B - Image Perimeters
Technicians in a pathology lab analyze digitized images of slides. Objects on a slide are selected for analysis by a mouse click on the object. The perimeter of the boundary of an object is one useful measure. Your task is to determine this perimeter for selected objects.
The digitized slides will be represented by a rectangular grid of periods, '.', indicating empty space, and the capital letter 'X', indicating part of an object. Simple examples are

An X in a grid square indicates that the entire grid square, including its boundaries, lies in some object. The X in the center of the grid below is adjacent to the X in any of the 8 positions around it. The grid squares for any two adjacent X's overlap on an edge or corner, so they are connected.
XXX
XXX Central X and adjacent X's
XXX
An object consists of the grid squares of all X's that can be linked to one another through a sequence of adjacent X's. In Grid 1, the whole grid is filled by one object. In Grid 2 there are two objects. One object contains only the lower left grid square. The remaining X's belong to the other object.
The technician will always click on an X, selecting the object containing that X. The coordinates of the click are recorded. Rows and columns are numbered starting from 1 in the upper left hand corner. The technician could select the object in Grid 1 by clicking on row 2 and column 2. The larger object in Grid 2 could be selected by clicking on row 2, column 3. The click could not be on row 4, column 3.
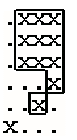
One useful statistic is the perimeter of the object. Assume each X corresponds to a square one unit on each side. Hence the object in Grid 1 has perimeter 8 (2 on each of four sides). The perimeter for the larger object in Grid 2 is illustrated in the figure at the left. The length is 18.
Objects will not contain any totally enclosed holes, so the leftmost grid patterns shown below could NOT appear. The variations on the right could appear:

The input will contain one or more grids. Each grid is preceded by a line containing the number of rows and columns in the grid and the row and column of the mouse click. All numbers are in the range 1-20. The rows of the grid follow, starting on the next line, consisting of '.' and 'X' characters.
The end of the input is indicated by a line containing four zeros. The numbers on any one line are separated by blanks. The grid rows contain no blanks.
For each grid in the input, the output contains a single line with the perimeter of the specified object.
Example input:
2 2 2 2
XX
XX
6 4 2 3
.XXX
.XXX
.XXX
...X
..X.
X...
5 6 1 3
.XXXX.
X....X
..XX.X
.X...X
..XXX.
7 7 2 6
XXXXXXX
XX...XX
X..X..X
X..X...
X..X..X
X.....X
XXXXXXX
7 7 4 4
XXXXXXX
XX...XX
X..X..X
X..X...
X..X..X
X.....X
XXXXXXX
0 0 0 0
Example output:
8
18
40
48
8
垃圾poj,ascall都不能正确输出,这题是求周长的,八个方向都搜一遍就好了,搜完改变自身的值
#include<iostream>
#include<stdio.h>
#include<stdlib.h>
#include <iomanip>
#include<cmath>
#include<float.h>
#include<string.h>
#include<algorithm>
#define sf scanf
#define pf printf
#define pb push_back
#define mm(x,b) memset((x),(b),sizeof(x))
#include<vector>
#include<map>
#define rep(i,a,n) for (int i=a;i<n;i++)
#define per(i,a,n) for (int i=a;i>=n;i--)
typedef long long ll;
typedef long double ld;
typedef double db;
const ll mod=1e12+100;
const db e=exp(1);
using namespace std;
const double pi=acos(-1.0);
char a[25][25];
int sum;
void dfs(int x,int y)
{
// cout<<x<<" "<<y<<endl;
a[x][y]='a';//把经过的位置改变
if(a[x+1][y]=='.')
sum++;
if(a[x-1][y]=='.')
sum++;
if(a[x][y+1]=='.')
sum++;
if(a[x][y-1]=='.')
sum++;
if(a[x-1][y-1]=='X')//左上
dfs(x-1,y-1);
if(a[x-1][y+1]=='X')//右上
dfs(x-1,y+1);
if(a[x+1][y-1]=='X')//左下
dfs(x+1,y-1);
if(a[x+1][y+1]=='X')//右下
dfs(x+1,y+1);
if(a[x-1][y]=='X')//上
dfs(x-1,y);
if(a[x][y-1]=='X')//左
dfs(x,y-1);
if(a[x][y+1]=='X')//右
dfs(x,y+1);
if(a[x+1][y]=='X')//下
dfs(x+1,y);
}
int main()
{
int n,m,x,y;
while(1)
{
sum=0;
char d[25][25];
sf("%d%d%d%d",&n,&m,&x,&y);
if(!n&&!m) return 0;
mm(a,'.');
rep(i,1,n+1)
{
sf("%s",&a[i][1]);
//pf("1%s\n",&d[i]);
a[i][m+1]='.';
}
dfs(x,y);
pf("%d\n",sum);
}
}
B - Image Perimeters的更多相关文章
- ZOJ 1047 Image Perimeters
原题链接 题目大意:鼠标点击一块,求与之联通的所有区域的边长之和. 解法:广度优先搜索.从选中的这个点开始,往周围8个点依次搜索,访问过的点做上标记.如果该点上下左右的一个或多个方向没有相邻的点,边长 ...
- 深搜(DFS),Image Perimeters
题目链接:http://poj.org/problem?id=1111 解题报告: 1.这里深搜有一点要注意,对角线上的点,如果为'.',则total不应该增加,因为这不是他的边长. #include ...
- POJ1111 Image Perimeters
Time Limit: 1000MS Memory Limit: 10000K Total Submissions: 8790 Accepted: 5260 Description Techn ...
- [POJ]1111 Image Perimeters
Description Technicians in a pathology lab analyze digitized images of slides. Objects on a slide ar ...
- poj1111 Image Perimeters 广搜
题目大意: 输入一个矩阵,再输入其中一个“X”的位置(从1开始).从该位置向八个方向扩展,如果是“X”就可以并在一起.问最后得到的模块的周长是多少. 解题思路: 按照广搜的思路来做.用一个二维的数组标 ...
- Image Perimeters
Description 给出一张由"x"和"."组成的矩阵.每个"x"可以向上下左右及两个斜对角进行连通,请问由某个点开始的"x& ...
- Project Euler 94:Almost equilateral triangles 几乎等边的三角形
Almost equilateral triangles It is easily proved that no equilateral triangle exists with integral l ...
- POJ题目细究
acm之pku题目分类 对ACM有兴趣的同学们可以看看 DP: 1011 NTA 简单题 1013 Great Equipment 简单题 102 ...
- HOJ题目分类
各种杂题,水题,模拟,包括简单数论. 1001 A+B 1002 A+B+C 1009 Fat Cat 1010 The Angle 1011 Unix ls 1012 Decoding Task 1 ...
随机推荐
- 使用Let’s Encrypt生成免费的SSL证书
SSL(安全套接层,Secure Sockets Layer),及其继任者 TLS (传输层安全,Transport Layer Security)是为网络通信提供安全及数据完整性的一种安全协议.TL ...
- React页面隐藏#
将 hashHistory 改为 browserHistory 路由用到的,可以在routes.jsx上把hashHistory 改成browserHistory https://github.com ...
- Eclipse 4.5.0 离线安装 Veloeclipse 插件
下载 Veloeclipse 在 Eclipse eclipse-jee-mars-R-win32-x86_64 版本 4.5.0,Build id 为 20150621-1200,离线安装 Velo ...
- Connection is read-only. Queries leading to data modification are not allowed
看了下mysql-connector-5.1.40版本中,如果设置failoverReadOnly=true (即默认值,参考链接),当mysql连接failover时,会根据jdbc连接串将当前连接 ...
- 微软BI 之SSIS 系列 - 变量查询语句引起列输出顺序不一致的解决方法
开篇介绍 这个问题来自于 天善BI社区,看了一下比较有意思,因为我自己认为在 SSIS中处理各种类型文件的经验还比较丰富(有一年的时间几乎所有ETL都跟文件相关),但是这个问题确实之前没有特别考虑过. ...
- Java 基础【17】 异常与自定义异常
1.异常的分类 Throwable 是所有异常类的基类,它包括两个子类:Exception 和 Error. a. 错误 (Error) 错误是无法难通过程序来解决的,所以程序不应该抛出这种类型的对象 ...
- 一个可以参考的JVM内存分配
下面是java命令有关JVM内存分配的参数 JAVA_MEM_OPTS="" BITS=`java -version >& | -bit` if [ -n " ...
- OpenCV 学习笔记 05 人脸检测和识别 AttributeError: module 'cv2' has no attribute 'face'
1 环境设置: win10 python 3.6.8 opencv 4.0.1 2 尝试的方法 在学习人脸识别中,遇到了没有 cv2 中没有 face 属性.在网上找了几个方法,均没有成功解决掉该问题 ...
- git报ssh variant 'simple' does not support setting port解决办法
解决办法 在git bash中输入命令 1 git config --global ssh.variant ssh 照着来一遍,肯定解决
- Winform开发框架之图表报表在线设计器2-图表-SNF.EasyQuery项目--SNF快速开发平台3.3-Spring.Net.Framework
上一篇讲到,如何快速创建报表程序了.这篇教大家如何快速制作图表报表. 继上一篇,Winform开发框架之图表报表在线设计器-报表 上一篇讲到如何了创建数据源,这里就不在介绍了.那我们就直接从图表设计器 ...
