明“我是我”
*** Certificate chain
chain [] = [
[
Version: V3
Subject: CN=*.****.com, ST=北京市, L=北京市, O=***公司, C=CN
Signature Algorithm: SHA256withRSA, OID =
Key: Sun RSA public key, bits
modulus: ...
public exponent:
Validity: [From: Wed May :: CST ,
To: Fri May :: CST ]
Issuer: CN=WoSign OV SSL CA, O=WoSign CA Limited, C=CN
SerialNumber: [ 363fa17d 5c46082c dc707c24 6a8d81b2]
Certificate Extensions:
[]: ObjectId: Criticality=false
AuthorityInfoAccess [[
accessMethod: ocsp
accessLocation: URIName: http://wosign-ovca.ocsp-certum.com,
accessMethod: caIssuers
accessLocation: URIName: http://repository.certum.pl/wosign-ovca.cer]]
[]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
: A1 DC 2C CA C8 EF EE BF ..T.Vs,'........
: FD 5F AB ._.V
]]
[]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
[]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://wosign.crl.certum.pl/wosign-ovca.crl]
]]
[]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.2]
[] ]
[CertificatePolicyId: [1.2.616.1.113527.2.5.1.12.2]
[PolicyQualifierInfo: [
qualifierID:
qualifier:
: E4 1F 6F .....Asseco Da
: 6D 2E 2E ta Systems S.A.
...
]] ]
]
[]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
[]: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: *.dcpc.com
DNSName: dcpc.com
]
[]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
: B3 A6 AD D8 B7 D5 E1 E5 B2 BC E6 ..S....Q........
: B5 F2 2B ...+
]]]
Algorithm: [SHA256withRSA]
Signature:
: 9A A4 8F B2 A8 CE 9A B6 2F 8F AA ........./...Ey
: DE D6 6E D7 5E C1 1F EC 7F C9 ..".n..E^......
...
]
***
==客户端从本地找到的信赖证书(如果找不到会直接报certificate_unknow)==
Found trusted certificate:
[
[
Version: V3
Subject: CN=*.****.com, ST=北京市, L=北京市, O=****公司, C=CN
Signature Algorithm: SHA256withRSA, OID =
Key: Sun RSA public key, bits
modulus: ....
public exponent:
Validity: [From: Wed May :: CST ,
To: Fri May :: CST ]
Issuer: CN=WoSign OV SSL CA, O=WoSign CA Limited, C=CN
SerialNumber: [ 363fa17d 5c46082c dc707c24 6a8d81b2]
Certificate Extensions:
[]: ObjectId: Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://wosign-ovca.ocsp-certum.com
,
accessMethod: caIssuers
accessLocation: URIName: http://repository.certum.pl/wosign-ovca.cer
]
]
[]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
: A1 DC 2C CA C8 EF EE BF ..T.Vs,'........
: FD 5F AB ._.V
]
]
[]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
[]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://wosign.crl.certum.pl/wosign-ovca.crl]
]]
[]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.2]
[] ]
[CertificatePolicyId: [1.2.616.1.113527.2.5.1.12.2]
[PolicyQualifierInfo: [
qualifierID:
qualifier:
: E4 1F 6F .....Asseco Da
: 6D 2E 2E ta Systems S.A.
...
]] ]
]
[]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
[]: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: *.dcpc.com
DNSName: dcpc.com
]
[]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
: B3 A6 AD D8 B7 D5 E1 E5 B2 BC E6 ..S....Q........
: B5 F2 2B ...+
]
]
]
Algorithm: [SHA256withRSA]
Signature:
: 9A A4 8F B2 A8 CE 9A B6 2F 8F AA ........./...Ey
: DE D6 6E D7 5E C1 1F EC 7F C9 ..".n..E^......
...
]
[read] MD5 and SHA1 hashes: len =
: 0B D0 CD CA C6 ..............
: AE A0 3F A1 7D 5C .........?..\F.
...
*** ServerHelloDone
[read] MD5 and SHA1 hashes: len =
: 0E ....
*** ClientKeyExchange, RSA PreMasterSecret, TLSv1
[
: BD EA 0F 0A BD ........r.......
: 0F 6E C4 A2 F0 D2 BA 0B A0 ..rQ..n).....x..
...
DefaultQuartzScheduler_Worker-, WRITE: TLSv1 Handshake, length =
[Raw
: BD .............r..
: EA 0F 0A BD 0F 6E C4 A2 F0 .......rQ..n)...
...
SESSION KEYGEN:
PreMaster Secret:
: 4B FA 1D CE F4 3D 4A A7 ....K......=J..
...
CONNECTION KEYGEN:
Client Nonce:
: 5A D8 5F D8 CD 1E F0 B2 Zr.T_x..E".I....
...
Server Nonce:
: 5A 4E F2 CF 4B 0F CE 0E EF D4 F3 3E ZrcN..K..X....>
...
Master Secret:
: C4 B7 FB 5F 8A 8E 2C C1 C7 ......#_....,..r
...
Client MAC write Secret:
: BA CD D9 5F FA 7A DF DE 0A "...a'.b_..z....
...
Server MAC write Secret:
: D2 AC AC CE F2 D2 E6 4F 8A DE E3 8D ..s......O.....
: BA D2 sR..
Client write key:
: CA FB B2 E7 3F CB AB FF EF 1E .....?y.Ua.....v
: 4C DD DE 6F 8E 5D A2 .L...U.o(..].%.
Server write key:
: 1A D2 3B D7 5F 9A FF D5 B3 .%1i.;E.p._....q
: 9D D6 F0 8B 8E BE B1 s..R..!.......uF
Client write IV:
: C3 A2 A0 F3 AC DA C3 EF hI....u........
Server write IV:
: 2C 9D 6F C2 7D BD B1 AA E5 6E EA ,..(o......0n..
DefaultQuartzScheduler_Worker-, WRITE: TLSv1 Change Cipher Spec, length =
[Raw
: ......
*** Finished
verify_data: { , , , , , , , , , , , }
***
[
: 0C A9 A0 2B C6 E5 8C A0 FB 4C ......+.d....L.
Padded plaintext before ENCRYPTION: len =
: 0C A9 A0 2B C6 E5 8C A0 FB 4C ......+.d....L.
: F5 B1 BB DE F4 ED A2 3A 9D C8 8E EE 2B A6 .....%..:.....+.
: 4A 1E 3A C7 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B J.:.............
DefaultQuartzScheduler_Worker-, WRITE: TLSv1 Handshake, length =
[Raw
: 4E 1F 3A 1F C8 1B 9F 6B 3A ....0N..:.....k:
: CC 2C 2C 9D CA DA 4F 8E D8 5A .,g,..X.O.!...Z7
: B8 BD A9 E4 F3 E9 9C E6 E1 BB 8D 0E g.....y....R...
: 5F F5 7E 7A E_..z
[Raw read]: length =
: .....
[Raw read]: length =
: .
DefaultQuartzScheduler_Worker-, READ: TLSv1 Change Cipher Spec, length =
[Raw read]: length =
: ....
[Raw read]: length =
: A9 B4 AB 6C BA DB CF 6E EF 8A F2 6F BD ...lh.G..n...o.s
: E4 C8 1B 4B C6 D9 A3 DB 4D 3B E0 8D .DU...K....M.;..
: ED E8 CA D8 F8 C8 1B DD 6F F2 g...c....@.T.o.
DefaultQuartzScheduler_Worker-, READ: TLSv1 Handshake, length =
Padded plaintext after DECRYPTION: len =
: 0C 5A F4 F0 FA C9 BE 1D 6A A5 3A ....XZ......'j.:
: DC D1 C8 DD CB E9 F0 F7 E2 9F ...R.S.......F..
: 9E A6 EF 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B 0B ...c............
*** Finished
verify_data: { , , , , , , , , , , , }
***
%% Cached client session: [Session-, TLS_RSA_WITH_AES_256_CBC_SHA]
[read] MD5 and SHA1 hashes: len =
: 0C 5A F4 F0 FA C9 BE 1D 6A A5 3A ....XZ......'j.:
DefaultQuartzScheduler_Worker-, setSoTimeout() called
Padded plaintext before ENCRYPTION: len =
##发送数据
: 4F 2F 6D 2F 2F 6E POST /idm/ws/Uni
: 2F 2E tService HTTP/.
: 0D 0A 6F 6E 6E 2D 3A ..Content-Type:
: 2F 6D 6C 3B text/xml; chars
: 3D 2D 0D 0A et=utf-..Accept
: 3A 6C 6F 6E 2F 6F : application/so
: 2B 6D 6C 2C 6C ap+xml, applicat
: 6F 6E 2F 6D 2C 6D 6C ion/dime, multip
: 2F 6C 2C art/related, tex
: 2F 2A 0D 0A 2D 6E 3A t/*..User-Agent:
00A0: 20 41 78 69 73 2F 31 2E 34 0D 0A 48 6F 73 74 3A Axis/1.4..Host:
00B0: 20 69 64 6D 74 65 73 74 2E 64 63 70 63 2E 63 6F ***.***.co
00C0: 6D 3A 38 34 34 33 0D 0A 43 61 63 68 65 2D 43 6F m:8443..Cache-Co
...
DefaultQuartzScheduler_Worker-3, WRITE: TLSv1 Application Data, length = 960
[Raw write]: length = 965
0000: 17 03 01 03 C0 76 73 C9 5C 37 18 B3 8D 85 B6 4A .....vs.\7.....J
0010: A5 FF 06 E0 81 74 E2 46 22 C7 32 12 51 A6 C4 10 .....t.F".2.Q...
0020: 7E 1D 14 C6 1E 1B 44 95 57 6E AC 83 AA 8D A7 92 ......D.Wn......
0030: 4C 34 01 5D E9 A1 1E 8C BB 03 55 D9 7A 09 0F 1E L4.]......U.z...
0040: 5D C4 71 46 CA 29 72 0D C1 CC F8 CE 6E F9 51 3A ].qF.)r.....n.Q:
...
[Raw read]: length = 5
0000: 17 03 01 01 60 ....`
[Raw read]: length = 352
0000: CD C2 06 A2 9F EA 9F 00 C7 27 5E F0 B3 C4 3D 78 .........'^...=x
0010: 2E 9B F4 52 08 FF D7 05 2E A8 1B 42 3F 9A 3D 73 ...R.......B?.=s
...
DefaultQuartzScheduler_Worker-3, READ: TLSv1 Application Data, length = 352
##接收数据
Padded plaintext after DECRYPTION: len = 352
0000: 48 54 54 50 2F 31 2E 31 20 32 30 30 20 0D 0A 43 HTTP/1.1 200 ..C
0010: 6F 6E 74 65 6E 74 2D 54 79 70 65 3A 20 74 65 78 ontent-Type: tex
0020: 74 2F 78 6D 6C 3B 63 68 61 72 73 65 74 3D 55 54 t/xml;charset=UT
0030: 46 2D 38 0D 0A 44 61 74 65 3A 20 54 68 75 2C 20 F-8..Date: Thu,
0040: 30 31 20 46 65 62 20 32 30 31 38 20 30 39 3A 30 01 Feb 2018 09:0
0050: 35 3A 32 35 20 47 4D 54 0D 0A 43 6F 6E 6E 65 63 5:25 GMT..Connec
0060: 74 69 6F 6E 3A 20 63 6C 6F 73 65 0D 0A 0D 0A 3C tion: close....<
0070: 73 6F 61 70 3A 45 6E 76 65 6C 6F 70 65 20 78 6D soap:Envelope xm
0080: 6C 6E 73 3A 73 6F 61 70 3D 22 68 74 74 70 3A 2F lns:soap="http:/
0090: 2F 73 63 68 65 6D 61 73 2E 78 6D 6C 73 6F 61 70 /schemas.xmlsoap
00A0: 2E 6F 72 67 2F 73 6F 61 70 2F 65 6E 76 65 6C 6F .org/soap/envelo
...
[Raw read]: length = 5
0000: 15 03 01 00 20 ....
[Raw read]: length = 32
0000: 10 E4 3E EF D9 D6 A2 0F F3 11 85 6F 8F 68 48 C8 ..>........o.hH.
0010: 26 73 2E C8 FA 9D 00 03 AB 3B 79 46 DE ED CC 40 &s.......;yF...@
DefaultQuartzScheduler_Worker-3, READ: TLSv1 Alert, length = 32
Padded plaintext after DECRYPTION: len = 32
0000: 01 00 C2 40 0A 51 E1 F1 28 06 65 73 E4 84 81 01 ...@.Q..(.es....
0010: 8F A9 A1 FD A9 6E 09 09 09 09 09 09 09 09 09 09 .....n..........
DefaultQuartzScheduler_Worker-3, RECV TLSv1 ALERT: warning, close_notify
DefaultQuartzScheduler_Worker-3, called closeInternal(false)
DefaultQuartzScheduler_Worker-3, SEND TLSv1 ALERT: warning, description = close_notify
Padded plaintext before ENCRYPTION: len = 32
0000: 01 00 4F BB 75 8C 9C 8A 12 64 D7 62 F6 AF 81 90 ..O.u....d.b....
0010: 92 0E 91 25 6F 9B 09 09 09 09 09 09 09 09 09 09 ...%o...........
DefaultQuartzScheduler_Worker-3, WRITE: TLSv1 Alert, length = 32
[Raw write]: length = 37
0000: 15 03 01 00 20 C1 60 66 8A 2A 1D A5 6C 82 C3 59 .... .`f.*..l..Y
0010: A8 D5 E9 28 70 1D 93 F1 DD 34 00 14 1F 56 12 46 ...(p....4...V.F
0020: 33 0C 4C 3F 51 3.L?Q
DefaultQuartzScheduler_Worker-3, called closeSocket(selfInitiated)
DefaultQuartzScheduler_Worker-3, called close()
DefaultQuartzScheduler_Worker-3, called closeInternal(true)
DefaultQuartzScheduler_Worker-3, called close()
DefaultQuartzScheduler_Worker-3, called closeInternal(true)
如果遇到了前面的报错信息,首先应该做的就是到这里来看看服务器给客户端发送的到底是个什么证书!知道是什么证书之后,尝试获取到这个证书,导入到本地就行了。
正确地导入证书
服务器颁发给我们的cer证书文件需要导入到keystore文件中,Java才能识别。
keytool工具实现了对keystore文件中的证书进行曾删查功能。
证书管理
增加(导入证书)
keytool -import -noprompt -trustcacerts -alias test -file D:\certs\some.cer -keystore cacerts -storepass changeit
-keystore:指定证书导入到的文件位置,文件不存在时会自动创建,存在时会追加
-file:指定导入的cer文件
-storepass:指定keystore文件的访问密码
-alias:指定别名,其实可以理解为ID,别名不能重复,删除的时候也依靠它
查询
keytool -list -keystore cacerts |findstr /s test
因为结果可能很多,这里用windows的findstr来过滤。
删除
keytool -delete -alias test -keystore cacerts
证书识别
Java程序对受信证书的查找顺序是:
1,javax.net.ssl.trustStore
就是System.setProperty("javax.net.ssl.trustStore","D:\\cacert.keystore");或者通过JVM参数指定:-Djavax.net.ssl.trustStore=D:\cacert.keystore。
2,JAVA_HOME\jre\lib\security\jssecacerts 【推荐】
默认没有jssecacerts,一般把cacerts复制成jssecacerts,然后再使用keytool来修改它。jsse的全称是Java Secure Socket Extension。
3,JAVA_HOME\jre\lib\security\cacerts
通常情况下不就建议通过-Djavax.net.ssl.trustStore=D:\cacert.keystore来直接修改keystore文件的位置,因为这样会造成系统中其他模块可能找不到自己对应的证书了。推荐使用jssecacerts。我们需要什么证书直接往这个位置导就行了。程序不需要做调整。
其他注意事项
System.setProperty("javax.net.ssl.trustStore",..)可能不会生效
写一个JUnit单元测试可以这么改:
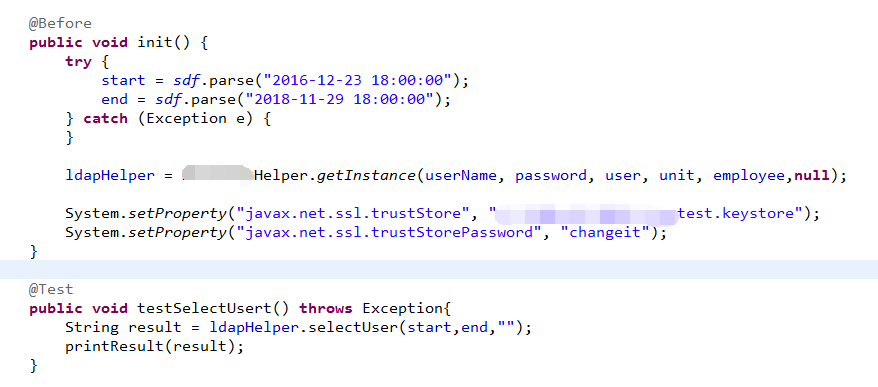
但是在Spring的Service中动态修改就不见得会生效了。你虽然动态调整了System的属性,但是别人用不用就不确定了。具体可以参考这里:https://stackoverflow.com/questions/271506/why-cant-system-setproperty-change-the-classpath-at-runtime
使用JVM参数强制指定keystore
用JVM参数的形式就比上面这种方式更有效,并且意图更加明确,程序肯定会使用这个参数指定位置的keystore。
-Djavax.net.ssl.trustStore=C:\Java\jre\lib\security\jssecacerts -Djavax.net.ssl.trustStorePassword=changeit
后话
密码和安全相关的主体确实太有意思了,应该专题研究一下,什么是PKI、什么是X.509,要扫清盲点,知其所以然,这样才能在遇到异常时知道那个环节出了问题。
个人学习总结,有不对之处还望赐教。
参考:
阮一峰:图解SSL/TLS协议,http://www.ruanyifeng.com/blog/2014/09/illustration-ssl.html
What is SSL:https://www.youtube.com/watch?v=dsuVPxuU_hc
Java Secure Socket Extension:https://docs.oracle.com/javase/1.5.0/docs/guide/security/jsse/JSSERefGuide.html#Debug
彻底弄懂“PKIX path building failed”问题的更多相关文章
- 【问题记录】Java服务发起HTTPS请求报错:PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException
问题报错 今天上线了我开发的一个OAuth2单点登录客户端的实现,在测试系统验证没问题,到生产环境由于单点登录服务端HTTPS协议,报错如下: I/O error on POST request fo ...
- 解决 java 使用ssl过程中出现"PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target"
今天,封装HttpClient使用ssl时报一下错误: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorExc ...
- 解决PKIX(PKIX path building failed) 问题 unable to find valid certification path to requested target
最近在写java的一个服务,需要给远程服务器发送post请求,认证方式为Basic Authentication,在请求过程中出现了 PKIX path building failed: sun.se ...
- 解决CAS单点登录出现PKIX path building failed的问题
在一次调试中,出现了这个错误: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderExceptio ...
- jsoup访问页面: PKIX path building failed
在用jsoup访问页面时报错javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX p ...
- 抓取https网页时,报错sun.security.validator.ValidatorException: PKIX path building failed 解决办法
抓取https网页时,报错sun.security.validator.ValidatorException: PKIX path building failed 解决办法 原因是https证书问题, ...
- javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed
1.使用HttpClient4.3 调用https出现如下错误: javax.net.ssl.SSLHandshakeException: sun.security.validator.Validat ...
- 解决 sun.security.validator.ValidatorException: PKIX path building failed
今天用java HttpClients写爬虫在访问某Https站点报如下错误: sun.security.validator.ValidatorException: PKIX path buildin ...
- 解决PKIX path building failed
起因 上周在生产环境部署时,把安全证书加到k8s-ingress中时发现报该错误 解决 找网上解决方案,因为这种问题相对比较少见,也没百度,直接谷歌,找到解决方案如下:https://stackove ...
随机推荐
- oracle unix时间戳与date转换
linux 时间戳 转date: 创建自定义函数: create or replace function unix_to_oracle(in_number number) return date ...
- 2019.01.24 NOIP训练 旅行(轮廓线dp)
传送门 题意简述: 给一个n∗mn*mn∗m的有障碍的网格图,问你从左上角走到左下角并覆盖所有可行格子的路径条数. 思路: 路径不是很好算. 将图改造一下,在最前面添两列,第一列全部能通过,第二列只有 ...
- 2019.01.19 bzoj4592: [Shoi2015]脑洞治疗仪(ODT)
传送门 ODT水题. 支持区间01赋值,区间填补(把区间[l,r][l,r][l,r]从左往右数kkk个1都变成0),区间查询最长连续1个数. 思路: 区间填补操作感觉不是很好弄,写线段树的神仙可以套 ...
- 2019.01.14 codeforces685B. Kay and Snowflake(树形dp)
传送门 题意简述:给出一棵树,求每个子树的重心. 首先通过画图可以观察出一个性质,我们从叶子结点向根节点递推重心的话重心的位置是不会下降的. 然后由于一个点的重心要么是自己,要么在重儿子子树内,因此如 ...
- 创建Java程序并设置快捷提示
1.new Java project 创建项目 2.new package 创建包,cn.com.test 3.创建Java文件 4.Java智能提示的设置 window/preference 在Au ...
- ACM-ICPC 2018 徐州赛区网络预赛 A Hard to prepare
https://nanti.jisuanke.com/t/31453 题目大意: 有n个人坐成一圈,然后有\(2^k\)种颜色可以分发给每个人,每个人可以收到相同的颜色,但是相邻两个人的颜色标号同或不 ...
- java Concurrent包学习笔记(三):ReentrantLock
一.可重入性的理解 从名字上理解,ReenTrantLock的字面意思就是再进入的锁,其实synchronized关键字所使用的锁也是可重入的,两者关于这个的区别不大.两者都是同一个线程每进入一次,锁 ...
- 关于CSS的优先级,CSS优先级计算,多个class引用
原则一: 继承不如指定 原则二: #id > .class > 标签选择符 原则三:越具体越强大 原则四:标签#id >#id ; 标签.class > .class CSS优 ...
- C++ char, unsigned char, signed char
C语言中的 char, unsigned char, signed char 一.他们是什么? signed char是有符号的,但是unsigned char没有符号,两者在存储上没有任何区别都是8 ...
- Atcoder Grand-014 Writeup
A - Cookie Exchanges 题面 Takahashi, Aoki and Snuke love cookies. They have A, B and C cookies, respec ...
