Ethical Hacking - NETWORK PENETRATION TESTING(6)
Creating a fake access point (honeypot)
Fake access points can be handy in many scenarios, one example is creating an open AP, this will attract a lot of clients, many of which will automatically connect to it. Then we can sniff all the traffic created by the clients that connect to it, and since its open, the traffic will not be encrypted!
In order to do this, we need two cards:
1. One connected to the Internet.
2. WiFi card to broadcast as an access point.
Clients now send requests to the hacker's wifi card, the hacker sets up his machine so that every request coming from the wifi card is forwarded to the 2nd card that's connected to the Internet.
The response comes back from the 2nd card, through the hacker's machine to the wifi card which forwards it to the client that requested it.
Tool: Mana-Toolkit
Mana-Toolkit makes the whole progress very simple, it automatically creates a new AP and starts sslstrip/firelamp and even attempts to bypass HSTS which is used by Gmail and Facebook.
Mana has 3 main start scripts:
1. Start-noupstream: starts an AP with NO internet connection.
2.Start-nat-simple: this starts a regular AP using Internet connection in the upstream interface.
3.start-nat-full: starts AP with an Internet connection, it also starts sslstrip, sslsplit, firelamp and attempts to bypass HSTS.
apt-get install mana-toolkit
gvim /etc/mana-toolkit/hostapd-mana.conf
gvim /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
bash /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
The first ethernet card connects to the Internet.
The second wifi card is ready for use.

Download and install Mana from https://github.com/sensepost/mana.
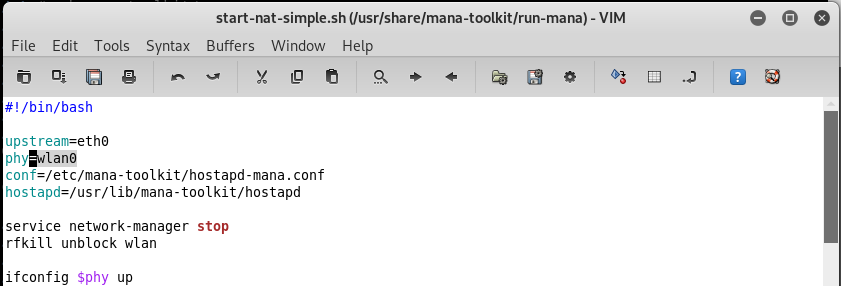
Modify the start-nat-simple.sh file.
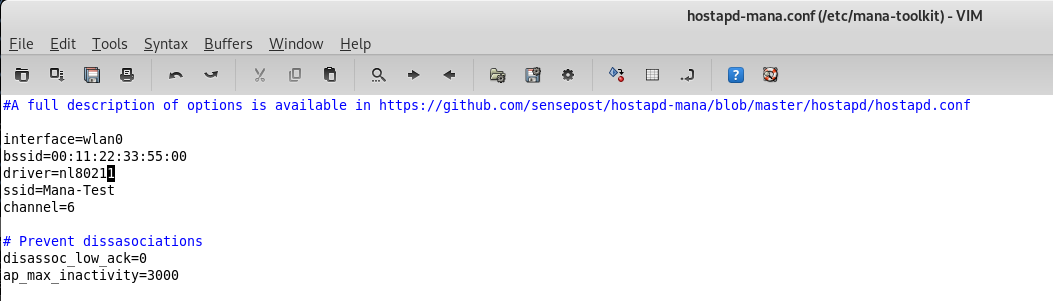
Modify the hostpad-mana.conf file.
Run mana script successfully.
bash start-nat-simple.sh
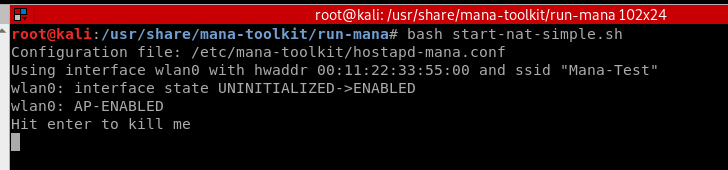
But it doesn't work well. Please see the detailed information:
https://www.slideshare.net/sensepost/improvement-in-rogue-access-points-sensepost-defcon-22
More information about hostpad setting:
https://github.com/sensepost/hostapd-mana/blob/master/hostapd/hostapd.conf
I will try Berate_ap or BetterCap later.
https://github.com/sensepost/berate_ap
https://www.bettercap.org/intro/
Ethical Hacking - NETWORK PENETRATION TESTING(6)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- Java并发编程的艺术(一、二章) ——学习笔记
第一章 并发编程的挑战 需要了解的一些概念 转自 https://blog.csdn.net/TzBugs/article/details/80921351 (1) 同步VS异步 同步和异步通常用来 ...
- TCP 粘包拆包
一.什么是粘包拆包? 粘包拆包是TCP协议传输中一种现象概念.TCP是传输层协议,他传输的是“流”式数据,TCP并不知道传输是哪种业务数据,或者说,并不关心.它只是根据缓冲区状况将数据进行包划分,然后 ...
- 008.OpenShift Metric应用
一 METRICS子系统组件 1.1 metric架构介绍 OpenShift metric子系统支持捕获和长期存储OpenShift集群的性能度量,收集节点以及节点中运行的所有容器的指标. metr ...
- idea安装docker插件
Preferences->Plugins 根据上图安装docker插件,安装完成后可使用idea来管理docker项目了.docker运行项目请参加"Docker开发环境搭建" ...
- Linux中bash的一些命令
Linux——bash的简单使用 bash及其特性: 1.bash实质上是一个可执行的程序,一个用户的工作环境. 2.每一个shell下可以再打开一个shell,新打开的shell称为子shell,每 ...
- JavaWeb网上图书商城完整项目--13.项目所需环境的搭建
1.首先安装mysql 创建项目所需的数据库,直接运行项目提供的goods.sql文库 2.myeclipse创建一个web project ,项目的名称是goods 把视频中提供的项目原型下的提供的 ...
- 前端笔记(关于webpack打包时内存溢出问题的解决)
首先安装increase-memory-limit cnpm install -g increase-memory-limit 重启cmd,并在项目跟目录中运行一下 increase-memory-l ...
- codeforce 796C - Bank Hacking(无根树+思维)
题目 Although Inzane successfully found his beloved bone, Zane, his owner, has yet to return. To searc ...
- $.post 参数定义
//重置密码 function ResetPassword(id, accounts) { //alert("重置密码id-" + id + "-" + acc ...
- Javascript中的"函数是第一类对象(first-class object)"
本身这句话很好解释,函数有两个主要特点,援引自 陈新 译的<JavaScript模式>: 1.函数是第一类对象: 函数可以在运行时动态创建,还可以在程序执行过程中创建. 函数可以分配变量, ...
