RouterOS 设定NAT loopback (Hairpin NAT)回流
In the below network topology a web server behind a router is on private IP address space, and the router performs NAT to forward traffic to its public IP address to the web server behind it.
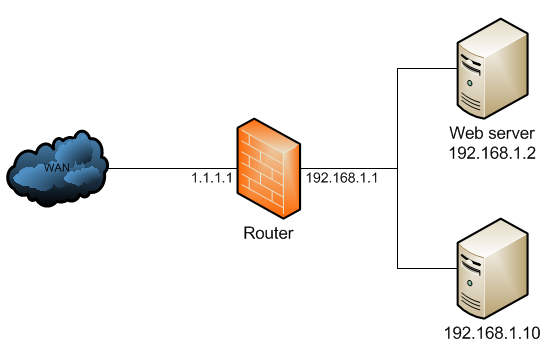
The NAT configuration would look like below:
/ip firewall natadd chain=dstnat dst-address=1.1.1.1 protocol=tcp dst-port=80 \ action=dst-nat to-address=192.168.1.2add chain=srcnat out-interface=WAN action=masquerade
When a client out on the Internet with IP address 2.2.2.2 establishes a connection to the web server, the router performs NAT as configured.
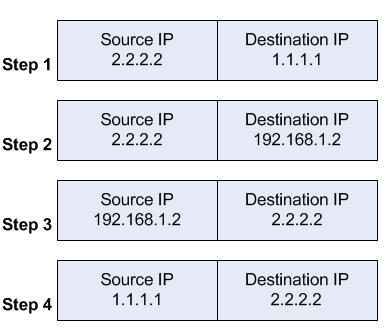
- the client sends a packet with a source IP address of 2.2.2.2 to a destination IP address of 1.1.1.1 on port tcp/80 to request some web resource.
- the router destination NATs the packet to 192.168.1.2 and replaces the destination IP address in the packet accordingly. The source IP address stays the same: 2.2.2.2.
- the server replies to the client's request and the reply packet has a source IP address of 192.168.1.2 and a destination IP address of 2.2.2.2.
- the router determines that the packet is part of a previous connection and undoes the destination NAT, and puts the original destination IP address into the source IP address field. The destination IP address is 2.2.2.2, and the source IP address is 1.1.1.1.
The client receives the reply packet it expects, and the connection is established.
When a client on the same internal network as the web server requests a connection to the web server's public IP address, the connection breaks.
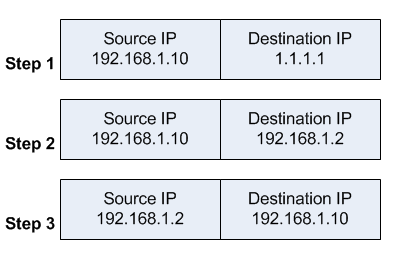
- the client sends a packet with a source IP address of 192.168.1.10 to a destination IP address of 1.1.1.1 on port tcp/80 to request some web resource.
- the router destination NATs the packet to 192.168.1.2 and replaces the destination IP address in the packet accordingly. The source IP address stays the same: 192.168.1.10.
- the server replies to the client's request. However, the source IP address of the request is on the same subnet as the web server. The web server does not send the reply back to the router, but sends it back directly to 192.168.1.10 with a source IP address in the reply of 192.168.1.2.
The client receives the reply packet, but it discards it because it expects a packet back from 1.1.1.1, and not from 192.168.1.2. As far as the client is concerned the packet is invalid and not related to any connection the client previously attempted to establish.
To fix the issue, an additional NAT rule needs to be introduced on the router to enforce that all reply traffic flows through the router, despite the client and server being on the same subnet. The rule below is very specific to only apply to the traffic that the issue could occur with - if there are many servers the issue occurs with, the rule could be made broader to save having one such exception per forwarded service.
/ip firewall natadd chain=srcnat src-address=192.168.1.0/24 \ dst-address=192.168.1.2 protocol=tcp dst-port=80 \ out-interface=LAN action=masquerade
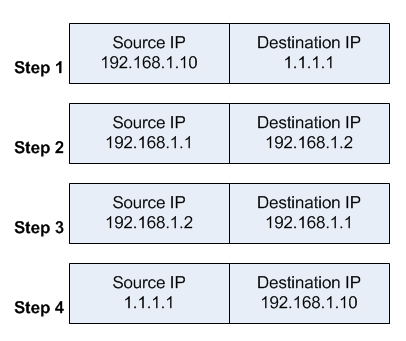
With that additional rule, the flow now changes:
- the client sends a packet with a source IP address of 192.168.1.10 to a destination IP address of 1.1.1.1 on port tcp/80 to request some web resource.
- the router destination NATs the packet to 192.168.1.2 and replaces the destination IP address in the packet accordingly. It also source NATs the packet and replaces the source IP address in the packet with the IP address on its LAN interface. The destination IP address is 192.168.1.2, and the source IP address is 192.168.1.1.
- the web server replies to the request and sends the reply with a source IP address of 192.168.1.2 back to the router's LAN interface IP address of 192.168.1.1.
- the router determines that the packet is part of a previous connection and undoes both the source and destination NAT, and puts the original destination IP address of 1.1.1.1 into the source IP address field, and the original source IP address of 192.168.1.10 into the destination IP address field.
The client receives the reply packet it expects, and the connection is established.
However, the web server only ever sees a source IP address of 192.168.1.1 for all requests from internal clients regardless of the internal client's real IP address. There is no way to avoid this without either using a router that can do application level DNS inspection and can rewrite A records accordingly, or a split DNS server that serves the internal clients the internal server IP address and external clients the external server IP address.
This is called - among other terms - hair pin NAT because the traffic flow has clients enter the router through the same interface it leaves through, which when drawn looks like a hair pin.
RouterOS 设定NAT loopback (Hairpin NAT)回流的更多相关文章
- Linux 与 CONE NAT 和 Symmetric NAT
http://alexanderlaw.blog.hexun.com/31883661_d.html 1. NAT 的划分 RFC3489 中将 NAT 的实现分为四大类: 1. Full Cone ...
- 静态NAT、动态NAT
静态NAT.动态NAT 实验拓扑: 实验目的:熟悉网络地址转换协议 掌握静态NAT 和动态NAT的配置 分析静态NAT 和动态NAT的区别 使用show命令来检查NAT的运行情况 实验要求:按拓扑图来 ...
- 运营商级NAT(Carrier-grade NAT)
运营商级NAT(Carrier-grade NAT) 运营商级(Carrier-grade)NAT,是用于缓解是IPV4地址枯竭的一种方法,通过这种方法,原来被分配公网ip的端点.家庭网络等可以被 ...
- CONE NAT 和 Symmetric NAT
CONE NAT 和 Symmetric NAT 1. NAT 的划分 RFC3489 中将 NAT 的实现分为四大类: Full Cone NAT 完全锥形 NAT Restricted Cone ...
- 什么叫NAT,设置NAT的两个方法
NAT是网络地址翻译就是把公网IP翻译成私有地址, 又叫端口映射或端口转发. 采用路由方式是指ADSL拥有一个动态或固定的公网IP,ADSL直接接在HUB或交换机上,所有的电脑共享上网.这时ADSL的 ...
- NAT and Traversal NAT(TURN/STUN/ICE)
http://www.cnblogs.com/whyandinside/archive/2010/12/08/1900492.html -------------------------------- ...
- 静态NAT、动态NAT、PAT(端口多路复用)的配置
静态NAT.动态NAT.PAT(端口多路复用)的配置 NAT的实现方式有三种,即静态转换Static Nat.动态转换Dynamic Nat 和 端口多路复用OverLoad. 静态转换 ( ...
- NAT原理与NAT穿越
最近在看东西的时候发现很多网络程序中都需要NAT穿越,特意在此总结一下. 先做一个约定: 内网A中有:A1(192.168.0.8).A2(192.168.0.9)两用户 网关X1(一个NAT设备)有 ...
- NAT与FULL NAT的区别
LVS 当前应用主要采用 DR 和 NAT 模式,但这 2 种模式要求 RealServer 和 LVS在同一个 vlan中,导致部署成本过高:TUNNEL 模式虽然可以跨 vlan,但RealSer ...
随机推荐
- phpstorm 常用指令
先选中移动内容 块向右移动:Tab键 块向左移动:Shift + Tab键 ctrl+/行注释ctrl+shift+/块注释 ctrl+g跳转行 alt + 上/下 键实现在类中的方法切换ctrl + ...
- 37行代码实现一个简单的打游戏AI
不废话,直接上码,跟神经网络一点关系都没有,这37行代码只能保证电脑的对敌牺牲率是1:10左右,如果想手动操控,注释掉autopilot后边的代码即可. 哪个大神有兴趣可以用tensorflow或者s ...
- HDU 3998
http://acm.hdu.edu.cn/showproblem.php?pid=3998 求LIS的长度,并且求有多少组互不相交的LIS 求组数用最大流 建图如下: if(dp[i]==1)add ...
- SPSS教程学习笔记1:K个独立样本秩和检验及多重比较 (转载) (非参数假设检验)
本文地址:http://www.datasoldier.net/archives/173版权声明:本文为原创文章,版权归 数据小兵 所有,欢迎分享本文,转载请保留出处! 方差分析经常会出现不满 ...
- 程序运行时间c++/matlab
前言 一般在调试程序的过程中,需要查看代码运行速度的快慢,此时则需要计算代码的运行时间. 实验过程: c++: #include<iostream> #include<time.h& ...
- 20155204 2016-2017-2 《Java程序设计》第7周学习总结
20155204 2016-2017-2 <Java程序设计>第7周学习总结 教材学习内容总结 在只有Lambda表达式的情况下,参数的类型必须写出来,如果有目标类型的话,在编译程序可推断 ...
- 代理模式及Spring AOP (二)
一.Spring AOP 1.1 Spring AOP 底层还是用的动态代理.如果目标对象所对应的类有接口,spring就用jdk生成代理对象: 如果目标对象所对应的类没有接口,spring就用C ...
- HihoCoder - 1501:风格不统一如何写程序
时间限制:10000ms 单点时限:1000ms 内存限制:256MB 描述 小Hi写程序时习惯用蛇形命名法(snake case)为变量起名字,即用下划线将单词连接起来,例如:file_name. ...
- 转-java编译时error: illegal character '\ufeff' 的解决办法-https://blog.csdn.net/t518vs20s/article/details/80833061
原文链接:https://blog.csdn.net/shixing_11/article/details/6976900 最近开发人员通过SVN提交了xxx.java文件,因发布时该包有问题需要回退 ...
- Oracle 跨库 查询 复制表数据
在目前绝大部分数据库有分布式查询的需要.下面简单的介绍如何在oracle中配置实现跨库访问. 比如现在有2个数据库服务器,安装了2个数据库.数据库server A和B.现在来实现在A库中访问B的数据库 ...
