Envoy:TLS双向认证
环境准备
| 主机 | 角色 | 数量 |
|---|---|---|
| front-envoy | front envoy | 1 |
| service envoy | 作为内部后端的envoy | 2 |
| end | 后端应用程序 | 2 |
访问 / front-envoy ==> end * 2
访问 /red/colorful ==> end red 不验证客户端证书 单项tls
访问 /gray/colorful ==> end gray 验证客户端证书 双项tls
docker-compose
version: '3'
services:
front-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
ports:
- 80:80
- 443:443
- 82:9901
volumes:
- ./envoy.yaml:/etc/envoy/envoy.yaml
- ./certs/front-envoy/:/etc/envoy/certs/
- ./certs/CA/:/etc/envoy/ca/
networks:
envoymesh:
aliases:
- front-envoy
depends_on:
- webserver1
- webserver2
gray-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
volumes:
- ./service_gray.yaml:/etc/envoy/envoy.yaml
- ./certs/service_gray/:/etc/envoy/certs/
- ./certs/CA1/:/etc/envoy/ca/
network_mode: "service:webserver1"
depends_on:
- webserver1
red-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
volumes:
- ./service_red.yaml:/etc/envoy/envoy.yaml
- ./certs/service_red/:/etc/envoy/certs/
- ./certs/CA1/:/etc/envoy/ca/
network_mode: "service:webserver2"
depends_on:
- webserver2
webserver1:
image: sealloong/envoy-end:latest
networks:
envoymesh:
aliases:
- service_gray
- front_envoy
environment:
- VERSION=v1
- COLORFUL=gray
expose:
- 90
webserver2:
image: sealloong/envoy-end:latest
networks:
envoymesh:
aliases:
- service_red
- front_envoy
environment:
- VERSION=v1
- COLORFUL=red
expose:
- 90
networks:
envoymesh: {}
front-envoy
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
secrets:
- name: servers
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
- name: clients
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/client.crt"
private_key:
filename: "/etc/envoy/certs/client.key"
- name: validation
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
listeners:
- name: listener_http
address:
socket_address: { address: 0.0.0.0, port_value: 80 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
codec_type: auto
stat_prefix: ingress_http
route_config:
name: local_route
virtual_hosts:
- name: service
domains: [ "*" ]
routes:
- match: { prefix: "/" }
redirect:
https_redirect: true
port_redirect: 443
http_filters:
- name: envoy.router
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/gray/colorful" }
route:
prefix_rewrite: "/colorful"
cluster: gray
- match: { prefix: "/red/colorful" }
route:
prefix_rewrite: "/colorful"
cluster: red
- match: { prefix: "/" }
route:
cluster: front_envoy
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: servers
clusters:
- name: front_envoy
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: front_envoy
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: front_envoy, port_value: 90 }
- name: gray
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: gray
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: service_gray, port_value: 443 }
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: clients
validation_context_sds_secret_config:
name: validation
- name: red
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: red
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: service_red, port_value: 443 }
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: clients
service gray
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
listeners:
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/" }
route:
cluster: service_gray
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
require_client_certificate: true
clusters:
- name: service_gray
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: service_gray
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: 127.0.0.1, port_value: 90 }
service red
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
listeners:
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/" }
route:
cluster: service_red
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
- certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
clusters:
- name: service_red
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: service_red
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: 127.0.0.1, port_value: 90 }
配置说明
docker-compose
network_mode: "service:webserver1" 指定网络类型,使envoy和后端程序运行在一个网络下
secrets:
- name: servers
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
- name: clients
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/client.crt"
private_key:
filename: "/etc/envoy/certs/client.key"
- name: validation
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
server
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
validation_context: # 验证机制的相关配置
trusted_ca: # 信任的ca证书,未指定时不会验证对端证书
filename: "/etc/envoy/ca/ca.crt" # 这里指定的为根ca
require_client_certificate: true # boolval 设置为ture,Envoy将拒绝没有有效客户端证书的连接。
验证结果
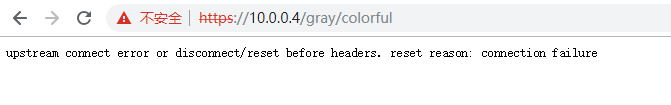
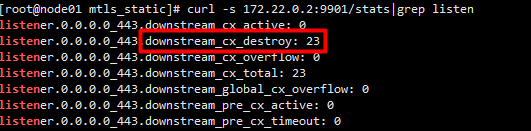
/gray/colorful后端服务开启了验证客户端ca,访问报错,后端程序并没收到请求,因证书无效,envoy销毁了请求
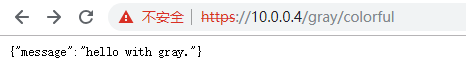
将根ca设置为可信任后
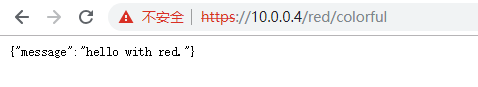
/red/colorful 没开启验证客户端证书
Envoy:TLS双向认证的更多相关文章
- linux运维、架构之路-Kubernetes集群部署TLS双向认证
一.kubernetes的认证授权 Kubernetes集群的所有操作基本上都是通过kube-apiserver这个组件进行的,它提供HTTP RESTful形式的API供集群内外客户端调 ...
- tls 双向认证 client端代码例子
example: python import httplib import json import ssl import urllib2 import requests CA_FILE = " ...
- 使用wireshark观察SSL/TLS握手过程--双向认证/单向认证
SSL/TLS握手过程可以分成两种类型: 1)SSL/TLS 双向认证,就是双方都会互相认证,也就是两者之间将会交换证书.2)SSL/TLS 单向认证,客户端会认证服务器端身份,而服务器端不会去对客户 ...
- SSL双向认证和SSL单向认证的流程和区别
refs: SSL双向认证和SSL单向认证的区别https://www.jianshu.com/p/fb5fe0165ef2 图解 https 单向认证和双向认证!https://cloud.tenc ...
- php实现https(tls/ssl)双向认证
php实现https(tls/ssl)双向认证 通常情况下,在部署https的时候,是基于ssl单向认证的,也就是说只要客户端认证服务器,而服务器不需要认证客户端. 但在一些安全性较高的场景,如银行, ...
- mosquitto ---SSL/TLS 单向认证+双向认证
生成证书 # * Redistributions in binary form must reproduce the above copyright # notice, this list of ...
- https 单向双向认证说明_数字证书, 数字签名, SSL(TLS) , SASL_转
转自:https 单向双向认证说明_数字证书, 数字签名, SSL(TLS) , SASL 因为项目中要用到TLS + SASL 来做安全认证层. 所以看了一些网上的资料, 这里做一个总结. 1. 首 ...
- 基于mosquitto的MQTT服务器---SSL/TLS 单向认证+双向认证
基于mosquitto的MQTT服务器---SSL/TLS 单向认证+双向认证 摘自:https://blog.csdn.net/ty1121466568/article/details/811184 ...
- tomcat配置SSL双向认证
一.SSL简单介绍 SSL(Secure Sockets Layer 安全套接层)就是一种协议(规范),用于保障客户端和服务器端通信的安全,以免通信时传输的信息被窃取或者修改. 怎样保障数据传输安全? ...
随机推荐
- istio sidecar使用自定义镜像源
Istio 和 sidecar 配置保存在 istio 和 istio-sidecar-injector 这两个 ConfigMap 中,其中包含了 Go template,所谓自动 sidecar ...
- GitlabCI/CD&Kubernetes项目交付流水线实践
GitlabCI实践 GitLabCI/CD基础概念 为什么要做CI/CD? GitLab CI/CD简介 GitLabCI VS Jenkins 安装部署GitLab服务 GitLabRunner实 ...
- Linux 服务器性能测试报告-sysbench命令实践
Linux 服务器性能测试报告 我们使用linux 工具sysbench 来测试linux服务器性能,目前在Centos上进行操作 Install sysbench yum -y install sy ...
- Python爬虫知乎文章,采集新闻60秒
前言 发现很多人需要新闻的接口,所以自己去搜索了下,发现知乎上正好有对应的用户每天发布新闻简讯,所以自己想写一个新闻的爬虫.如果想做成接口的话,可以加上flask模块即可,这里就暂时只进行爬虫部分的编 ...
- [Fundamental of Power Electronics]-PART I-2.稳态变换器原理分析-2.5/2.6 多极点滤波器电压纹波估计及要点小结
2.5 含两极点低通滤波器变换器的输出电压纹波估计 在分析包含两极点低通滤波器的变换器如Cuk变换器及Buck变换器(图2.25)输出时,小纹波近似将会失效.对于这些变换器而言,无论输出滤波电容的值是 ...
- 201871030103-陈荟茹 实验二 个人项目―《D{0-1}KP问题》项目报告
项目 内容 课程班级博客链接 班级博客链接 这个作业要求链接 作业要求链接 我的课程学习目标 1.理解掌握软件设计的过程中的各个环节2.掌握github的使用,将自己的项目上传至githu中 这个作业 ...
- 将一个字符串进行反转:将字符串中指定部分进行反转。比如“abcdefg”反转为”abfedcg”
将一个字符串进行反转:将字符串中指定部分进行反转.比如"abcdefg"反转为"abfedcg"方式一:转换为char[] public String reve ...
- B1029/A1048 旧键盘损坏了,在输入一段文字时坏了的键不可以正常使用,现给出应输入的一段文字,和实际输出的文字,找出坏掉的键。
#include<cstdio> #include<cstring> const int maxn = 1000; bool HashTable[maxn] = { false ...
- commons-pool2 池化技术探究
一.前言 我们经常会接触各种池化的技术或者概念,包括对象池.连接池.线程池等,池化技术最大的好处就是实现对象的重复利用,尤其是创建和使用大对象或者宝贵资源(HTTP连接对象,MySQL连接对象)等方面 ...
- red and black(BFS)
Red and Black Time Limit: 1000MS Memory Limit: 30000K Total Submissions: 40685 Accepted: 22079 D ...
