upload-labs-env文件上传漏洞 1-10关
Pass-01
首先先看源码:
function checkFile() {
var file = document.getElementsByName('upload_file')[].value;
if (file == null || file == "") {
alert("请选择要上传的文件!");
return false;
}
//定义允许上传的文件类型
var allow_ext = ".jpg|.png|.gif";
//提取上传文件的类型
var ext_name = file.substring(file.lastIndexOf("."));
//判断上传文件类型是否允许上传
if (allow_ext.indexOf(ext_name + "|") == -) {
var errMsg = "该文件不允许上传,请上传" + allow_ext + "类型的文件,当前文件类型为:" + ext_name;
alert(errMsg);
return false;
}
}
源码发现是前段验证上传文件,那么前段验证绕过的方法就很多也很简单啦
前段的绕过:
1、修改前段的JS,添加白名单
2、浏览器解析禁用JS
3、破坏JS代码,修改引用的地方
4、修改webshell后缀名,shell.php->shell.png,拦截数据包,修改后缀名,最后放行
Pass-02
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . $_FILES['upload_file']['name'];
$is_upload = true; }
} else {
$msg = '文件类型不正确,请重新上传!';
}
} else {
$msg = $UPLOAD_ADDR.'文件夹不存在,请手工创建!';
}
}
在响应中,Content-Type标头告诉客户端实际返回的内容的内容类型
看代码发现是Content-Type请求头白名单验证,那么好我满足你
上传shell.php文件-》抓包-》修改Content-Type请求头为image/jpeg-》上传成功
Pass-03
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array('.asp','.aspx','.php','.jsp'); //黑名单
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空 if(!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR. '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR .'/'. $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = '不允许上传.asp,.aspx,.php,.jsp后缀文件!';
}
} else {
$msg = $UPLOAD_ADDR . '文件夹不存在,请手工创建!';
}
}
通过源码发现这个限制有点多啊=。=,
什么大小写绕过啊,利用windows系统特性的空格和.绕过啊,NTFS文件流绕过啊,MIME验证绕过都不能用啊
最后发现用服务器解析特性可以进行绕过
如以下后缀名有可能被解析为前面的文件(需要服务器的配置文件有解析的配置)
ASP:asa/cer/cdx
ASPX:ashx/asmx/ascx
PHP:php4/php5/phtml
JSP:jspx/jspf
操作步骤:上传shell.php-》抓包-》修改文件为shell.phtml-》上传成功-》成功连接蚁剑(直接连接shell.phtml文件就好)

Pass-04
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空 if (!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = '此文件不允许上传!';
}
} else {
$msg = $UPLOAD_ADDR . '文件夹不存在,请手工创建!';
}
}
源码中除了把03关的禁用了之外,基本跟03相同。
在发现没有前段过滤的情况下,果断的使用.htaccess文件绕过
.htaccess文件是Apache服务器中的一个配置文件,它负责相关目录下的网页配置。通过htaccess文件,可以实现:网页301重定向、自定义404错误页面、改变文件扩展名、允许/阻止特定的用户或者目录的访问、禁止目录列表、配置默认文档等功能
1、创建1.htaccess文件,写入如下代码
<FilesMatch "xxx.jpg">
SetHandler application/x-httpd-php
</FilesMatch>
代码主要作用于把jpg的文件当做php的代码来执行
2、把一句话木马文件改为.jpg格式
3、把1.htaccess和shell.jpg文件分别上传
4、使用蚁剑连接shell.jpg成功
Pass-05
源码:
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
发现源码中什么都有,就是没有大小写绕过,那么好后缀大小写绕过
把shell.php改为shell.PhP
上传shell.PhP文件
Pass-06
源码:
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
缺少首尾去空
利用Windows系统特性,以空格和.结尾的文件对于windows来说,是不允许的,最后保存的 时候把空格和.去掉
上传顺序:上传文件shell.php-》抓包-》在shell.php后面加个空格-》上传成功-》蚁剑连接成功
Pass-07
源码:
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
缺少删除文件名末尾的点
利用Windows系统特性,以空格和.结尾的文件对于windows来说,是不允许的,最后保存的 时候把空格和.去掉
上传顺序:上传文件shell.php-》抓包-》在shell.php后面加个点.-》上传成功-》蚁剑连接成功
Pass-08
源码:
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = trim($file_ext); //首尾去空
没有去除字符串::$DATA,选择利用NTFS文件流绕过,具体如下
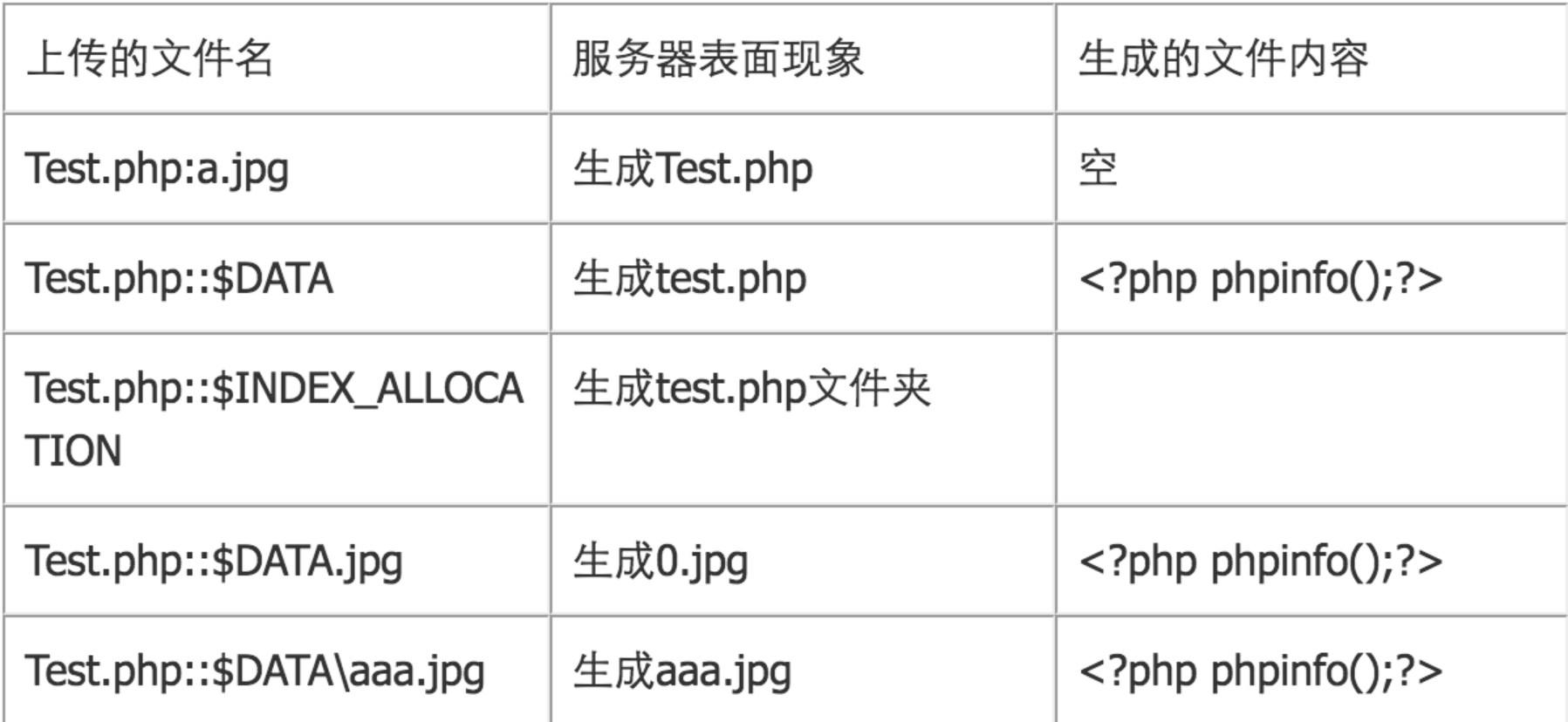
我们这里选择Test.php::$DATA
上传顺序:上传文件shell.php-》抓包-》在shell.php后面加上::$DATA-》上传成功-》蚁剑连接成功
上传成功的文件名为shell.php
Pass-09
源码
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
可以看到源码的处理顺序为,1、删除文件末尾的点,最后在去空
那我们写一个shell.php. . 的文件处理出来是什么样子呢?
答案是shell.php.
所以我们通过bp抓包之后修改文件名为:shell.php. .就可以了
那么最后上传出来的文件是这个样子的 shell.php 所以我们就可以为所欲为啦=。=
Pass-10
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess"); $file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $file_name)) {
$img_path = $UPLOAD_ADDR . '/' .$file_name;
$is_upload = true;
}
} else {
$msg = $UPLOAD_ADDR . '文件夹不存在,请手工创建!';
}
}
$file_name = str_ireplace($deny_ext,"", $file_name);
可以看到上面这句话的大概意思是:如果有黑名单的后缀出现则转换为空
那么能不能也像SQL注入的那样进行双写或者重写呢?
pphphp和phphpp两种双写方式输出的后缀一样吗?
pphphp通过解析完的后缀是php p后面的php通过上面的代码直接转换为了空 所以输出php
而phphpp解析完的后缀则是hpp 所以这种双写是不可以用的
所以我们通过bp抓包之后修改文件名为:shell.pphphp就可以了

upload-labs-env文件上传漏洞 1-10关的更多相关文章
- WordPress NextGEN Gallery ‘upload.php’任意文件上传漏洞
漏洞名称: WordPress NextGEN Gallery ‘upload.php’任意文件上传漏洞 CNNVD编号: CNNVD-201306-259 发布时间: 2013-06-20 更新时间 ...
- 1.5 webshell文件上传漏洞分析溯源(1~4)
webshell文件上传漏洞分析溯源(第一题) 我们先来看基础页面: 先上传1.php ----> ,好吧意料之中 上传1.png ----> 我们查看页面元素 -----> ...
- DVWA 黑客攻防演练(五)文件上传漏洞 File Upload
说起文件上传漏洞 ,可谓是印象深刻.有次公司的网站突然访问不到了,同事去服务器看了一下.所有 webroot 文件夹下的所有文件都被重命名成其他文件,比如 jsp 文件变成 jsp.s ,以致于路径映 ...
- 【DVWA】File Upload(文件上传漏洞)通关教程
日期:2019-08-01 17:28:33 更新: 作者:Bay0net 介绍: 0x01. 漏洞介绍 在渗透测试过程中,能够快速获取服务器权限的一个办法. 如果开发者对上传的内容过滤的不严,那么就 ...
- DVWA之File Upload (文件上传漏洞)
目录 Low: Medium: 方法一:抓包修改文件的type 方法二:00截断 High: Impossible : Low: 源代码: <?php if( isset( $_POST[ 'U ...
- web安全之文件上传漏洞
成因: 当文件上传时,若服务端脚本语言未对上传的文件进行严格验证和过滤,若恶意用户上传恶意的 脚本文件时,就有可能控制整个网站甚至是服务器,这就是文件上传漏洞. 权限: 1. 后台权限:登陆了后台,可 ...
- Web应用安全之文件上传漏洞详解
什么是文件上传漏洞 文件上传漏洞是在用户上传了一个可执行的脚本文件,本通过此脚本文件获得了执行服务器端命令的功能,这种攻击方式是最为直接,最为有效的,有时候,几乎没有什么门槛,也就是任何人都可以进行这 ...
- 文件上传漏洞演示脚本之js验证
文件上传漏洞演示脚本之js验证 0 0 716 关于文件上传漏洞,想必玩web安全的同学们都有接触,之前本站也发布过一篇文章介绍文件上传漏洞的各种绕过方法,但是只是有文档却没有演示代码 ...
- PHP漏洞全解(九)-文件上传漏洞
本文主要介绍针对PHP网站文件上传漏洞.由于文件上传功能实现代码没有严格限制用户上传的文件后缀以及文件类型,导致允许攻击者向某个可通过 Web 访问的目录上传任意PHP文件,并能够将这些文件传递给 P ...
- CVE-2018-20129:DedeCMS V5.7 SP2前台文件上传漏洞
一.漏洞摘要 漏洞名称: DedeCMS V5.7 SP2前台文件上传漏洞上报日期: 2018-12-11漏洞发现者: 陈灿华产品首页: http://www.dedecms.com/软件链接: ht ...
随机推荐
- [原]NTP时钟同步服务设置
服务器列表 192.168.0.2 ntp服务端 192.168.0.3 ntp客户端 192.168.0.4 ntp客户端 192.168.0.5 ntp客户端 注:以下操作均以root操作 一.N ...
- 区分移动端和pc端
区分移动端和pc端: window.navigator.userAgent.toLowerCase().indexOf('mobile')== -1 判断 等于-1就是pc,false就是移动端 ...
- Spring Boot 项目本地运行无异常,部署到 Linux 服务器运行报错:java.lang.ClassNotFoundException
一 背景 最近在用 Springboot 开发项目 A,引了小伙伴开发的模块 B,本地起服务,运行的好好的,等部署到服务器上,一运行就报错:Caused by: java.lang.ClassNotF ...
- py related issues
在python中安装包出现Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) pip inst ...
- linux面试经验
互联网面试想必是每个学计算机的学生必不可少的环节,无论你的项目经验再多,你不准备基础知识,也还是无济于事.首先来说说关于工作的事情. 三年前,那时候我还是刚刚快要大四毕业的小鲜肉,那时候有个超大的招聘 ...
- 【PAT甲级】1029 Median (25 分)
题意: 输入一个正整数N(<=2e5),接着输入N个非递减序的长整数. 输入一个正整数N(<=2e5),接着输入N个非递减序的长整数.(重复一次) 输出两组数合并后的中位数.(200ms, ...
- request和response对象如何解决中文乱码问题?
出现中文乱码的问题,一般的原因编码和和解码不一致造成的. /* 乱码:编码和解码不一致导致的 GET:你好 POST:?????? tomcat版本:8.5及以上版本 GET请求方式,request对 ...
- vector的clear和swap
vector的clear()操作只是清空vector的元素,而不会将内存释放掉 vector<int> vec1{ 1,2,3,4,5 }; vec1.clear(); cout<& ...
- CSS文本居中显示
因为一直为元素居中问题而困扰,所以决定把自己遇到和看到的方法记录下来,以便以后查看 如果要让inline或inline-block元素居中显示,则父元素css中包含text-align:center; ...
- Centos7 nginx 反向代理的配置
一.正向代理与反向代理 1.正向代理 正向代理往VPN理解 正向代理,也就是传说中的代理,他的工作原理就像一个跳板(VPN),简单的说: 我是一个用户,我访问不了某网站,但是我能访问一个代理服务器,这 ...
