Cyber Security - Palo Alto Security Policies(1)
Security policies:
- Enforcing network traffic by configuring rules of what is allowed or denied to communicate between logical network segments (zones)
- Traffic can be policed with the following parameters:
- IP Address (source and/or destination)
- Users
- Services(ports)
- Applications

(From Packt)
- Enforcement hierarchy:
- Is essential to understand the security policy order of enforcement to avoid policy overruling
- "A clean policy table limits the possibility of policy overruling"
Task 1
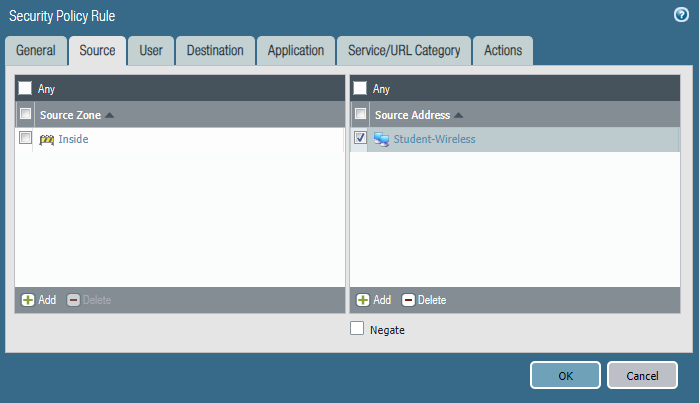
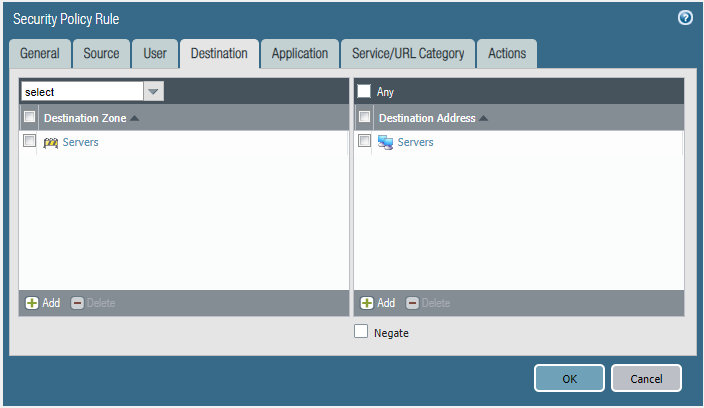
Please block the student wireless network from reaching the server subnet.
Source Zone Source Address Student Wireless: 10.10.0.0/22 Server Subnet: 10.30.0.0/23 Destination Zone Destination Address
Configure the firewall policy.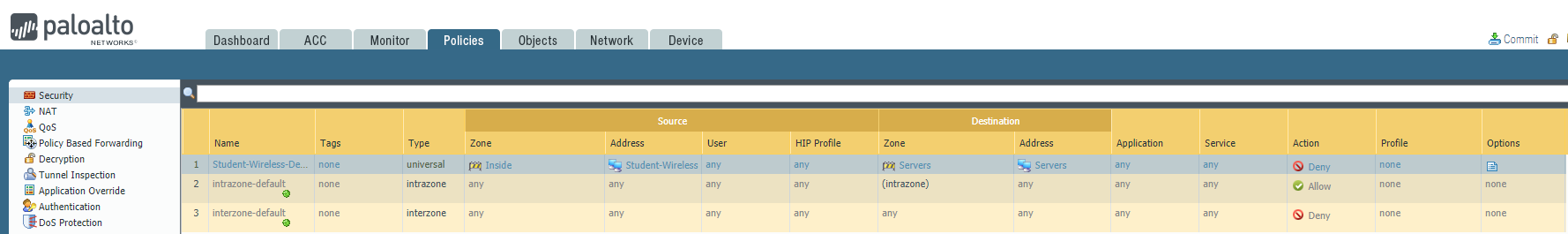


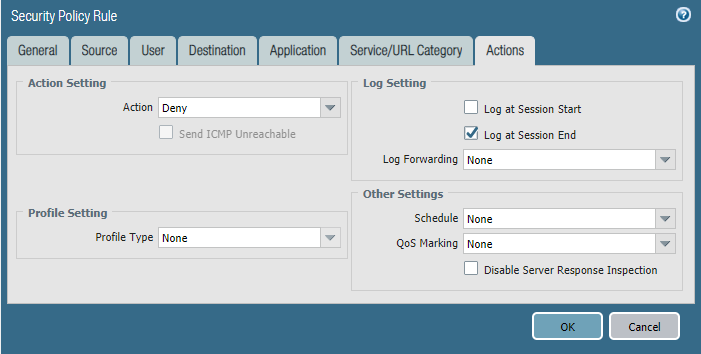
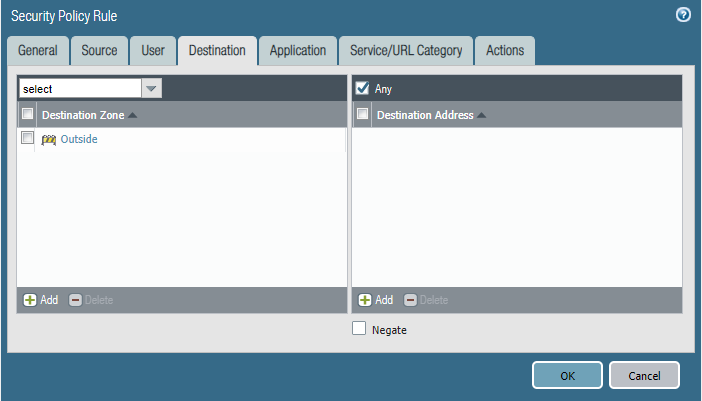
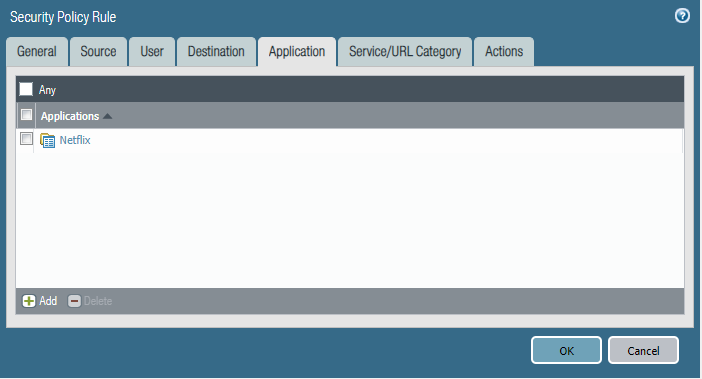
Task 2
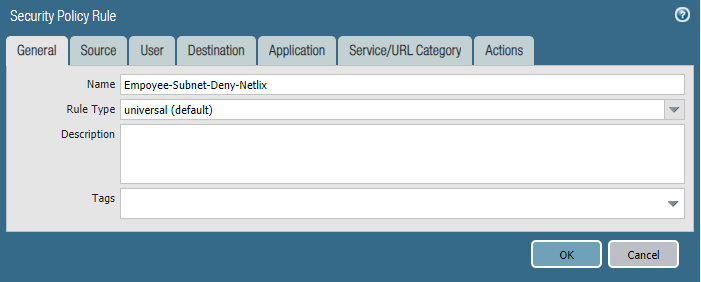
We are getting complaints of employees watching Netflix during work hours and it's causing our internet connection to crawl.
- Please block the employee subnet 10.25.0.0/23 from accessing Netflix.
Configure the firewall policy.


Cyber Security - Palo Alto Security Policies(1)的更多相关文章
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- input属性设置type="number"之后, 仍可输入e;input限制只输入数字
只需在行内输入 onKeyUp="this.value=this.value.replace(/[^\.\d]/g,'');" 就解决了 <input typ ...
- 【JMeter_08】JMeter逻辑控制器__While控制器<While Controller>
While控制器<While Controller> 业务逻辑: 当条件为非false时,执行该节点下的脚本内容,判断条件包括数字.null.空白.字母.符号.true. 当条件为fals ...
- RabbitMQ:三、进阶
保证消息的安全 持久化 交换器持久化:声明交换器时指定持久化 队列持久化:声明队列时指定持久化 消息持久化:发送消息时指定持久化 一般队列和消息持久化要同时声明,此外消息假如进了交换器却找不到队列,也 ...
- python3 闭包函数 装饰器
闭包函数 1.闭:定义在函数内部的函数 2.包:内部函数引用了外部函数作用域的名字 在函数编程中经常用到闭包.闭包是什么,它是怎么产生的及用来解决什么问题呢.给出字面的定义先:闭包是由函数及其相关的引 ...
- mybatis缓存之一级缓存(二)
这篇文章介绍下mybatis的一级缓存的生命周期 一级缓存的产生 一级缓存的产生,并不是看mappper的xml文件的select方法,看下面的例子 mapper.xml <select id= ...
- .NET 5.0预览版6发布:支持Windows ARM64设备
2020年6月25日,微软dotnet团队在博客宣布了第六个 .NET 5.0 的预览版:https://devblogs.microsoft.com/dotnet/announcing-net-5- ...
- EDM邮件制作
EDM营销(Email Direct Marketing)也叫:Email营销.电子邮件营销.是指企业向目标客户发送EDM邮件,建立同目标顾客的沟通渠道,向其直接传达相关信息,用来促进销售的一种营销手 ...
- Python实用笔记 (9)高级特性——列表生成式
列表生成式即List Comprehensions,是Python内置的非常简单却强大的可以用来创建list的生成式. 举个例子,要生成list [1, 2, 3, 4, 5, 6, 7, 8, 9, ...
- 黑鸟码表BB10S骑行记录导入行者
前言 开始骑车用行者app记录, 后来觉得每次都要开app很麻烦, 于是在骑友的推荐下入手了黑鸟BB10S, 使用了一段时间感觉还不错, 不过也遇到之前大家说的问题, 黑鸟不支持直接导出fit文件, ...
- 什么是EL表达式?
1.什么是EL表达式? EL(Expression Language) 是为了使JSP写起来更加简单.表达式语言的灵感来自于 ECMAScript 和 XPath 表达式语言,它提供了在 JSP 中简 ...
