Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment:
Download and Install Pan-OS from the following website https://docs.gns3.com/appliances/pan-vm-fw.html or https://me.csdn.net/download/hotbrandon

URL https://IP
Default Username/Password: admin/admin
PAN-OS 8 Configuration Tabs:
- Object tab: Configure Firewall objects(address - services - object groups)
- Policy tab: Configure Firewall policies(security -NAT -QoS - PBR)
- Network tab: Configure Firewall interfaces and routing settings
- Device tab: Perform maintenance tasks and administrative tasks.
- Configuration backup and restore.
- High availability.
- Users and administrators.
- Directory synchronization(Active Directory)
PAN-OS 8 Monitoring Tabs:
- ACC Tab: Application command center overview
- Monitor tab: User traffic monitoring based on applied policies
Dashboard:
Console - Based Administration
Action commands - show, request, test, configure
CLI structure:{action}{section}{element}
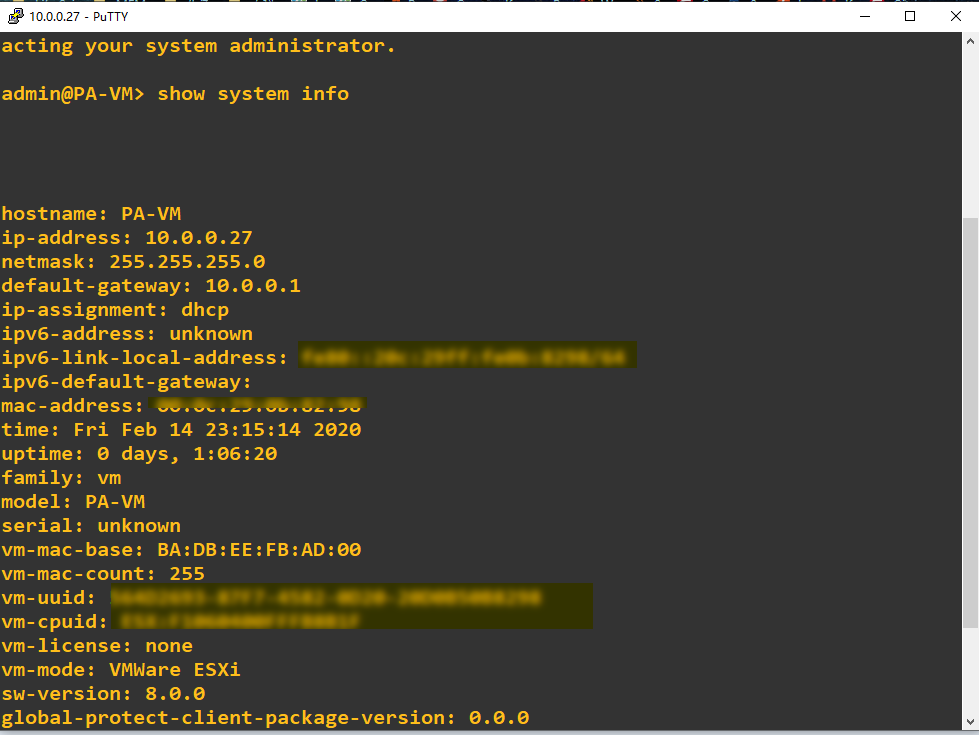
show:
show system info
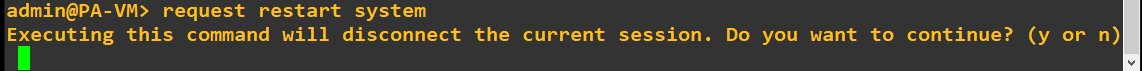
request:
request system restart
Test:
test vpn ike-sa gateway {name}
test vpn ipsec-sa gateway {name}
Device Management Overview
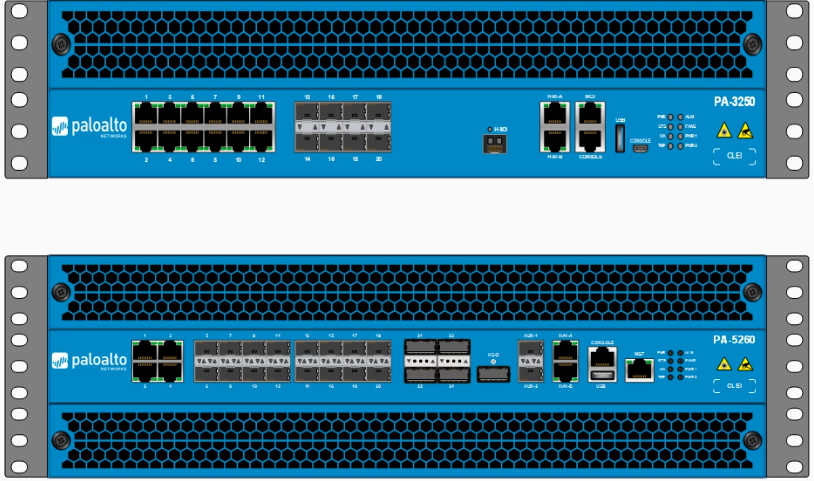
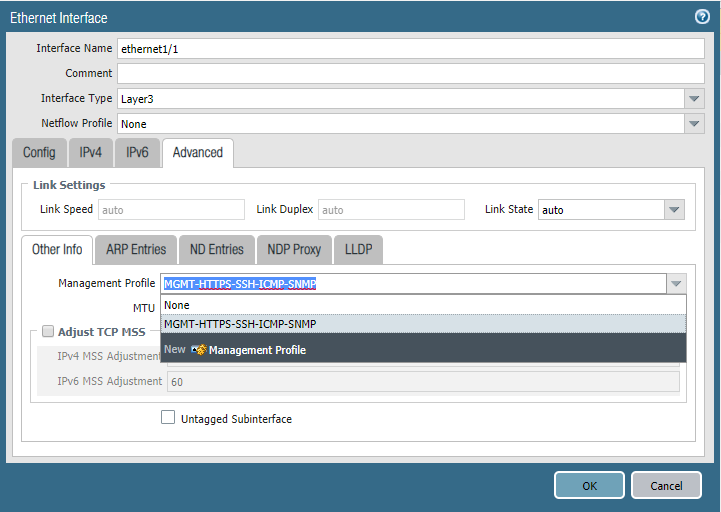
Interface Management Profile
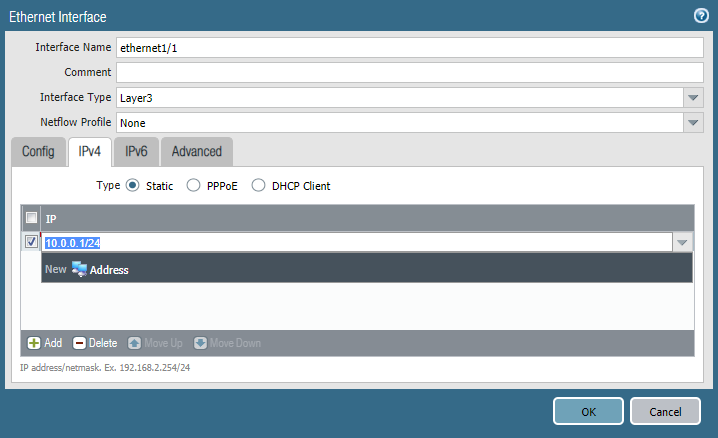
Ethernet Interface
Local admin
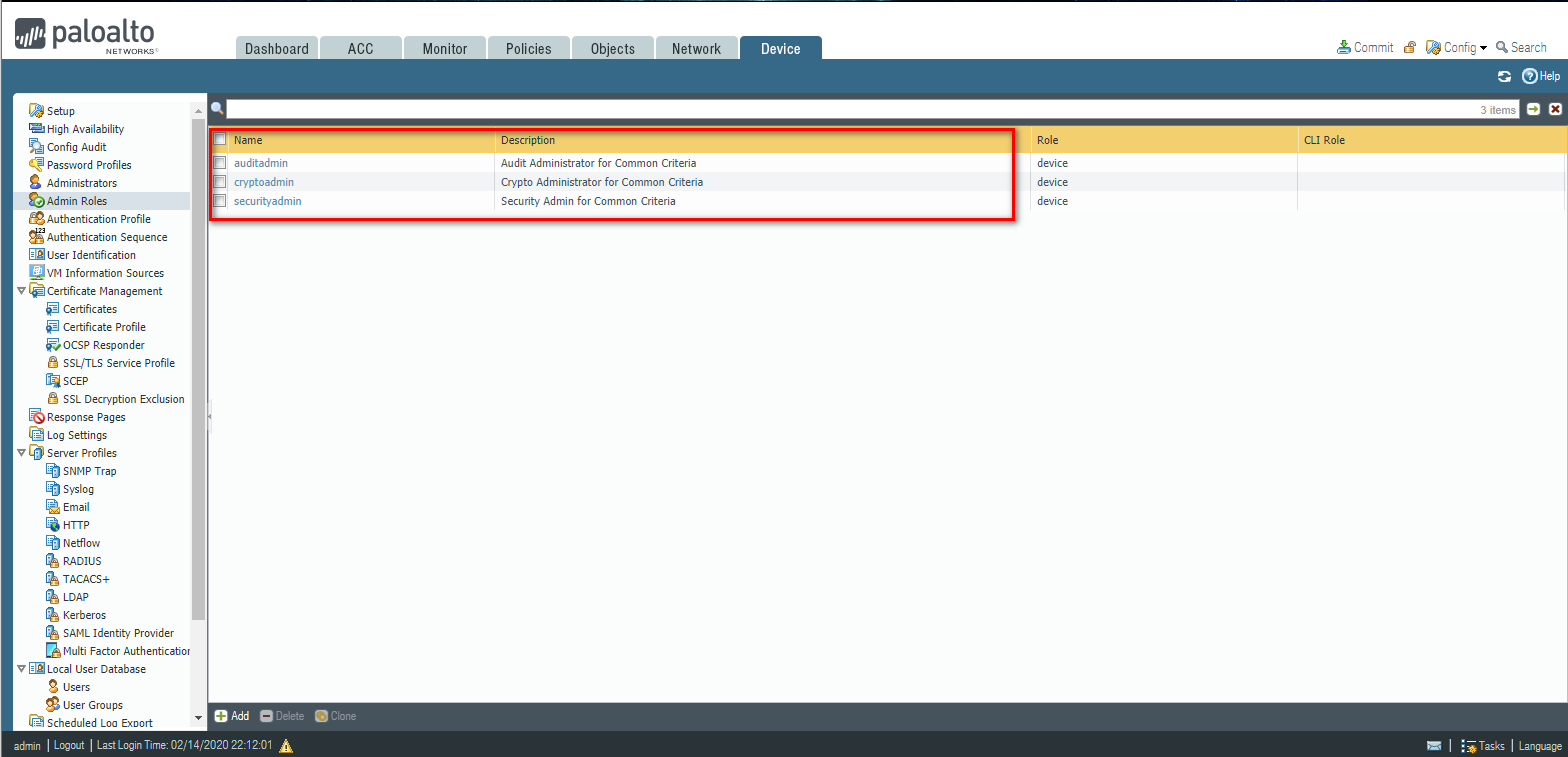
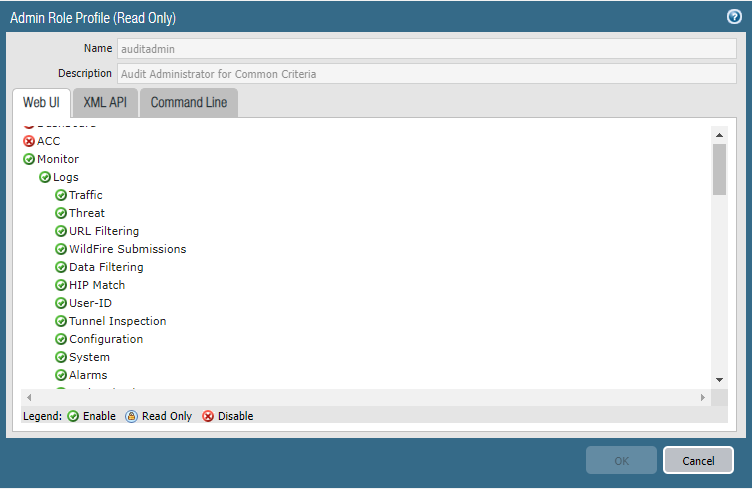
Create a new Role Profile(All function except Policies, Objects, Device, and Privacy.)
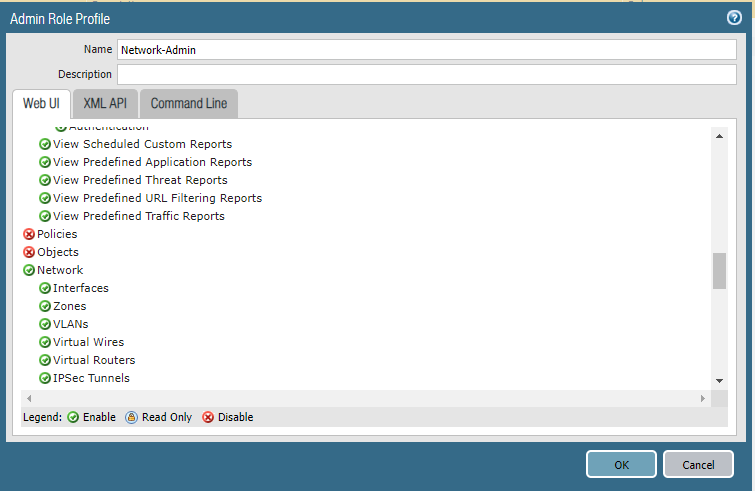
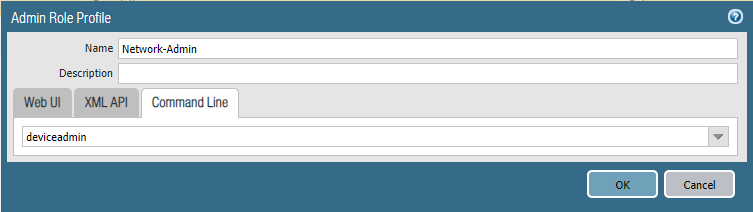
Add a new network administrator.

Cyber Security - Palo Alto Basic Introduction的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 通过char与varchar的区别,学习可变长的字符类型
转自http://www.uphtm.com/database/232.html 在mysql教程中char与varchar的区别呢,都是用来存储字符串的,只是他们的保存方式不一样罢了,char有固定 ...
- php读取富文本处理html标签问题
thinkphp的一项配置会将富文本编辑器的内容中的html标签进行转义处理 'DEFAULT_FILTER' => 'htmlspecialchars', // 默认参数过滤方法使用htmls ...
- web api(基于NFine框架) 中接口跳转数据格式错误解决方案
using NFine.Code; using NFine.Domain; using System.Web.Http; using Newtonsoft.Json; namespace Api.Co ...
- PHP丨PHP基础知识之流程控制WHILE循环「理论篇」
昨天讲完FOR循环今天来讲讲他的兄弟WHILE循环!进入正题: while是计算机的一种基本循环模式.当满足条件时进入循环,进入循环后,当条件不满足时,跳出循环.while语句的一般表达式为:whil ...
- 【K8S学习笔记】初识K8S 及架构组件
K8S是什么?发展历史 Kubernetes (简称 k8s)是 Google 在2014年开源的,对容器生命周期管理的开源平台,致力于对容器集群提供易于管理.高可用.弹性负载与故障转移的能力,提高服 ...
- java中的excel操作
导入jxl.jar包: 下载个jxl.jar包,然后这个包放在什么位置都行,在你的项目中导入这个包就可以. 具体做法: 项目上右键,点击“属性”, 类别那里选择”库“,点击"添加jar文 ...
- 基于领域驱动设计(DDD)超轻量级快速开发架构
smartadmin.core.urf 这个项目是基于asp.net core 3.1(最新)基础上参照领域驱动设计(DDD)的理念,并参考目前最为了流行的abp架构开发的一套轻量级的快速开发web ...
- C# 9.0 新特性之只读属性和记录
阅读本文大概需要 2 分钟. 大家好,这是 C# 9.0 新特性系列的第 4 篇文章. 熟悉函数式编程的童鞋一定对"只读"这个词不陌生.为了保证代码块自身的"纯洁&quo ...
- Shiro授权
Shiro三种授权方式 编程式:通过写 if/else 授权代码块完成: Subject subject = SecurityUtils.getSubject(); if(subject.hasRol ...
- Linux远程连接mongodb
当没有客户端工具,eg:robo3T时,如何修改mongodb里的数据呢? 1.连接mongodb服务器mongo 1.1.1.1:1688 2.查看数据库列表show dbs 3.选择使用log库u ...
