Lab 3-2
Analyze the malware found in the file Lab03-02.dll using basic dynamic analysis tools.
Questions and Short Answers
How can you get this malware to install itself?
A: To install the malware as a service, run the malware’s exported installA function via rundll32.exe with rundll32.exe Lab03-02.dll,installA.
How would you get this malware to run after installation?
A: To run the malware, start the service it installs using the net command net start IPRIP.
How can you find the process under which this malware is running?
A: Use Process Explorer to determine which process is running the service. Since the malware will be running within one of the svchost.exe files on the system, hover over each one until you see the service name, or search for Lab03-02.dll using the Find DLL feature of Process Explorer.
Which filters could you set in order to use procmon to glean information?
A: In procmon you can filter on the PID you found using Process Explorer.

What are the malware’s host-based indicators?
A: By default, the malware installs as the service IPRIP with a display name of Intranet Network Awareness (INA+) and description of “Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes.” It installs itself for persistence in the registry at HKLM\SYSTEM\CurrentControlSet\Services\IPRIP Parameters\ServiceDll: %CurrentDirectory%\Lab03-02.dll. If you rename Lab03-02.dll to something else, such as malware.dll, then it writes malware.dll into the registry key, instead of using the name Lab03-02.dll.
Are there any useful network-based signatures for this malware?
A: The malware resolves the domain name practicalmalwareanalysis.com and connects to that host over port 80 using what appears to be HTTP. It does a GET request for serve.html and uses the User-Agent %ComputerName% Windows XP 6.11.
Detailed Analysis
We begin with basic static analysis by looking at the PE file structure and strings. Figure 3-5L shows that this DLL has five exports, as listed from \({\color{red}1}\) and below. The export ServiceMain suggests that this malware needs to be installed as a service in order to run properly.

Figure 3-5L: PEview of Lab03-02.dll exports
The following listing shows the malware’s interesting imported functions in bold.

These include service-manipulation functions, such as CreateService, and registry-manipulation functions, such as RegSetValueEx. Imported networking functions, such as HttpSendRequest, suggest that the malware uses HTTP.
Next, we examine the strings, as shown in the following listing.
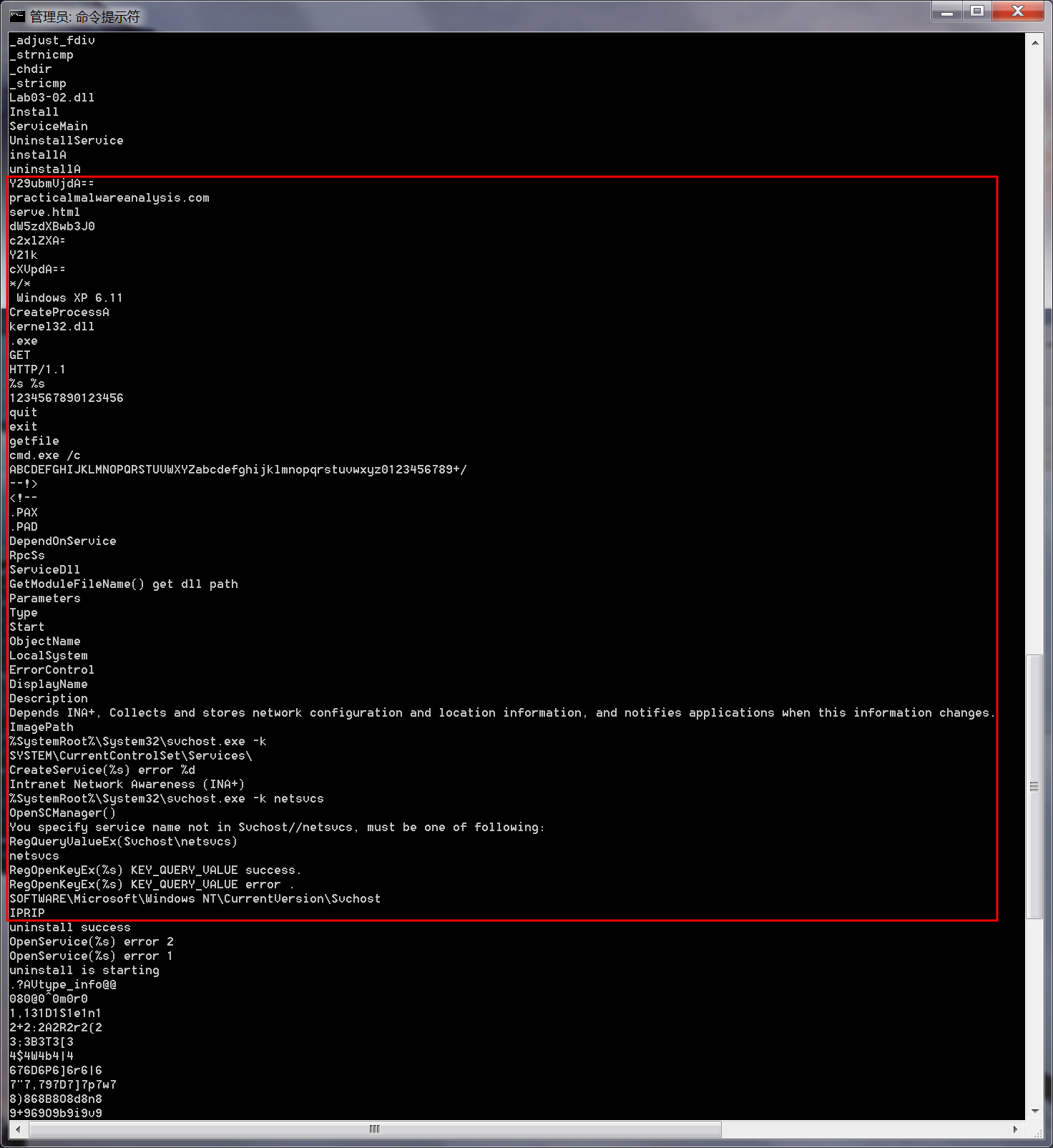
We see several interesting strings, including registry locations, a domain name, unique strings like IPRIP and serve.html, and a variety of encoded strings. Basic dynamic techniques may show us how these strings and imports are used.
The results of our basic static analysis techniques lead us to believe that this malware needs to be installed as a service using the exported function installA. We’ll use that function to attempt to install this malware, but before we do that, we’ll launch Regshot to take a baseline snapshot of the registry and use Process Explorer to monitor the processes running on the system. After setting up Regshot and Process Explorer, we install the malware using rundll32.exe, as follows:
C:\>rundll32.exe Lab03-02.dll,installA
注:win7中无法复现,使用Windows XP可成功复现。
After installing the malware, we use Process Explorer to confirm that it has terminated by making sure that rundll32.exe is no longer in the process listing. Next, we take a second snapshot with Regshot to see if the malware installed itself in the registry.
The edited Regshot results are shown in the following listing.
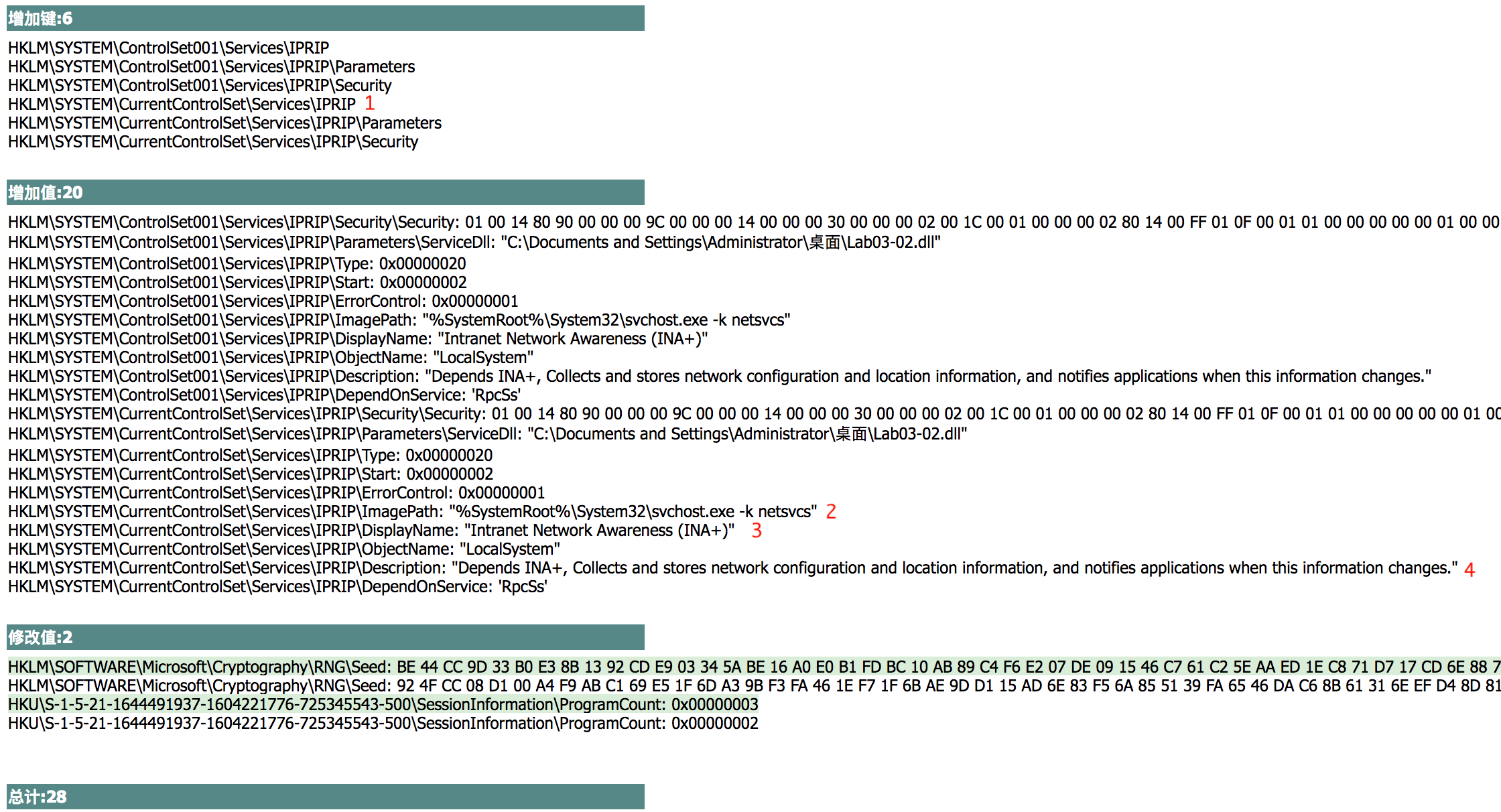

The Keys added section shows that the malware installed itself as the service IPRIP at \({\color{red}1}\). Since the malware is a DLL, it depends on an executable to launch it. In fact, we see at \({\color{red}2}\) that the ImagePath is set to svchost.exe, which means that the malware will be launched inside an svchost.exe process. The rest of the information, such as the DisplayName and Description at \({\color{red}3}\) and \({\color{red}4}\), creates a unique fingerprint that can be used to identify the malicious service.
If we examine the strings closely, we see SOFTWARE\Microsoft\Windows NT CurrentVersion\SvcHost and a message "You specify service name not in Svchost// netsvcs, must be one of following". If we follow our hunch and examine the \SvcHost\netsvcs registry key, we can see other potential service names we might use, like 6to4 AppMgmt. Running Lab03-02.dll,installA 6to4 will install this malware under the 6to4 service instead of the IPRIP service, as in the previous listing.
After installing the malware as a service, we could launch it, but first we’ll set up the rest of our basic dynamic tools. We run procmon (after clearing out all events); start Process Explorer; and set up a virtual network, including ApateDNS and Netcat listening on port 80 (since we see HTTP in the strings listing).
Since this malware is installed as the IPRIP service, we can start it using the net command in Windows, as follows:
C:\>net start IPRIP
The Intranet Network Awareness (INA+) service is starting.
The Intranet Network Awareness (INA+) service was started successfully.The fact that the display name (INA+) matches the information found in the registry tells us that our malicious service has started.
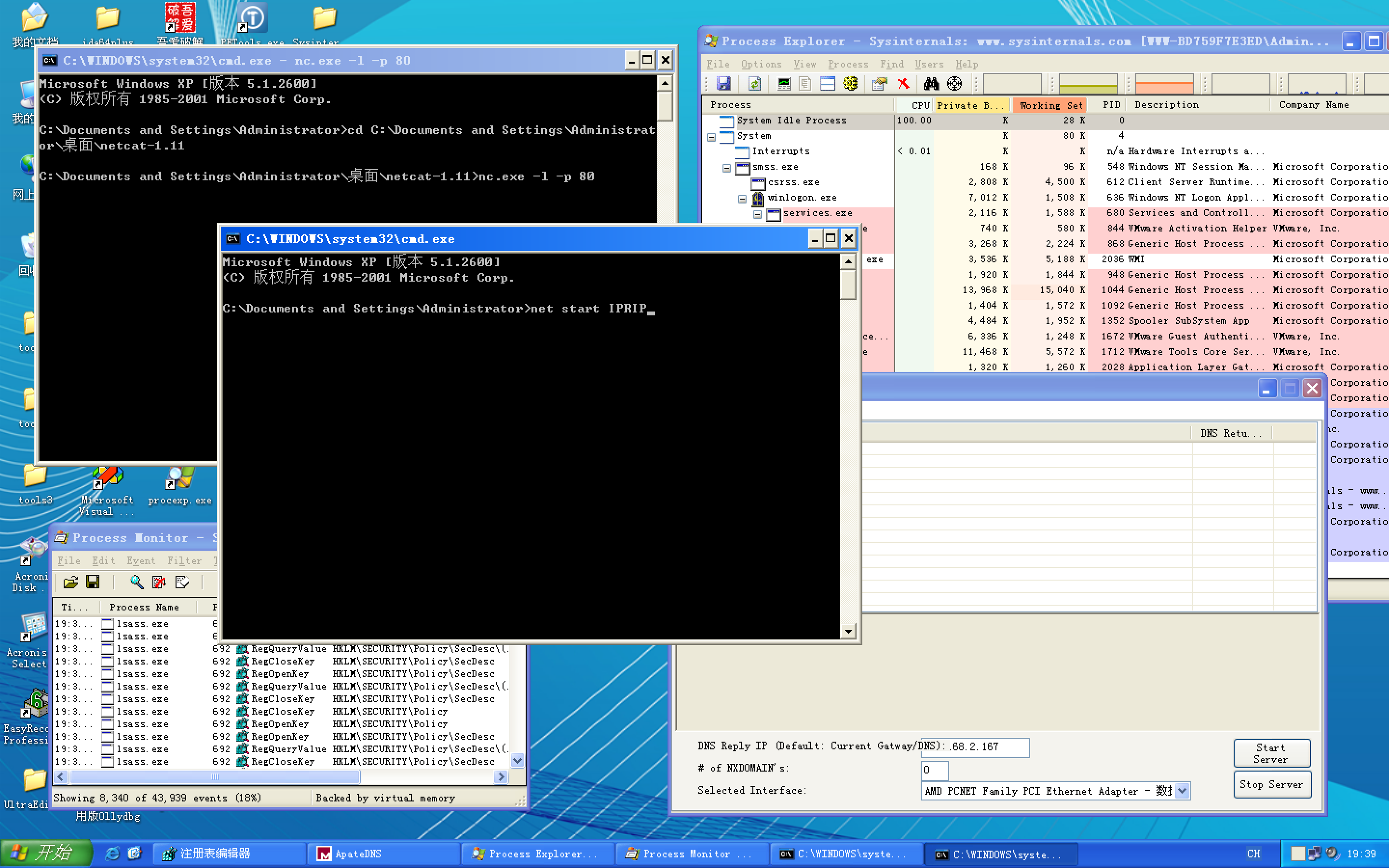
注:上图按 Enter 键前,记得ApateDNS软件点击Start Server。

Next, we open Process Explorer and attempt to find the process in which the malware is running by selecting Find -> Find Handle or DLL to open the dialog shown in Figure 3-6L. We enter Lab03-02.dll and click Search. As shown in the figure, the result tells us that Lab03-02.dll is loaded by svchost.exe with the PID 1044. (The specific PID may differ on your system.)
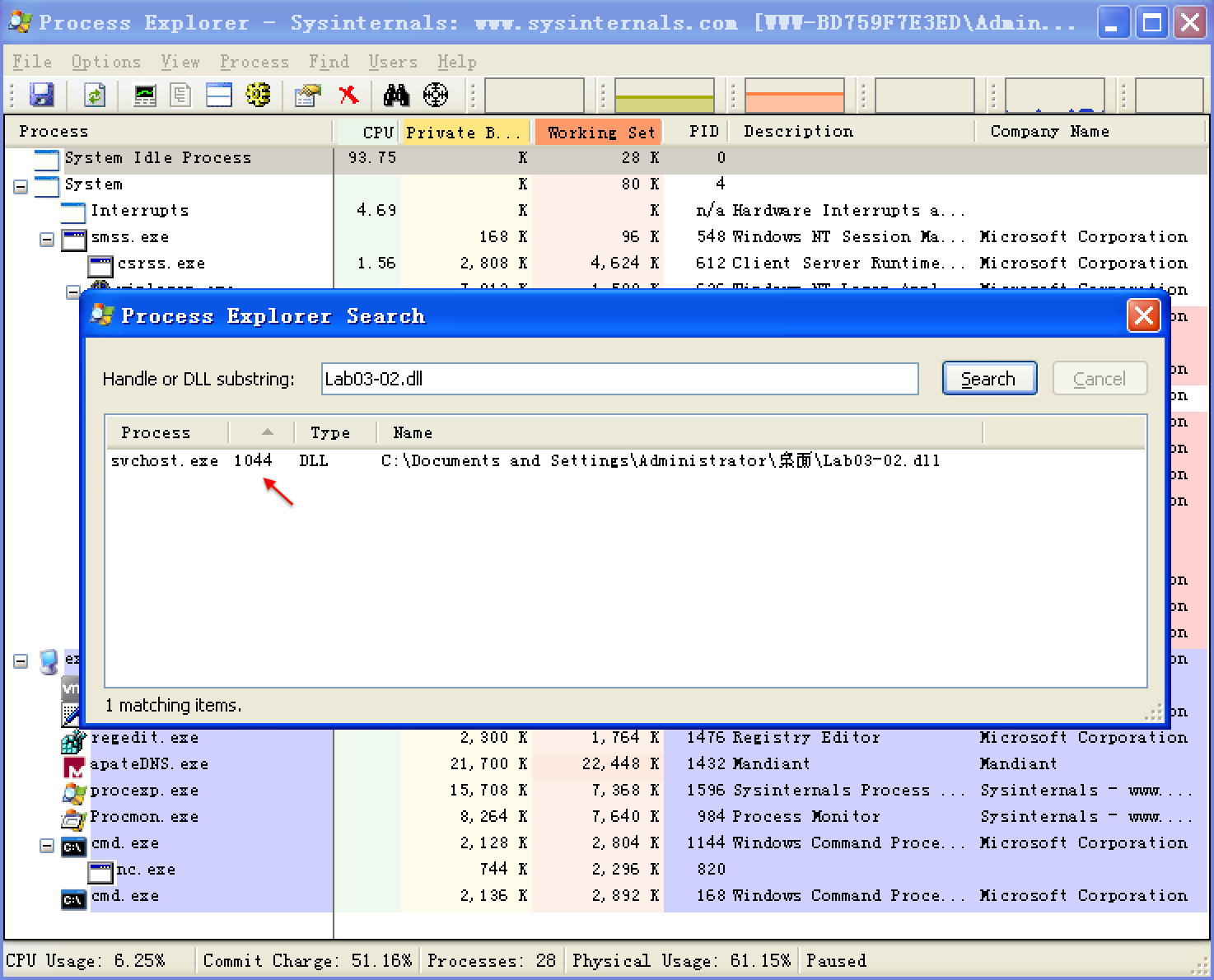
Figure 3-6L: Searching for a DLL in Process Explorer
In Process Explorer, we select View -> Lower Pane View -> DLLs and choose the svchost.exe running with PID 1044. Figure 3-7L shows the result. The display name Intranet Network Awareness (INA+) shown at \({\color{red}1}\) confirms that the malware is running in svchost.exe, which is further confirmed when we see at \({\color{red}2}\) that Lab03-02.dll is loaded.

Figure 3-7L: Examining service malware in Process Explorer
Next, we turn our attention to our network analysis tools. First, we check ApateDNS to see if the malware performed any DNS requests. The output shows a request for practicalmalwareanalysis.com, which matches the strings listing shown earlier.
NOTE
It takes 60 seconds after starting the service to see any network traffic (the program does a Sleep(60000) before attempting network access). If the networking connection fails for any reason (for example, you forgot to set up ApateDNS), it waits 10 minutes before attempting to connect again.
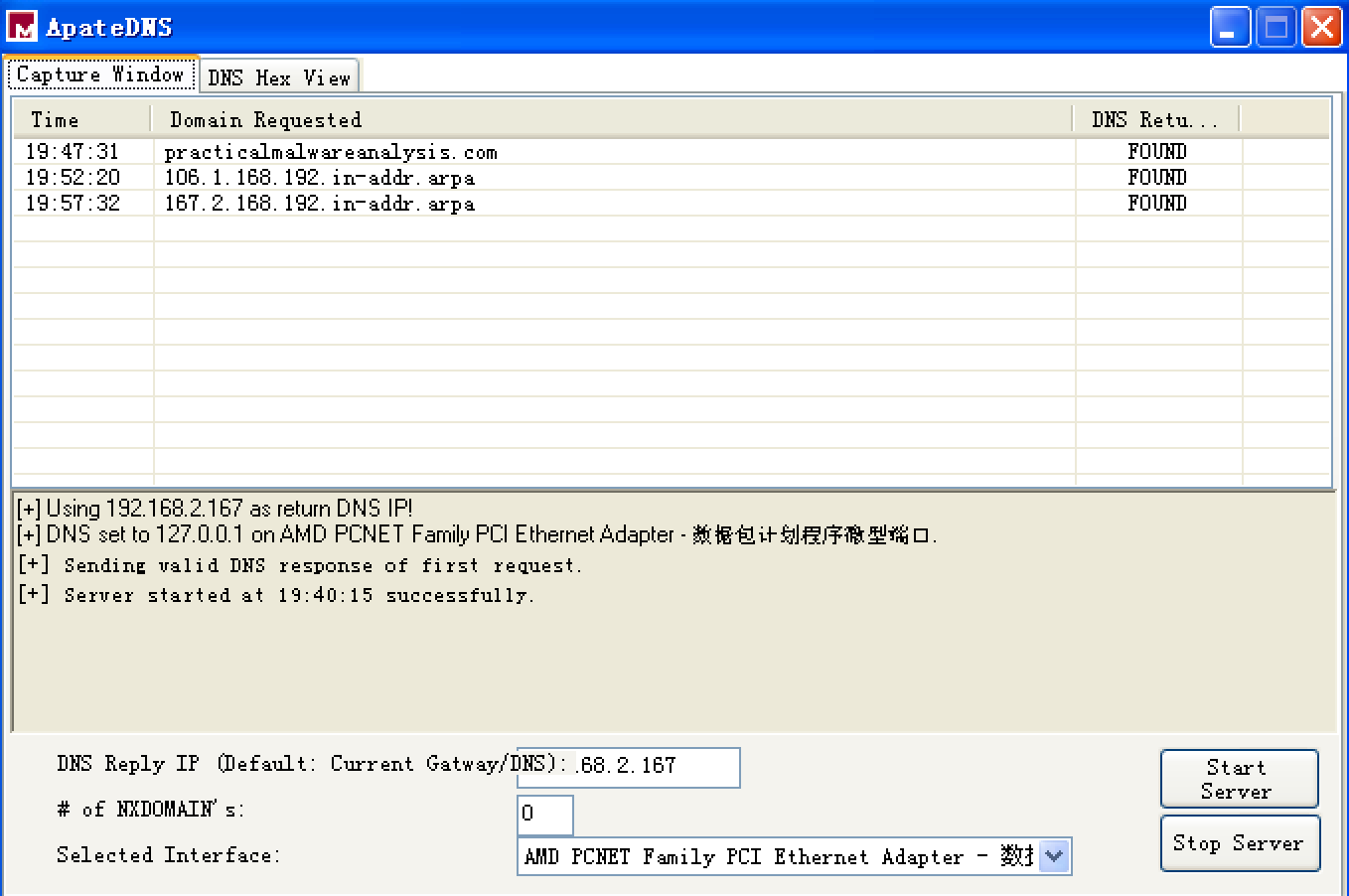
双击 ApateDNS 的 Capture Window 窗口的 Domain Requested 相应条目,显示 DNS Hex View,如下:
最后 ApateDNS 点击 Stop Server,在服务器端,快捷键 control + c 结束服务器,查看生成的日志文件 report.3385.txt 如下:

We complete our network analysis by examining the Netcat results, as follows:

书中的结果是如下:

We see that the malware performs an HTTP GET request over port 80 (we were listening over port 80 with Netcat since we saw HTTP in the string listing). We run this test several times, and the data appears to be consistent across runs.
We can create a couple of network signatures from this data. Because the malware consistently does a GET request for serve.html, we can use that GET request as a network signature. The malware also uses the User-Agent MalwareAnalysis2 Windows XP 6.11. MalwareAnalysis2 is our malware analysis virtual machine’s name (so this portion of the User-Agent will be different on your machine). The second part of the User-Agent (Windows XP 6.11) is consistent and can be used as a network signature.
Preference
Lab 3-2的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- topcoder srm 485 div1
problem1 link 枚举第一个数和第二个数即可确定公差. problem2 link 设高度为$n$,宽度为$m$,且$n \ge m$ 如果$m \ge 5$,那么答案为0.这个可以通过抽屉 ...
- topcoder srm 713 div1
problem1 link 如果$a^{b}=c^{d}$,那么一定存在$t,x,y$使得$a=t^{x},c=t^{y}$.一旦$t,x,y$确定,那么可以直接计算出二元组$b,d$有多少.对于$t ...
- Linux使用——Linux命令——Linux 系统基本命令使用记录
查看系统版本信息 查看系统版本:cat /proc/version 查看cpu相关信息,包括型号.主频.内核信息:cat /proc/cpuinfo 快速了解CPU使用情况:free -h 解压文件 ...
- 【做题】CF196E. Opening Portals 排除无用边&最小生成树
题意:给出一个有\(n\)个结点,\(m\)条边的连通无向图,边有边权,等于经过这条边所需的时间.有\(k\)个点设有传送门.一开始,所有传送门关闭.你从\(1\)号点出发,每当你到达一个有传送门的点 ...
- Linux/shell: Concatenate multiple lines to one line
$ cat file START Unix Linux START Solaris Aix SCO 1. Join the lines following the pattern START with ...
- Eclipse和Tomcat使用过程的一些配置、错误等的总结记录
背景:公司项目使用jdk1.6.tomcat7.SVN,本文总结使用到现在的一些配置和问题. 1.Eclipse项目几点配置:(1)Windows -> Preferences -> Ja ...
- 题解——ATCoder AtCoder Grand Contest 017 B - Moderate Differences(数学,构造)
题面 B - Moderate Differences Time limit : 2sec / Memory limit : 256MB Score : 400 points Problem Stat ...
- Twenty score
1.上图中有两个人对读书的看法有较大的不同. There are two people in the cartoon who treat books in completely different w ...
- Netty 核心组件笔记
Netty是一款高效的NIO框架和工具,基于JAVA NIO提供的API实现. 在JAVA NIO方面Selector给Reactor模式提供了基础,Netty结合Selector和Reactor模式 ...
- javascript创建函数的20种方式汇总
http://www.jb51.net/article/68285.htm 工作中常常会创建一个函数来解决一些需求问题,以下是个人在工作中总结出来的创建函数20种方式,你知道多少? function ...
