How to verify Certificate Pinning?
Some friends of mine they worry about the risk of Man-in-the-middle so they ask me how to verify the potential risk of some Apps.
Take a popular shopping app “X” for example, If “X” does not meet the requirement of “Certificate Pinning”, we could definitely use proxy tool like Burp Suite to intercept any confidential between mobile device and servers.
- Run Burp Suite on my laptop and my laptop becomes a proxy server. (Don’t foreget to change policy of firewall to allow connection to its proxy server listening port.)
- Download Certificate from Burp Suite and install this cert file into my mobile phone.
- Setup the proxy server ip and port in my mobile phone’s wifi settings.(Of course the ip is my laptop’s ip; the port number is the listening port of proxy server on my laptop)
- Make sure Burp suite is ready to intercept packets.
Now we could run this app “X” and start to login. Let’s see what data Burp could intercept. To my surprise “nothing” found in intercept tab.
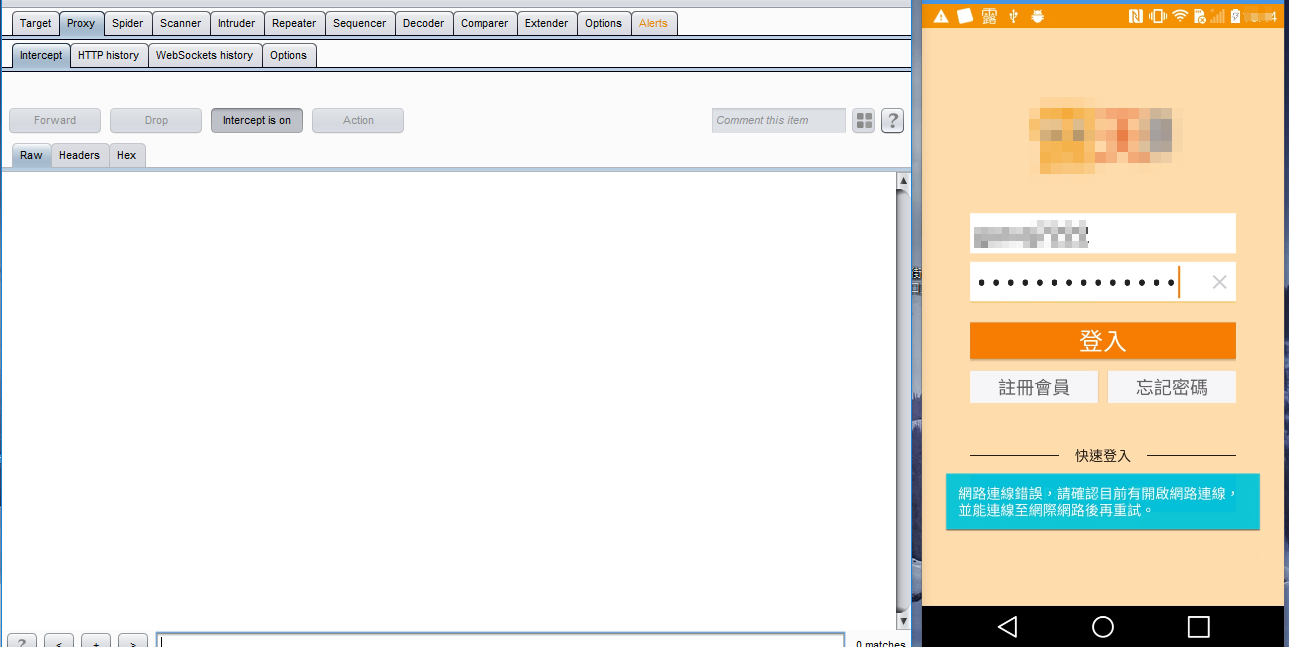
The “Alert” tab turns orange means something happens. It looks like “X” could meet the requirement of certificate pinning.
Don’t jump to conclusions too soon. Let’s take a look at account registry. Input some data such as ID, username , password, phone number, e-mail and click “Submit”. Guess what? Those confidential data being intercepted by Burp suite.
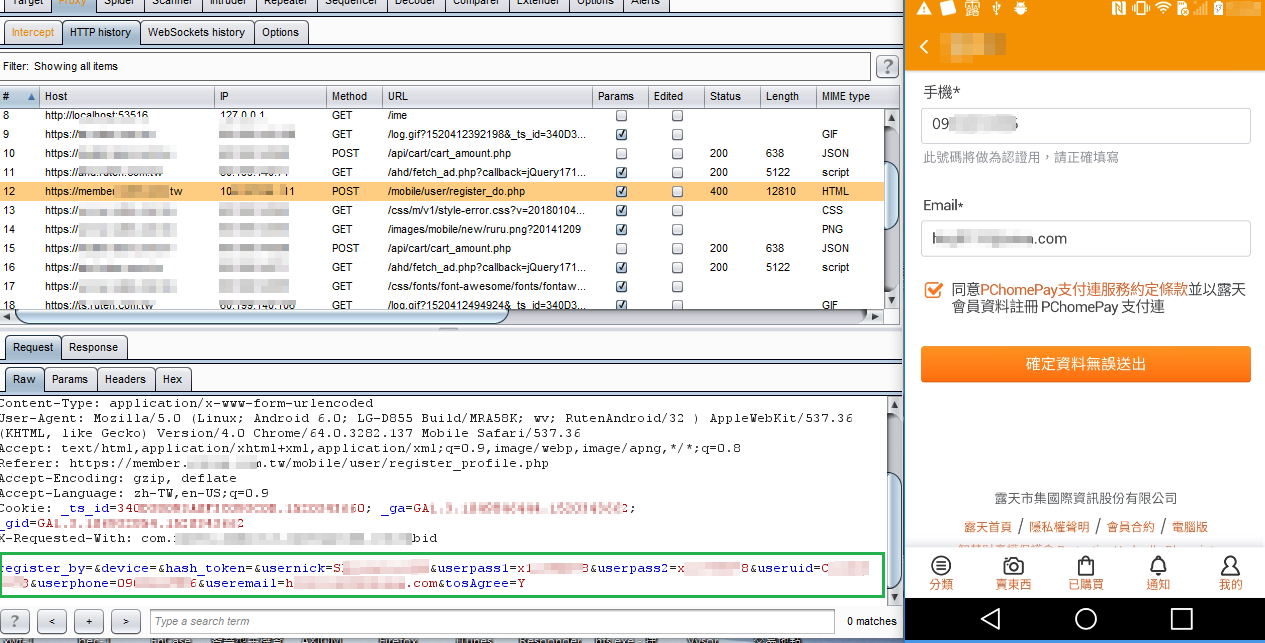
“X” still need to do certificate pinning to avoid the risk of MITM. Now my friends know how to verify certificate pinning by using proxy.
How to verify Certificate Pinning?的更多相关文章
- 008_ssl Certificate Pinning
证书锁定Certificate Pinning技术 在中间人攻击中,攻击主机通常截断客户端和服务器的加密通信.攻击机以自己的证书替代服务器发给客户端的证书.通常,客户端不会验证该证书,直接接受该证书, ...
- 证书锁定Certificate Pinning技术
证书锁定Certificate Pinning技术 在中间人攻击中,攻击主机通常截断客户端和服务器的加密通信.攻击机以自己的证书替代服务器发给客户端的证书.通常,客户端不会验证该证书,直接接受该证 ...
- Mobile game analysis
Let's take a look at a very popular mobile game "Garena 传说对决" . It would be very interesti ...
- Mobile game forensics
My friend Carrie'd like to know "Garena 传说对决" violates any mobile risks such as insecure d ...
- About certificate
证书spec, X509, 类似规定了一个目录结构.其中重要内容包括 issuer: who isued this certificate subject: the ID of this certif ...
- 证书锁定SSL/TLS Pinning
前言 APP端抓包中, 设置抓包代理后会发现部分APP(如app store.Facebook)直接无法访问,其他部分app又功能正常,为什么呢?这涉及 ssl-pinning,证书锁定. 证书锁定( ...
- IP, TCP, and HTTP--reference
IP, TCP, and HTTP Issue #10 Syncing Data, March 2014 By Daniel Eggert When an app communicates with ...
- Android 1.5-7.0(持续更新)安全机制一览
Android 1.5 ProPolice to prevent stack buffer overruns (-fstack-protector),在缓冲区buffer与返回地址之间加入Canary ...
- OkHttp 官方Wiki【设计思想】
官方Wiki之Calls 原文位置:https://github.com/square/okhttp/wiki/Calls The HTTP client's job is to accept you ...
随机推荐
- BZOJ 3991: [SDOI2015]寻宝游戏 [虚树 树链的并 set]
传送门 题意: $n$个点的树,$m$次变动使得某个点有宝物或没宝物,询问每次变动后集齐所有宝物并返回原点的最小距离 转化成有根树,求树链的并... 两两树链求并就可以,但我们按照$dfs$序来两两求 ...
- Windows Server 2016-FSMO操作主机角色介绍
FSMO五个操作主机角色 1.林范围操作主机角色(两种): 架构主机角色:Schema Master 域命名主机角色:Domain Naming Master 2.域范围操作主机角色(三种): 域范围 ...
- mongodb window安装配置
下载mongodb安装包 1. https://www.mongodb.org/dl/win32/x86_64-2008plus-ssl?_ga=2.233271640.711265466.15193 ...
- Windows实用快捷键
1 返回上一级目录:Backspace 2 复制当前窗口:Ctr + N 3 在当前文件目录中选定首个文件(夹):Space 4 切换窗口:Alt + Tab 5 当前浏览器Tab页倒退或前进历史页 ...
- Arbiter 系统使用说明
Arbiter 系统使用说明 Overview Arbiter是NOI系列赛事的官方评测软件, 由北航的相关人员开发. 在OIer会经历的几场大型比赛中, 除了省选和PKUSC/THUSC不使用Arb ...
- easyui+ajax获取同表关联的数据
easyui是我们常用的前端框架之一,easyui的使用使得前端页面更加美观.为了能够使用combobox,ajax必须同步. 该小程序是使用ssm框架,对数据库的数据进行查询,所以url对应着map ...
- 对 url 中含有的中文进行转码操作
对 url 中含有的中文进行转码操作 一般情况下,将带有中文的 url 拷贝到开发工具,开发工具都会有相应的转码(自动转码), 现在大部分的浏览器也可以对含有中文的 url 进行转码(自动转码) 情景 ...
- XAMPP环境访问非Web DocumentRoot下绝对路径
假设你的XAMPP网站文档根目录在C:/xampp/apache/htdocs/下面,那么访问这个目录下的文件是很直接的. 但是有时候需要把用户上传文件指定到特殊目录,比如E盘,那么就需要用户能够访问 ...
- linux下卸载已安装的软件
1.先查询该软件是否安装,是否存在 rpm -qa | grep -i teamview 2.根据一中的结果(软件包名称),执行如下命令 rpm -e [软件包名]
- Visual Studio 2017 Enterprise 发布 15.3.2 版,附离线安装包下载。
Visual Studio 2017 Enterprise 更新至 15.3.2 ,本安装包使用微软原版安装文件,配合layout指令全量下载后制作,内置中文语言包,包含 Visual Studio ...
